5 BYOD Challenges & Solutions For Mitigating Associated Risks
BYOD, or Bring Your Own Device, is a double-edged sword that increases work productivity while putting businesses at risk of exposing confidential and sensitive data.1
BYOD was born out of the increasing prevalence of personal mobile devices, such as smartphones and tablets, in the workplace. The concept emerged as employees started to bring their personal devices to work and began using them to access work-related applications, email, and data.
This article looks into the challenges BYOD poses to cybersecurity in terms of endpoint security and data security.
5 challenges of BYOD
Though BYOD implementations are popular and widely applied, the management of BYOD comes with multiple challenges that increase pressure on cybersecurity. Here are 5 common challenges companies face when implementing BYOD.
1- Lack of employee training & employee confusion
Many security breaches that result in data loss occur due to human error or negligence. Employees may not be aware of the security risks associated with BYOD or may not follow best practices for securing their devices. Providing regular training and awareness of BYOD rules is essential.
2- Policy definition and implementation
Enforcing security policies on personal devices can be challenging. Organizations need clear and comprehensive policies regarding BYOD usage, including acceptable use, data handling, security protocols, etc. Ensuring that employees adhere to these policies can be difficult. Device control policies are such policies that define security measures and promote adherence to security rules.
3- Privacy concern
Employees may become concerned that their privacy is being restricted if they are asked to refrain from using specific applications that have extra requirements, like maintaining a secure network connection. As a result, employees may lack the motivation to follow the BYOD rules defined in the policy.
4- Lack of uniformity & inability to control devices
The task of asset management and maintaining an updated asset inventory may be strained by the use of various types of network devices, as pointed out in endpoint security statistics. Employee-owned personal devices used for work may be tagged or labeled before being added to the asset inventory. Devices may need to meet minimum requirements in order to run specific apps or adhere to safe connection guidelines. IT teams can ensure that devices are used securely and effectively.
5- Loss of data when devices are lost or stolen or an employee leaves
As pointed out in endpoint security best practices, lost or stolen devices make up the category that has the second highest probability of resulting in data breaches. Unmanaged personal devices carry the risk of unauthorized access, which in turn leads to data loss or breaches. Here are some common endpoint threats that utilize unauthorized access in different ways.
What is BYOD?
It is an utilized implementation in workplaces or educational institutions where employees or students are allowed to use their personal electronic devices, such as laptops, smartphones, or tablets, for work or learning purposes. This trend has become increasingly popular due to the proliferation of personal devices and the desire for flexibility and convenience in accessing work or educational resources. There are different kinds of BYOD, as below.2
- BYOD-as-a-Complement: In this approach, BYOD is used alongside existing company-provided devices. Employees or students are allowed to bring their own devices, but the organization still provides devices as needed. This strategy offers flexibility and allows individuals to use devices they are comfortable with while still ensuring that everyone has access to necessary tools.
- BYOD-as-a-Replacement: This approach involves replacing company-provided devices entirely with personal devices brought in by employees or students. The organization no longer purchases or provides devices for work or educational purposes, relying entirely on individuals bringing their own devices. This strategy can result in cost savings for the organization but may also introduce challenges in terms of device compatibility, security, and support.
- BYOD-as-an-Addition: In this approach, BYOD is introduced as an additional option alongside existing company-provided devices. Employees or students can choose to use their own devices in addition to those provided by the organization. This strategy provides flexibility and accommodates individual preferences while still ensuring that everyone has access to the necessary tools and support.
Intel’s trust approach to BYOD
Intel has been an early advocate of BYOD implementation. Back in 2012, the company published a white paper on “Delivering Cloud-Based Services in a Bring Your Own Device Environment” in which it talks about taking advantage of BYOD initiatives while staying aware of the related security risks. The technology company shows the positive outcomes correlated with BYOD while highlighting the need for new perspectives on aspects such as trust.3 The company delivers an appropriate approach on devices by calculating security control in accordance with the sensitivity level of the data or source in question.4 The figures below depict Intel’s trust approach to the use of personal devices.
Figure 1. Schema of Intel’s Trust Architecture
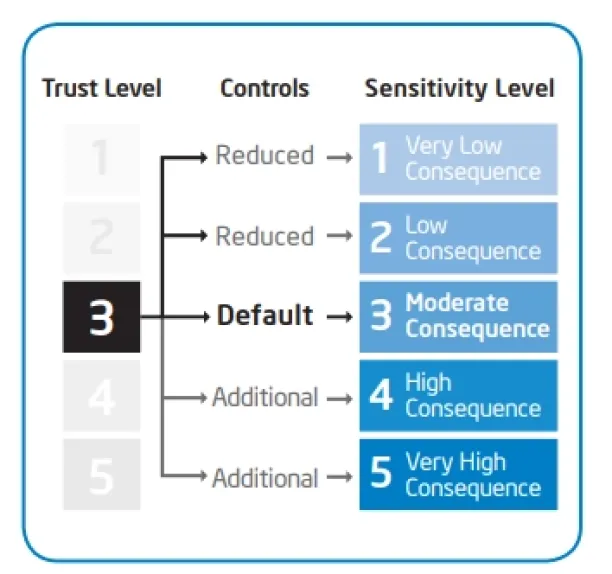
Source: Intel IT.5
Figure 2. Schema of Intel’s Trusted Application Portal
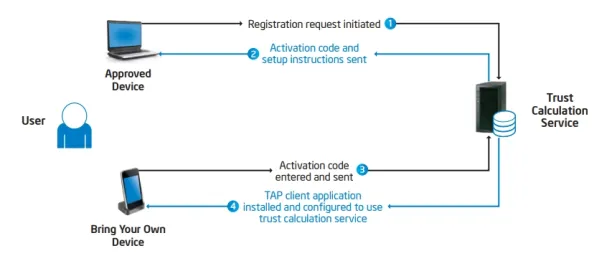
Source: Intel IT.6
5 cybersecurity solutions to mitigate BYOD risks
As depicted in the above appearing figures, security measures focused on the sensitivity level of operations and data motivate businesses to seek authentication and authentication tools. Such tools can range from multi factor authentication (MFA) to an approach that has broader coverage, such as the Zero Trust Approach (ZTNA). Below are 5 perspectives on mitigating BYOD security risks.
1- Defining a BYOD security policy
Establishing well-defined guidelines facilitates BYOD adoption by both employees and employers. Making sure the policy includes privacy terms and legal commitments helps both parties come to an agreement on BYOD rules.
2- Regularly update software and operating systems
Regularly updating devices mitigates security risks by eliminating vulnerabilities. Endpoint management tools such as patch management feature help make sure endpoints are up to date.
3- Application installation control
Restricting the installation of potential security risk carrying applications helps prevent vulnerabilities.
4- Encryption for data at rest and in transit
For more on endpoint encryption
5- Secure each device’s connection
Secure network connection help sensitive data and endpoints by implementing various measures to protect against unauthorized access, data breaches, and other security threats. Here’s more on network security best practices
FAQ
1- What is the difference between managed devices and unmanaged devices?
The difference between managed and unmanaged devices lies in how they are controlled, monitored, and maintained within an organization’s network environment.
Managed devices are centrally controlled, monitored, and maintained by the organization’s IT department or a managed service provider, while unmanaged devices are not subject to such oversight and may pose security and compliance risks within the organization’s network environment.
2- What are Bring Your Own Service (BYOS) and Bring Your Own Apps (BYOA)?
Bring Your Own Service (BYOS) and Bring Your Own Apps (BYOA) are similar concepts to Bring Your Own Device (BYOD), but they focus on employees or users bringing their own software services or applications into the workplace environment.
Further reading
- Top 9 Hexnode Alternatives Based on 10K+ Reviews
- Top 5 NinjaOne Alternatives Based on 4.5K+ Reviews
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. “Management Briefing:Bring your own device – Effective policies and practice” (PDF). Intel UK IT Center. Retrieved April 17, 2024.
- 2. “Understanding the Bring-Your-Own-Device landscape” (PDF). Deloitte UK. Retrieved April 17, 2024.
- 3. “Understanding the Bring-Your-Own-Device landscape” (PDF). Intel IT. Retrieved April 17, 2024.
- 4. “Granular Trust Model Improves Enterprise Security” (PDF). Intel IT. Retrieved April 17, 2024.
- 5. “Granular Trust Model Improves Enterprise Security” (PDF). Intel IT. Retrieved April 17, 2024.
- 6. “Granular Trust Model Improves Enterprise Security” (PDF). Intel IT. Retrieved April 17, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.