According to Microsoft’s Digital Defense Report, the most common case of cybercrime is unauthorized access to unmanaged devices.1
With the rise of bring-your-own-device (BYOD) implementations and remote/hybrid work trends, businesses are strengthening their network security measures to prevent security compromises. Endpoint management software solutions provide IT professionals with the necessary tools to orchestrate network elements securely and efficiently.
Analyze the top 5 endpoint management software based on differentiating features such as remote support and file sharing.
Top 5 endpoint management software comparisons
Features
| Product | Remote support | File sharing |
|---|---|---|
| NinjaOne Endpoint Management | ✅ | ❌ |
| Microsoft Intune | add-on | ✅ |
| VMware Workspace One | ✅ | ✅ |
| Cisco Meraki System Manager | ✅ | ✅ |
| Citrix Endpoint Management | ✅ | ✅ |
See definitions for common and differentiating features.
Prices
| Product | Pricing | Price | Free trial |
|---|---|---|---|
| NinjaOne Endpoint Management | pay-per-endpoint | n/a | ✅ |
| Microsoft Intune | pay-per-endpoint | n/a | ✅ |
| VMware Workspace One | pay-per-endpoint | $1.66 | ❌ |
| Cisco Meraki System Manager | pay-per-endpoint | n/a | ✅ |
| Citrix Endpoint Management | pay-per-endpoint | n/a | ❌ |
Reviews & ratings
| Product | Total number of reviews* | Average score* | Number of employees** |
|---|---|---|---|
| NinjaOne Endpoint Management | 1,428 | 4.7 | 1,000 |
| Microsoft Intune | 163 | 4.0 | 244,900 |
| VMware Workspace One | 63 | 4.4 | 287 |
| Cisco Meraki System Manager | 52 | 4.0 | 100,466 |
| Citrix Endpoint Management | 27 | 4.0 | 5,012 |
*Based on the total number of reviews and average ratings (on a 5-point scale) from leading software review platforms.
**The number of employees is gathered from publicly available resources (i.e., LinkedIn).
Ranking: Vendors with links are sponsors and listed at the top. Other products are ranked based on their total number of reviews.
Analysis of the endpoint management software
NinjaOne Endpoint Management
NinjaOne, formerly NinjaRMM, provides tools for IT teams and MSPs, including automated patch management, remote monitoring and management, endpoint management, and mobile device management (MDM).
Pros
- Asset management and ease of use: Users claim it is easy to use and find the asset management features efficient.
- Policy management: Reviewers praise the tool, adding that it is customizable and easy to use.
Cons
- User interface: Reviewers admit that though a single platform enables ease, the graphic interface can be improved.
- 3rd party integrations: Some users are not content with the available 3rd party integrations, such as Splashtop and TeamViewer.
Microsoft Intune
Intune is Microsoft’s endpoint management solution and benefits from deep integrations to the Microsoft ecosystem (i.e., Windows operating systems and software applications such as Microsoft 365).
Pros
- Easy to use: The product’s remote monitoring and management capabilities are praised by the reviewer.
- Integration: The product is claimed to be seamlessly integrated with the Microsoft ecosystem.
Cons
- App management: The app management tool is found to be problematic by the reviewer. The tool is time-consuming because it demands unnecessary tasks.
- Operating system compatibility features: The product is found to be less efficient on macOS than on Windows.
For a Microsoft solution in an adjacent category, see Microsoft Purview DLP and its alternatives.
Omnissa previously VMware Workspace One
VMware is a cloud computing company that produces app management tools, and cloud-based security and networking software solutions. VMware was acquired by Broadcom Inc in 2023 and its end-user computing products were spin-off under the brand Omnissa.
Pros
- MDM: According to multiple reviewers, the AirWatch feature makes mobile device management practical.
Cons
- Learning curve: Users claim that the product demands a steep learning curve.
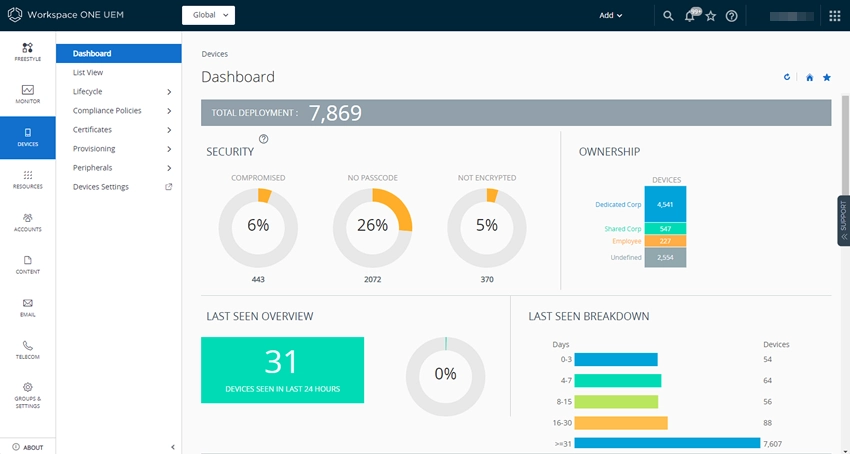
Source: VMware
Figure 4. The above screenshot captures Workspace One UEM’s dashboard.
Cisco Meraki System Manager
Cisco designs and sells a broad range of technologies, including networking hardware, telecommunications equipment, and high-technology services and products.
Pros
- Device configuration: The device configuration is found to be practical.
Cons
- Cost: According to multiple users, the total cost is deemed expensive.
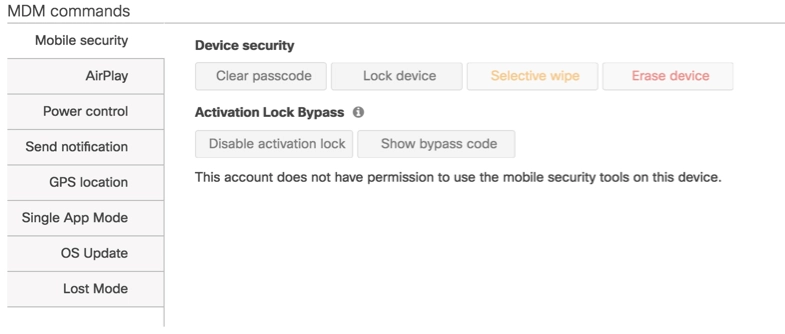
Source: Documentation Meraki
Figure 5. The above screenshot captures Meraki’s MDM common page.
Citrix Endpoint Management
Citrix delivers IT solutions focused on hybrid/remote work settings, such as employee work performance analytics, remote connection services, network access solutions, and endpoint management.
Pros
- Mobile access: Users report being pleased with mobile access to the product.
- Easy to use: Most users are satisfied with the product’s easy setup.
Cons
- Updates: The updates run on the product are found to be slow.
- System performance: Some users describe the deployment process as time-consuming due to the numerous features the product offers.
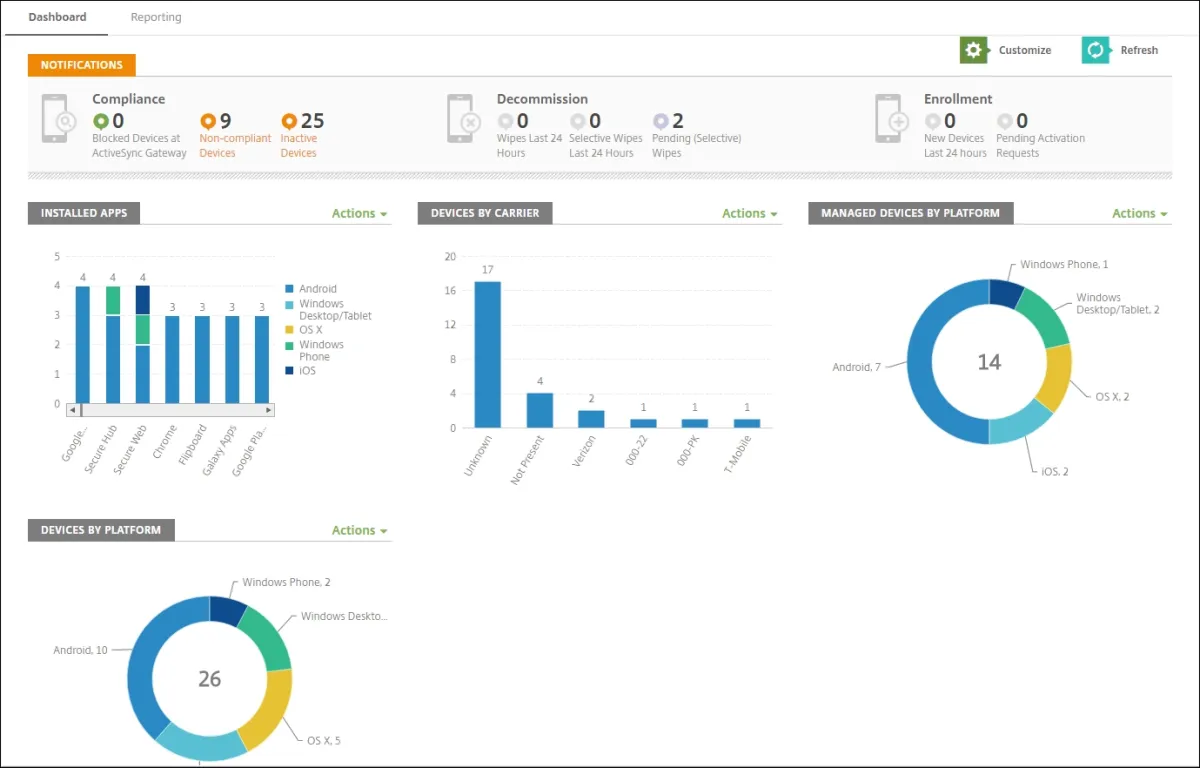
Source: Citrix
Figure 7. The above screenshot captures Citrix Endpoint Management’s dashboard.
How does the remote working trend affect the IT industry?
The rapid development of network and remote connection technologies is correlated with the hype around hybrid and remote working hype around the world. Employees and employers prefer remote working over traditional on-prem work because of its promising advantages, such as enhanced productivity and decreased costs for both sides.
According to the data summarized by Forbes, remote working in the US will rise and make up 22% of the workforce by 2025.2 Data indicates that remote working is becoming more common, and this will put additional pressure on IT security systems to maintain adequate and secure network systems.
IT teams and managed service providers (MSPs) will utilize qualified software solutions for endpoint management and security. Device management and endpoint security, with a focus on network security solutions, will be in high demand. According to Statista, the global market for endpoint security is expected to rise to $27 billion by 2027.
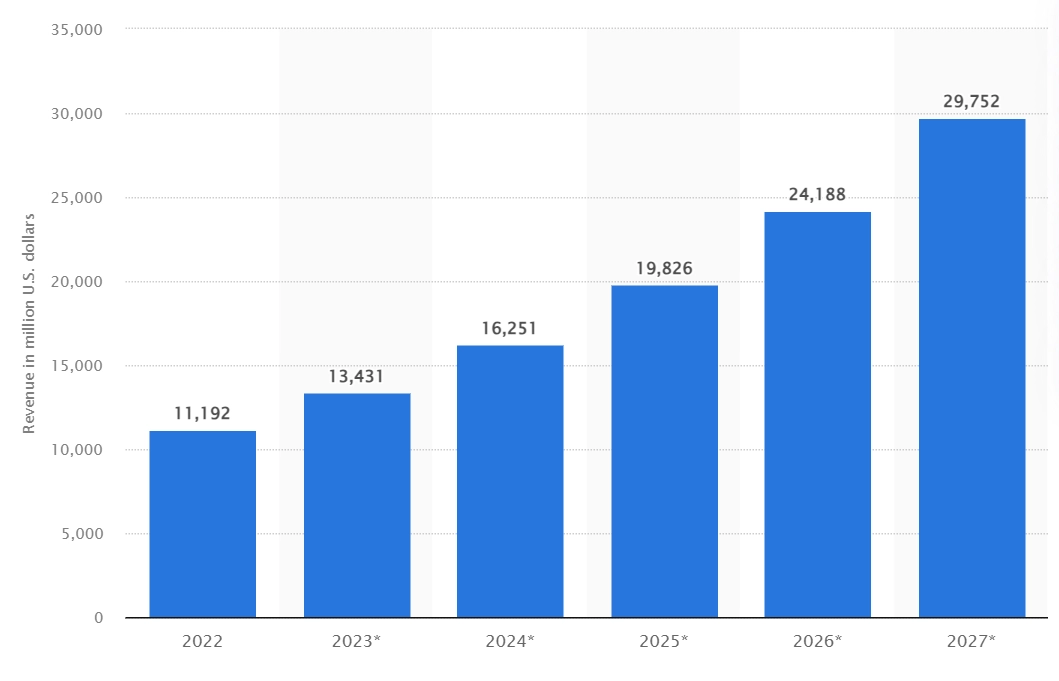
Source: Statista
Figure 8. The above column graph shows the projected revenue values of the endpoint security market from 2023 to 2027.
What does endpoint management software do?
Endpoint management software protects network devices, including mobile phones, PCs, USBs, and other hardware, against data loss and malicious attacks that aim at data theft. Endpoint management software also ensures the efficiency of the network system by regularly monitoring and managing it.
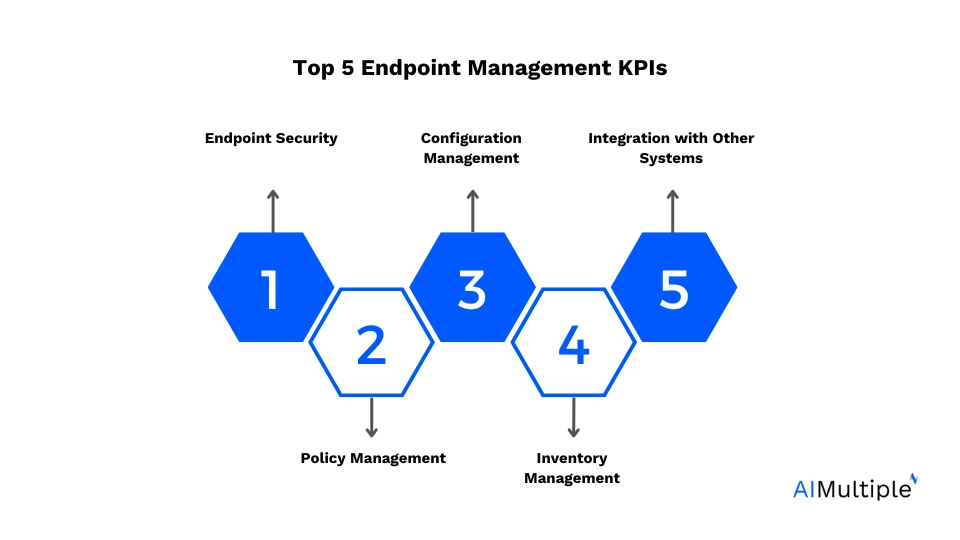
What are endpoint management software capabilities?
Endpoint management software typically offers a wide range of capabilities to help organizations efficiently manage their endpoint devices. Here are some common capabilities:
1. Inventory management: Keep track of all endpoint devices connected to the network, including hardware specifications, software inventory, and network configurations.
2. Configuration management: Remotely configure settings and policies on endpoint devices, such as security configurations, network settings, and software configurations.
3. Patch management: Automate the deployment of software updates and security patches to ensure that all endpoint devices are up-to-date and protected against vulnerabilities.
4. Security management: Enforce security measures such as antivirus software, firewalls, encryption, and compliance with security policies and standards.
5. Remote monitoring and troubleshooting: Monitor the health, performance, and security status of endpoint devices in real-time and troubleshoot issues remotely.
6. Remote deployment and software distribution: Remotely deploy new software applications, updates, and patches to endpoint devices without the need for physical access.
7. Policy enforcement: Define and enforce policies governing device usage, data access, and security practices across the organization.
8. Asset tracking and reporting: Track the usage, performance, and status of endpoint devices over time and generate reports for auditing, compliance, and optimization purposes.
9. Integration with other systems: Integrate with other IT systems such as identity management, ticketing systems, and network monitoring tools to provide a comprehensive IT management solution.
10. Mobile device management (MDM): Manage mobile devices such as smartphones and tablets, including security, application management, and data protection.
11. User and access management: Manage user access to endpoint devices, applications, and data, including user authentication, authorization, and access control.
12. Backup and recovery: Provide backup and recovery capabilities for endpoint devices to protect against data loss and enable quick recovery in the event of hardware failures or security incidents.
13. Compliance management: Ensure compliance with regulatory requirements and industry standards by enforcing security policies, tracking compliance status, and generating compliance reports.
Top 3 challenges for endpoint management software
Implementing endpoint management can come with its own set of challenges. Here are three common ones:
1. Device diversity: One challenge is managing the diversity of endpoint devices within an organization. Companies often have a mix of devices running different operating systems (Windows, macOS, Linux, iOS, and Android), each requiring unique management configurations and tools. Ensuring consistency and compatibility across this diverse landscape can be a significant challenge for IT administrators.
2. Security risks: With the increasing number of endpoints connected to corporate networks, security risks multiply. Endpoint devices are often the target of cyberattacks, including malware, ransomware, and phishing attempts.
Implementing effective endpoint security measures, such as antivirus software, firewalls, encryption, and patch management, while ensuring compliance with security policies and regulations, is a constant challenge for IT teams.
3. Remote workforce management: The rise of remote work has further complicated endpoint management. With employees accessing corporate resources from various locations and devices, IT administrators need to ensure secure remote access, enforce security policies, and manage endpoint devices outside the traditional corporate network perimeter.
Balancing security and usability for remote workers while maintaining visibility and control over endpoint devices poses a significant challenge for IT teams.
Top 3 best practices for endpoint management software
Implementing endpoint management effectively involves following best practices to ensure smooth operation, security, and efficiency. Here are three key practices:
1. Inventory and asset management: Begin by establishing a comprehensive inventory of all endpoint devices within the organization. This includes desktops, laptops, servers, mobile devices, and any other network-connected devices.
Maintain detailed records of hardware specifications, software inventory, network configurations, and ownership information.
Regularly update the inventory to reflect changes in the IT environment, such as new device deployments, retirements, or replacements. Having a complete understanding of the endpoint landscape is crucial for effective management, security, and compliance.
2. Centralized policy management and automation: Implement centralized policy management and automation to streamline configuration, security, and compliance management across all endpoint devices.
Define and enforce standardized policies governing device configurations, security settings, software installations, and user access controls.
Leverage automation tools and scripts to deploy and enforce policies consistently across the organization, reducing manual effort and minimizing the risk of configuration errors.
Regularly review and update policies to align with evolving security threats, regulatory requirements, and business needs.
3. Continuous monitoring and remediation: Implement robust monitoring and remediation processes to detect and address security threats, compliance violations, and performance issues across endpoint devices.
Utilize endpoint management software to monitor device health, security status, and compliance posture in real-time. Set up alerts and notifications to promptly identify and respond to security incidents, system errors, or policy violations.
Establish proactive remediation workflows to address identified issues swiftly, such as deploying security patches, quarantining malware-infected devices, or initiating user education and awareness campaigns.
Regularly conduct vulnerability assessments, security audits, and compliance checks to ensure the effectiveness of monitoring and remediation efforts.
Common features for endpoint management software
- Inventory management: Tracks and manages hardware and software assets across an organization’s IT environment.
- Application management: Oversees and maintains the performance and availability of software applications.
- Compliance reports: Generate documentation that ensures systems and processes adhere to regulatory and internal standards.
- Compliance monitoring: Continuously checks and ensures that IT systems comply with relevant policies, regulations, and standards.
- Alerting & notifications: Sends real-time alerts and notifications about system issues, performance problems, and security breaches.
- Audit logs: Records detailed logs of system activities and user actions for security and compliance purposes.
- Policy management: Defines, deploys, and enforces IT policies and procedures across an organization.
- Patch management: Automates the process of applying updates and patches to software and systems to ensure security and functionality.
- Auto-remediation: Automatically resolves detected issues and system errors without human intervention.
- Developer tools: Offers software and utilities to aid developers in creating, debugging, and maintaining applications.
Differentiating features for endpoint management software
- Pricing: Determines the cost structure; often based on subscription or usage.
- Remote support: Provides assistance and troubleshooting for IT issues from a remote location. Enables remote lock, wipe, and block controls for admins.
- File sharing: Enables the secure exchange and collaboration on files between users and systems.
FAQ
1. What is the difference between endpoint management and endpoint security?
Endpoint management is a compact IT solution that gives its users control over devices by administering policies that set access and authorization rules in order to keep endpoints managed, and it also delivers automation on IT tasks that help IT administrators gain control over updates, system failures, and configuration changes.
Endpoint security aims to keep endpoints secure by utilizing security tools such as VPNs, firewalls, antivirus programs (AVs), and encryption. In order to succeed at keeping endpoints secure, endpoint security solutions work hand in hand with endpoint management tools such as endpoint monitoring and policy management. The two security solutions focus on endpoints to sustain a safe network system by utilizing endpoint detection and response tools, automation tools, and connection tools.
2. What is the difference between device control and mobile device management (MDM)?
Device control tools maintain the security of the network by controlling access to a range of devices, including printers, USBs, HDDs, CDs, Bluetooth devices, USB modems, card readers, memory cards, webcams, and removable drives. Device control aims at preventing unauthorized access to data-at-rest and data-in-transit with encryption and authentication features. For more on device control and device control products, see.
While networked devices can be tracked within the scope of the network, mobile devices, when not connected to the network, are still able to transfer sensitive data. Using mobile devices outside of network range increases the risk of malware attacks and data breaches in bring-your-own-device (BYOD) settings. Endpoint management, by utilizing mobile device management functionalities, can limit access to sensitive data and applications of choice.
Further reading
- Top 10 USB Blocking Software: Based on 3.9K+ Reviews
- Top 10 Device Control Software: Review-based Analysis
- Top 10 RMM Software: Analysis From 7,700+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:


Comments
Your email address will not be published. All fields are required.