Digital information is constantly being shared and stored on cloud and connected services. According to IBM, the average cost for a data breach involving 50 million to 65 million records is more than $400 million.1 Protecting sensitive data is the backbone of cybersecurity, and encryption has become a critical tool in safeguarding personal and confidential information due to cyber threats appearing in numerous instances.
We cover the definition of data encryption, its various types, importance, challenges, and the best practices for implementing it effectively.
What is data encryption?
Data encryption converts plain text into unreadable code to protect sensitive information from unauthorized access. It uses algorithms to scramble data to prevent unauthorized access and ensure the confidentiality and integrity of the data.
Encryption is data security’s fundamental building block; it aims to protect sensitive information from unauthorized access, theft, or manipulation, ensuring the confidentiality and integrity of the data. It helps to secure sensitive data transmitted over networks, stored on devices, and shared between systems and users.
WhatsApp, for example, employs an end-to-end encrypted messaging system, which means that only the sender and receiver can see what is sent via the app.(See Figure 1)
Source: Teskalabs2
Figure 1. WhatsApp end-to-end encryption
Why is data encryption important for businesses?
In technology-based businesses, data encryption is widely used in backup and archiving, internet communications, internal networks, etc.3 According to research, seven million unencrypted data records are compromised every day.4 encryption is essential for several reasons:
- Confidentiality: It prevents unauthorized access to sensitive information, ensuring that only authorized users can view it.
- Security: Encryption helps protect data from theft or hacking, making it more difficult for attackers to access and steal sensitive information, thus improving data security.
- Compliance: In many industries, data encryption is a requirement to meet regulations, such as HIPAA for healthcare and PCI DSS for payment card data.
- Privacy: Encrypt data protects personal information, such as financial and health records, from being accessed or used without permission.
- Trust: Encryption helps to build trust between organizations, customers, and partners by demonstrating a commitment to protect sensitive information.
Encryption is especially used to protect sensitive data in industries like healthcare, where compliance and confidentiality are top priorities. For examples of how it’s applied in practice, see our article on data encryption in healthcare.
Encryption also complements endpoint security strategies. When data is stored or accessed on devices, endpoint encryption adds another layer of protection, especially in remote or hybrid work settings.
How does data encryption work?
Data encryption works by converting plaintext into unreadable code using encryption algorithms and keys. The encrypted data is known as ciphertext and can only be decrypted and read by someone with the correct decryption key.
The steps of the data encryption process can be listed as:
- Key Generation: A unique encryption key is generated, which is used to encrypt and decrypt the data.
- Encryption: The encryption algorithm and the encryption key are processed by the plain text data, producing a ciphertext.
- Transmission: The encrypted data (ciphertext) is transmitted or stored on devices.
- Decryption: The ciphertext is decrypted by the decryption key and the encryption algorithm, converting it back into plain text.
The strength of the encryption process depends on the encryption algorithm and the protection of the encryption key. The encrypted data can be easily compromised if the encryption key is lost or stolen.
What are the types of data encryption?
There are two types of data encryption:
Symmetric encryption
Also known as shared-key encryption, it uses the same key for encryption and decryption. The key must be kept secret and shared only between the sender and recipient of the encrypted data as seen in Figure 2. For example, Advanced Encryption Standard (AES encryption) is a widely-used symmetric encryption algorithm.
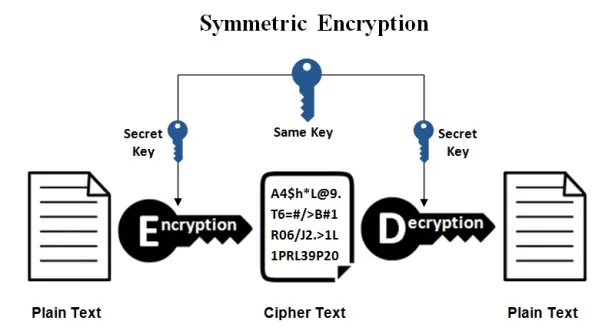
Source: Ssl2buy5
Figure 2. The visualization of symmetric encryption
Asymmetric encryption
Also known as public-key encryption, it uses two different keys, one for encryption and one for decryption. The encryption key can be public, while the decryption must be private. This type of encryption is commonly used for secure communication and digital signatures as seen in Figure 3. For example, RSA encryption is a widely-used public-key encryption algorithm.
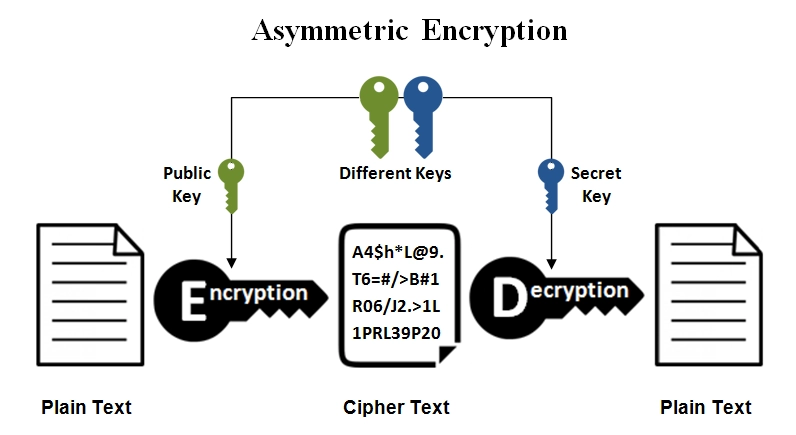
Source: Ssl2buy6
Figure 3. Visualization of asymmetric encryption
Other encryption types include:
- Block encryption: Refers to encrypting data in fixed-size blocks.
- Stream encryption: Encrypts data as a continuous stream of bits or bytes.
A key component of any encryption strategy is how cryptographic keys are handled. Topics like secure storage, rotation, and lifecycle management are covered in detail in our article on encryption key management.
For advanced use cases, some teams are implementing homomorphic encryption, which allows data to be processed while still encrypted—useful in privacy-sensitive applications like healthcare and finance.
Moreover, with the rise of more powerful computing capabilities, organizations are also starting to explore quantum cryptography to prepare for potential threats posed by quantum computers.
Frequently Asked Questions (FAQ) about data encryption
What are the differences between data at rest vs transit?
Data at rest can include files stored on a hard drive, data in a database, or backups stored in the cloud. Encrypting this data helps to ensure that it is unreadable to anyone without the proper decryption key or password.
Data in transit refers to data that is being transmitted from one location to another, such as over a network or through the internet. This data can include sensitive information such as financial data, personal information, or confidential business information.
Encryption at rest is often used in conjunction with encryption in transit, which protects data as it is being transmitted between devices or networks. This combined approach provides a comprehensive layer of security for sensitive data, both when it is stored and when it is in transit.
Is data encryption standardized?
Data encryption is not a standardized technology. However, data encryption tools commonly apply several widely used encryption algorithms and standards.
The U.S. government has embraced the Advanced Encryption Standard (AES), a popular symmetric-key encryption technique widely used in business applications. Businesses should aim to use such standards instead of an outdated data encryption standard. For example, the Data Encryption Standard (DES) was widely used in the 1970s and 1980s but is now considered obsolete and vulnerable to attacks.
In addition to these encryption algorithms, there are also encryption standards such as SSL/TLS, which are used to secure communication over the internet, and various other encryption-related standards and protocols used to encrypt sensitive data.
Can data encryption be hacked?
Data encryption can be vulnerable to hacking if the encryption algorithm or key is weak and if the encrypted data is accessed without proper authorization. However, if the encryption is implemented correctly and the key is kept secure, the encrypted data can be considered secure against most hacking attempts.
Encryption algorithms can become vulnerable to attacks over time as computing power increases and new attack methods are developed, so it is essential to regularly review and update encryption methods to ensure the security of encrypted data.
It is also important to note that the weakest point in an encryption system is often the human element, such as lost or stolen encryption keys, weak passwords, and social engineering attacks. To minimize these risks, it is essential to implement security awareness training for all users.
Can encrypted data be recovered?
Whether encrypted data can be recovered depends on the type and strength of the encryption used and the method of recovery attempted.
If the encryption key is lost or stolen, it may only be possible to recover the encrypted data with the key. In some cases, the encrypted data may be recovered using brute-force attacks, where many keys are tried until the correct key is found. This process can be extremely time-consuming and may not be feasible for large amounts of encrypted data.
In some cases, encrypted data may be recovered using flaws or vulnerabilities in the encryption algorithm or implementation, but this is less likely with well-established and widely-used encryption algorithms. It is important to keep backup copies of encryption keys and implement encryption key management best practices to ensure that encrypted data can be recovered in case of loss or damage.
Is data encryption supported on removable media?
The short answer is yes; data encryption is supported on removable media such as USB drives, external hard drives, and memory cards. Encrypting data on removable media helps protect sensitive information if the media is lost or stolen.
There are several data encryption solutions available that support encryption on removable media. These solutions typically use encryption such as AES or RSA to encode the data, and the encryption key is stored on the removable media or a separate device. This allows the encrypted data to be decrypted only with the proper key or password, helping to ensure that the data remains secure.
Data encryption best practices
- Use robust encryption algorithms: AES, RSA, and Twofish are usually regarded as some of the strongest.
- Keep encryption keys secure: The security of encrypted data is only as strong as the encryption keys used to protect it. Ensure keys are stored securely and restrict access to only authorized personnel.
- Use multi-factor authentication: Adding an extra layer of security through multi-factor authentication helps to prevent unauthorized access to encrypted data.
- Regularly update encryption software: Encryption software is updated regularly to address vulnerabilities and improve safety. Ensure that your encryption software is kept up-to-date.
- Enable data backups: Encrypted data should be backed up regularly to prevent data loss in the event of a cyber attack or hardware failure.
- Encrypt data in transit: Data transmitted over networks should be encrypted to protect it from eavesdropping and interception.
- Conduct security audits: Security audits help identify potential vulnerabilities in your encryption setup and ensure that best practices are followed.
- Educate employees: Ensure that all employees know the importance of encryption and the best practices for using it effectively.
- Use data encryption software: Data encryption software is used to protect sensitive information by converting it into a coded format that can only be deciphered with the right key or password.
Data encryption challenges
- Complexity: Encryption algorithms can be complex and challenging to implement, especially for organizations with limited IT resources.
- Performance overhead: Encrypting and decrypting data can impact system performance and slow down processes.
- Key management: Properly managing encryption keys is crucial to securing encrypted data, but it can also be challenging and time-consuming; 56% of respondents cite encryption key management as a challenging process.
If you want to learn more about cyber security practices, reach us:
External Links
- 1. IBM. “Cost of a Data Breach Report 2021.” 2021
- 2. Better Late Than Never - WhatsApp Is Using End-to-End Encryption – Finally! · TeskaLabs Blog.
- 3. Encryption technology use by business area 2021| Statista. Statista
- 4. The World in Data Breaches. Varonis
- 5. Symmetric vs. Asymmetric Encryption - What are differences?. SSL2BUY
- 6. Symmetric vs. Asymmetric Encryption - What are differences?. SSL2BUY

Comments
Your email address will not be published. All fields are required.