What is Homomorphic Encryption? Benefits & Challenges (2024)
The increasing usage of cloud services and collaboration between companies to monetize data is raising concerns over data privacy. Regulations such as the General Data Protection Regulations (GDPR) aim to protect the privacy of consumers, and businesses pay serious fines in case of non-compliance. This creates a tradeoff between data privacy and utility for companies.
Homomorphic encryption is an emerging technology that can help businesses to ensure the privacy of their customers without undermining their ability to gain insights from their data.
What is homomorphic encryption?
Homomorphic encryption (HE) is a type of encryption method that allows computations to be performed on encrypted data without first decrypting it with a secret key. The results of the computations also remain encrypted and can only be decrypted by the owner of the private key.
How does homomorphic encryption work?
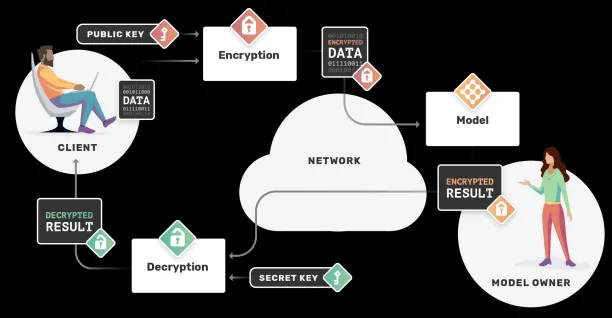
The image below demonstrates how homomorphic encryption works:
- The process starts with data in its decrypted form (i.e., plain text). The owner of the data wants some other party to perform a mathematical operation (e.g., some function, or a machine learning (ML) model) on it without revealing its content.
- The owner encrypts the data with a public key and sends it to the other party.
- The other party receives encrypted data (i.e., cipher text), performs operations on it, and sends the encrypted result to the owner.
- The owner of the data decrypts it with a private key and reveals the result of the intended mathematical operation, which is identical to the result if the unencrypted data had been used.
What are the different types of homomorphic encryption?
There are three main types of homomorphic encryption:
- Partially Homomorphic Encryption (PHE): PHE only allows selected mathematical functions to be performed on encrypted data.
- Somewhat Homomorphic Encryption (SHE): SHE allows a limited number of mathematical operations up to a certain complexity to be performed, for a limited number of times.
- Fully Homomorphic Encryption (FHE): FHE allows any kind of mathematical operation to be performed for an unlimited number of times.
Why is homomorphic encryption important now?
Sharing private data sets with third parties, such as cloud services or other companies, is a challenge due to data privacy regulations such as GDPR and CCPA. Failure to comply with these regulations can lead to serious fines and damage business reputation.
Traditional encryption methods provide an efficient and secure way to store sensitive data on cloud environments in an encrypted form. However, to perform computations on data encrypted with these methods, businesses either need to decrypt the data on the cloud, which can lead to security problems, or download the data, decrypt it, and perform computations, which can be costly and time-consuming.
Homomorphic encryption enables businesses to share private data with third parties to get computational services securely. With HE, the cloud service provider or the outsourcing company has access only to encrypted data and perform computations on it. These services then return the encrypted result to the owner who can decrypt it with a private key.
What are the benefits of homomorphic encryption?
- Allows secure and efficient cloud use: Homomorphic encryption can allow businesses to leverage cloud computing and storage services securely. It eliminates the tradeoff between data security and usability. Businesses don’t have to rely on cloud services regarding the security of their private data while retaining the ability to perform computations on it.
- Enables collaboration: HE enables organizations to share sensitive business data with third parties without revealing the data or the results of the computation to them. This can accelerate collaboration and innovation without the risk of sensitive information getting compromised.
- Ensures regulatory compliance: HE can allow businesses operating in heavily regulated industries, such as healthcare and finance, to get outsourcing services for research and analytical purposes without the risk of non-compliance.
How to implement homomorphic encryption?
Some popular open-source libraries for implementing homomorphic encryption schemes include:
Check Homomorphic Encryption Standardization’s relevant section for more details on different tools.
What are the challenges to homomorphic encryption?
Partial and somewhat homomorphic encryption systems have existed since the late 70s but a fully homomorphic encryption scheme that allows all mathematical operations on encrypted data was first established in 2009 by Craig Gentry. In its current form, fully homomorphic encryption is impractically slow.
It can be said that FHE schemes are still emerging techniques for data security and utility. But it’s a promising one and we are likely to see faster versions of it that can be applied to a variety of use cases. In 2017, Researchers from organizations such as Microsoft, IBM, Google, government organizations and academia have formed a an open consortium to standardize homomorphic encryption and to advance secure computation.
What are alternatives to homomorphic encryption?
As businesses can collect large volumes of data that often contain personally identifiable information (PII) of customers, data privacy is likely to remain a hot topic. There are other cryptography algorithms and privacy-preserving technologies that allow businesses to leverage analytical methods without privacy and non-compliance risks.
For a comprehensive account of privacy-enhancing technologies (PETs), check our article on the topic.
To learn more about cybersecurity best practices you can read our Top 9 Cybersecurity Practices for Corporations article.
If you need a cybersecurity solution in your business, take a look at our cybersecurity software and services hub.
If you still have questions about homomorphic encryption or other privacy-enhancing technologies, we would like to help:

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.