Endpoint Encryption in 2024: 4 Benefits & 3 Best Practices
Unauthorized physical access to endpoint devices (e.g., lost and stolen devices) should not grant unauthorized access to confidential or sensitive data.1 Such incidents may result in data breaches if regulatory and advisory security measurements are not taken.
Endpoint encryption is a crucial component of endpoint security. It assures that data on endpoints is only readable by authorized users and prevents incidents such as data tampering and interception. This article provides key benefits of endpoint encryption by defining its importance, challenges, and best practices.
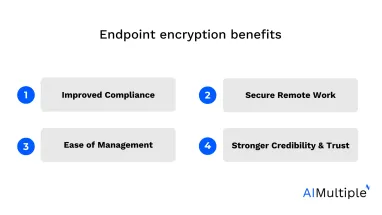
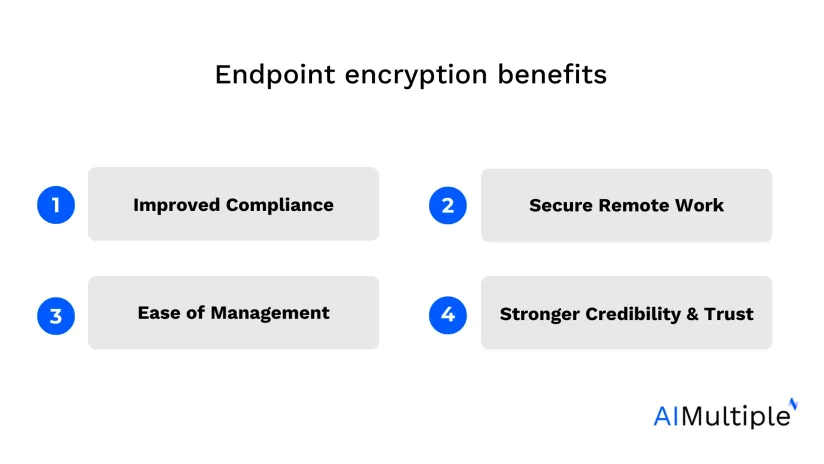
4 key benefits of endpoint encryption
Endpoint encryption strengthens data security, which is one of the main concerns of data loss prevention (DLP) solutions. It protects sensitive data stored on endpoint devices and ensures that even if a device is lost, stolen, or compromised, the encrypted data remains unreadable without the proper decryption key, reducing the risk of data breaches. Strong data security allows companies to work efficiently by eliminating risks related to endpoint management, compliance with regulations, remote working, and reputation. For more: Top 10 Data Loss Prevention or DLP Software
Here are several key benefits that are offered by endpoint encryption:
1. Improved compliance
Many regulations and data protection laws, such as GDPR and HIPAA, require organizations to implement measures to protect confidential data. Endpoint encryption helps organizations comply with these regulations by safeguarding data at rest on endpoint devices.
2. Secure remote work
With the rise of remote work, endpoint encryption becomes even more critical. Encrypting data on laptops and other remote devices ensures that sensitive information remains protected, regardless of where employees work. Device control software is widely used together with encryption and security tools to avoid risks that remote work poses.
3. Ease of management
Many endpoint encryption solutions come with centralized management capabilities, allowing IT administrators to enforce encryption policies, manage encryption keys, and monitor the security status of endpoint devices from a central console. This simplifies the deployment and management of encryption across an organization’s endpoint infrastructure. For more: Top 10 Endpoint Management Software in 2024
4. Stronger credibility and trust
Implementing strong security measures, such as endpoint encryption, enhances an organization’s trustworthiness and reputation. Customers, partners, and stakeholders are more likely to trust an organization that demonstrates a commitment to protecting sensitive data.
What is endpoint encryption?
Endpoint encryption contributes to endpoint security or endpoint protection by protecting data stored on endpoints, such as laptops, desktop computers, smartphones, and tablets. It involves encrypting data at rest, meaning the data is encrypted when it’s stored on the endpoint device’s storage media (such as hard drives, solid-state drives, or USBs). This encryption ensures that even if an unauthorized user gains physical access to the device or its storage media or intercepts data involving processes (messaging, file transfer, etc.), they won’t be able to manipulate or access data without the encryption key.
How does endpoint encryption work?
Endpoint encryption typically works by converting plaintext data into ciphertext using encryption algorithms and keys. Only authorized users with the correct decryption key or credentials can access the encrypted data, ensuring confidentiality and preventing unauthorized access or data breaches.
The 2 types of endpoint encryption
Both types of endpoint encryption provide protection against unauthorized access to sensitive data stored on endpoint devices, but they differ in terms of scope and granularity of protection. Organizations often deploy a combination of these encryption techniques based on their security requirements and compliance needs. Below are the two types of endpoint encryption:
1. Full-disk encryption (FDE)
Full Disk Encryption encrypts the entire storage volume of the endpoint device. This means that all data stored on the device, including the operating system, applications, and user files, is encrypted. FDE ensures comprehensive protection against unauthorized access to data, as everything on the disk is encrypted. Examples of FDE solutions include BitLocker (for Windows) and FileVault (for macOS).
2. File-encryption
Unlike full disk encryption, which encrypts the entire storage volume, file and folder encryption selectively encrypts specific files or folders. Users can choose which files or folders to encrypt, allowing for more granular control over data protection. This type of encryption is often used when users need to protect specific sensitive files or folders while leaving other data unencrypted. Examples of file and folder encryption solutions include VeraCrypt and AxCrypt.
Removable media encryption
Removable media like USBs, HDDs, and SD cards are encrypted for protection. For example, USB blocking software offers management and encryption features to control access and data transfers involving USBs.
Why is endpoint encryption important?
The use of endpoint encryption helps secure stored data on endpoints and provides additional security against data theft. Protecting confidential data demands a security strategy, and endpoint encryption is part of it.
Common encryption algorithms
Several common encryption algorithms are used in endpoint encryption solutions. Some of these algorithms include:
- Advanced Encryption Standard (AES): AES is a widely adopted symmetric encryption algorithm used for securing sensitive data. It supports key lengths of 128, 192, or 256 bits and is known for its efficiency and strong security.
- Triple Data Encryption Standard (3DES): 3DES is a symmetric encryption algorithm based on the Data Encryption Standard (DES). It applies the DES algorithm three times to each data block, enhancing security compared to the original DES.
- RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm commonly used for securing communications and generating digital signatures. It relies on the mathematical properties of large prime numbers for encryption and decryption.
- Elliptic Curve Cryptography (ECC): ECC is an asymmetric encryption algorithm that offers strong security with shorter key lengths compared to traditional algorithms like RSA. It is well-suited for resource-constrained environments, such as mobile devices.
- Blowfish: Blowfish is a symmetric encryption algorithm designed to be fast and efficient while providing strong security. It supports variable key lengths and is often used in applications where speed and flexibility are essential.
- Twofish: Twofish is a symmetric encryption algorithm developed as a candidate for the AES standard. Although it wasn’t selected as the AES algorithm, Twofish remains a popular choice for encryption due to its security and performance.
How does endpoint encryption contribute to endpoint security solutions?
Endpoint protection solutions include multiple and different functionalities to mitigate and avoid security deficiencies. Against more complex attacks on endpoints, endpoint security solutions deploy effective tools and incorporate them. Endpoint encryption contributes to endpoint security solutions by strengthening access control rules, complying with regulatory data security rules, and increasing the overall security of the network.

Top 3 challenges & best practices for endpoint encryption
Implementing endpoint encryption comes with its own set of challenges, but there are also best practices to address these challenges effectively. Here are the top three challenges and corresponding best practices for endpoint encryption:
Challenges
- User acceptance and training: One of the primary challenges with endpoint encryption is ensuring user acceptance and providing adequate training. Users may resist encryption due to perceived complexity or inconvenience, leading to non-compliance or circumvention of security policies.
- Performance impact: Encryption and decryption processes can sometimes introduce performance overhead, especially on older or resource-constrained endpoint devices. This performance impact may affect user experience and productivity, particularly for tasks involving large volumes of data.
- Key management: Effective key management is crucial for endpoint encryption to ensure secure storage and distribution of encryption keys. Managing encryption keys securely and ensuring their availability when needed can be complex, especially in large-scale deployments with diverse endpoint environments.
Best practices
- User education and awareness: Provide comprehensive training and awareness programs to educate users about the importance of endpoint encryption and how to use encryption tools effectively. Emphasize the benefits of encryption for data security and privacy, and address any concerns or misconceptions users may have.
- Performance optimization: Choose encryption algorithms and settings carefully to minimize performance impact while still providing adequate security. Consider factors such as hardware capabilities, workload characteristics, and encryption strength when configuring encryption solutions. Additionally, regularly monitor endpoint performance to identify and address any performance bottlenecks proactively.
- Robust key management practices: Implement robust key management practices to ensure the secure generation, storage, distribution, and rotation of encryption keys. Use centralized key management solutions where possible to streamline key management processes and enforce consistent policies across the organization. Regularly audit key management processes to identify and address any vulnerabilities or compliance issues.
FAQ
1. What is the difference between data in motion and data at rest?
The main difference between data in motion and data at rest lies in their state and activity: data in motion is actively being transmitted between endpoints, while data at rest is stored on storage devices or media without active transmission. Both states of data require appropriate security measures to protect against unauthorized access, interception, or tampering, with encryption being a common security measure for both data in motion and data at rest.
2. How are encryption keys generated?
Encryption keys are generated using various cryptographic algorithms and random number generators. The process of generating encryption keys typically involves the following steps:
Random number generation (RNG): The first step in key generation is to obtain random data that will serve as the basis for the encryption key. This randomness is essential to ensuring that the resulting key is unpredictable and resistant to cryptographic attacks. Random number generators (RNGs) are used to produce random data, often by measuring physical phenomena such as atmospheric noise or electronic noise.
Key length determination: The length of the encryption key is an important factor in determining its strength and resistance to brute-force attacks. Longer keys generally provide greater security but may also require more computational resources for encryption and decryption. The desired key length is chosen based on the security requirements of the encryption scheme and the capabilities of the cryptographic algorithm being used.
Key derivation: In some cases, the random data generated by the RNG may be used directly as the encryption key. However, in many encryption schemes, the raw random data is processed further to derive a final encryption key. This may involve applying cryptographic functions such as hashing or key derivation functions (KDFs) to transform the raw data into a suitable key format.
Key management: Once the encryption key is generated, it needs to be managed securely to prevent unauthorized access or disclosure. This includes storing the key securely, distributing it only to authorized parties, and rotating or replacing keys periodically to maintain security. Key management systems and protocols are used to facilitate these tasks and ensure that encryption keys are handled securely throughout their lifecycle.
Further reading
- Top 10 Hexnode Alternatives Based on 10,800+ Reviews
- Top 10 Device Control Software: Review-based Analysis
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
External Links
- 1. “2023 Data Breach Investigations Report”. Verizon. Accessed: 25/March/2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.