Top 9 Endpoint Protection Software with 2024 Prices


With the rise of hybrid and remote working, keeping work devices secure outside of the network area has become more important. IT teams need reliable security solutions that can prevent data breaches, which can lead to reputational losses and legal fees.
The term endpoint includes not just gadgets but all exit points of data. E-mails, storage devices such as USBs and HDDs, computers, mobile devices including smartphones, tablets, and smart watches, and more generally, IoT devices capable of sending and receiving data are examples of endpoints. This article lays out endpoint protection software by analyzing the top 10 endpoint protection software.
Top endpoint protection software comparison
Table 1. Number of reviews, average rating, and price
| Endpoint protection software | # of reviews* | Rating* | Price** |
|---|---|---|---|
| Trellix Endpoint Security (ENS) | 3,591 | 4.3 | n/a |
| Symantec Endpoint Security Complete | 3,177 | 4.4 | n/a |
| Sophos Intercept X: Next-Gen Endpoint | 2,298 | 4.7 | n/a |
| Microsoft Defender for Endpoint | 2,006 | 4.4 | Depends on numerous factors such as the buyer’s current ownership
of Microsoft products
|
| SentinelOne Singularity Platform Enterprise | 1,809 | 4.8 | n/a |
| ThreatDown Endpoint Protection | 1,613 | 4.6 | $767 |
| WeBroot Endpoint Protection | 1,001 | 4.3 | $150 |
| CylanceEndpoint by BlackBerry | 866 | 4.6 | n/a |
| FortiClient | 831 | 4.4 | n/a |
* Based on the total number of reviews and average ratings (on a 5-point scale) from Gartner, G2, Capterra, and TrustRadius software review platforms as of March 13, 2024.
** Other licensing terms, such as the minimum quantity of licenses needed, are not taken into account; features and prices are in accordance with the selected tiers/packages:
The price for ThreatDown Endpoint Protection Ultimate (with mobile security add-on) is for 5 devices annually. The price for WeBroot Endpoint Protection is for 5 devices and an annual subscription.
Table 2. Additional features
| Endpoint protection software | Data obfuscation | File shadowing | Sandboxing |
|---|---|---|---|
| Trellix Endpoint Security (ENS) | ✅ | ❌ | ✅ |
| Symantec Endpoint Security Complete | ✅ | ✅ | ✅ |
| Sophos Intercept X: Next-Gen Endpoint | ✅ | ✅ | ✅ |
| Microsoft Defender for Endpoint | ✅ | ✅ | integrated |
| SentinelOne Singularity Platform Enterprise | integrated | ✅ | integrated |
| ThreatDown Endpoint Protection | ❌ | ✅ | ✅ |
| WeBroot Endpoint Protection | ❌ | ❌ | ❌ |
| CylanceEndpoint by BlackBerry | ❌ | ✅ | ✅ |
| FortiClient | integrated | ❌ | ✅ |
Notes
- The table was created from publicly available and verifiable data.
To present an objective assessment of vendors, we took into account verifiable information from the public, like the number of reviews and user ratings on software review portals.
Vendor selection criteria
- Number of reviews: We included vendors with more than 100 total user reviews.
- Average rating: Above 4/5 rating on average across all software review platforms.
Common features and minimum requirements of endpoint protection software
We selected the vendors that deliver antivirus, firewall, intrusion detection and prevention system (IDPS), endpoint detection and response (EDR), web protection, email security, device control, data encryption, and central management console solutions.
For more: Main components of endpoint protection solutions
Differentiating features of endpoint protection software
Below are some additional features that a group of selected endpoint security solutions offers or integrates with.
- Data obfuscation: Also called data masking, data obfuscation makes sensitive data indiscernible to unauthorized users and endpoints while authorized users can still read it. This helps prevent vulnerable data, such as personal information (PI), from emanating.
- File shadowing: This feature allows to store data that is uploaded, transferred, written, or, more generally, interacted with at a point in time by endpoints. The volume of data that is duplicated in return helps to collect information about user behavior.
- Sandboxing: Sandboxing lets IT professionals run and test applications in an isolated environment so that resources stay unaffected and safe. Sandboxing regarding endpoint protection software helps to point security holes by testing and mimicking potential endpoint behavior.
Top 10 endpoint protection software analyzed
This section provides a user-reviewed product analysis with a focus on endpoint protection software solutions from sites such as G2, Gartner, Capterra, and TrustRadius. Pros and cons from user reviews are only chosen if several users bring up the same issue.
1. Trellix Endpoint Security (ENS)
Trellix provides data, network, and email security to its clients, in addition to extended endpoint detection and security (XDR). The CEO of the company at present is Bryan Palma, who serves as COO and president of BlackBerry.
Pros
- Integration: Reviewers claim the product is well integrated with 3rd party applications.1
Cons
- Utilization of system resources: Though the software offers comprehensive endpoint protection, it is found to be resource intensive by multiple reviewers.2

Source: Gartner.3
2. Symantec Endpoint Security Complete
Broadcom, Inc. is the owner of the Symantec brand, which offers a variety of hardware and software options. Cybersecurity products for server and endpoint security are available under the Symantec brand.
Pros
- Firewall & scalability: Reviewers are content with the product’s firewall capabilities, such that they claim network security is intact. Also, the software is found to be easy to scale up based on the number of users.4
Cons
- Utilization of system resources: Despite providing thorough endpoint protection, the program is found to be resource-intensive by several reviewers. 5
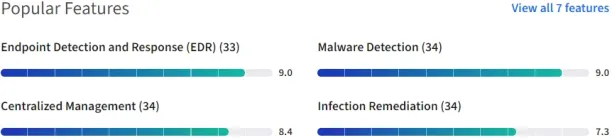
Source: TrustRadius.6
3. Sophos Intercept X: Next-Gen Endpoint
Sophos Intercept X is a Santa Fe-based product from Line-Securesoft that focuses on endpoint security and threat intelligence.
Pros
- Web protection: Most of the reviewers praise the software’s web protection capabilities.7
Cons
- Training: Multiple user reviews mention that the software asks for a steep learning curve.8
Source: G2.9
4. Microsoft Defender for Endpoint
Microsoft was founded in 1975 by Bill Gates and Paul Allen in New Mexico, United States. Applications like Microsoft Azure and Microsoft Purview, as well as hardware like HoloLens, are produced by the technology collaboration.
Pros
- EDR & deployment: The cloud-based deployment of Microsoft Defender for Endpoint and its EDR capabilities have been appreciated by many reviewers.10
Cons
- Reporting: The reporting feature is found to be uncustomizable and confusing by some reviewers.11
Source: G2.12
5. SentinelOne Singularity Platform Enterprise
SentinelOne was founded in 2013 in California, United States. The cofounder and CEO of the company is Tomer Weingarten. The company has products directed at endpoint security solutions in its portfolio.
Pros
- Behavior based analytics: This feature has been praised by multiple reviewers.13
Cons
- False positives: Many reviewers dislike the occurrence of false positives.14
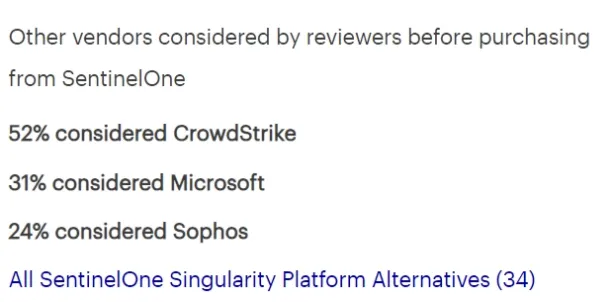
Source: Gartner.15
6. ThreatDown Endpoint Protection
Malwarebytes established TreatDown, a brand of IT security solutions. It provides endpoint security-focused IT security solutions.
Pros
- Ease of use: Most of the users find the software easy to implement.16
Cons
- Customer support: Multiple reviewers mention that support could be better because it takes time to get a response from it.17
Source: G2.18
7. WeBroot Endpoint Protection
Webroot was founded in 2007. It produces security solutions for endpoints and e-mails, as well as DNS protection.
Pros
- Utilization of system resources: The program is claimed to be found lightweight in comparison to other products in the market.19
Cons
- User experience: Widgets on the management console are claimed to lack reliability.20
Source: G2.21
8.CylanceEndpoint by BlackBerry
Cylance Inc. was established in California, United States, and was later acquired by mobile phone producer BlackBerry. The company offers its customers cybersecurity solutions.
Pros
- Antivirus (AV) system: The antivirus functionality of the software has been found satisfactory by multiple reviewers.22
Cons
- Policy management: The configuration and deployment of policies are found to be cumbersome for multiple reviewers.23
Source: Gartner.24
9.FortiClient by Fortinet
Fortinet was founded in 2002 by brothers Ken Xie and Michael Xie in California, United States. The company delivers its customers IT security solutions focused on network and endpoint protection.
Pros
- Compatibility and integration: The program is claimed to offer good functionality with other operating systems and with other applications found in the Fortinet portfolio.25
Cons
- Updates: Multiple reviewers mention that updates can upset the workflow.26
Main components of endpoint protection solutions
Endpoint protection software consists of the below listed components aimed at providing security for endpoint devices. These components work together to detect, prevent, and remediate various types of cyber threats. Here are the main components of endpoint protection software:
- Antivirus: This component scans files and processes on endpoint devices for known malware signatures or behavioral patterns indicative of malicious activity. It aims to detect and remove viruses, worms, Trojans, ransomware, and other types of malware.
- Firewall: A firewall monitors and controls incoming and outgoing network traffic based on predetermined security rules. It helps prevent unauthorized access to the endpoint device and blocks potentially malicious network connections.
- Intrusion detection and prevention system (IDPS): IDPS monitors network traffic and system activities for signs of suspicious or malicious behavior. It can detect and block intrusion attempts.
- Endpoint detection and response (EDR): EDR provides real-time monitoring, threat detection, and incident response capabilities on endpoint devices. It detects advanced threats, conducts behavioral analysis, and facilitates investigation and remediation of security incidents.
- Web protection: Web protection components block access to malicious or inappropriate websites and URLs, protecting endpoint devices from web-based threats such as phishing attacks, drive-by downloads, and malicious scripts.
- Email security: Email security features scan incoming and outgoing emails for malware, phishing attempts, and other email-based threats. They may include anti-spam, anti-phishing, and attachment scanning capabilities.
- Device control: Device control functionality enables administrators to manage and control the use of peripheral devices (e.g., USB drives, external hard drives) connected to endpoint devices. It helps prevent data leakage and the spread of malware through removable media.
- Data encryption: Encryption features protect sensitive data stored on endpoint devices by encrypting it to prevent unauthorized access in case of theft or loss. USBs, as one of the most common storage devices, are widely encrypted.
- Policy management: Policies help secure endpoints by making sure endpoints are used in alignment with predefined rules. These rules together constitute policies, which control endpoints, users, and their activities. For example, device control policy is implemented to confirm devices are used in compliance.
- Central management console: A central management console provides administrators with a unified interface for configuring, monitoring, and managing endpoint protection policies across the organization’s network.
How do we test the best endpoint protection software?
Testing the best endpoint protection software involves a comprehensive evaluation process to ensure that it meets your organization’s security requirements and effectively protects against various threats. Here are some of the important steps to follow:
- Define requirements: Begin by clearly defining your organization’s security requirements, considering factors such as the number of endpoints, types of devices, operating systems, network infrastructure, compliance standards, and specific threats you need protection against.
- Research: Conduct thorough research on available endpoint protection solutions. Consider factors such as reputation, vendor credibility, features, scalability, performance, ease of use, and customer reviews.
- Create test plan: Develop a detailed test plan outlining the evaluation criteria, testing methodologies, scenarios, and metrics. Include both functional and non-functional requirements in your plan.
- Installation and configuration: Install the endpoint protection software in a test environment that mirrors your production environment. Configure the software according to your organization’s requirements and security policies.
- Test functionality: Evaluate the software’s core functionality by performing various tests on the main components of endpoint protection software laid above.
- Usability testing: Assess the software’s user interface, ease of installation, configuration, and management. Evaluate the availability and effectiveness of documentation, support resources, and training materials.
- Compatibility testing: Verify that the endpoint protection software is compatible with different operating systems, applications, and hardware configurations commonly used within your organization.
- Integration testing: Test the software’s integration with other security tools, such as SIEM (Security Information and Event Management) systems, threat intelligence feeds, and incident response platforms.
- Security and compliance testing: Evaluate the software’s ability to meet regulatory compliance requirements relevant to your industry, such as GDPR, HIPAA, PCI DSS, and SOX.
- Real-world testing: Conduct real-world simulations or use cases to evaluate how the software performs in actual threat scenarios, such as targeted attacks, zero-day exploits, and advanced persistent threats.
- Gather feedback: Solicit feedback from key stakeholders, including IT administrators, security analysts, and end-users, to gather insights into their experience with the endpoint protection software.
- Benchmarking: Compare the performance, features, and effectiveness of the tested endpoint protection software against industry benchmarks and competitors.
- Decision making: Based on the evaluation results and feedback, make an informed decision on selecting the best endpoint protection software that aligns with your organization’s security needs, budget, and strategic objectives.
FAQ
1. What is the difference between endpoint security and a firewall?
Endpoint security focuses on protecting individual devices from security threats, while a firewall focuses on controlling and monitoring network traffic to protect the network infrastructure as a whole. Both are essential components of a layered cybersecurity strategy designed to provide comprehensive protection against a wide range of threats.
2. Are endpoint security and antivirus the same?
Antivirus software is an important component of endpoint security. Endpoint security software encompasses a broader set of tools and techniques aimed at protecting endpoints from a wider range of threats.
Antivirus software uses signature-based and specifically focuses on identifying, preventing, and removing malicious software (such as viruses, worms, trojans, etc.) from individual devices (endpoints), such as computers, laptops, smartphones, and tablets.
Endpoint security, on the other hand, is a broader term that encompasses a range of security measures designed to protect endpoints within a network from various types of security threats. For more: Endpoint Security vs. Antivirus: What To Choose?
3. What is the difference between endpoint management and endpoint security?
The two approaches differ in purpose and activities. While the software market for endpoint management and security does offer overlapping features, endpoint management software and endpoint security are different, as portrayed below.
Purpose
Endpoint management: Focus on managing endpoints by making use of administrative tools such that all endpoints are working intact in a secure environment.
Endpoint security: Focus on the security of endpoints such that endpoints are adversely affected by malicious software, insider threats, and data leakage.
Activities
Endpoint management: Endpoint management involves tasks such as software deployment, patch management, inventory tracking, remote troubleshooting, configuration management, and policy enforcement. For more: Top 10 Endpoint Management Software Based on 12K+ Reviews
Endpoint security: Endpoint security involves implementing various security measures and controls, including antivirus software, firewalls, intrusion detection/prevention systems, encryption, endpoint detection and response (EDR), and security policies. For more: main components of enpoint protection solutions
Overlapping features
Endpoint management software may include endpoint security software as inherently or excluding. Because endpoint management aims at managing endpoints and their sustainability in terms of their security, most endpoint management solutions on the market offer joint products.
External Links
- 1. “Industry best “. Capterra. Accessed: 15/March/2024.
- 2. “Good Endpoint Protection “. Gartner. Accessed: 15/March/2024.
- 3. “Solid Contender For A Comprehensive Endpoint Security Suite Across Multiple OS’s.”. Gartner. Accessed: 15/March/2024.
- 4. “Solid Contender For A Comprehensive Endpoint Security Suite Across Multiple OS’s.”. TrustRadius. Accessed: 15/March/2024.
- 5. “Symantec Endpoint Security review”. Capterra. Accessed: 15/March/2024.
- 6. “Popular Features”. TrustRadius. Accessed: 15/March/2024.
- 7. “For your enterprise, endpoints and everything in between”. G2. Accessed: 15/March/2024.
- 8. “Experience with Sophos Intercept X”. G2. Accessed: 15/March/2024.
- 9. “Sophos Intercept X: Next-Gen Endpoint Media”. G2. Accessed: 15/March/2024.
- 10. “A complete guide for vulnerability management”. G2. Accessed: 15/March/2024.
- 11. “My experience about the Microsoft defender”. G2. Accessed: 15/March/2024.
- 12. “Microsoft Defender for Endpoint Media”. G2. Accessed: 15/March/2024.
- 13. “Protect Platform From Attackers”. Gartner. Accessed: 15/March/2024.
- 14. “Long time user of Sentinel One”. G2. Accessed: 15/March/2024.
- 15. “Top SentinelOne Singularity Platform Alternatives”. Gartner. Accessed: 15/March/2024.
- 16. “Malwarebytes Endpoint Protection”. Gartner. Accessed: 15/March/2024.
- 17. “ThreatDown REVIEW”. G2. Accessed: 15/March/2024.
- 18. “ThreatDown Media”. G2. Accessed: 15/March/2024.
- 19. “Great Endpoint Security”. G2. Accessed: 15/March/2024.
- 20. “So far the experience of the product has been favorable to our team and clients”. G2. Accessed: 15/March/2024.
- 21. “Webroot Business Endpoint Protection Media”. G2. Accessed: 15/March/2024.
- 22. “Technical Account Manager For An MSSP’s Opinion Of Cylance”. Gartner. Accessed: 15/March/2024.
- 23. “This product will save your backside!”. Capterra. Accessed: 15/March/2024.
- 24. “Product Screenshots”. Gartner. Accessed: 15/March/2024.
- 25. “FortiEDR – Comprehensive EDR Solution For Endpoints”. Gartner. Accessed: 15/March/2024.
- 26. “My Experience With FortiEDR”. Gartner. Accessed: 15/March/2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.