We analyzed insights from industry leaders, IoT experts, and real-world case studies to provide a structured approach to IoT implementation and best practices.
Successful IoT deployment requires a clear strategy, starting with defining business objectives, selecting the right technology stack, ensuring security, and integrating IoT with enterprise systems.
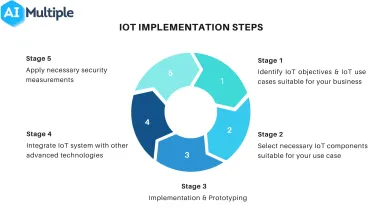
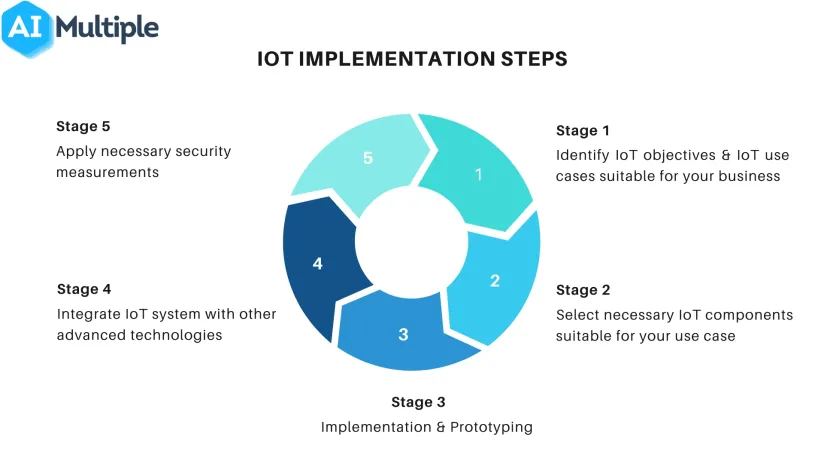
IoT Implementation Steps
Even if your business expectations on IoT projects are high and you can afford the technical tools and human resources, focusing on proofs of concept (PoCs), sandboxes, human resource alignment, pilots, and narrowing use cases for IoT deployments is advisable. This will enable you to learn from your mistakes and be encouraged by success.
1. Identify IoT objectives & IoT use cases suitable for your business
As with other digital transformation initiatives, IoT implementation starts with identifying project objectives. It would be best if you determined what your organization wants to achieve through IoT technology. Each organization has different needs; some may aim to decrease operational costs, while others target customer experience.
It may be hard to identify use cases that suit your business needs. IoT consulting companies help businesses understand IoT technology. You can also check out our list of IoT applications based on company objectives and create a roadmap to achieve your business goals.
2. Select the necessary IoT components suitable for your use case
Hardware and software selection is a critical decision during implementation. IoT projects involve various tools, and businesses need to be careful about these systems’ connectivity and interoperability. Required components in IoT implementation include
- sensors to collect data such as weight, volume, temperature, humidity, pressure, etc.
- edge gateways to serve as a network entry point for devices and sensors talking to cloud services
- communication protocols for machine to machine (M2M) communication like SigFox Zigbee, 6LoWPAN, etc.
- IoT platforms to transmit information from a variety of hardware to the cloud and manage devices
- cloud data management and analytics software to transform generated data into insight.
3. Implementation & Prototyping
IoT requires a team that contains a mix of experts across IT and operations to work together. It would be best if you started implementation by building an IoT team that meets the requirements of selected use cases. Skills you may need during the IoT journey are listed below.
However, this depends on the exact project. Many companies rely on turnkey IoT solutions and only need to oversee solution implementation, which requires significantly fewer resources.
- Industrial & embedded systems design
- Electrical & mechanical knowledge
- Back-end & front-end development
- General technical expertise
A team with these skills can build IoT devices and implement the network; however, you need to enhance your team with data talent to make collected data useful. Skills your IoT team may rely on after implementation are listed below:
- Information systems expert to handle data storage
- Data scientist to analyze the data gathered
- Statistician to assist in data analysis and quality control.
4. If necessary: Integrate IoT system with other advanced technologies
After sensors collect and store data, businesses can introduce new technologies, such as analytics, machine learning, and edge computing, to their IoT infrastructure.
For instance, cognitive IoT refers to the use of machine learning in conjunction with data generated by connected IoT devices and the actions those devices can perform.
The growth of unstructured data collected from IoT devices exceeds that of structured data. Cognitive IoT technologies aim to understand and learn using both structured and unstructured data for training and continuous improvement.
5. Apply necessary security measurements
Data security and privacy are top concerns for businesses. IoT implementation security breaches are common, and businesses need to inform their data security officer about IoT projects to ensure that data governance best practices are integrated into the project.
If necessary, GDPR compliance should be considered. In addition, IoT security solutions can be integrated to minimize security breaches. Endpoint security, communication protocols, access control, encryption, and fraud management are some measures you can take to enhance data security and privacy.
Explore IoT security and IoT cybersecurity in more detail.
Challenges during IoT implementation
1. Compatibility & Longevity
IoT infrastructure encompasses a range of tools, sensors, and devices, and each vendor competes to establish itself as the standard. A successful implementation requires the integration of IoT components with existing systems.
Some compatibility challenges include non-unified cloud services, a lack of standardized M2M protocols, and diversity in firmware and operating systems among IoT devices.
For example, ZigBee, Z-Wave, Wi-Fi, Bluetooth, and Bluetooth Low Energy (BTLE) protocols are transport mechanisms between devices and hubs. This variety presents challenges in implementation and necessitates the deployment of additional hardware and software when connecting devices.
Learn more about IoT communication protocols.
2. Security issues
Although IoT implementation projects offer various business opportunities, adding new devices to your network increases the risk of cyberattacks. Studies show that 57% of IoT devices are vulnerable to cybersecurity attacks, making cybersecurity the biggest barrier to IoT implementation.
3. Data storage issues
Once you deploy IoT systems, your database grows exponentially. Organizations need high-capacity and high-speed storage and advanced memory processing technologies to capture IoT data and perform analytics.
4. Power management of IoT devices
Although IoT implementation devices operate via AC power, industrial IoT (IIoT) involves devices located in extreme conditions, and they often use their battery as their primary power source. Companies should track when the battery of an IoT device needs to be recharged or replaced. Finding devices that conserve or produce power when not in use enables businesses to design a sustainable IoT system. Battery replacements can be overwhelming, especially when a device is placed in a difficult place to access.
5. Unstructured data processing that requires data cleaning
IoT sensors collect unstructured data that is difficult to use for analysis. Collected data may contain anomalies if the sensors’ environment or systems are unstable. It is important to identify such data quality issues to improve decision-making.
Learn more about data cleaning.
6. Analytics challenges
IoT analytics are applications that help analyze data collected by IoT sensors to make informed, data-driven decisions. IoT analytics has specific challenges, but common analytics challenges also apply to IoT implementation.
Interested in learning more about IoT implementation and other key technological advances that are changing how we do business? Check out our research for a wide range of IoT/AI-related topics.

Comments
Your email address will not be published. All fields are required.