Top 5 NinjaOne Alternatives in 2024 Based on 4.5K+ Reviews
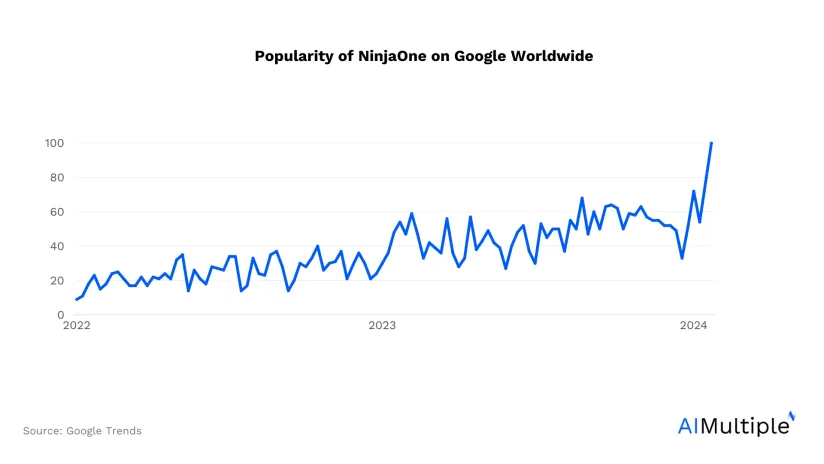
NinjaOne, before rebranding in late October 2021 as NinjaRMM, is a software company that offers software solutions for endpoint management and security, as well as remote access and monitoring.
This article offers a comparison of the top alternative vendors of NinjaOne based on pricing, features, and reviews. It also evaluates the capabilities of NinjaOne in terms of the key features of endpoint management and remote monitoring tools.
Top alternatives to NinjaOne
This section compares the top endpoint management tools with similar capabilities to NinjaOne.
Table 1. Alternatives to NinjaOne
| Software product | # of reviews* | Rating* | Price** | Pricing driver*** | On-prem deployment |
|---|---|---|---|---|---|
| Endpoint Central ManageEngine | 2,480 | 4.5 | $ 3,945 | per-user license | ✅ |
| NinjaOne Endpoint Management | 1,391 | 4.8 | n/a | flexible | ❌ |
| Atera IT Management | 892 | 4.6 | $ 2,868 | per-technician | ❌ |
| Kaseya VSA | 619 | 4.0 | $ 3,945 | flexible | ❌ |
| N-Able N-Central RMM | 309 | 4.0 | n/a | flexible | ❌ |
| Action1 | 252 | 4.9 | n/a | n/a | ❌ |
* Based on the total number of reviews and average ratings (on a 5-point scale) from Gartner, G2, Capterra, and TrustRadius software review platforms as of March 5, 2024.
** Other licensing terms, such as the minimum quantity of licenses needed, are not taken into account.
*** Features and prices are in accordance with the selected tiers/packages as follows: Security (cloud-based) for Endpoint Central ManageEngine; Master for Atera IT Management.
Vendor selection criteria
To present an objective assessment of vendors, we took into account easily verifiable information from the public, like the number of reviews and user ratings on software review portals. Pros and cons from user reviews are only chosen if several users bring up the same issue.
- Number of reviews: We included the vendors with more than 300 total user reviews.
- Average rating: Above 4/5 rating on average across all software review platforms.
- Price: Endpoint management software products vary in price, and publicly available prices of products are added to the table. Potential users can compare products according to their price and pricing drivers.
- Pricing driver: The price of products depends on multiple aspects, such as minimum licensing or admin user quantity, device quantity, or domain quantity. Businesses can choose between pricing driver options in accordance with the quantity and admin user.
- Deployment: All selected vendors offer cloud-native software, which cuts costs on data storage and hardware.
- Common features (minimum requirements): We selected the vendors that deliver patch management, asset management, endpoint security, integration with 3rd party applications, and application deployment.
NinjaOne overview
The company was founded in 2013. Though it was founded in Austin, Texas, NinjaOne now has headquarters in Berlin, Sydney, and Tampa. At present, NinjaOne claims to offer a range of features, including remote monitoring and management services, endpoint management, and patch management.
Selection from the offered products by NinjaOne
- Endpoint management: A bundle of multiple tools aimed at monitoring endpoints, including IoT devices, virtual machines, and other aspects listed below.
- Remote control: NinjaOne offers two options: remote access via 3rd party application integration such as TeamViewer or through its own devised remote desktop protocol (RDP) tool and gateway
- Patch management: Automation and scheduling on patches claim to help avoid zero days. Visibility on who denied or approved which patches. Finally, a cumulative report on the patch is offered.
- Endpoint backup: The endpoint backup tool aims to encrypt and backup data to cloud storage. Users can customize along with their backup choices.
- Endpoint security: Role based access controls, drive encryption and its monitoring, and management of 3rd party endpoint security integrations.
NinjaOne’s shortcomings
Reviewers have identified the following flaws * with NinjaOne:
* Only issues that have been raised multiple times are chosen to be list objects.
1. Limited reporting features
Multiple reviewers find the reporting tool insufficient and superficial because they claim it lacks customization features.
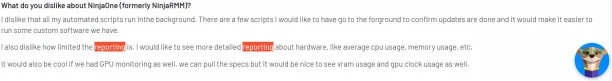
Source: G2.1
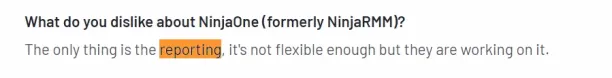
Source: G2.2
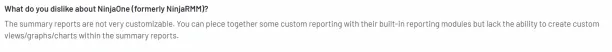
Source: G2.3
2. Unproductive user interface (UI)
Multiple reviewers mentioned that the user interface regarding the dashboard platform needs improvement because the present setting makes navigation complicated.

Source: Gartner.4
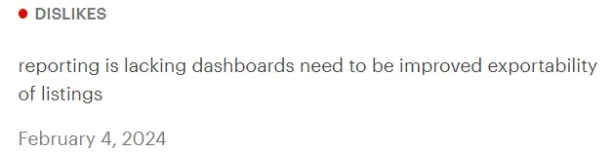
Source: Gartner.5
3. Inadequate mobile device management (MDM) features (regarding the beta version)
Multiple reviewers remark that MDM has room for improvement.

Source: TrustRadius.6

Source: Capterra.7
Detailed analysis of the alternatives
Below listed 5 alternatives for NinjaOne are ordered ascending to the total review numbers described in Table 1.
1. Endpoint Central ManageEngine
ManageEngine offers IT management solutions such as cloud, security, IT operation solutions.
Pros
- Mobile device management (MDM) features: Multiple reviewers expressed satisfaction with MDM features.
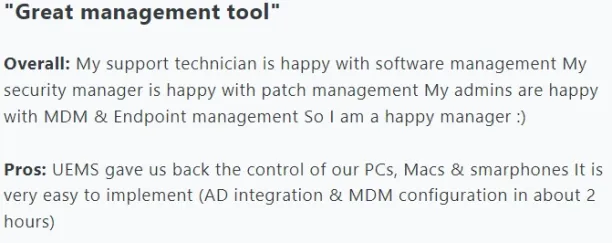
Source: Capterra.8
Cons
- Ease of use: User menu is found to be complicated when navigating.
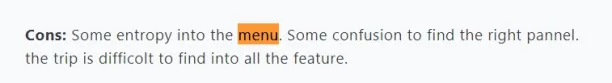
Source: Capterra.9
2. Atera IT Management
Atera launched its first product in 2016. The company is based in Tel Aviv and offers security management solutions, including IT automation, patch management, and remote access.
Pros
- Ease of use: Users find the onboarding and navigation around menu items displayed on the platform easy.
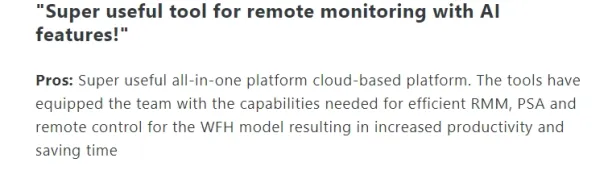
Source: Capterra.10
Cons
- Integration with 3rd party applications: Some user reviewers express hardship with integrating 3rd party applications.

Source: G2.11
3. Kaseya VSA
Kaseya has been delivering IT management solutions since 2000. The company provides its customers with IT security software, service automation, ticket management, and quote management.
Pros
- Ease of use: Reviewers like the easy setting of Kaseya VSA.
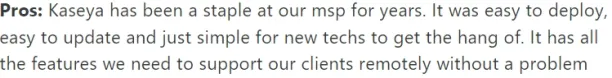
Source: Capterra.12
Cons
- Billing: Monthly billing is troublesome for many reviewers. Numbers do not align and lead to complications.

Source: G2.13
4. N-Able N-Central RMM
N-Able delivers its customers IT management software. In 2021, N-Able parted ways with the IT management company SolarWinds.
Pros
- Customization: Reviewers like customization features on the monitoring tool.

Source: Capterra.14
Cons
- Support: Many users claim the support team falls behind because it is slow and hard to reach for.
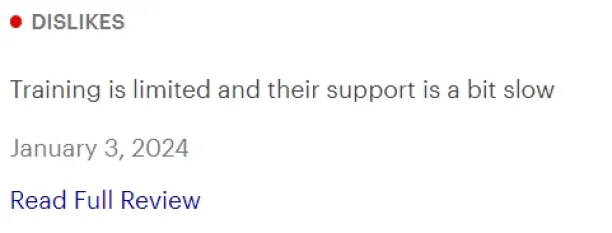
Source: Gartner.15
5. Action1
Action1 is a software solutions company that offers its customers security and automation tools under its platform. The company also offers compliance assistance for businesses.
Pros
- Windows OS compatibility: Many users are satisfied with the product’s alignment with the Windows operating system.
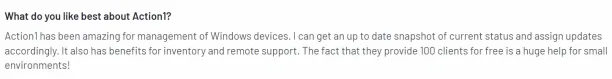
Source: G2.16
Cons
- Remote access: Multiplier reviewers claim that they are not able to transfer files when in the remote mode.
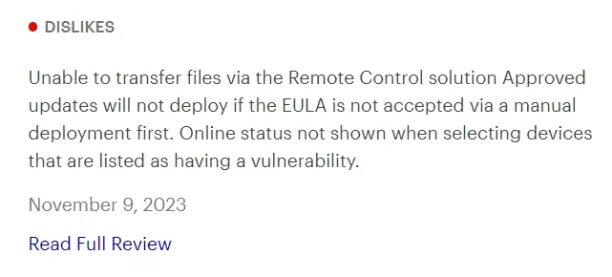
Source: Gartner.17
Challenges and practices for 3 endpoint management key features
By addressing these challenges and following best practices, organizations can establish effective endpoint management.
1. Patch management
Patch management is a critical aspect of IT management, ensuring that software vulnerabilities are identified and patched in a timely manner to minimize security risks. Here are some common challenges and best practices associated with patch management tools:
Challenges
- Complexity of IT environments: Managing patches across diverse IT environments with a variety of operating systems, software applications, and devices can be challenging.
- Patch prioritization: Determining which patches are most critical and need to be applied immediately can be difficult, especially when dealing with a large number of patches.
- Patch deployment: Ensuring patches are deployed promptly without disrupting business operations or causing downtime requires careful planning and coordination.
- Vendor dependencies: Relying on third-party vendors to release patches in a timely manner, especially for legacy software or systems, can be problematic.
- Resource constraints: Limited resources, including time, manpower, and budget, can hinder effective patch management efforts.
Best practices
- Automate patch management processes: Utilize patch management tools that automate the process of scanning for, downloading, testing, and deploying patches to streamline workflows and minimize human error.
- Establish patch management policies: Develop clear policies and procedures outlining patch management practices, including patch prioritization, testing methodologies, and deployment schedules.
- Centralized patch management console: Use a centralized patch management console to monitor patch status, track compliance, and generate reports across the organization.
- Patch rollback mechanism: Implement mechanisms to rollback patches quickly in case of compatibility issues or unexpected system behavior.
- Regular vulnerability scanning: Conduct regular vulnerability scans to identify security gaps and prioritize patching efforts based on the severity of vulnerabilities.
2. Asset management
Challenges
- Asset discovery and inventory: Identifying all assets within the organization’s infrastructure can be challenging, especially in large and complex environments where assets may be distributed across multiple locations.
- Integration with IT systems: Integrating asset management tools with existing IT systems, such as help desk software, procurement systems, and network monitoring tools, can be complex and may require customizations or third-party integrations.
- License compliance: Ensuring compliance with software licensing agreements and avoiding under- or over-licensing can be challenging without accurate visibility into software usage and license entitlements.
- Asset security: Protecting asset data and ensuring that sensitive information, such as serial numbers, license keys, and configuration details, is secure from unauthorized access or breaches is essential for maintaining data integrity and confidentiality.
- Asset lifecycle management: Managing the entire lifecycle of assets, from procurement to disposal, including tracking warranties, maintenance contracts, and end-of-life processes, can be complex and time-consuming.
Best practices
- Establish asset management policies: Develop clear policies and procedures for asset management, including asset acquisition, tracking, disposal, and security, to ensure consistency and compliance across the organization.
- Automate asset discovery: Utilize automated discovery tools to scan the network and identify all connected devices and software assets, including endpoints, servers, virtual machines, and cloud resources.
- Asset tagging and labeling: Implement a standardized asset tagging and labeling system to uniquely identify and track assets throughout their lifecycle, making it easier to locate and manage assets.
- Software license management: Implement software license management processes to track software installations, usage, and license entitlements to ensure compliance with licensing agreements and optimize software costs.
- Security controls: Implement security controls, such as access controls, encryption, and regular security assessments, to protect asset data from unauthorized access, breaches, and tampering.
3. Application deployment
Application deployment tools are essential for IT management as they streamline the process of deploying, updating, and managing software applications across an organization’s infrastructure.
Challenges
- Compatibility issues: Ensuring that applications are compatible with different operating systems, hardware configurations, and software dependencies can be challenging, leading to deployment failures or compatibility issues.
- Deployment automation: Configuring and automating the deployment process for various applications and environments while maintaining consistency and reliability can be challenging, especially in heterogeneous environments.
- Rollback mechanism: Implementing a reliable rollback mechanism to revert to the previous version of an application in case of deployment failures or issues is essential but can be difficult to implement effectively.
- Dependency management: Managing dependencies between applications and ensuring that all required libraries, frameworks, and components are installed and configured correctly during deployment can be challenging, especially for complex applications with numerous dependencies.
- Security concerns: Ensuring that the deployment process is secure and that sensitive data, credentials, and configuration settings are protected from unauthorized access or tampering is essential but can be challenging to implement effectively.
Best practices
- Standardized deployment process: Define and document a standardized deployment process, including deployment procedures, configurations, and best practices, to ensure consistency and reliability across deployments.
- Automated testing: Implement automated testing, including unit tests, integration tests, and acceptance tests, as part of the deployment process to detect and prevent issues early in the deployment lifecycle.
- Continuous Integration/Continuous Deployment (CI/CD): Implement CI/CD pipelines to automate the build, test, and deployment process, enabling faster and more frequent releases with reduced manual intervention and errors.
- Configuration management: Use configuration management tools to automate the configuration of servers and applications during deployment, ensuring consistency and compliance with desired configurations.
- Monitoring and logging: Implement monitoring and logging mechanisms to track the progress of deployments, detect issues or failures, and troubleshoot problems quickly, ensuring visibility and accountability throughout the deployment process.
FAQ
Is it reasonable to be concerned about endpoint data being stored in a cloud provided by endpoint management software solutions?
When subscribing to cloud-based endpoint management software, you may want to look at public statements disclosed by the provider. As an example, see Action1’s statement on data security.18You should consider a few key factors before allowing third-party providers to store your data in the cloud. Here are some of the key considerations:
Security: Storing sensitive endpoint data in the cloud raises concerns about security. You should ensure that the cloud provider follows industry-standard security practices and employs encryption to protect data both in transit and at rest.
Compliance: Depending on the type of data being stored, there may be regulatory requirements or compliance standards that need to be met. You should verify that the endpoint management software solution and its cloud storage meet these requirements.
Privacy: Endpoints may contain sensitive information about users, organizations, or clients. It’s essential to understand how the endpoint management software solution handles and protects this data to safeguard privacy.
Reliability: Cloud-based storage solutions are subject to downtime and outages. You should evaluate the reliability and uptime guarantees provided by the endpoint management software vendor to ensure uninterrupted access to your endpoint data.
Data ownership: Clarify the terms of service regarding data ownership. Ensure that you retain ownership of your endpoint data and that the endpoint management software vendor does not claim any rights to use or access your data beyond what is necessary for providing the service.
Further reading
- Top 10 Hexnode Alternatives Based on 10,800+ Reviews
- Top 10 RMM Software: Analysis From 7,700+ Reviews
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. “Easy to learn, easy deployments!”. G2. Accessed: 5/March/2024.
- 2. “Best MSP partner easy automation and endpoint management”. G2. Accessed: 5/March/2024.
- 3. “The next generation RMM”. G2. Accessed: 5/March/2024.
- 4. “Easy Configuration And Multitude Of Options To Protect Your Devices”. Gartner. Accessed: 5/March/2024.
- 5. “Patch Management Done Easy”. Gartner. Accessed: 5/March/2024.
- 6. “Growing and Adapting with NinjaOne”. TrustRadius. Accessed: 5/March/2024.
- 7. “Great Product – Continuing to add features”. Capterra. Accessed: 5/March/2024.
- 8. “Great management tool”. Capterra. Accessed: 5/March/2024.
- 9. “Good Job ME”. Capterra. Accessed: 5/March/2024.
- 10. “Atera has been the perfect tool for my startup MSP”. Capterra. Accessed: 5/March/2024.
- 11. “Atera has been the perfect tool for my startup MSP”. G2. Accessed: 5/March/2024.
- 12. “Kaseya VSA is easy to use and learn”. Capterra. Accessed: 5/March/2024.
- 13. “Product is decent, bill is suspect.”. G2. Accessed: 5/March/2024.
- 14. “Powerful RMM Tool, Reporting Can Be Improved”. Capterra. Accessed: 5/March/2024.
- 15. “Great BCDR Solution”. Gartner. Accessed: 5/March/2024.
- 16. “Action1 is awesome.”. G2. Accessed: 5/March/2024.
- 17. “Fantastic, Simple To Use, Comprehensive RMM Solution On Its Way To Being Perfect.”. Gartner. Accessed: 5/March/2024.
- 18. “Security”. Action1. Accessed: 6/March/2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on


Comments
Your email address will not be published. All fields are required.