Top 6 Data Security Best Practices for Organizations in 2024
Increasing and evolving insider threats and data privacy regulations such as GDPR and CCPA oblige businesses to pay greater attention to the security of their data. Data breaches are costly and harm business reputations. A proactive approach combined with insider threat management (ITM) software can be formulated by companies to prevent and manage data threats. Here are some of the best practices for data privacy and security for organizations:
Assess and classify data
First, assess your business data comprehensively to understand what types of data you have. Then, classify your data according to its sensitivity and the value it adds to your business. This would enable organizations to determine data to be retained and secured. Discarding non-productive data is a good practice especially if it contains sensitive data such as personally identifiable information (PII).
Develop a data usage policy
After classification, you should develop different data access and usage policies for different classes of data. This involves determining:
- Who has access to data and for how long?
- Who can modify the data?
Restricting data usage and deactivating when a task is completed can enable you to ensure that only the people who should see and change your business data do so. In this respect, the principle of least privilege is a sound strategy that involves giving users the minimum level of permission needed to perform their jobs.
Monitor sensitive data
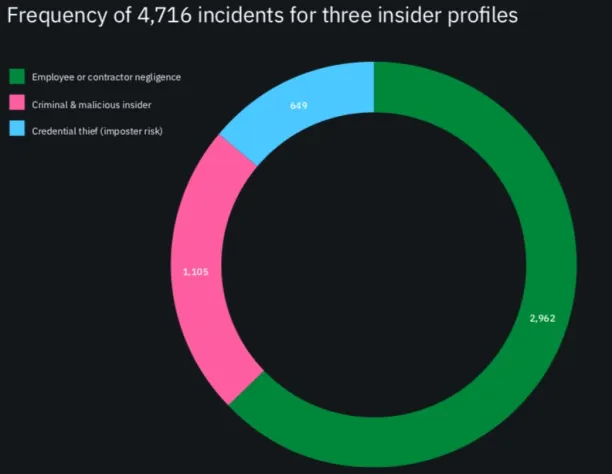
Classifying and limiting usage of sensitive data may not be adequate to ensure safety. According to the 2020 Cost of Insider Threats report by IBM and Ponemon Institute, the frequency of insider data breach incidents per company is tripled. According to the report,
- 60% of incidents were due to negligent and inadvertent employees
- 25% were caused by malicious insiders
- 15% involved stolen credentials of privileged users
Monitoring the users and their actions on sensitive data can enable your organization to detect and prevent incidents.
Leverage privacy-enhancing technologies
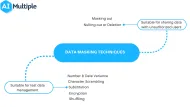
Privacy-enhancing technologies (PETs) enable organizations to utilize their data without risking privacy and safety. PETs include:
- Cryptographic methods such as homomorphic encryption and zero-knowledge proofs. These methods prevent unauthorized access to sensitive data and increase data usability without privacy risks.
- Data masking techniques such as data anonymization. Data masking refers to a set of practices of modifying sensitive information within a dataset without changing structural properties.
- AI-based privacy methods such as federated learning and synthetic data. Generating synthetic versions of real data with machine learning algorithms can enable organizations to store and share sensitive information without privacy risks.
Be prepared for incidents
Whether due to human error, system failure, or malicious attacks, data breaches can occur in every organization. Therefore, it is also important to be prepared and develop an incidence response plan in addition to prevention methods. A plan should involve procedures, division of tasks, and methods of communication both internally and externally.
Running simulations of data compromise is a good way to test the effectiveness of an incidence response plan. Since security threats are constant and evolving, periodically conducted simulations can enable organizations to stay up-to-date and well-practiced against them.
Train your employees to increase data privacy awareness
As mentioned above, one of the most common reasons for data breaches is employee error. Thus, establishing a culture of data security is vital for organizations that take data security seriously. Employees should know and follow security practices from the beginning regardless of their job since anyone can cause a data breach.
Regular training on password security, phishing emails, malware, and physical security can help companies to minimize the risk of a data breach due to employee negligence.
For more on data privacy technologies
There are numerous technologies designed to enhance data privacy and system securities, feel free to scroll down our data-driven lists of privacy enhancing technologies:
If you have questions on data privacy or privacy-enhancing technologies, feel free to contact us:

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.