Cryptography is the science of combining and reading a message only through a key, created by using an algorithm called a password or a cryptosystem. In order for a cryptosystem to be considered secure, it should be impossible to unlock the message without a key.
See what quantum cryptography is, how it works, and showcase the top vendors in the market.
What is quantum encryption?
Quantum encryption, also called quantum cryptography, in a nutshell, uses the principles of quantum mechanics to both:
- Encrypt data and transmit it in a way that cannot be hacked,
- Decrypt messages encrypted with quantum or classical cryptography.
Quantum encryption enables the two parties to communicate with a random common bit sequence that only they can know. This bit sequence is used to encrypt or decrypt messages.
An important feature of quantum cryptography is the ability of two communicating parties to detect the presence of a third party trying to capture the key.
The third-party who secretly listens to the key has to somehow measure it, and this measurement causes quantum entanglement to break. For any changes in the state of the photon make it impossible to generate a secure key and communication will be stopped.
Quantum cryptography is used only to generate and distribute the key, not to move data. The generated key is then used for encryption and decryption in any encryption algorithm.
How does quantum encryption work?
Quantum encryption uses a method called quantum key distribution (QKD). The purpose of this system is to send the information transmitted from one point to another without any reading process.
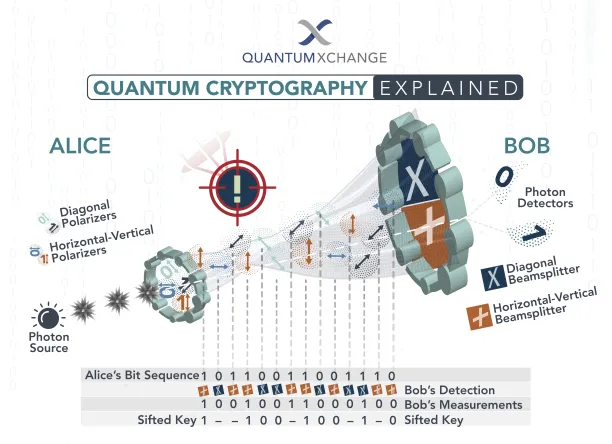
QKD uses a series of photons to transmit data from one location to another over fiber optic cables:
- The transmitter sends photons through a polarizer, which gives them one of four possible polarizations: vertical, horizontal, 45 degrees right, or 45 degrees left.
- When the photons arrive, the receiving end uses two beam splitters to estimate the polarization of each photon. Type of the beam splitter to use for each photon is not known by the receiver, so it needs to do a randomized estimate.
- After the transmitter sends all the information, the receiver tells the transmitter which beam splitter was used for each of the photons.
- Transmitter compares the information sequence including the type of splitters used and the matching sequence in both ends becomes the key.
If a third party tries to read the sequence, the photon’s state will change and the change is detected in endpoints.
Why is it important?
Thanks to quantum computing’s market size increase1 it is getting more advanced to soon replace the classical encryption approaches.
Recently, there have been developments in quantum computing with the investments of tech giants and military technology companies. Quantum computing is a technology that has the potential to solve problems in minutes that take years for classical computers to solve.
Hence, while decoding the encryption systems used today can take years even for supercomputers, it can be simple math for quantum computing.
Although quantum computing is not ready yet, encryption systems must be ready in advance. For more information about quantum computing, feel free to visit our article.
Critical for network security
An increasing data communication rate creates an increasing need for network security. Data security can become one of the top priority issues as more data means greater risk. In particular, one of the primary challenges of military technologies is the maintenance of secure communication.
Quantum technology brings a whole new perspective to solve the problem of secure communication, making it impossible even for quantum computers to decrypt certain messages.
Post-quantum encryption vs. quantum encryption
Both post-quantum encryption and quantum encryption are terms that aim to minimize or even make it impossible for communication to be hacked by quantum computers.
Post-quantum encryption aims to produce algorithms that can not be hacked by quantum computers. Post-quantum encryption is the development of existing security algorithms using mathematical methods and making them resistant to quantum computing. However, it does not guarantee the impossibility of decryption, it just reduces the possibility.
Quantum encryption refers to the use of quantum mechanics principles to send secure messages. Unlike mathematical encryption, quantum encryption is impossible to hack. The main difference is that post-quantum encryption is a mathematical method, while quantum encryption aims to encrypt using the nature of quantum physics.
Algorithms produced for post-quantum encryption are candidates to provide more secure communication in the short term. Quantum encryption is a more secure approach, however quantum computing needs to become widespread and more mature for quantum encryption.
What are the top quantum cryptography companies?
IdQuantique
A Switzerland based company provides quantum secure security solutions for the protection of transmitted data by upgrading existing network encryption products with QKD.
Qrypt
Qrypt is a New York-based startup that has its own cryptographic solution. The company claims that its encryption solution is capable of securing enterprises and private information in the present and in the future.
Single Quantum
The Netherlands based company provides solutions for the detection of photons in the receiver end with a high precision.
Post-Quantum
The company provides solutions for protection against quantum threats and offers commercial and government solutions. Post-Quantum has solutions like encryption algorithms and cybersecurity solutions.
Crypto Quantique
Crypto Quantique’s technology products, platforms, and services provide end-to-end security throughout IoT networks with quantum-driven cybersecurity. The company claims to have quantum-driven security on a chip that can generate multiple cryptographic keys that don’t need to be stored and used independently on multiple applications.
CryptoNext Security
France based startup aims to provide cryptographic standards that can make IT infrastructures secure against quantum computers. Recently, KETS Quantum and Cryptonext Security announced a partnership to build quantum-safe solutions.
Quantum Resistant Ledger
QRL is a cryptocurrency ledger that is designed from the outset to be resistant to both classical and quantum computing attacks.
For more on quantum computing
To learn more about quantum computing, read:
- Future of Quantum Computing
- Cloud Quantum Computing & Top cloud QC vendors
- Quantum Entanglement: What it is & Why it is important
Finally, if you believe your business would benefit from leveraging a quantum computing platform, we have a data-driven list of vendors.
We will help you choose the best one based on your specifications:


Comments
Your email address will not be published. All fields are required.