FireMon Alternatives in 2024 based on 1,000+ Reviews
Digital companies that deal with network security rules, each with a unique set of guidelines, might get overwhelmed while managing hundreds of configurations to mitigate risks and threats.
FireMon Security Manager is a network security policy management (NSPM) provider that can help companies govern, control, and customize network security policies, however, user reviews highlight that the software may be cumbersome in ensuring efficient network mapping, reporting structure, and subject-oriented customer service.
This article compares the top 4 FireMon alternatives and summarizes each vendor, including their market presence, key specifications, and user reviews.
Top 4 FireMon Security Manager alternatives for network security policy management (NSPM)
Table 1: Feature based comparison of FireMon Security Manager alternatives
| Vendors | Integration & platforms | Price | Mobile support | OS support | Firewall management | DLP |
|---|---|---|---|---|---|---|
| Tufin | AWS, GCP, Microsoft Azure, Red Hat, Check Point, Cisco | Usage-based | N/A | Rocky Linux 8 | ✅ | ✅ |
| FireMon Security Manager | IBM Rapid 7 AWS Azure | Configuration-based | N/A | Linux/Unix, CentOS 8 | ✅ | N/A |
| Microsoft System Center | N/A | Edition-based (Datacenter & Standard) | ✅ | N/A | ✅ | ❌ |
| AlgoSec | AWS Microsoft Azure VMware GCP | N/A | ✅ | CentOS 7 | ✅ | N/A |
| SolarWinds Network Configuration Manager | AWS Microsoft Azure GCP | The number of devices | N/A | Windows, Windows Server 2022 Base windows-server-2022-english-full-base-x86/x.x.x | ✅ | N/A |
Core features
Each vendor listed in the provided table offers compatibility with the specified features:
- Automated security policy management: Streamlines the process of securing networks by reducing manual overhead in managing complex network environments.
- Workload monitoring: Monitors the application, the data it generates, and the network resources supporting user-application interactions.
- Endpoint protection: Safeguarding endpoints, devices like laptops, smartphones, and tablets, enabling threat hunting and automated response actions.
- Support for hybrid environments: Maintaining a consistent security policy platform across all environments to streamline security operations.
- Compatibility with cloud platforms: Understanding and addressing the security challenges presented by cloud environments.
Table 2: The market presence of the top 4 FireMon Security Manager alternatives
| Vendors | Total reviews* | Average rating* (5-point scale) |
|---|---|---|
| Tufin | 296 | 4.0 |
| FireMon Security Manager | 174 | 4.1 |
| Microsoft System Center | 762 | 4.1 |
| AlgoSec | 393 | 4.4 |
| SolarWinds Network Configuration Manager | 375 | 4.4 |
*Based on the total number of reviews and average ratings on Gartner, G2, PeerSpot, and TrustRadius software review platforms as of 01/09/2024.
Disclaimer: With FireMon Security Manager positioned at the top, other vendors are sorted by the total number of reviews in descending order.
Vendor selection criteria:
Given the abundance of network security policy management (NSPM) software, the list (above) is filtered down based on the vendor criteria listed below.
- Number of reviews: 100+ reviews on Gartner, G2, PeerSpot, and TrustRadius.
- Average rating: Above 4.0/5 on Gartner, G2, PeerSpot, and TrustRadius.
FireMon Security Manager
FireMon is a network security policy management (NSPM) solution by Palo Alto Networks that integrates firewall and policy management capabilities from on-premises networks to the cloud. FireMon was founded in 2004 and claims to have served 1,700+ businesses in 70 countries.1
Firemon Security Manager gives control and visibility across organizations’ IT environments, enabling users to streamline security policies, and security risks, meet legal and compliance requirements, and mitigate policy-related risks.
Read more: Automated security risk assessment.
FireMon Security Manager offers integrations that allow users to improve and integrate policy management with technologies such as:
- SD-WAN (software-defined wide area network)
- SASE (secure access service edge)
- XDR (extended detection and response)
- SOAR (security orchestration automation and response)
Pros
Automated rule reviews: Users liked the fact that they could conduct automated rule reviews using policy optimizer tickets.2
Firewall analyzer: Users claim that FireMon has a simple firewall analyzer and provides an efficient risk assessment and risk management for all allowed firewall rules.3
Visibility of rules: Some users appreciate the fact that they can effectively see the redundant rules and the logical rule list.4
Cons
Network mapping: Reviews show that the map feature is confusing and useless.5
Reporting structure: Users say that the reports provide unnecessary information that needs to be filtered out.6
Query interfaces: Some users express that query interfaces for more advanced users may not usually include simple query conversion.7
Subject-oriented customer service: Some users suggest that FireMon Security Manager’s service might be improved by having more subject matter experts for their product.8
User Ratings
- Gartner: 4.0/5 with 2 reviews
- G2: 4.4/5 with 7 reviews
- PeerSpot: 4.3/5 with 52 reviews
- TrustRadius: 7.1/10 with 113 reviews
Top 4 Firemon Security Manager alternatives
1. Tufin
Tufin is a network security solution that aims to streamline the operation of complicated networks and hybrid cloud network infrastructure by leveraging its network security policy management, security risk assessment, and network security automation technologies.
Tufin serves over 2,900 customers including IBM, a Fortune 500 tech company, and is ranked among the top 50 security software in 2023 by G2.9Tufin offers network security solutions for businesses with up to 10,000+ devices, other network components, and 200M+ routes.10
Key features of Tufin include the following:
Automated security policy management: Operates network control checkpoints on both internal networks and in the cloud systems, enabling network security professionals to create customized policies to improve the security posture of their company (e.g. setting up a password policy for specific company resources for certain stakeholders according to their job roles).
Firewall management: Sets firewall rules and policies, tracks changes, and monitors compliance logs for on-premises and cloud firewalls.
Network segmentation: Uses granular zones, microsegmentation, and/or fully automated zero trust network access (ZTNA) technologies to segment the network into finer-grained parts.
Read more: Top 10 microsegmentation tools,
Network audit: Provides oversight of AI audit efforts while ensuring regulatory compliance.
Vulnerability-based change automation (VCA): Integrates with vulnerability scanners and routinely scans for vulnerabilities before implementing new cybersecurity policies or giving additional privileges to them.
Read more: Vulnerability testing
Data compliance: Evaluates the network configuration by enabling data encryption, role-based access control (RBAC), and software-defined micro-perimeter compliance standards for network components (e.g. firewalls, routers, switches, and web-based platforms).
Figure: Tufin’s products and services
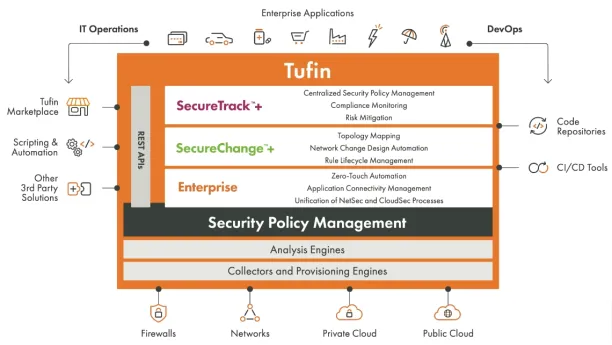
Source: Tufin11
Pros
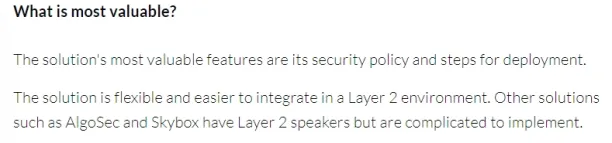
Security policy and deployment (Layer 2): Some users indicate that Tufin’s most useful features are its security policy and deployment procedures. They also state that Tufin is adaptable and simple to implement in a Layer 2 environment, other options, such as AlgoSec and Skybox, use Layer 2 speakers but are difficult to deploy.12
Firewall integrations: Users express that Tufin has a simple integration with firewalls such as Cisco, Fortinet/FortiManagers, etc.13
Firewall rules: Some users note that establishing firewall rules based on traffic monitoring is easy.14
Here is AIMultiple’s data-driven analysis of the top 10 firewall audit software.
Cons
Troubleshooting: Some users note that troubleshooting with Tufin is difficult, identifying and resolving issues with Tufin could be more straightforward.15
Layer 2 integrations: Some users suggest that integration for Layer 2 devices may be enhanced, as it involves manual programming.16
Topology management: Some users state that topology is difficult to manage when the network is large and diverse.17
User Ratings
- Gartner: 3.8/5 with 8 reviews
- G2: 4.4/5 with 95 reviews
- PeerSpot: 4.0/5 with 180 reviews
- TrustRadius: 7.1/10 with 13 reviews
Read more: Other popular Tufin competitors: AlgoSec.
2. Microsoft System Center
Microsoft System Center is a suite of IT management programs that includes network monitoring, software updates, and patches, endpoint security including anti-ransomware, data protection, and backup against cyberattacks.
Microsoft System Center is available in two versions: standard and datacenter. The datacenter plan includes data virtualization for private clouds, while the standard plan is intended for non-virtualized private cloud operations.
Pros
Installation: Users note that the installation process is fast.18
Usability: Users say that Microsoft SCCM allows them to effortlessly manage security devices and servers, such as application deployment, monthly patch updates, vulnerability management, and end-user device security.19
Monitoring and ticketing tools: Some users address that monitoring and ticketing tools are simple to handle.20
Cons
Price: Some reviewers find the solution expensive based on the services it provides.21
GUI: Some users claim that the graphical user interface (GUI) may be sluggish at times.22
HTML5 analyst portal: Some users indicate that the product does not have an HTML5 analyst portal; only a desktop console is accessible for analysts.23
User Ratings
- Gartner: 4.1/5 with 162 reviews
- G2: 4.1/5 with 584 reviews
- PeerSpot: 4.0/5 with 16 reviews
- TrustRadius: No information is available.
3. AlgoSec
AlgoSec is a network security policy management (NSPM) platform that assists companies in implementing network security management practices across on-premises, cloud, or hybrid environments.
AlgoSec improves security visibility by monitoring the network, incorporating firewall rules into business applications, and detecting compliance issues.
Pros
Automated risk analysis and prioritization: Users claim that AlgoSec effectively analyzes network data detects cyber threats and allows their IT teams to focus their attention on the most important issues.24
Network map and topology: Some users say that the overview of the network map and implementation of topology changes based on source, destination, and port is easy.25
Integrations: Some users indicate that AlgoSec is efficient in integrating firewalls, datacenter routers, and web proxies with a variety of network security devices.26
Cons
Reporting tools: Some security professionals believe that reporting systems should be more simple and accessible.27
User interface: Some users complain about the interface complexity of AlgoSec, noting that navigating the user interface can be difficult, particularly for new users.28
Integrations: While some users state that AlgoSec has efficient integrations, some users point out integration issues with certain technologies (Cisco FTD, Cisco Firepower).29
User Ratings
- Gartner: 4.3/5 with 64 reviews
- G2: 4.5/5 with 146 reviews
- PeerSpot: 4.4/5 with 173 reviews
- TrustRadius: 9/10 with 10 reviews
4. SolarWinds Network Configuration Manager
SolarWinds’ Network Configuration Manager (NCM) is an NSPM solution that enables users to keep track of and configure their network devices by scanning and identifying them to collect up-to-date data.
Pros
Topology mapper: Some users assert that the topology mapper function accurately shows the connectivity of your network devices (for example, recognizes when a laptop or hardware is disconnected or connected to the organization’s network).30
Configuration management: Some reviews indicate that the configuration management option on the console is useful.31
Network monitoring: Some users conclude that one of the most useful features of the solution was its capacity to track and monitor shifts in the configuration of devices on a network that are specific to the device or system.32
Read more: IoT monitoring.
Cons
Learning curve: Some users say that it requires experience to build up unique policy-based reports to assess compliance.33
Activity notifications: Some users assert that when they plan a task or perform another activity, sometimes they fail to receive reports, whether via SMS or email.34
AI security capabilities: Some customers would prefer to see more AI capabilities to add configurations by word rather than inputting instructions on the devices.35
User Ratings
- Gartner: 4.2/5 with 62 reviews
- G2: 4.5/5 with 32 reviews
- PeerSpot: 4.3/5 with 18 reviews
- TrustRadius: 8.8/10 with 263 reviews
For guidance on choosing the right tool or service, check out our data-driven lists of software-defined perimeter (SDP) software and zero trust networking software.
Further reading
- Top 10 Microsegmentation Tools
- Microsegmentation: What is it? Benefits & Challenges
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
External links
External Links
- 1. ”FireMon Company“. FireMon. 2023. Retrieved January 22, 2024.
- 2. ”FireMon Security Manager Reviews“. TrustRadius. February 25, 2023. Retrieved January 22, 2024.
- 3. ”FireMon Security Manager Reviews“. TrustRadius. March 1, 2022. Retrieved January 22, 2024.
- 4. ”FireMon Security Manager Reviews“. Gartner. January 7, 2021. Retrieved January 22, 2024.
- 5. ”FireMon Security Manager Reviews“. Gartner. January 7, 2021. Retrieved January 22, 2024.
- 6. ”FireMon Security Manager Reviews“. TrustRadius. October 19, 2022. Retrieved January 22, 2024.
- 7. ”FireMon Security Manager Reviews“. TrustRadius. October 19, 2022. Retrieved January 22, 2024.
- 8. ”FireMon Security Manager Reviews“. TrustRadius. March 21, 2023. Retrieved January 22, 2024.
- 9. ”SecureTrack+ Unlocks Clarity in Hybrid-Cloud Network Security“. Tufin. January 4. Retrieved January 22, 2023.
- 10. ”Network Security Policy Management“. Tufin. January 9. Retrieved January 22, 2023.
- 11. ”Network security orchestration“. Tufin. January 2024. Retrieved January 4, 2023.
- 12. ”Tufin Reviews“. PeerSpot. October 12, 2022. Retrieved January 9, 2024.
- 13. ”Tufin Reviews“. G2. October 27, 2022. Retrieved January 9, 2024.
- 14. ”Tufin Reviews“. G2. October 2, 2023. Retrieved January 22, 2024.
- 15. ”Tufin Reviews“. G2. September 20, 2023. Retrieved January 9, 2024.
- 16. ”Tufin Reviews“. PeerSpot. October 12, 2022. Retrieved January 9, 2024.
- 17. ”Tufin Reviews“. G2. December 26, 2022. Retrieved January 9, 2024.
- 18. ”Microsoft System Center Reviews“. G2. February 20, 2023. Retrieved January 22, 2024.
- 19. ”Microsoft System Center Reviews“. G2. June 22, 2023. Retrieved January 22, 2024.
- 20. ”Microsoft System Center Reviews“. G2. December 26, 2021. Retrieved January 22, 2024.
- 21. ”Microsoft System Center Reviews“. G2. July 24, 2022. Retrieved January 22, 2024.
- 22. ”Microsoft System Center Reviews“. G2. May 2, 2022. Retrieved January 22, 2024.
- 23. ”Microsoft System Center Reviews“. Gartner. April 15, 2022. Retrieved January 22, 2024.
- 24. ”AlgoSec Reviews“. G2. February 16, 2023. Retrieved January 22, 2024.
- 25. ”AlgoSec Reviews“. TrustRadius. November 3, 2021. Retrieved January 22, 2024.
- 26. ”AlgoSec Reviews“. G2. January 26, 2023. Retrieved January 22, 2024.
- 27. ”AlgoSec Reviews“. G2. September 25, 2023. Retrieved January 22, 2024.
- 28. ”AlgoSec Reviews“. G2. February 1, 2023. Retrieved January 22, 2024.
- 29. ”AlgoSec Reviews“. G2. May 18, 2022. Retrieved January 22, 2024.
- 30. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. February 10, 2023. Retrieved January 22, 2024.
- 31. ”SolarWinds Network Configuration Manager Reviews“. G2. January 6, 2023. Retrieved January 22, 2024.
- 32. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. January 6, 2023. Retrieved January 22, 2024.
- 33. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. April 20, 2023. Retrieved January 22, 2024.
- 34. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. January 6, 2023. Retrieved January 22, 2024.
- 35. ”SolarWinds Network Configuration Manager Reviews“. PeerSpot. April 19, 2023. Retrieved January 22, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.