As the CISO of an enterprise managing firewalls from multiple vendors, I have seen that a unified firewall management tool is essential to streamline configuration & ensure compliance and reduce the complexity & work load. I have compiled the top 11 solutions. Click the links to understand the rationale behind each selection:
- Tufin Orchestration Suite for firewall policy management orchestration
- Microsoft Azure Firewall Manager
- AWS Firewall Manager for businesses that rely mostly on AWS (i.e. no significant multi cloud or on-prem deployments)
- Cisco Secure Firewall Management Center
- Palo Alto Network Panorama for organizations relying only on Palo Alto firewalls
- Fortinet FortiManager
- Sophos Central
- Barracuda CloudGen Firewall Control Center
- Skybox Security Firewall Assurance
- Manage Engine Firewall Analyzer for log analysis and management
- FireMon Security Manager
- Titania Nipper for configuration assessment
See top firewall management tools based on their key features such as compliance and rule management, user reviews, and the key criteria for selecting the right tool including integrations:
Pricing calculator for firewall management tools
Top 11 firewall management software
Table 1. Technical capabilities comparison
| Product / Platform Name | SIEM Integration | Ticketing Tools Integration | Performance Management | VTM* | ZTNA** |
|---|---|---|---|---|---|
| Tufin Orchestration Suite | ✅ | ✅ | ✅ | ✅ | ✅ |
| Microsoft Azure Firewall Manager | ✅ | ❌ | ❌ | ✅ | ❌ |
| AWS Firewall Manager | ✅ | ✅ | ❌ | ❌ | ❌ |
| Cisco Secure Firewall Management Center | ✅ | ❌ | ❌ | ❌ | ❌ |
| Palo Alto Network Panorama | ✅ | ✅ | ❌ | ❌ | ❌ |
| Fortinet FortiManager | ✅ | ✅ | ✅ | ❌ | ✅ |
| Sophos Central | ✅ | ✅ | ❌ | ✅ | ✅ |
| Barracuda CloudGen Firewall Control Center | ✅ | ✅ | ❌ | ❌ | ❌ |
| Skybox Security Firewall Assurance | ✅ | ❌ | ❌ | ✅ | ❌ |
| Manage Engine Firewall Analyzer | ✅ | ✅ | ❌ | ❌ | ❌ |
| Titania Nipper | ✅ | ✅ | ❌ | ✅ | ✅ |
| FireMon Security Manager | ✅ | ✅ | ❌ | ❌ | ❌ |
*Vulnerability and threat management
**Zero trust network access
Table 2. Compliance-related capabilities comparison
| Product / Platform Name | Compliance Management | Change Management | Rule Management | Audit Management |
|---|---|---|---|---|
| Tufin Orchestration Suite | ✅ | ✅ | ✅ | ✅ |
| Microsoft Azure Firewall Manager | ✅ | ❌ | ✅ | ❌ |
| AWS Firewall Manager | ✅ | ❌ | ✅ | ✅ |
| Cisco Secure Firewall Management Center | ✅ | ✅ | ✅ | ❌ |
| Palo Alto Network Panorama | ❌ | ✅ | ✅ | ❌ |
| Fortinet FortiManager | ✅ | ✅ | ❌ | ✅ |
| Sophos Central | ✅ | ✅ | ❌ | ❌ |
| Barracuda CloudGen Firewall Control Center | ❌ | ✅ | ❌ | ✅ |
| Skybox Security Firewall Assurance | ✅ | ✅ | ✅ | ✅ |
| Manage Engine Firewall Analyzer | ✅ | ✅ | ✅ | ✅ |
| Titania Nipper | ✅ | ✅ | ❌ | ✅ |
| FireMon Security Manager | ✅ | ✅ | ✅ | ✅ |
Table 3. Market presence
| Software | User Rating* | # of employees** | Pricing*** |
|---|---|---|---|
| Tufin Orchestration Suite | 3.8 out of 100 reviews | 458 | N/A |
| Microsoft Azure Firewall Manager | 4.3 out of 21 reviews | 244,900 | $100 Monthly license fee for 1 device pack & 2 user with basic support |
| AWS Firewall Manager | 4.4 out of 48 reviews | 130,371 | $457 Monthly license fee for 1 device pack with 100 Config rule evaluations |
| Cisco Secure Firewall Management Center | 4.3 out of 24 reviews | 100,466 | N/A |
| Palo Alto Network Panorama | 4.5 out of 60 reviews | 16,348 | N/A |
| Fortinet FortiManager | 4.6 out of 238 reviews | N/A | |
| Sophos Central | 4.3 out of 81 reviews | 4,686 | N/A |
| Barracuda CloudGen Firewall Control Center | 4.4 out of 39 reviews | 2,198 | N/A |
| Skybox Security Firewall Assurance | 4.4 out of 4 reviews | 296 | N/A |
| Manage Engine Firewall Analyzer | 4.5 out of 141 reviews | 387 | $395 Monthly license fee for 1 device pack & 2 user within standard package |
| FireMon Security Manager | 4.1 out of 81 reviews | 231 | N/A |
| Titania Nipper | 4.4 out of 4 reviews | 90 | N/A |
*Based on data from B2B review leading platforms
**Based on data from LinkedIn
***Calculated based on the minimum price provided by the vendor for 730 hours usage and 2,500 GB process storage per month. N/A means that the vendor doesn’t publicly share its pricing.
Disclaimer: ❌ means that the AIMultiple team couldn’t identify public evidence about a specific feature.
Inclusion criteria:
- All vendors featured in this list employ over 200 individuals.
- Every tool provides compliance and policy management services in addition to other cyber security solutions.
- Not all firewall management tools are compatible with every firewall. For more information, check firewall integration.
Ranking: The companies are ranked based on the total of employees except for the sponsored products ranked at the top. Sponsored products can be identified by their links.
Analysis based on customer reviews

This section offers some relevant user reviews gathered from B2B review platforms like G2, TrustRadius, and Capterra. We analyzed the reviews and picked the ones relevant to the companies’ firewall management tools.
Tufin Orchestration Suite
Tufin encompasses features such as compliance management, change management, rule management, performance management, audit management, VTM, and ZTNA. These functionalities help to adherence to regulatory requirements, facilitate efficient policy changes, optimize network performance, provide auditing capabilities, and enable secure access and traffic management.
Figure 1. Compliance monitoring with Tufin
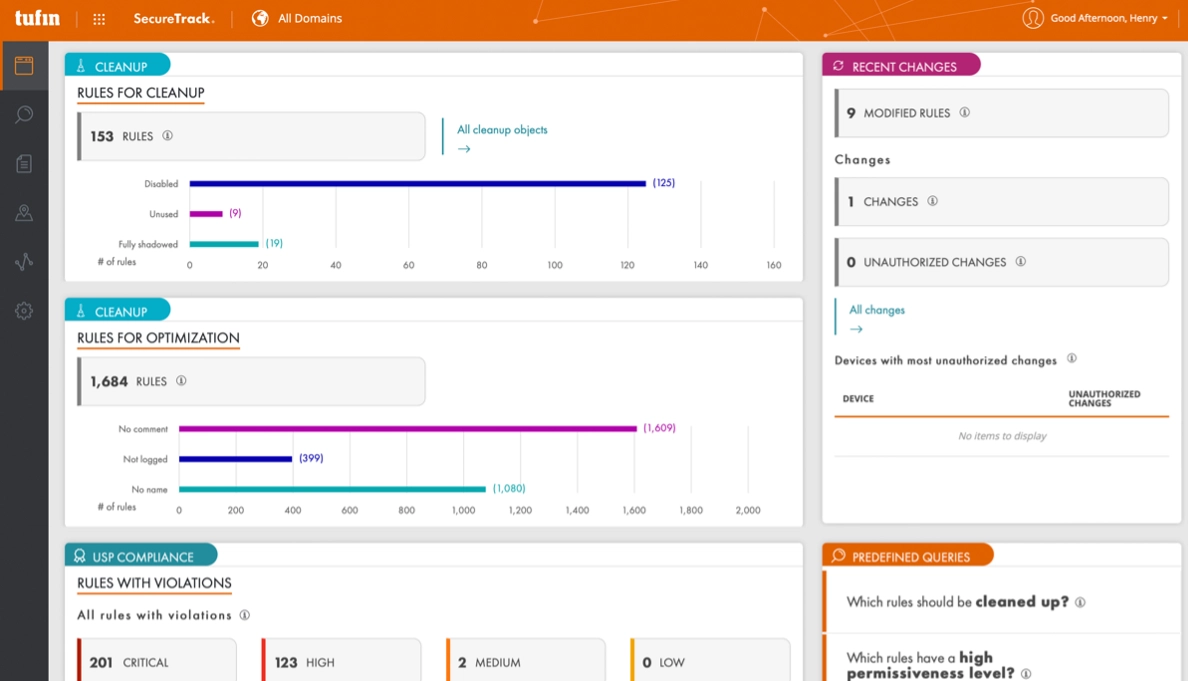
User Reviews
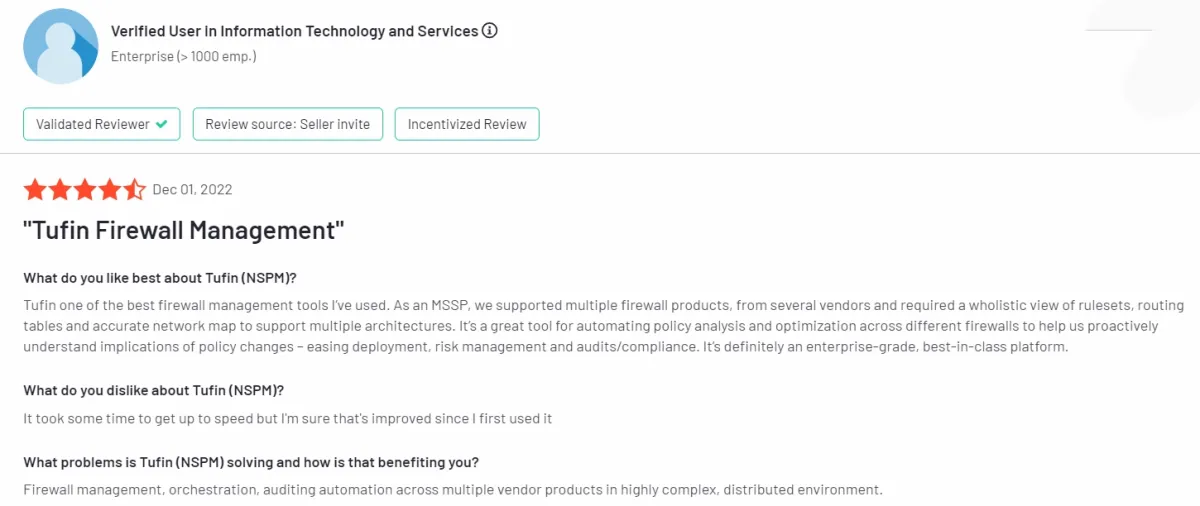
✅ Users appreciate Tufin’s holistic view of rulesets, routing tables, and network mapping, which aids in understanding the implications of policy changes, easing deployment, risk management, and audits/compliance.
✅ The platform is regarded as enterprise-grade and best-in-class, offering automation for policy analysis and optimization across different firewalls.
❌ Limitations are noted for EC2 Managed firewalls, with suggestions for enhancements in future versions1 .
Figure 2. A user review on Tufin Orchestration Suite
Microsoft Azure Firewall Manager
Microsoft Azure Firewall Manager, one of the firewall management tools, focus in compliance and rule management, and VTM, ensuring regulatory adherence, enforcing security policies, and mitigating cyber threats, but lacks features for performance, audit and change management, and ZTNA, crucial for optimizing system performance, conducting thorough security audits, managing operational changes, and enhancing secure remote access capabilities.
User Reviews
✅ Reviews appreciate the integration of the service with the platform’s other services and third-party security solutions, ensuring a robust security ecosystem.
❌ Some users feel that the dashboard interface could be improved for better usability and functionality.
❌Limited network address translation (NAT) functionality, with only one-way NATing available, is seen as restrictive by some users.
Figure 7. A user review on Microsoft Azure Firewall Manager
AWS Firewall Manager
Amazon Web Service (AWS) offers firewall management services focusing on compliance, rule management, audit management, and ZTNA, crucial for ensuring regulatory adherence, maintaining rule-based security policies, conducting audits, and enforcing strict access controls. However, AWS doesn’t directly provide features for change management, performance management, or VTM, which are essential for monitoring and optimizing operational changes, enhancing system performance, and managing network traffic routing efficiently.
User Reviews
✅ The ability of AWS Firewall Manager to create custom firewall rules tailored to specific application needs is appreciated.
❌ Some users find the cost structure of AWS Firewall Manager to be high compared to other products, suggesting a need for better cost management options.
❌ Users have reported occasional issues with response times and support availability, indicating room for improvement in performance and customer service.
Cisco Secure Firewall Management Center
Cisco’s managed firewall service offers essential capabilities like change management, compliance management, and rule management, crucial for maintaining security policies and regulatory adherence, but lacks features such as performance management, audit management, VTM, and ZTNA, which are vital for optimizing network performance, conducting thorough audits, and enhancing secure remote access capabilities.
User Reviews
✅ Users appreciate the centralized administration capability, making it easier to manage multiple firewall operations from a single interface.
❌ Users have expressed the need for improvement in the initial setup and switching from existing firewalls, which can be complex and time-consuming.
Palo Alto Network Panorama
Palo Alto Networks’ secure firewall management center primarily focuses on change and rule management, which is essential for maintaining optimized number of policies and controlling access. While lacking features like compliance, performance, and audit management, VTM and ZTNA are crucial for regulatory compliance, optimizing network performance, comprehensive auditing, and secure access management, respectively.
User Reviews
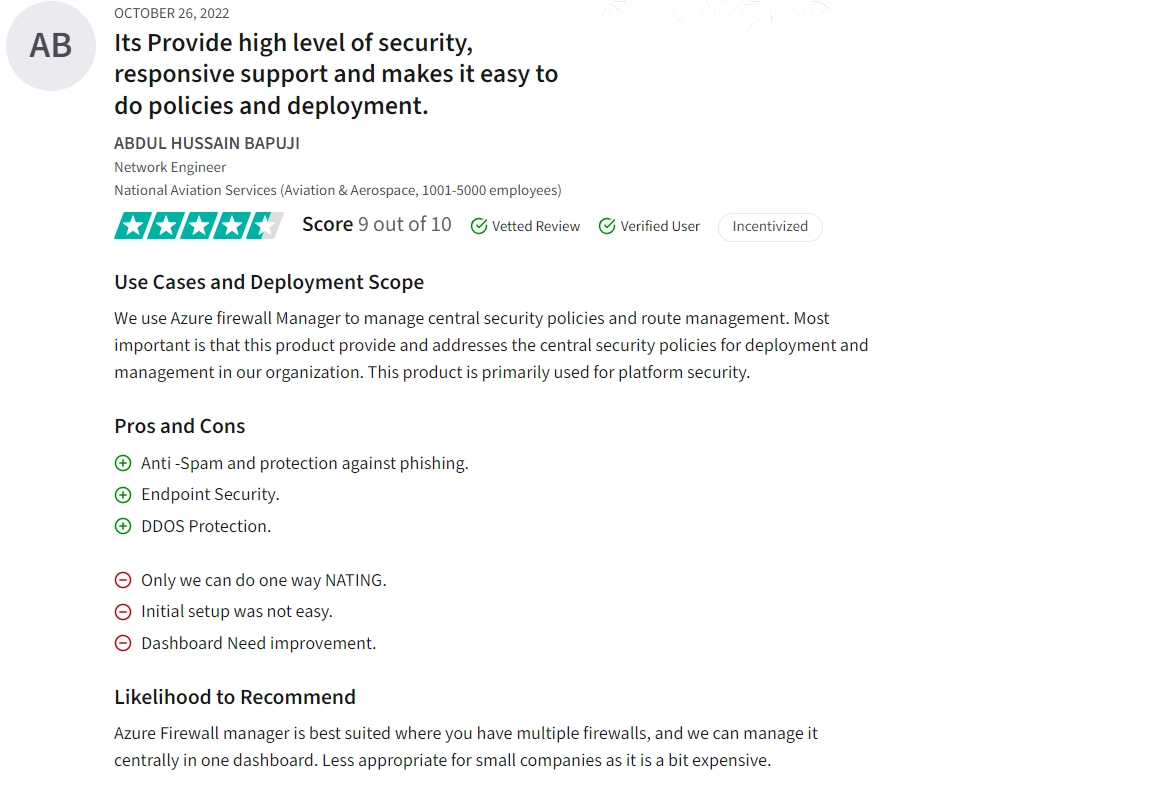
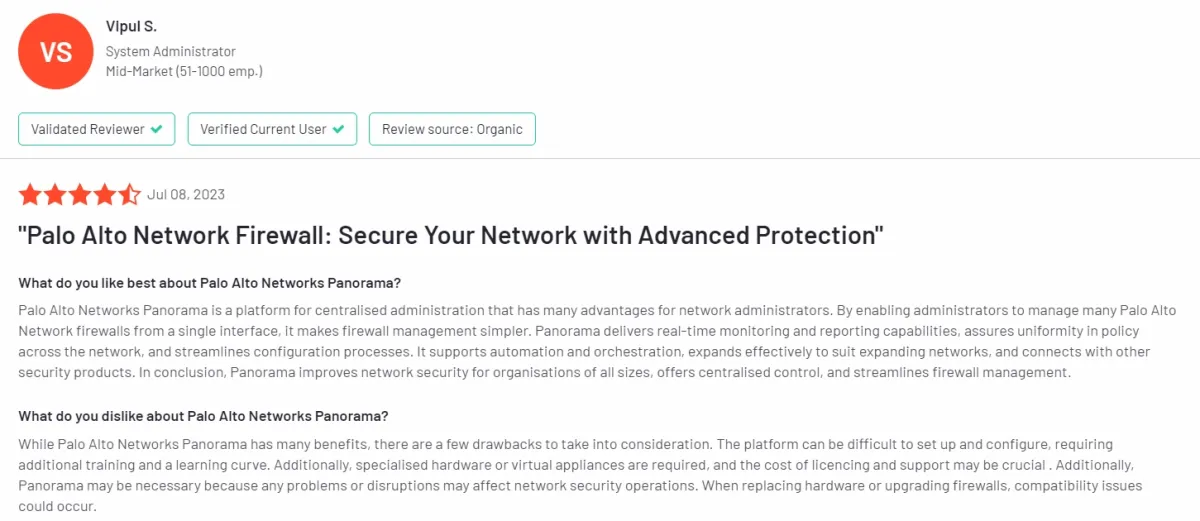
✅ Palo Alto Network Panorama simplifies firewall management by allowing administrators to manage multiple firewalls from a single interface.
❌ Users noted that setting up and configuring Panorama can be challenging and may require additional training and a learning curve.
Figure 3. A user review on Palo Alto Network Panorama
Fortinet FortiManager
Fortinet’s FortiManager, one of the firewall management tools, focus on critical aspects like change management, performance management, compliance management, audit management, and ZTNA, prioritizing operational efficiency, security compliance, and network performance optimization, although it may not offer extensive rule management or VTM functionalities.
User Reviews
✅ Users appreciate its capability to manage multiple cloud environments effectively, streamlining management processes and ensuring consistent security.
❌ Users report that they need to manage next-generation firewalls individually, adding complexity to contract management2 .
Figure 6. A user review on FortiManager
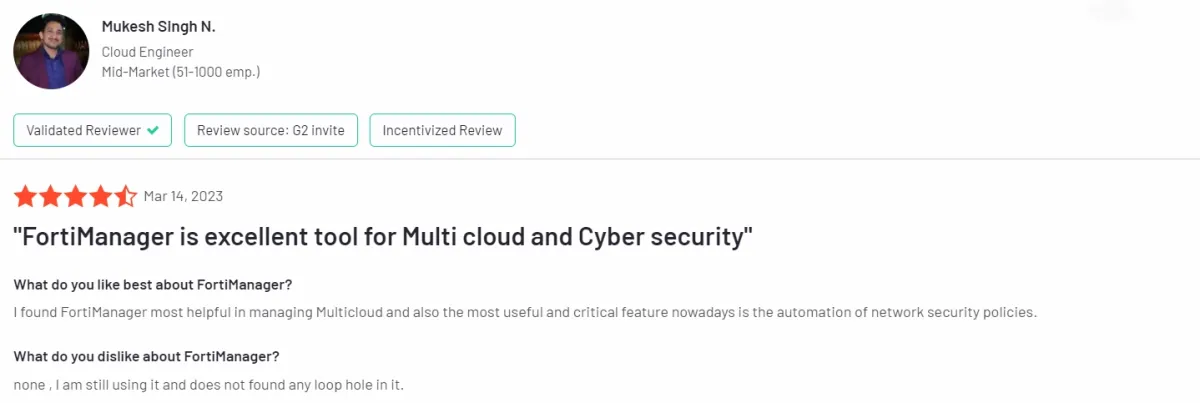
Sophos Central
Sophos, one of the firewall management tools, focuses on critical aspects like change management, compliance management, VTM (Virtual Traffic Management), and ZTNA (Zero Trust Network Access), which are crucial for maintaining a secure and compliant firewall infrastructure. However, it lacks features for performance management, rule management, and audit management, which are vital for optimizing network efficiency, fine-tuning security rules, and maintaining comprehensive security audits.
User Reviews
✅ Users appreciate the manageable licensing options, especially at an enterprise scale, which contributes to cost savings.
❌ Sophos Central may face challenges in integrating with third-party tools and can be dependent on internet connectivity, limiting its functionality without online access3 .
❌ Users have noted inconsistencies and vagueness in alerting mechanisms, along with limited customization options, suggesting areas for refining alert systems and providing more customization flexibility.
Figure 5. A user review on Sophos Central
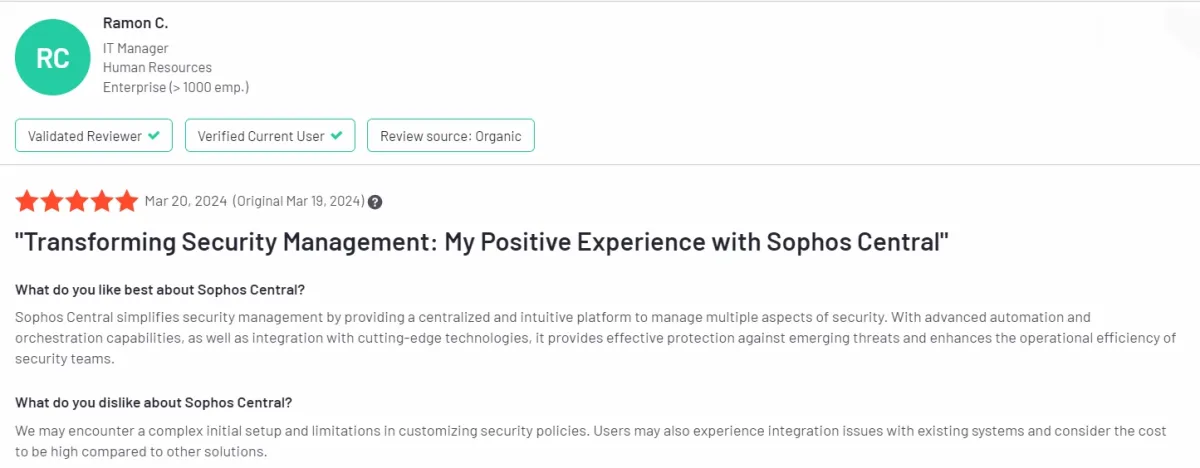
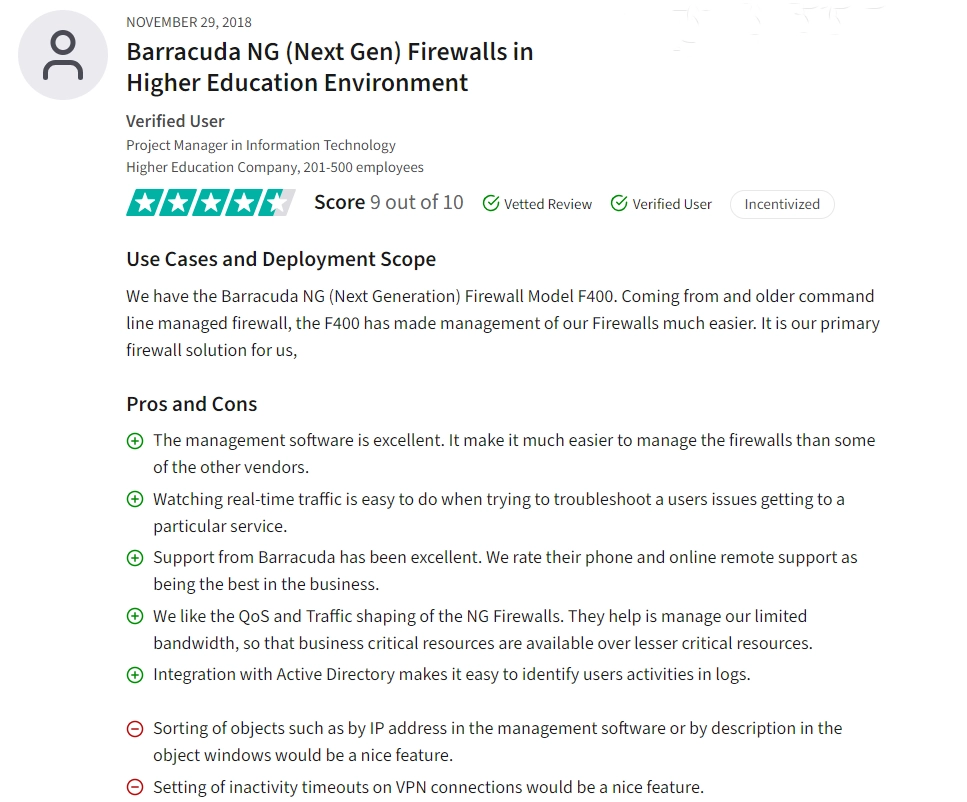
Barracuda CloudGen Firewall Control Center
Barracuda’s managed firewall service offers change management and audit management for firewall configurations and auditing. However, its capabilities fall short in comprehensive tools like compliance management, performance management, rule management, VTM, and ZTNA, which are vital for regulatory adherence, network optimization, policy enforcement, and secure remote access.
User Reviews
✅ Barracuda’s support services, including phone and remote support, are highly rated and considered among the best in the industry, providing reassurance and assistance when needed4 .
❌ The user interface of Barracuda CloudGen firewall is mentioned as being outdated, which may affect user experience and perception of the product’s modernity despite its functional capabilities.
Figure 4. A user review on Barracuda CloudGen Firewall Control Center
Skybox Security Firewall Assurance
Skybox Security’s firewall security management tool offers compliance, rule, audit, change management, and VTM functionalities, crucial for maintaining security policies, ensuring regulatory adherence, and proper configuration management, yet it lacks specific features for performance management and ZTNA, which are vital for optimizing network performance and enforcing secure remote access policies.
User Reviews
✅ Users appreciate Skybox’s ability to manage compliance for firewalls, ensuring adherence to security policies.
❌Some users report issues with identifying dynamic objects, which may affect accurate detection and management.
Check also Skybox Security alternatives.
ManageEngine Firewall Analyzer
ManageEngine’s Firewall Analyzer, one of the firewall management tools, offers essential functionalities such as change management, audit management, compliance management, and rule management, which are crucial for maintaining security standards, tracking modifications, and ensuring regulatory compliance. However, it lacks tools for performance management, VTM, and ZTNA, which are crucial for optimizing network performance, enhancing secure remote access capabilities, and ensuring advanced threat protection.
User Reviews
✅ The examining capabilities of ManageEngine Firewall Analyzer, which aid in identifying weaknesses in network security posture and suggesting necessary policy changes, are praised by users.
✅ Users appreciate the decent technical support provided by ManageEngine for implementation and troubleshooting.
❌ Improvement is suggested in providing more detailed information on monitoring employee internet usage.
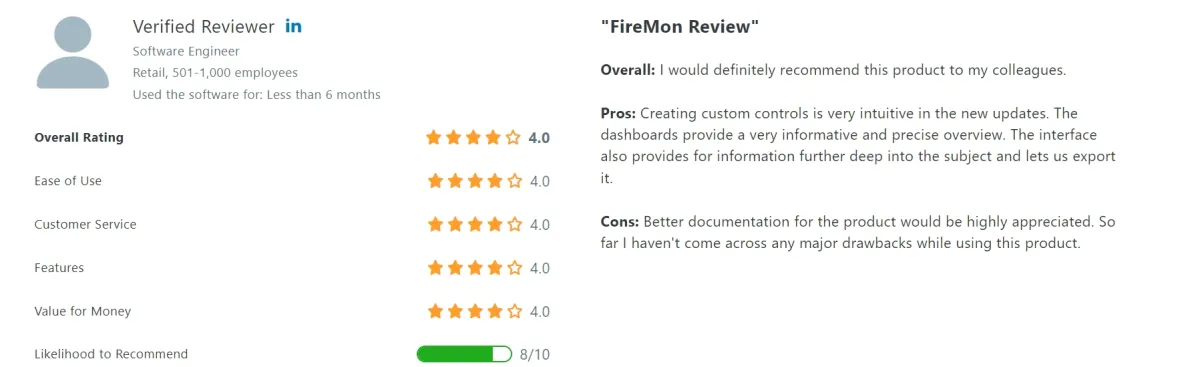
FireMon Security Manager
FireMon Security Manager, one of the firewall management tools, provides in compliance, rule, audit, and change management, crucial for ensuring regulatory adherence, maintaining security policies, conducting audits, and implementing controlled changes, but lacks features like performance management, VTM, and ZTNA, which are vital for optimizing system performance, advanced traffic routing, and secure remote access, respectively.
User Reviews
✅Some users appreciate personalized query capabilities for compliance and custom reports.
❌Improved documentation is desired for better understanding and usage.
Figure 8. A user review on FireMon Security Manager
Titania Nipper
Titania Nipper is a firewall management solution that offers integration with SIEM and ticketing tools to streamline incident and workflow management. It focuses on compliance and audit management, allowing organizations to maintain regulatory standards and security postures effectively. However, Nipper does not provide rule or performance management, making it ideal for compliance-focused environments but potentially less suited for ongoing firewall rule adjustments or performance optimization tasks.
User reviews
✅ Users appreciate the quick generation of detailed reports, essential for compliance audits and configuration analysis, enhancing time-to-market and improving client service.
❌ The tool lacks support for Next-Generation firewalls like FTD and other OSs, limiting its flexibility for diverse network environments.5
Common features checklist
Here is a list of common features that a good firewall management solution should have:
- Ease of deployment and activation: A good firewall management solution should allow for quick, straightforward deployment and activation with minimal setup complexity.
- Workload on security/network teams: It should effectively streamline workflows, minimizing manual tasks and reducing the operational burden on security and network teams.
- Required company maturity: The solution should match the company’s security maturity level, offering flexible scaling for both small organizations and complex enterprise environments.
- Change management life cycle process value addition: It should enhance the firewall change management process by providing clear, documented workflows that ensure safe and efficient updates.
- DAST tools integration: The solution should seamlessly integrate with Dynamic Application Security Testing (DAST) tools to detect vulnerabilities during runtime.
- Detection of risky situations: Effective firewall management includes risk detection capabilities, alerting teams to potential threats or misconfigurations in real-time.
- Automation support: Automation features allow for repetitive tasks like rule adjustments and compliance checks to be handled efficiently without manual intervention.
- Dead rule detection and cleaning (cyber hygiene): It should identify and remove obsolete or unused rules, improving firewall performance and reducing security risks.
- Compliance readiness: A good solution aids compliance efforts by maintaining records, tracking policy changes, and generating reports for regulatory requirements.
- Reporting: Comprehensive reporting features enable insight into firewall performance, compliance status, and security posture, supporting informed decision-making.
Key criteria for selecting the right tool
Key features
Firewall management provides features for maintaining a secure and efficient network environment. The features below are offered by a subset of vendors. Based on how businesses value these features, they can use them to choose some products over others.
1. Firewall Integration & Compatibility
| Firewall Management Tools | Check Point | Cisco | Fortinet | Palo Alto | Sophos |
|---|---|---|---|---|---|
| Tufin Orchestration Suite | ✅ | ✅ | ✅ | ✅ | ❌ |
| Palo Alto Network Panorama | ❌ | ❌ | ❌ | ✅ | ❌ |
| Barracuda CloudGen Firewall Control Center | ❌ | ❌ | ❌ | ❌ | ❌ |
| ManageEngine Firewall Analyzer | ✅ | ✅ | ✅ | ✅ | ✅ |
| Sophos Central | ✅ | ✅ | ✅ | ❌ | ✅ |
| AWS Firewall Manager | ❌ | ❌ | ✅ | ✅ | ❌ |
| Fortinet FortiManager | ❌ | ❌ | ✅ | ❌ | ❌ |
| Cisco Secure Firewall Management Center | ❌ | ✅ | ❌ | ❌ | ❌ |
| Microsoft Azure Firewall Manager | ✅ | ❌ | ❌ | ❌ | ❌ |
| FireMon Security Manager | ✅ | ✅ | ✅ | ✅ | ❌ |
| Skybox Security Firewall Assurance | ✅ | ✅ | ✅ | ✅ | ✅ |
Firewall integrations involve incorporating firewall devices, policies, and configurations into your overall network security architecture, including firewall management service. These tools need to be seamlessly configured so that firewalls can send syslogs to the firewall management tools server. This integration ensures that security policies, rules, and threat intelligence are efficiently managed and applied across the network infrastructure.
2. SIEM Integration
Table 4. SIEM and IT ticketing tool integration
| Software | SIEM integration | Ticketing Tools Integration | ||
|---|---|---|---|---|
| Tufin Orchestration Suite | IBM QRadar, Splunk, Microsoft Azure Sentinel | BMC, ServiceNow, HP ServiceManager, RSA, Puppet, CA Technologies | ||
| Palo Alto Network Panorama | Splunk | VMware NSX, ServiceNow, Aruba, Any REST API | ||
| Barracuda CloudGen Firewall Control Center | IBM QRadar | Autoask, Connectwise, ServiceNow | ||
| Manage Engine Firewall Analyzer | Included in the software** | Jira, ServiceNow | ||
| Sophos Central | N/A* | Autotask, Connectwise | ||
| AWS Firewall Manager | IBM QRadar, Sumo Logic | AWS Service Catalog | ||
| Fortinet FortiManager | IBM QRadar, | ServiceNow, FortiSIEM | ||
| Cisco Secure Firewall Management Center | IBM QRadar, Splunk | Jira, ServiceNow | ||
| Microsoft Azure Firewall Manager | Microsoft Sentinel | Jira, ServiceNow*, BMC Helix* | ||
| FireMon Security Manager | Splunk | BMC, ServiceNow, Jira, Accenture, REDSEAL | ||
| Skybox Security Firewall Assurance | Splunk | BMC, ServiceNow | ||
| Titania Nipper | Splunk, Elastic, ArcSight | ServiceNow |
*Integrations possible via SIEM /ITSM API : SIEM Script for Sophos and ITSM connector for Microsoft Azure
** Since ManageEngine Firewall Analyzer included SIEM capability, no integration is needed.
Security Information and Event Management (SIEM) systems are essential for preventing, detecting, and responding to cyber-attacks by providing comprehensive visibility into potential security risks.6 SIEM solutions collect and analyze security data from various sources, identifying areas of high risk and enabling proactive mitigation strategies to reduce incident response time and costs.
Integration of SIEM with firewall management tools is crucial because it allows for real-time monitoring and analysis of firewall events, enhancing threat detection and response capabilities. As SIEM systems evolve to converge with big data analytics, they offer enhanced functionality for managing and securing critical infrastructures.
3. IT Ticketing Tools Integration
An IT/ITSM ticketing system is a tool that helps organizations manage and track IT incidents and service requests by creating “tickets” that record the problem, its status, and its resolution process. These systems streamline IT support by organizing workflows, prioritizing tasks, and ensuring accountability.
Integrating IT ticketing tools with a centralized firewall management system is crucial because it enables automatic creation and tracking of firewall-related issues, such as security incidents or configuration changes. This integration ensures that security teams can manage and resolve firewall issues more efficiently, improve compliance, and maintain detailed logs for auditing purposes.
4. Compliance management
Firewall compliance management includes ensuring that your firewall rules and firewall configurations align with industry standards and regulatory requirements to protect sensitive data and prevent data breaches.
5. Change management
This feature allows you to track and audit changes to firewall rules and firewall configurations, ensuring that modifications are made securely and in line with industry standards and organizational policies.
Read more: NCCM software and Top 7 Firewall Configuration Software.
6. Rule management
It includes the ability to create, modify, and delete rules as needed to enhance security posture and streamline network traffic management.
7. Performance management
This enables monitoring firewall performance metrics, optimizing rule sets for efficiency, and identifying and mitigating performance bottlenecks to ensure optimal network performance.
8. Audit management
Firewall audit includes maintaining audit logs, conducting periodic audits, and generating audit reports for compliance purposes to track and analyze firewall activities.
9. Virtual Traffic Management (VTM) and Zero Trust Network Access (ZTNA)
Firewall management solutions that incorporate VTM and ZTNA capabilities for advanced network traffic management and secure access controls enhance network security, especially in remote locations and cloud environments. You may also check Top 10 ZTNA Solutions.
Market presence
1. User ratings and reviews
Insights from existing users can provide valuable information about the software’s reliability, ease of use, customer support, and overall satisfaction.
2. Number of employees
A company’s workforce size is an indicator of its innovation potential, and customer service capabilities. In network security, a company’s size plays a role in providing the necessary support and expertise.
3. Pricing
Pricing is a critical factor in selecting the right firewall management tools as it directly impacts the total cost of ownership (TCO) and return on investment (ROI), influencing the affordability and value proposition of the solution for the organization.
FAQ
What is the difference between firewall management software & firewall management services?
These terms are sometimes used interchangeably. A software solution to manage firewalls that is offered as a SaaS application can be called a firewall management service.
However, firewall management service has another meaning as well. There are managed service providers (MSPs) that manage firewall configurations of their clients. This service is also called firewall management service.
Why is firewall management important?
Data breaches on a global scale exceed $4 million on average according to network security statistics, highlighting the critical need for network security and robust firewall management tools.
In what areas are firewall management tools the ideal solution? When are firewall management tools especially needed?
Firewall management tools are particularly essential for maintaining firewall security through regular firewall security audits to ensure compliance and the proper functioning of firewall devices. For network administrators and security professionals, these tools help identify and resolve firewall rule misconfigurations or violations of network security policies that could lead to security breaches.
These tools are indispensable for security and traffic analysis, making firewall rules clearer, more stable, and easier to understand. Firewall management software assists in policy optimization and firewall performance tuning, allowing users to optimize firewall rulesets. Additionally, they provide logging and reporting capabilities, generating compliance reports that auditors require, such as details on firewall policies, when/why/what/who/where rules were deployed, and proof of compliance with security policy management.
Finally, firewall security management software increases network security by providing centralized management of multi-vendor firewalls and other network devices. Whether dealing with traditional firewalls, next-generation firewalls, or cloud security groups, these tools allow for effective firewall rule management and firewall configuration to mitigate security threats and ensure a secure network across hybrid or multi-cloud environments.
Important security software to combine with firewall management tools
Network security audit tools: Identify threats, vulnerabilities, and malicious activity to help companies mitigate cyber attacks and follow compliance with regulations.
NCCM software: Monitor information about your organization’s network devices by documenting network device configurations.
DSPM vendors: Provide network visibility into where to find sensitive data, who has access to it, and how it has been used across the cloud.
Network security policy management solutions (NSPM): Protect network infrastructure using firewalls and security policies against all threats.
SDP software: Deliver a software-defined perimeter (SDP) across the cloud to determine who gets access to what resources.
ZTNA Solutions: Enable secure, efficient remote access for employees working from various locations, and ensure that only authorized users can access sensitive corporate resources.
Further reading
- Firewall Integration of Top Management Services
- Firewall Audit Logs: Analysis and 6 Steps for Improvement
- Top 7 Open Source Firewall Audit Tools: Analysis & Comparison
External Links
- 1. Tufin Orchestration Suite Reviews 2025: Details, Pricing, & Features | G2.
- 2. Best Choice for Managing FortiGates | TrustRadius. TrustRadius
- 3. Sophos Central Reviews 2025: Details, Pricing, & Features | G2.
- 4. Barracuda NG (Next Gen) Firewalls in Higher Education Environment | TrustRadius. TrustRadius
- 5. A very useful tool in vulnerability process assessment, at a very affordable cost | TrustRadius. TrustRadius
- 6. González-Granadillo, G., González-Zarzosa, S., & Diaz, R. (2021). Security information and event management (SIEM): analysis, trends, and usage in critical infrastructures. Sensors, 21(14), 4759.



Comments
Your email address will not be published. All fields are required.