Windows Firewall is a security feature within the Windows operating system, designed to protect devices from malware and unauthorized access. Windows firewall audit log analysis might be done manually or via a Windows Firewall log analyzer.
Explore the procedures and benefits of conducting a Windows Firewall audit, ensuring your network remains secure and resilient against threats:
Windows Firewall log analyzers
Table 1. Top 3 Windows Firewall event logs analyzers
| Tool | User Rating | Employee Size | Free Trial | |
|---|---|---|---|---|
| ManageEngine EventLog Analyzer | 4.8 out of 14 reviews | 387 | ✅ (30 days) | |
| SolarWinds Firewall Log & Event Manager | 3.3 out of 164 reviews | 2,626 | ✅ (30 days) | |
| Corner Bowl Event Log Manager | 4.8 out of 61 reviews | 1 | ✅ | |
A Windows Firewall log analyzer enables organizations to monitor activity, receive detailed graphical reports, and gain insights. It also allows full control over firewall settings and policies through configuration audits, and provides real-time security alerts to swiftly identify and mitigate network attacks.
If you are in search of a tool for a comprehensive firewall rule audit, check firewall audit software.
Windows Firewall overview
Windows Defender Firewall is a security feature that filters network traffic entering and exiting your device based on criteria like source and destination IP addresses, IP protocol, and port numbers.
Figure 1. Windows Defender Firewall dashboard
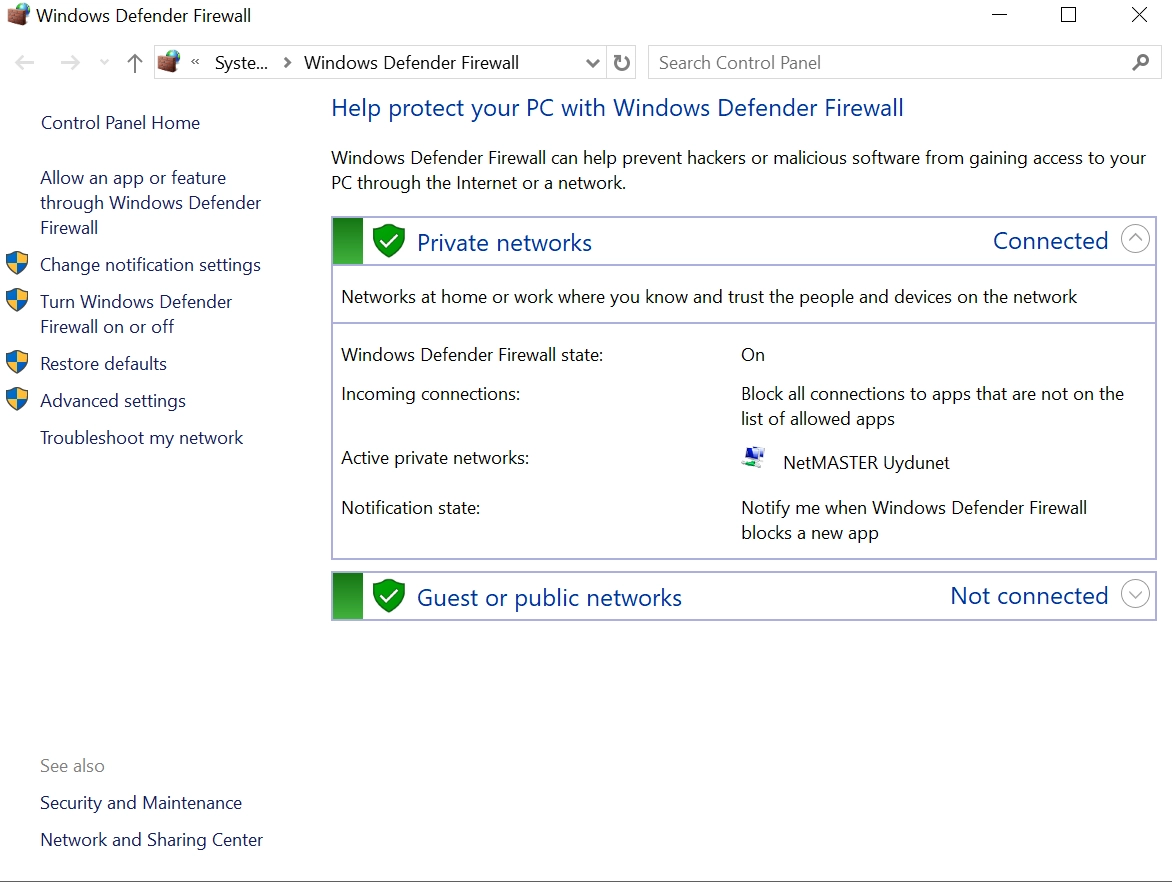
The Windows Firewall service is a host-based firewall included and enabled by default on all Windows editions, supporting Internet Protocol security (IPsec).1 IPsec can be used to require authentication for any device attempting to communicate, blocking unauthenticated devices from accessing your system.
Importance of Windows Firewall Audits mode
Recent test results highlight that the firewall successfully defended against 0-day malware attacks and detected prevalent malware with 100% accuracy, significantly surpassing the industry average of 99.4%.2
By configuring firewall rules, security administrators can block or allow traffic based on the services and applications installed, ensuring only authorized inbound connections are permitted. This feature provides an additional layer of network security and can be tailored to manage incoming traffic effectively, which is crucial for both domain network environments and public networks.
Additionally, firewall rules and settings can be managed using group policy on a domain network, enabling security administrators to maintain consistent security across multiple systems within an organization.
How to enable Windows Firewall Audit manually
By default, Windows Firewall with Advanced Security does not generate audit events for the Windows Firewall service or IPsec. To enable event logging for Windows Server 2008 or Windows Vista, you must manually turn it on, which is recommended only for troubleshooting purposes due to the potential high volume of events generated.
First, make sure that you have a local administrators group membership or appropriate authority to enable Windows Firewall audit mode. For this, open an administrative command prompt and execute the following command3 :
auditpol.exe /set /SubCategory:”MPSSVC rule-level Policy Change”,”Filtering Platform policy change”,”IPsec Main Mode”,”IPsec Quick Mode”,”IPsec Extended Mode”,”IPsec Driver”,”Other System Events”,”Filtering Platform Packet Drop”,”Filtering Platform Connection” /success:enable /failure:enable
After running the command, restart the Windows Firewall service with:
net stop MPSSVC
net start MPSSVC
To disable event logging later, use the same command but use:
/success:disable /failure:disable
How to reach audit event logs manually
An audit event is a security-relevant occurrence in the system, such as changes to the security state or violations of access control policies. These events are detected by programs and kernel modules, reported to the system audit logger, and include the event name, success or failure, and additional security-related information.4
To view the Windows Firewall audit log files in Event Viewer,
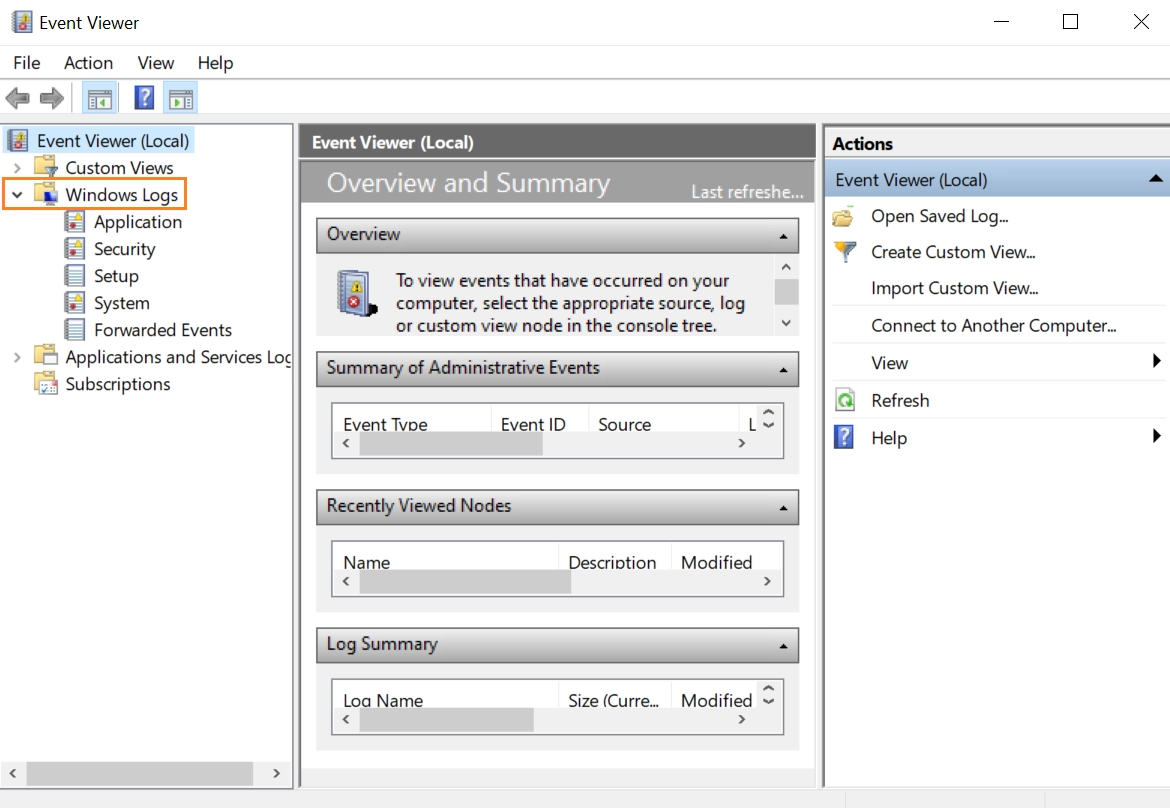
1-Open Event Viewer by clicking Start, typing eventvwr in the Start Search box, and pressing ENTER.
2-Confirm any User Account Control dialog boxes that appear and click Continue.
Figure 2. Event Viewer Dashboard
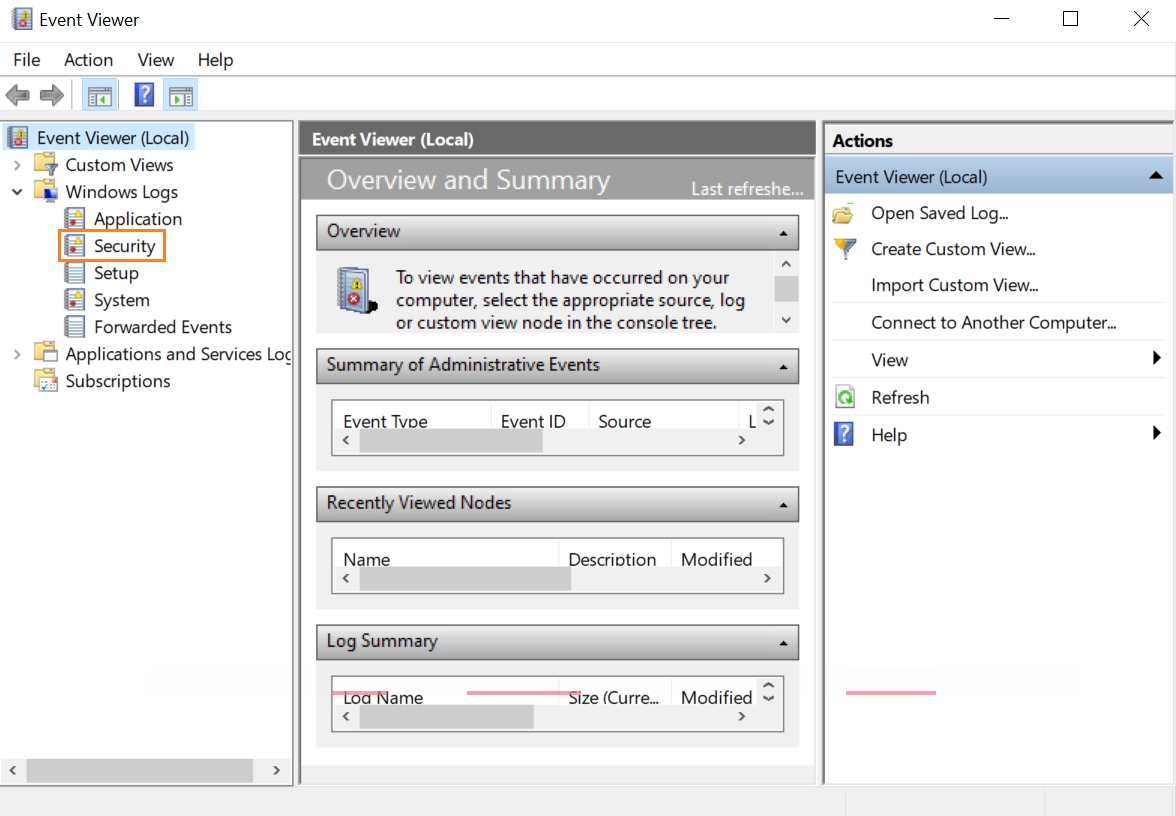
3-In the navigation pane of Event Viewer, expand the Windows Logs branch.
Figure 3. Event Viewer Windows event logs
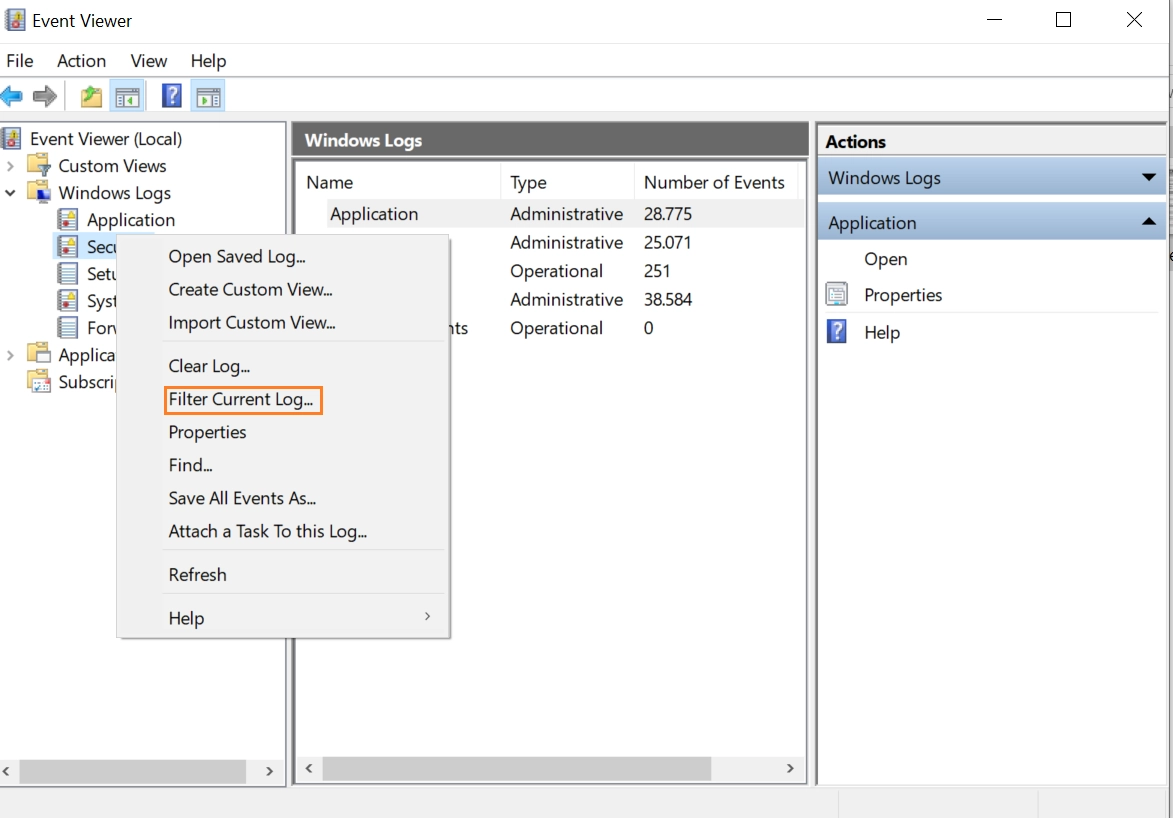
4-Right-click on Security and select Filter Current Log.
Figure 4. Filtering logs in Event Viewer
5-In the Includes/Excludes Event IDs box, type 4600-5500 to filter the events related to Windows Firewall audit.
Figure 5. Typing event ID in Event Viewer
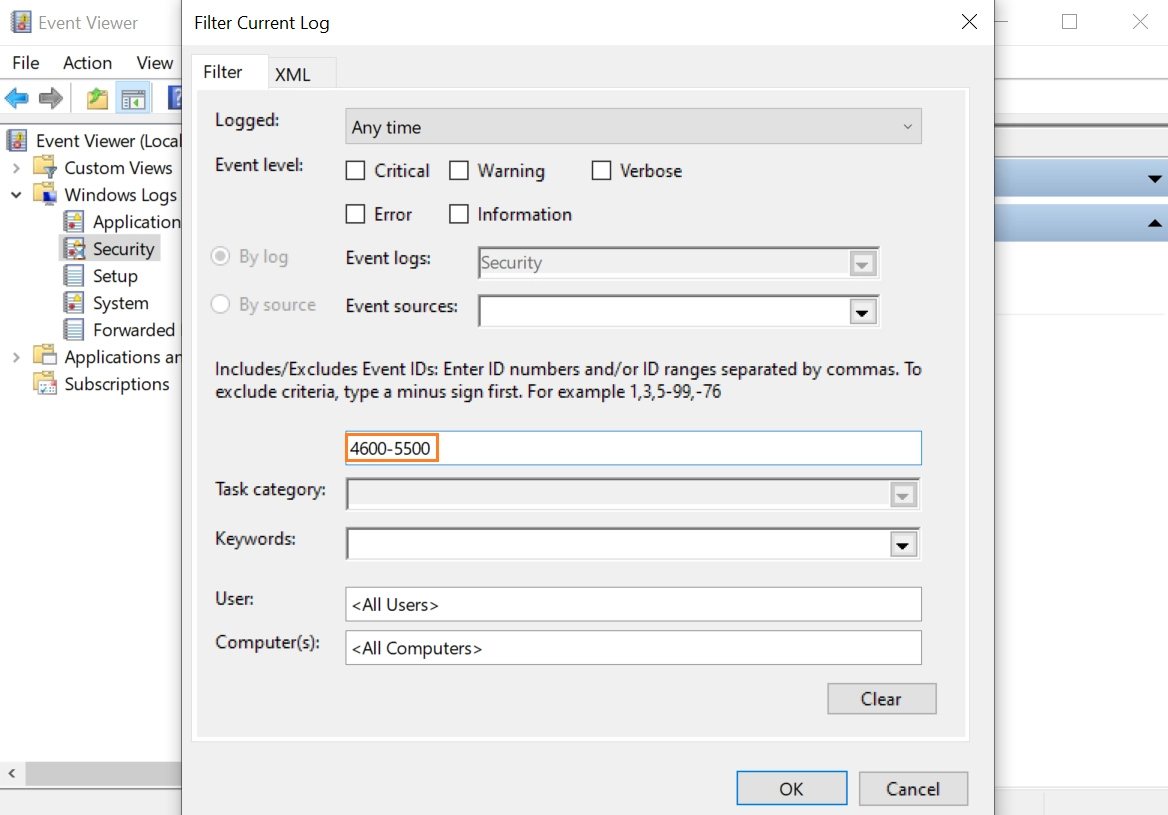
6-Click OK to apply the filter.
Figure 6. Filtered Windows firewall event logs
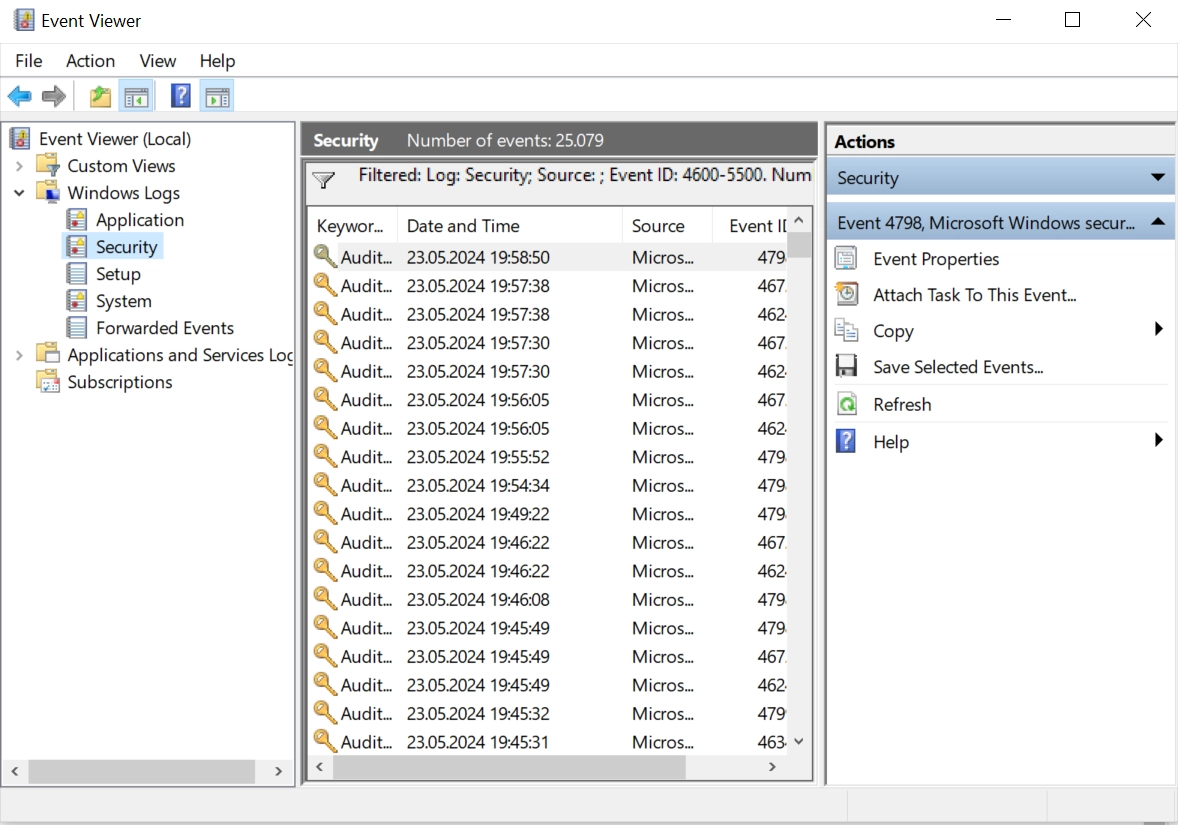
Windows Firewall logs can be viewed in Notepad++ or MS Excel to extract fields and analyze them for troubleshooting purposes.
FAQs
What is the purpose of a firewall audit?
A firewall audit is a thorough examination of firewall rules, configurations, and policies to assess the security posture of an organization’s network. It involves scrutinizing the firewall rule base, evaluating the firewall’s physical and virtual aspects, and ensuring compliance with internal policies and industry standards.
If you are looking for a firewall audit solution, you may check firewall audit software.
How secure is Windows Defender Firewall?
Recent test results highlight that the firewall successfully defended against 0-day malware attacks and detected prevalent malware with 100% accuracy, significantly surpassing the industry average of 99.4%. This exceptional performance emphasizes the importance of regular Windows Firewall audits to maintain this high level of security.
How do users evaluate Windows Defender Firewall?
Recent test results highlight its effectiveness, showcasing a solid protection score based on nearly 16K user experience.5
Further reading
- Top 12 Firewall Audit Software & Integration-Based Comparison
- Top 7 Open Source Firewall Audit Tools: Analysis & Comparison
- 5 Firewall Best Practices for SMEs and Large-Enterprises
- AI Firewall vs NGFWs: Detailed Analysis & Comparison
If you need help finding a vendor or have any questions, feel free to contact us:
External Resources
- 1. Enable IPsec and Windows Firewall Audit Events. Microsoft. Accessed: 24/May/2024.
- 2. AV-TEST Product Review and Certification Report. AV-TEST. Accessed: 24/May/2024.
- 3. Enable IPsec and Windows Firewall Audit Events. Microsoft. Accessed: 24/May/2024.
- 4. Audit events. IBM. Accessed: 24/May/2024.
- 5. AV-TEST Product Review and Certification Report. AV-TEST. Accessed: 24/May/2024.



Comments
Your email address will not be published. All fields are required.