As the Chief Information Security Officer of a fintech platform, compliance to standards like PCI DSS is a top priority for me. Since firewall audit software facilitate compliance & improve our security posture, I have reviewed all major solutions. See the top 12 solutions & click the links to see my rationale:
- Tufin Orchestration Suite for firewall policy management orchestration
- AlgoSec Firewall Analyzer for compliance reporting
- Qualys Enterprise TruRisk Platform
- ManageEngine Firewall Analyzer for log analysis and management
- FireMon Policy Manager
- Palo Alto Networks Panorama for organizations relying only on Palo Alto firewalls
- SolarWinds Security Event Manager
- AWS Firewall Manager for businesses that rely mostly on AWS (i.e. no significant multi cloud or on-prem deployments)
- Cisco Defense Orchestrator for organizations relying only on Cisco firewalls
- Titania Nipper for configuration assessment
- Skybox Firewall Assurance for automated compliance of industry security standards
- Network Perception
Firewall audit software helps validate compliance and manage firewall configurations. Explore top firewall audit tools along with their ticketing systems integrations, firewall compatibility, detailed comparison as well as customer satisfaction metrics like number of reviews:
Comparing the top 12 firewall audit software vendors
Table 1. Vendor comparison based on market presence
| Software | User Rating* | # of employees** | |
|---|---|---|---|
| Tufin Orchestration Suite | 3.8 out of 100 reviews | 458 | |
| AlgoSec Firewall Analyzer | 4.5 out of 189 reviews | 545 | |
| Qualys Enterprise TruRisk Platform | 4.2 out of 167 reviews | 2,783 | |
| ManageEngine Firewall Analyzer | 4.5 out of 141 reviews | 387 | |
| FireMon Policy Manager | 4.1 out of 81 reviews | 231 | |
| Palo Alto Network Panorama | 4.5 out of 60 reviews | 16,348 | |
| SolarWinds Security Event Manager | 4.6 out of 191 reviews | 2,625 | |
| AWS Firewall Manager | 4.4 out of 48 reviews | 130,371 | |
| Cisco Defense Orchestrator | 4.7 out of 16 reviews | 100,466 | |
| Titania Nipper | 4.2 out of 14 reviews | 90 | |
| Skybox Firewall Assurance | 4.4 out of 4 reviews | 296 | |
| Network Perception | N/A | 43 |
Table 2. Vendor comparison based on key features
| Software | Ticketing | Deployment | Real-time data |
|---|---|---|---|
| Tufin Orchestration Suite | ✅ | hybrid | ✅ |
| AlgoSec Firewall Analyzer | ❌ | hybrid | ❌ |
| Qualys Enterprise TruRisk Platform | ✅ | cloud | ✅ |
| ManageEngine Firewall Analyzer | ❌ | cloud | ✅ |
| FireMon Policy Manager | ✅ | cloud | ✅ |
| Palo Alto Network Panorama | ✅ | cloud | ✅ |
| SolarWinds Security Event Manager | ✅ | hybrid | ✅ |
| AWS Firewall Manager | ✅ | on-prem | ✅ |
| Cisco Defense Orchestrator | ❌ | hybrid | ✅ |
| Titania Nipper | ✅ | hybrid | ❌ |
| Skybox Firewall Assurance | ❌ | cloud | ❌ |
| Network Perception View | ✅ | on-prem | ✅ |
* Based on data from B2B review platforms like G2, Gartner, and TrustRadius. For more: Market presence criteria explained
** Based on data from LinkedIn
To understand features: Features and integrations explained
If you are looking for firewall compliance of industry regulations such as GDPR and HIPAA, read Key Components of Firewall Compliance.
Table 3. Firewall compatibility of firewall audit software
| Tools | Check Point | Cisco | Fortinet | Palo Alto | Sophos |
|---|---|---|---|---|---|
| Tufin Orchestration Suite | ✅ | ✅ | ✅ | ✅ | ❌ |
| AlgoSec Firewall Analyzer | ✅ | ✅ | ✅ | ✅ | ❌ |
| ManageEngine Firewall Analyzer | ✅ | ✅ | ✅ | ✅ | ✅ |
| FireMon Policy Manager | ✅ | ✅ | ✅ | ✅ | ❌ |
| Palo Alto Network Panorama | ❌ | ❌ | ❌ | ✅ | ❌ |
| SolarWinds Security Event Manager | ❌ | ✅ | ❌ | ✅ | ❌ |
| AWS Firewall Manager | ❌ | ❌ | ✅ | ✅ | ❌ |
| Cisco Defense Orchestrator | ❌ | ✅ | ❌ | ❌ | ❌ |
| Titania Nipper | ✅ | ✅ | ❌ | ✅ | ✅ |
| Skybox Firewall Assurance | ✅ | ✅ | ✅ | ✅ | ✅ |
| Network Perception | ✅ | ✅ | ✅ | ✅ | ❌ |
Ranking: Products are ranked based on the number of reviews across B2B review platforms except for the sponsored products ranked at the top.
Firewall audit tool inclusion criteria:
- Offering firewall audit and compliance products along with other network security offerings.
- Integration with security information and event management (SIEM) platforms. This integration enhances the overall security posture by providing timely analysis of security events.
Firewall inclusion criteria in firewall compatibility table: Firewall vendors with 1000+ reviews on Gartner were included.
To have a deeper understanding about firewall integration, read top firewall management services and their firewall integrations.
This article covers enterprise-focused solutions. If you are looking for free alternatives for your small business, check out open source firewall audit tools.
In-depth product analysis

Tufin Orchestration Suite
Tufin is highly advantageous in ease of deployment, identity-based rules, offering flexible IP block management, strong traffic engineering, almost real-time reporting, and effective rule violation alerts. However, Tufin has some licensing and subscription model disadvantages and custom report generation is limited.
Apart from firewall audit, Tufin offers these capabilities: Network security policy orchestration, compliance audit, and automation of security policies across complex networks.
Figure 1. Tufin’s SecureTrack reporting dashboard
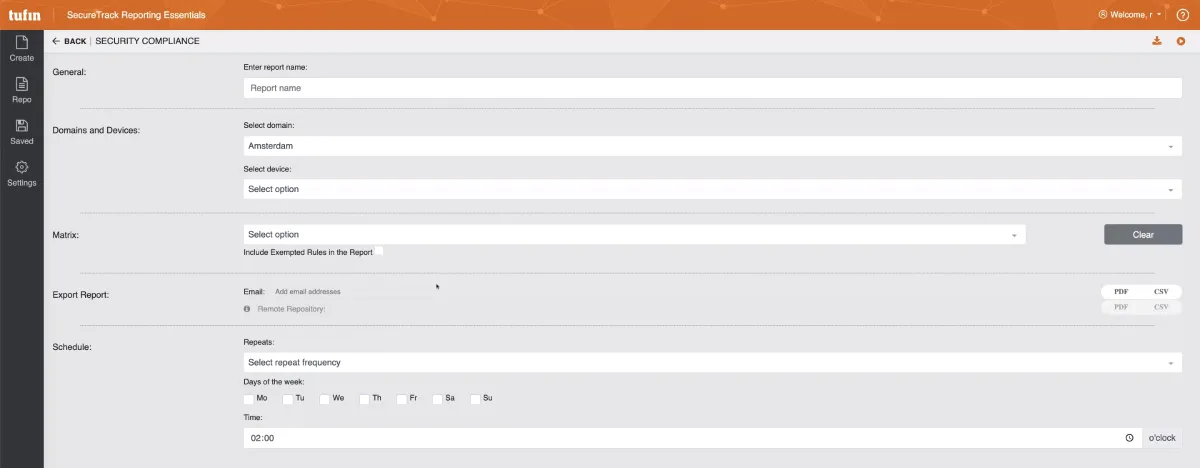
Apart from firewall audit, Tufin offers these capabilities: Network security policy orchestration, compliance audit, and automation of security policies across complex networks.
User reviews
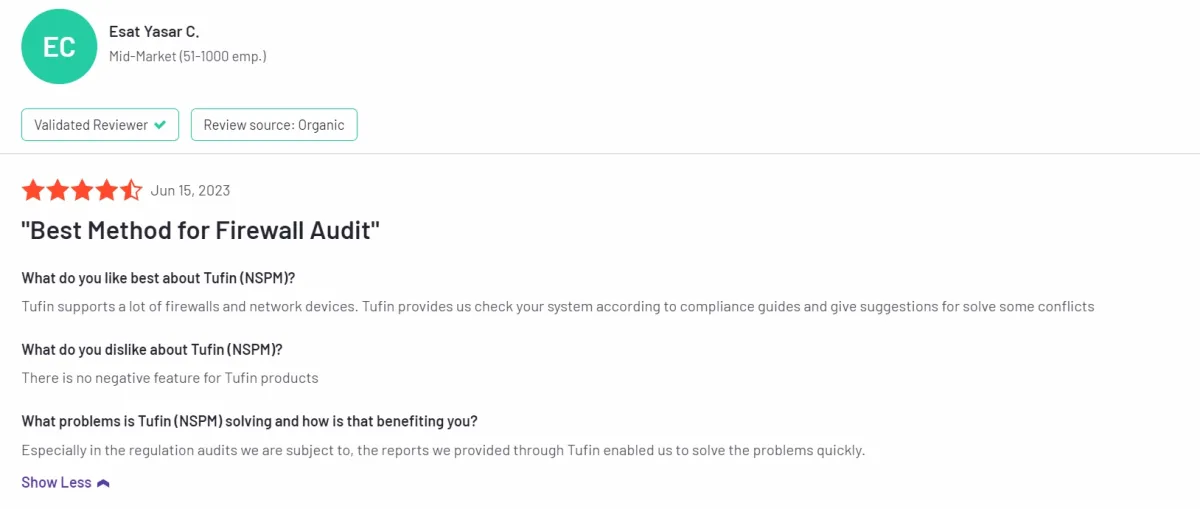
✅ Users on B2B review platforms highlight that Tufin supports numerous firewalls and network devices, offering compliance checks and conflict resolution suggestions.1
Figure 2. A customer review on Tufin
❌ Based on our comparison of different firewall audit tools and user comments, Tufin’s licensing fee was higher than the average provider’s.
AlgoSec Firewall Analyzer
AlgoSec offers network security policy management solutions that automate and orchestrate security policy configuration, compliance, and change management.
Algosec is noted for its ready-made report templates and optimization capabilities, though it struggles with vulnerability management and can become cumbersome with excessive reporting and static analysis.
User reviews
A customer review states that while AlgoSec offers many features, navigating the user interface (UI) can be a bit challenging, especially for users who are unfamiliar with the product.
Qualys Enterprise TruRisk Platform
Qualys Enterprise TruRisk Platform offers a cloud-based platform for compliance requirement monitoring and risk management, including Policy Compliance, File Integrity Monitoring, and Cloud Security Posture Management.
User reviews
✅Customers find Qualys’s PCI-DSS (industry regulation for securing cardholder data) firewall compliance tool user friendly.
❌They also found its subscription costs high.
ManageEngine Firewall Analyzer
ManageEngine Firewall Analyzer is a firewall audit software, capabilities of which includes real-time monitoring, firewall logs analysis, and continuous compliance reporting to enhance network security.
User reviews
✅ Users appreciate the reports being highly graphical, visually appealing, and can be set to automatically run and be emailed to users.
✅ Log analytics and IDS systems are highlighted as key strengths of the software.2
Figure 3. A customer review on ManageEngine Firewall Analyzer
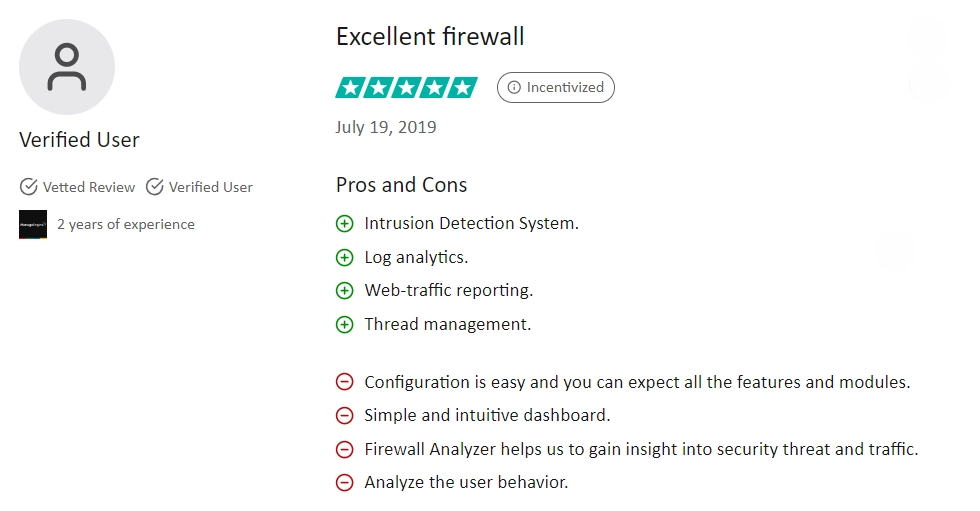
❌ Users stress the need to increase the firewall management capabilities for all vendors without issues.
FireMon Policy Manager
Firemon Policy Manager claims to provide network security policy management solutions, including compliance, risk analysis, and automated change management.
Each step in the firewall audit process at FireMon is at least partially automated, with automation aiding in identifying issues, suggesting changes, implementing those changes, and monitoring the outcomes.
User reviews
According to a customer review, manual data entry for the firewall laws is useful but risky due to irreversible deletion, requiring careful management and additional components for full functionality.
Palo Alto Networks Panorama
With the firewall audit software Panorama, Palo Alto Network supports firewall audits by providing centralized oversight of security policies, enabling detailed traffic analysis, and ensuring consistent policy enforcement across the network.
User reviews
✅Users can collect logs from various connected firewalls, aiding in comprehensive network analysis and troubleshooting.
❌There are no default templates or device groups for basic firewall configuration, which could simplify initial setup.
SolarWinds Security Event Manager
SolarWinds Security Event Manager enables to monitor logs including those from firewall. Based on other users’ reviews on review platforms, its pros and cons are:
✅ Users appreciate product’s ease of set up and use.
❌ There is a recent feedback criticizing pricing methods of SolarWinds SEM3 .
AWS Firewall Manager
AWS Firewall Manager provides audit capabilities by enabling automatic enforcement of internal policies on security tools, ensuring regulatory compliance with firewall rules organization-wide. It offers a centralized dashboard for monitoring protected resources, identifying non-compliant configurations.
User reviews
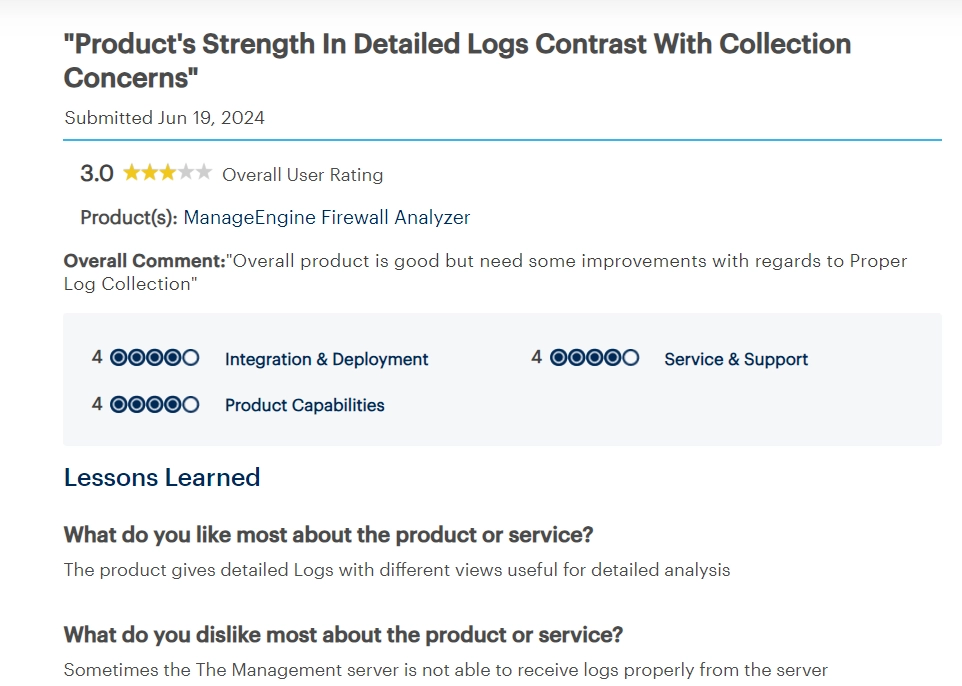
✅ Built-in features and pre-configured compliance frameworks help streamline compliance reports and auditing processes.
❌ Integrating certain third-party security tools can pose challenges due to compatibility issues or the need for additional configuration, potentially complicating the security setup.
Figure 4. A customer review on AWS Firewall Manager
Cisco Defense Orchestrator
Cisco claims that Defense Orchestrator, the firewall rule review product, is designed to streamline policy management across Cisco firewalls and public cloud infrastructure.
User reviews
✅ A positive review of Defense Orchestrator commends its accessible pricing and effective threat defense for firewalls.
❌ Users highlight the lack of features in comparison to the on-premises version.
Titania Nipper
Titania Nipper offers firewall auditing capabilities, generating detailed security audit reports on configuration issues and compliance gaps to bolster network security.
User reviews
✅ The ability to update the tool with the latest National Vulnerability Database (NVD) files improves results and threat insights.
❌ Some users suggest improving the reports, reducing false positives, and enhancing the dashboard for a more intuitive experience.
Skybox Firewall Assurance
claims to provide cybersecurity management solutions, including firewall rule review and compliance management. The company also offers products focusing on network visibility and vulnerability detection.
User reviews
While users found its firewall assurance tool simple and thorough, they also identified concerns regarding its local customer support for vendors and resellers.
Figure 5. A customer review on Skybox Firewall Assurance
Network Perception
Network Perception View delivers firewall auditing by visualizing firewall configurations and identifying potential security gaps to enhance network protection. Users can add comments to specific access rules and export an audit trail of all user comments for documentation and compliance purposes.
Comparison of 3 firewall audit software
See the benchmark table created by AIMultiple’s own experience:
Table 4. Firewall audit benchmark
| Criteria | Tufin | Skybox | Algosec | |
|---|---|---|---|---|
| Required effort for deployment and activation | 🏆 Low | High | Med | |
| Workload on Security/Network Teams | Med | 🏆 Low | High | |
| Ticketing Tools Integration | 🏆 Wide Variety | Narrow Variety | Wide Variety | |
| Detection of Risky Situations | 🏆 High | 🏆 High | Med | |
| Automation Support | 🏆 High | Med | Low | |
| Reporting | Med | High | 🏆 High |
Required effort for deployment and activation
- Tufin: Low🏆 – Tufin is relatively easy to deploy, particularly in smaller networks, and provides immediate value.
- Skybox: High – Skybox is complex to deploy and requires significant expertise and dedicated resources.
- Algosec: Medium – Algosec is somewhat easier to deploy but may be limited by its static nature and reliance on archived snapshots.
Workload on security/network teams
- Tufin: Medium – Tufin provides near real-time reporting and alerting, which can ease the workload if the network team is well-trained.
- Skybox: Low🏆 – Skybox excels in vulnerability management, integrating well with scanning tools, significantly reducing team workload.
- Algosec: High – The large volume of reports generated by Algosec can overwhelm teams, adding to their workload.
Ticketing tools integration
- Tufin: Wide Variety🏆 – Tufin integrates well with various ticketing tools, supporting automated deployment processes.
- Skybox: Narrow Variety – Skybox has no integration with ticketing tools.
- Algosec: Wide Variety- Algosec integrates well with various ticketing tools.
Detection of risky situations
- Tufin: High🏆 – Tufin provides almost instant notifications when risky scenarios are detected, ensuring high security.
- Skybox: High – Skybox’s strong vulnerability management capabilities contribute to effective risk detection.
- Algosec: Medium – Algosec is less effective in detecting risky situations, focusing more on reporting.
Automation support
- Tufin: High🏆 – Tufin supports automation, particularly in rule deployment and workflow management.
- Skybox: Med – Skybox offers automation in vulnerability management but less in rule deployment.
- Algosec: Low – Algosec is less dynamic and offers limited automation support.
Reporting
- Tufin: Medium – Tufin offers real-time reports but lacks customization options.
- Skybox: High – Skybox provides strong reporting, especially in large-scale environments.
- Algosec: High🏆 – Algosec excels in reporting with pre-built templates, making it the best in this category.
Features & integrations
One of the fundamental aspects to evaluate when selecting a firewall audit software vendor is the extent of integration it offers with other crucial cybersecurity and IT management systems such as ticketing systems.
Users should look for features such as comprehensive rule analysis, automated suggestions for rule optimization, integration with compliance requirements, and robust reporting capabilities. Common features include basic rule analysis and compliance reporting, while differentiated features like best-practice reports and built-in ticketing systems set it apart. Here are some other key integration points to consider:
1. Ticketing integration
Table 5. Ticketing system integrations
| Software | Ticketing Integrations | ||
|---|---|---|---|
| Tufin Orchestration Suite | BMC, ServiceNow, HP ServiceManager, RSA, Puppet, CA Technologies | ||
| AlgoSec Firewall Analyzer | ServiceNow, Jira | ||
| Qualys Enterprise TruRisk Platform | ServiceNow, RSA, CA Technologies | ||
| FireMon Security Manager | BMC, ServiceNow, Jira, Accenture, REDSEAL | ||
| Palo Alto Network Panorama | VMware NSX, ServiceNow, Aruba, Any REST API | ||
| SolarWinds Network Configuration | SolarWinds Web Help Desk | ||
| AWS Firewall Manager | AWS Service Catalog | ||
| Cisco Defense Orchestrator | – | ||
| Titania Nipper | ServiceNow | ||
| Skybox Firewall Assurance | – | ||
| Network Perception View | ServiceNow |
Integrating a ticketing system with firewall audit software is crucial for effective IT change management and streamlined workflow processes. By leveraging tools integrated with IT ticketing system, organizations can automatically manage tickets, ensure appropriate distribution, and escalate issues as needed, thereby eliminating the reliance on spreadsheets and reducing the risk of tickets getting lost in the shuffle.
For more information, read: ITSM Tools.
2. Deployment
The deployment model of a firewall audit tool is a crucial consideration based on the organization’s specific needs, infrastructure, and security requirements. Vendors should offer flexibility in deployment options to accommodate diverse organizational structures:
On-premises deployment: Some organizations may prefer the firewall audit tool deployed on-premises, providing them full control over the tool’s infrastructure and data.
Cloud-based deployment: Cloud-based deployment offers scalability, flexibility, and accessibility, allowing organizations to leverage the advantages of cloud infrastructure.
Hybrid deployment: Organizations leverage a mix of on-premises resources and cloud services in a hybrid deployment model, creating a unified and interconnected firewall audit system.
3. Real-time data
The ability to provide real-time data is a key criterion for evaluating the effectiveness of a firewall audit tool. Organizations need timely and accurate information to respond promptly to security threats. This capability enhances overall security risk by ensuring timely detection and mitigation of potential threats.
4. Firewall integration
Specific firewall brands and models, as not all firewalls may be supported, particularly older hardware with outdated OS versions, in addition to some open source alternatives.. Users should verify compatibility with specific firewall brands and models, as not all firewalls may be supported, particularly older hardware with outdated OS versions.
For detailed information, read firewall integration.
Market presence criteria explained
1. Number of Reviews
The volume of reviews available for a vendor or a particular firewall auditing tool can provide a good view of its user size.
2. User Ratings
User ratings provide a quantitative measure of customer satisfaction with a product or service. User ratings can reflect the tool’s efficiency in firewall security auditing, managing firewall rules compliance, and its ability to provide detailed risk assessments to prevent security incidents.
3. Number of employees
The size of a company’s workforce can indicate its financial stability, capacity for innovation, and ability to serve customers effectively. Larger companies often have more resources to invest in research and development, customer support, and marketing, which can contribute to their market presence. In network security, where specific support for firewall configurations, rule auditing, and network traffic monitoring is vital, the company’s size matters.
Key factors for effective firewall integration
Organizations must carefully consider several key factors to ensure successful and effective integration before embarking on firewall integration initiatives. According to NIST4 , organizations should keep four considerations in mind regarding firewall integrations.
1. Compatibility with network infrastructure
One of the foremost considerations in firewall integration is assessing whether the firewall requires specific hardware components to seamlessly integrate within the organization’s network infrastructure. This includes evaluating factors such as power capabilities, network interface card (NIC) compatibility, backup device requirements, and other hardware specifications. Ensuring compatibility with existing network hardware is essential to prevent compatibility issues and optimize firewall performance.
2. Integration with existing security devices
Another critical consideration is determining whether the firewall needs to be compatible with other devices on the network that provide security or other services. This includes evaluating compatibility with intrusion detection systems (IDS), intrusion prevention systems (IPS), network access control (NAC) solutions, and other security appliances. Integration with existing security devices ensures comprehensive threat detection and defense capabilities across the network.
3. Logging interoperability
Effective firewall integration also entails evaluating whether the firewall’s logging capabilities seamlessly interoperate with existing log management systems. Centralized log management is crucial for monitoring security events, analyzing network traffic, and detecting potential threats. Ensuring logging interoperability enables organizations to consolidate security event data and streamline incident response processes.
4. Network impact and changes
Installing a firewall as part of integration efforts may necessitate changes to other areas of the network. Organizations must assess the potential impact of firewall deployment on network traffic, access controls, and overall network performance. Planning for network changes, conducting impact assessments, and implementing necessary adjustments (proper change management life-cycle) are vital to minimize disruptions and ensure smooth firewall integration as well as business continuity.
Resources for effective firewall integration
To enhance firewall integration effectiveness and address potential challenges, organizations can tap into three main resources and strategies:
1. Vendor documentation and community support
Consult vendor resources, including comprehensive documentation, dedicated support services, and customer community support. These resources offer valuable insights into firewall rules, integration protocols, and best practices, aiding in seamless deployment and management.
2. Local partnership support
Establish partnerships with local service providers to address on-site challenges promptly. These partners ensure swift, effective support for hardware issues along with software support, critical patching or updating its operating system, configuration adjustments, and other critical needs, minimizing downtime and enhancing integration success.
3. Third-party integrators and consultants
Collaborate with experienced third-party integrators or consultants specializing in firewall integration. These experts provide in-depth knowledge, tailored solutions, and ongoing support, ensuring optimal configuration and performance.
4. Training and certification programs
Implement training and certification initiatives for IT teams involved in integration and management. These programs equip staff with the necessary skills, and knowledge of security protocols, and compliance standards, empowering them to navigate complex integration scenarios effectively.
FAQ
Why use a firewall audit tool?
Using firewall audit software is crucial in ensuring network security and operational efficiency. These tools provide a systematic and thorough examination of firewall configurations and rules, which is essential for several reasons:
Enhanced security: Firewall audit software identifies vulnerabilities and misconfigurations that could be exploited by cyber threats.
Compliance assurance: It helps ensure compliance with various regulatory standards by maintaining proper firewall configurations.
Optimized performance: Regular audits can optimize firewall performance by removing unnecessary or outdated rules, improving overall network efficiency.
In conclusion, selecting the right firewall audit software is crucial for ensuring a robust security posture in an increasingly automated world. By considering the key criteria and understanding the offerings of major vendors, businesses can effectively protect their network infrastructures against potential threats and maintain compliance with regulatory mandates.
What should a buyer expect from firewall audit software?
When evaluating firewall audit software, a buyer should expect several key features.
-First, the software must ensure visibility into all firewall rules, as unmanaged or randomly deployed rules can expose networks to significant risks.
-The software should detect and prevent overly permissive or dangerous rules that allow harmful traffic between the internet and internal networks.
-It should also provide detailed logging and reporting for internal or external audits, including who implemented rules, when, and why, to meet compliance requirements.
-Additionally, the software should help identify misconfigurations or policy violations, making rules clearer and more stable.
-Ultimately, firewall audit software enhances security by maintaining proper control and transparency over firewall configurations.
Further reading
- Top Firewall Management Tools in 2024: Analysis & Comparison
- Guide to Effective Firewall Auditing
- Key Components of Firewall Compliance
If you need further help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. Tufin Orchestration Suite Reviews 2025: Details, Pricing, & Features | G2.
- 2. Excellent firewall | TrustRadius. TrustRadius
- 3. Security Event Manager Pricing, Alternatives & More 2025 | Capterra.
- 4. NIST. Guidelines on Firewalls and Firewall Policy. Accessed: 18/April/2024.



Comments
Your email address will not be published. All fields are required.