Network Visibility in 2024: 4 Benefits & Challenges
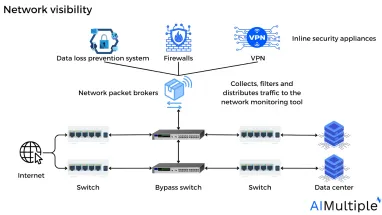
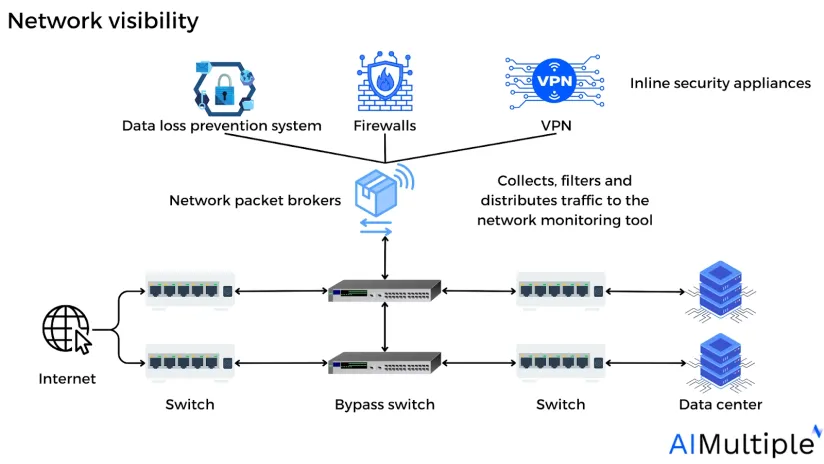
Figure: Network visibility
Companies now struggle to gain network visibility across increasingly complicated hybrid networks and cloud architecture, especially when combined with remote environments, since only ~35% of companies think their visibility strategy is successful.1
With ~90% of them saying it is critical to establish an end-to-end visibility framework that covers both on-premises and cloud, companies need to gain insight into network visibility techniques.2
This post discusses the challenges and benefits of network visibility and how companies may practice a controllable network visibility approach that improves security and digital monitoring.
What is network visibility?
Network visibility is a method to observe and comprehend the network traffic information that flows through network devices, software, and protocols.
To gain granular network perception, companies commonly use a mix of hardware and software technologies, such as network taps, probes, and analytics platforms. These tools can give an in-depth overview of network traffic, including detailed data insights provided by network components.
Network visibility tools are classified into numerous kinds, such as:
Network packet analyzers: Collect and analyze network traffic by reading packets and evaluating the data they carry.
Network traffic analyzers (NTA): Collects and analyzes network flow data to give insight into traffic volume and type and network device performance.
Network performance monitoring tools: Monitor and evaluate network performance to discover and rectify issues that may have an impact on the network’s overall performance including excessive latency, lost connections, and low performance.
Why is network visibility important?
Network visibility is becoming a growing critical issue as the volume and diversity of data transported by company networks expand. Companies are responsible for all information that goes via their network. As the data grows more complicated, network monitoring grows more challenging, and the risks increase.
The more the network is sourced and managed independently, the more inefficient administrators become when attempting to maintain network policies and adopt new solutions. This reduces their capacity to monitor and react quickly to network issues.
However, the most significant reason to emphasize network visibility is the influence on cyber security. All it takes is one attacker to locate a vulnerability and inflict havoc on the entire network. With ~70% of data breaches involving major corporate victims, enterprises are a potential target of hackers.3
Thus, network visibility can help companies better understand the traffic patterns on their networks, which can then be used to enhance network reliability, privacy, and performance.
Read more: Network audit, cybersecurity risk management, security risk assessment.
4 benefits of network visibility
1. Enhance security and quicker threat detection
Network visibility provides an overview of your typical operation which makes it significantly simpler to detect and halt malicious activity (e.g. a high rate of files leaving the network) as it occurs.
For example, numerous contemporary technologies—including IoT devices like linked speakers, printers, and even some appliances—cannot be secured in the same way that smartphones and laptops can. IoT devices typically lack the technical capabilities to execute endpoint security solutions or applications.
However, through tracking these devices at the network level, companies may identify threats or weaknesses and strengthen your protection. Network visibility might alert the user when an IoT device begins transferring large amounts of data from the company’s network, indicating a cyber attack.
Figure: Displaying network traffic, isolating the host and conversation
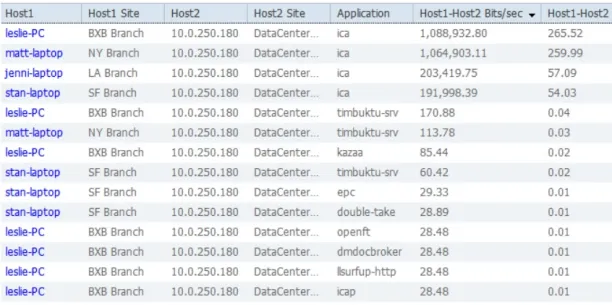
Source: Cisco4
Read more: Top 10 insider threat management software,
2. Reduce vulnerabilities
~90% of cybersecurity executives were concerned about outsiders in their environment.5
Strong network visibility may reveal weaknesses while reducing blind spots throughout the entire company network, especially for companies that continue to deploy new apps, software, and tools, all of which might introduce new vulnerabilities.
With network monitoring tools network visibility agents may generate a wide range of metrics based on TCP (transportation control protocol) traffic monitored. The metric browser provides advanced metrics for network objects of interest (PIE (performance impacting events), slow calls, stalls, errors, and network errors). Using time-based charts, you may notice and evaluate certain behaviors:
Network visibility metricsFigure: Network visibility metrics
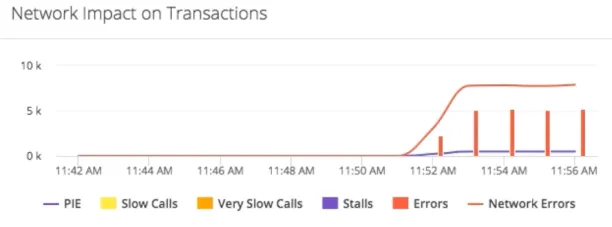
Source: Cisco6
3. Improve network performance
Network visibility enables administrators to recognize the types and volume of traffic passing across the network, which helps administrators discover and address concerns that may be creating slowdowns or other performance difficulties which can assist enhance the network’s performance.
Some of the network performance metrics include:
- Device health
- Device availability
- Bandwidth usage
- Latency and packet loss
- Network interface
- Network bottlenecks
- Other device-specific metrics
Figure: Network availability monitoring by response time
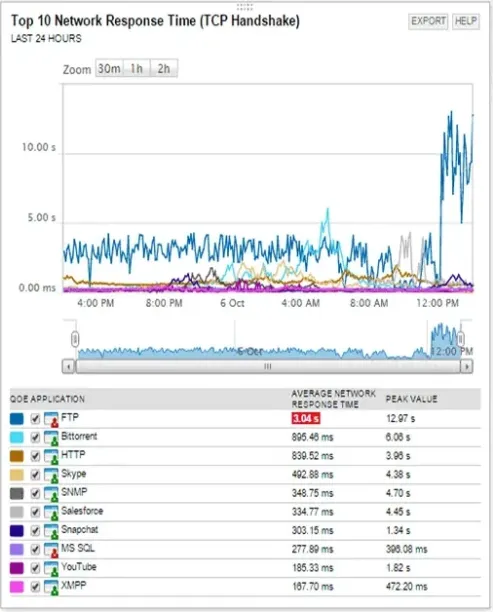
Source: SOLARWINDS7
Read more: 10 network performance best practices to improve network optimization, top 4 Solarwinds competitors.
4. Adhere to compliance
Network visibility may assist ensure that a company meets compliance standards by giving insight into the sorts of data being sent and the security policies in place.
Several companies (e.g. federal government agencies, contractors, or subcontractors who manage or process government data or operate a federal system) are obliged to follow a variety of rules and standards, such as the NIST Cybersecurity Framework or global regulations such as HIPAA and PCI DSS.
NIST: NIST issued a paper titled “Security and Privacy Controls for Information Systems and Organizations.” In this paper, NIST primarily suggests that enterprises monitor their systems to identify:
1. Attacks and signs of possible attacks
2. Unauthorized connections (local, network, and remote)8
HIPAA: The HIPAA Privacy Rule is a nationwide standard established by the U.S. Department of Health and Human Services (HHS) to secure specific health information that is stored or transferred electronically.9
PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) is a generally acknowledged set of rules and procedures designed to improve the security of credit, debit, and cash card operations while also protecting cardholders from the exploitation of their sensitive data.10
Read more: Top 10 network security policy management solutions (NSPM).
Challenges of network visibility
Network visibility concerns include responding to the rising speed and scale of modern corporate networks while maintaining performance. The following are some particular, common problems companies encounter with preserving network visibility:
1. Remote work
About half of U.S. employees state that they have worked remotely using company networks in off-site settings.11Virtual private networks (VPNs) allow workers to operate safely from an off-site location, however, they lack the visibility that on-premises employee technology provides. The other connection method that companies use on off-site locations is SD-WAN. Companies allow mobile users to use SD-WAN to connect to the cloud without using a VPN, resulting in less visibility.
2. Encrypted data
Encrypted data may have a substantial influence on network traffic visibility since it makes analyzing the network more difficult.
3. Limitations of visibility tools
Visibility is often maintained and monitored using a variety of network visibility technologies, each with its own set of goals and restrictions. Conventional network switches, for instance, only provide a few switching port analyzer (SPAN) ports. Replacing the physical network design may also reduce the effectiveness of old tools, which may lack the computing capability to handle increased network bandwidths. Network performance monitoring systems might get overwhelmed when presented with data that they are unable to comprehend or with an excessive amount of data.
4. Complex networks
Modern networks include a variety of network monitoring and analysis technologies such as firewalls, routers, data loss prevention (DLP), and anti-malware applications. As networks get more sophisticated and have more network segments to care for, it becomes increasingly challenging to connect these pieces efficiently while preserving performance and making all data available.
Network visibility tools
Network visibility tools may help companies monitor network performance, traffic, large-scale analytics, and controlled resources.
The following are some frequently used network visibility tools:
Network packet brokers (NPBs) — are network monitoring tools that gather data from several sources and distribute it over the network operations, application operations, and security administrators. They reduce the pressure on network security technologies like intrusion detection systems (IDS), which may be overloaded by large volumes of data. They use context-aware processing techniques to arrange and send data to security and monitoring systems. They improve the information acquired by other security systems so that they can make more educated decisions.
Figure: Possible deployment scenarios for network packet broker (NPB)
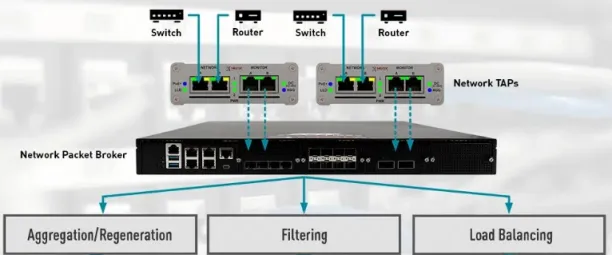
Source: Neox Networks12
Software-defined wide-area networking (SD-WAN) is a computerized, programmatic method for controlling business network connections. It transforms software-defined networking (SDN) into a program that allows companies to move visibility away from traditional appliance-centric approaches and toward software-defined approaches.
Network traffic flows through a managed cloud platform rather than on-premises equipment, resulting in improved performance and security by decreasing network complexity and eliminating the inherent limits of physical hardware such as conventional firewalls. It establishes a secure connection to cloud apps while sustaining visibility.
SD-WAN enables companies to:
- Centralize control over your network administration across security, traffic, and applications.
- Reduce WAN OpEx, CapEx, and overall cost of ownership.
- Enable end-to-end encryption for any corporate data that travels over networks.
- Improve network mobility by using any method of transportation.
- Allows for automatic provisioning and adjustments to premium network services such as VPNs, firewalls, security, WAN optimization, and application delivery control.
- Reduce network complexity by using a single platform for network managers.
Figure: SD-WAN framework
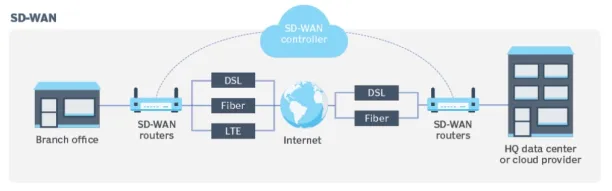
Source: Tech Target13
Network TAPs: A network tap, also known as a bypass switch, is a hardware device that examines local network activity. A tap is often a specialized hardware device that allows companies to access data flowing over a computer network. It creates a duplicate of the traffic and transmits it to another tool on the network without interfering with its flow.
Figure: TAP diagram showing logical flow
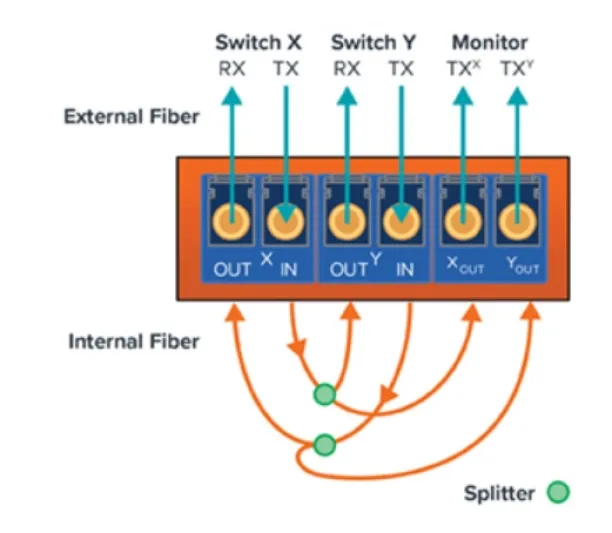
Source: Gigamon 14
Techniques for enhancing network control
Implementing quality of service (QoS): Quality of service (QoS) is a critical component of network control. It enables users to prioritize certain kinds of traffic over others, ensuring that vital applications like audio and video receive more priority and bandwidth.
Network segmentation: Network segmentation is a method that separates a network into many segments, each of which operates as its small network. This enables network users to manage the flow of network data between subnets using granular rules. Organizations utilize segmentation to improve monitoring, increase performance, identify technical faults, and, most significantly, strengthen security.
Read more: Microsegmentation, top 10 micro segmentation tools.
Network automation: Network automation refers to the process of automating the configuration, management, testing, deployment, and operation of physical and virtual devices in a network. Everyday network duties and operations are automated, and repetitive procedures are handled and maintained automatically, resulting in increased network availability.
Read more: IT automation.
Network audit: A network audit is the process of inspecting and assessing the performance and security of a network’s structure. It entails evaluating the network’s many components, including hardware, software, security protocols, and user access, to discover possible issues, security concerns, and places for improvement.
The process includes examining the network’s design, configuration, and protocols to discover potential vulnerabilities and problems that may affect network performance and security.
Read more: Vulnerability scanning automation.
Monitoring and analytics: Network monitoring & analytics helps network operators and managers gain a better knowledge of their networks. It enables the operator to collect useful continuous data, filter out noise, evaluate patterns, and forecast future behavior by collecting data from several devices, storing important time series data, and correlating that data in real time.
For guidance on choosing the right tool or service, check out our data-driven lists of software-defined perimeter (SDP) software and zero trust networking software.
Further reading
- Top 10 Microsegmentation Tools
- Microsegmentation: What is it? Benefits & Challenges
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. ”Network Visibility Architecture for the Hybrid, Multi-Cloud Enterprise“. (PDF). EMA. June, 2022. Retrieved January 26, 2024.
- 2. ”Network Visibility Architecture for the Hybrid, Multi-Cloud Enterprise“. (PDF). EMA. June, 2022. Retrieved January 26, 2024.
- 3. ”2023 Data Breach Investigations Report“. (PDF). Verizon. 2023. Retrieved January 29, 2024.
- 4. ”Network Visibility in the Data Center: Best Practices for Staying Ahead” (PDF). Cisco. 2014. Retrieved January 29, 2024.
- 5. ”Global Cybersecurity Outlook 2022”. (PDF). World Economic Forum. January, 2022. Retrieved January 26, 2024.
- 6. ”Network Visibility Overview”. Cisco. 2024. Retrieved January 26, 2024.
- 7. ”Network Availability Monitoring”. SOLARWINDS. 2024. Retrieved January 29, 2024.
- 8. ”Security and Privacy Controls for Information Systems and Organizations”. (PDF). NIST. 2024. Retrieved January 29, 2024.
- 9. ”U.S. Department of Health and Human Services”. HIPAA. 2024. Retrieved January 29, 2024.
- 10. ”PCI Security Standards Council”. PCI DSS. 2024. Retrieved January 29, 2024.
- 11. ”Remote Work Stable at Higher Rate Post-Pandemic“. Gallup. September 15, 2023. Retrieved January 26, 2024.
- 12. ”Next Generation Network Packet Brokers”. Neox Networks. 2024. Retrieved January 26, 2024.
- 13. ”What is SD-WAN? Software-defined WAN explained.” Tech Target. March, 2023. Retrieved January 26, 2024.
- 14. ”Understanding Network TAPs – The First Step to Visibility” Gigamon. 2024. Retrieved January 26, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.