Mandatory access control (MAC) is a security method that limits individuals’ capacity to grant or deny access to assets in a system.1
Mandatory access control helps organizations by enforcing strict security policies on access to resources. MAC assigns a unique identification to each network interface controller (NIC) and limits its role as a network address for intra-network communication. This helps protect critical data and limit cyber attacks.
Why is mandatory access control (MAC) important?
MAC protocol is an essential tool for controlling data access. It is frequently employed to secure information (private, sensitive, confidential, or restricted data) that might cause harm to the company in case of a cyber attack or data loss..
Here are several examples:
- Operational technology.
- Partnership or merger and acquisition planning.
- Intellectual property.
- Financial details and transactions.
- Medical data.
- Customer data.
Read more: Data loss prevention, network security software.
How does mandatory access control (MAC) work?
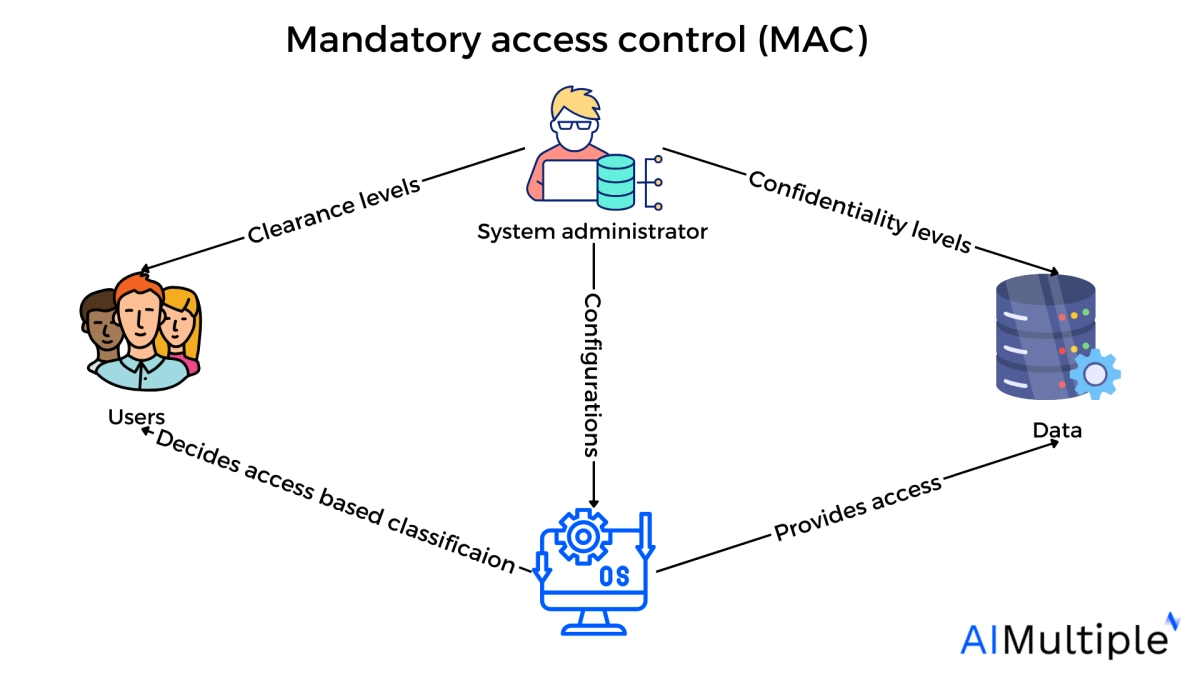
Mandatory access control enforces a set of security rules, or labels, that govern which users or systems have access to specified resources, access is allowed on a need-to-know basis.
These rules or security labels are established by an administrator and implemented by the system, limiting the individual capacity of resource owners to provide or prohibit access to file objects.
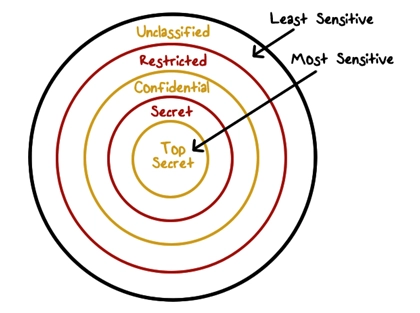
Security teams or administrators determine whether a resource is sensitive or not by assigning it a security level, such as “restricted,” “confidential,” “secret,” or “top secret,” and categorizing it as “users group XZ” or “sales department”.
Figure: Examples of labels/MAC
Read more: Role-based access control (RBAC), network segmentation, microsegmentation, network security statistics.
Mandatory access control labels
A security label consists of the following two components: Label = classification or compartment
- Classification, also known as a level: Classification represents a hierarchical degree of security. When used for employees, classification provides a level of trust. When used for data, a classification indicates the level of security.
- Compartments, also known as categories: A compartment denotes a grouping, such as a team, department, task, department, or topic. A classification does not have to include a compartment.
Figure: Mandatory access control labels
Source: Microsoft2
While assigning security classification to compartments, the categories used by the U.S. government include “top secret, secret, confidential, and unclassified”.
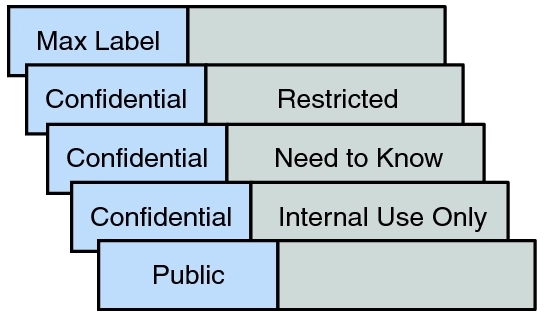
Nevertheless, industry categories are not as standard. An administrator can create unique categories such as “max label, confidential, and public” (see Figure 3). The terms on the left represent classifications. The terms on the right represent compartments.
The figure illustrates the Confidential classification with three exclusive compartments and five labels (Public and Max Label lack compartments).
- L1 = (max label)
- L2 = (confidential, {restricted, need to know, internal use only})
- L3 = (public)
Figure: Sensitivity labels for mandatory access control
Source: Oracle3
When a sensitivity label is applied to company resources (message, meeting invitation, or files), any protection settings established for that label apply to the content, and the MAC system determines how data will be limited based on the sensitivity label.
Case example: User1 from the sales department might have permission to view data within an object (also called resource) labeled “restricted to sales department” however user2 from finance may not. Similarly, user2 may have access to the resource labeled “finance project confidential,” but user1 may not.
Figure: An applied sensitivity label from the window bar on Excel
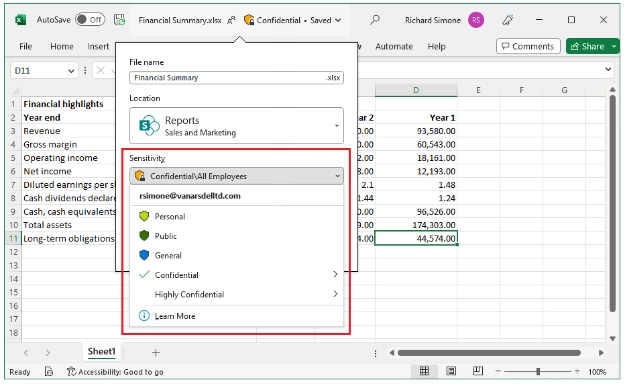
Source: Microsoft4
How to implement mandatory access control (MAC)
1. Establish common goals
Coordinate with decision-makers to foster an access control strategy.
Productivity: Provide employees with approved access to the applications and data they require to achieve their objectives—right when they demand it.
Security: Defend critical records and resources while reducing user access burden with reactive policies and rules that notify in real-time as risks occur.
Self-service: Assign identity forms, password changes, security auditing, and control access queries to save time and effort.
Read more: Automated security risk assessment.
2. Select a solution
Choose an MAC system that allows you to protect your data while also providing a positive end-user experience. The ideal should deliver first-rate support to both the users and the IT staff, from enabling remote access to staff members to reducing the workload for executives.
3. Establish policies
After you’ve deployed your selected solution, decide who has access to your resources, which ones they have access to, and under what terms. Access control lists can be created to give access, confine access via temporary controls, or even prohibit access—depending on your company’s requirements.
A few to ask along the journey may include:
- Which users, groups, positions, or workload profiles will be covered or excluded by the policy?
- Which industries does this policy apply to?
- Which devices and software does this policy apply to?
- Which user behaviors will be exposed to this policy?
Read more: Network policy management, top 10 network security policy management (NSPM) solutions.
Best practices of mandatory access control (MAC)
MAC is rarely used in small business or personal use. Nevertheless, it has confident essential use cases:
- Government, military, and intelligence institutions use MAC to impose tight clearance levels. Government agencies handle vast amounts of sensitive data that must be kept secure, however, it must also be available to employees. MAC makes this feasible. Administrators may define categories and securely connect people to the secret data they need.
- Businesses and other private organizations use MAC to protect consumer data. For example, MAC enables insurance and banking businesses to limit the number of people who may access financial data. This lowers the likelihood of data breaches, insider threats, cyber-attacks, and reputational harm.
Read more: Top 10 insider threat management software.
Benefits of mandatory access control (MAC)
Centralized control: MAC enables security managers to set and administer access policies and rules centrally, ensuring that sensitive data is carefully controlled and all access decisions adhere to defined security regulations.
Fine-grained control: MAC limits access to specified resources or activities depending on a variety of factors, including user identification, role, and location.
Improved security: MAC executes limitations by leveraging a computer system (rather than human judgments), this minimizes human error that can cause unauthorized access to critical information and lowers the chance of security breaches.
Enhanced compliance: MAC assists companies in meeting regulatory and compliance obligations by using a systematic and auditable strategy.
Challenges
Complexity: It can be challenging to administer a large number of systems and users since the administrator is responsible for configuring and maintaining multiple aspects of access policies. For the same reason, MAC is unsuitable for multi-user programs, such as web-based apps.
Productivity: MAC requires users to give their credentials every time they need to access data. This may be a serious issue when utilizing operating systems such as Linux or Windows, since users cannot update their access permissions and only administrators may do so using the security kernel. Limiting access in this way slows down data flows and may decrease productivity.
Scalability: MAC does not scale automatically. New users might get overwhelmed with continual updates to objects and account setups.
Sustainability: Manual setting of security levels and clearances necessitates constant monitoring from administrators.
Other access control types
Discretionary access control (DAC): In DAC models, each object in an encrypted data framework has an owner, who grants access to users at their own choice. DAC grants case-by-case authority over resources.
Role-Based Access Control (RBAC): RBAC models give access rights based on predetermined roles for a set of people inside an organization. These positions are based on employment duties, responsibilities, and organizational roles.
Attribute-based access control (ABAC): ABAC models provide for flexible access depending on a mix of qualities and environmental variables, such as time and location. ABAC is the most granular access control approach, which reduces the number of role assignments.
Note: These systems aren’t mutually exclusive. It may make sense to apply DAC throughout the company, followed by MAC or RBAC. For example, an organization may use the Linux security kernel to enforce MAC while accessing sensitive resources. However, users can access the remainder of the network via simple discretionary controls.
Mandatory access control (MAC) vs discretionary access control (DAC)
Authorization: In DAC, the resource’s owner has permission to determine who may access it. In MAC, a central authority, typically the system administrator, determines the access decision.
Flexibility: DAC is more versatile than MAC since it allows administrators to provide authorization for access to anybody they choose, and users can share resources. In contrast, MAC is rigid since access is regulated by predefined rules and regulations established by the central authority.
Security: MAC is regarded as more secure than DAC since it allows for greater control over who has access to resources. MAC maintains a rigorous hierarchy of security authorizations, and only individuals with the requisite permission are permitted access to the resource. In contrast, DAC is more sensitive to insider attacks and human mistakes since owners do not always execute the optimal access selections.
Complexity: MAC is more difficult than DAC since it needs a central authority to establish and monitor access control rules. DAC is easier since owners may make access selections on an individual basis.
Thus, the decision between MAC and DAC is based on the security needs of the company or network. In high-security workplaces (e.g. governmental or corporate settings), MAC may be the better option, however, in more adaptable and creative contexts, DAC may be more suited.
Further reading
External Links
- 1. Implementation of Mandatory Access Control in Distributed Systems | Automatic Control and Computer Sciences . Pleiades Publishing
- 2. Learn about sensitivity labels | Microsoft Learn.
- 3. Mandatory Access Control - Trusted Extensions User's Guide.
- 4. Learn about sensitivity labels | Microsoft Learn.



Comments
Your email address will not be published. All fields are required.