Data privacy

UTM vs NGFW in 2024: Which One to Choose?
Figure 1: Unified threat management (UTM) vs next-generation firewalls (NGFW) Network security is imperative for all organizations since 45% of experts see cyber incidents as the most feared source of commercial interruption.

Phishing vs Whaling in 2024: 6 Key Differences
Phishing attacks are rising, and there’s no sign they’ll stop anytime soon. In 2023, ~300,000 phishing attack incidents were reported to the Internet Crime Complaint Center (IC3) in the U.S., with a 100+% increase compared to the incidents reported (114, 702) in 2019.

Top 4 Microsoft System Center Alternatives in 2024
Network security statistics show that data breaches exposed over 6 million data records globally during the first quarter of 2023. Companies that deal with complex security rules and firewall assessment methods, each with different requirements, may find it difficult to manage network security policies that will prevent the IT environment from data breaches.

Top 8 Next-Generation Firewall (NGFW) Features in 2024
The network security statistics show that the number of incidents in North America increased from 23% of all cases in 2021 to 25% in 2022. The U.S. accounted for 80% of the North American region’s cybercrime. Recent security incidents in the U.S.
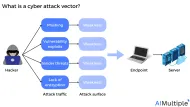
Most Common Cyber Attack Vectors in 2024 & How to Prevent Them
The cyber attack disruption levels have surged by 200% from 2019 to 2024, compared to a 4% increase from 2011 to 2016. The rise of cyber attacks is alarming since damage to information systems can harm processes, assets, individuals, and organizations by exploiting vulnerabilities that violate information security.

Third-Party Cyber Risk Management in 2024: 6 Best Practices
Organizations struggle to create resilience against third-party risks since 45% of them reported third-party-related interruptions in their business operations during the past two years, despite the ~15% growth in third-party cyber risk management (TPCRM) in 2023. Organizations need to improve their ability to manage third-party cybersecurity risk.

Data Breach Incident Response in 2024: 5-Step Methodology
Organizations that have an incident response strategy detect data breaches 54 days faster than those without. Building a data breach incident response team and plan can help organizations maintain strong network visibility, enabling them to identify breaches and insider threats quickly while preventing cybersecurity risks that may cause security incidents.
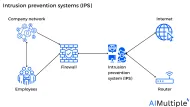
Intrusion Prevention in 2024: How does it work? & 3 Methods
The number of outbreak alerts issued in 2023 increased by 35% over 2022, indicating a surge in cyber threats across multiple sectors. Intrusion prevention tools help network security teams autonomously detect and prevent potential threats including malicious activity or policy violations.
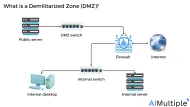
DMZ Network Security in 2024: How it Works & 3 Benefits
The number of data breaches in the U.S. was more than 1800 in 2022 and 422+ million people got exposed to data compromises that year. Implementing data isolation policies is crucial to enhance network visibility and prevent the most common cyber attack vectors.

Prisma Cloud Alternatives in 2024 based on 2,000+ Reviews
With increasing numbers of remote workers migrating to off-site settings using cloud applications, operational workloads are stacking on networks, and the conventional network segmentation approach of building a security perimeter is no longer effective against evolving risks that may break network boundaries.