Phishing vs Whaling in 2024: 6 Key Differences
Phishing attacks are rising, and there’s no sign they’ll stop anytime soon. In 2023, ~300,000 phishing attack incidents were reported to the Internet Crime Complaint Center (IC3) in the U.S., with a 100+% increase compared to the incidents reported (114, 702) in 2019.1
“Whaling,” or “whale phishing,” is a special phishing attack that sends fake emails, texts, or phone calls to senior company executives. The messages are skillfully crafted to persuade the target to disclose private information or to permit cybercriminals to accept significant payments.
Organizations may learn more about phishing and whaling attacks, and identify early indicators to protect company executives and resources. This article examines the similarities and differences between phishing and whaling attacks and highlights how to prevent, detect, and control them.
Phishing vs whaling
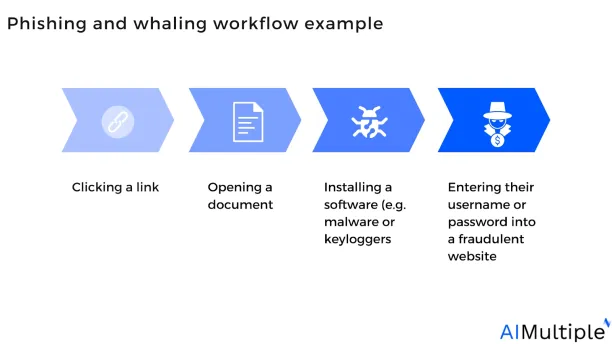
Figure 1: Phishing and whaling workflow example
A whaling attack is a phishing attack but with higher-value targets. Phishing attacks can target anybody, while whaling attacks are more focused on who they target, concentrating on a single high-level executive or advocate rather than a large population of victims.
Table 1: Phishing vs whaling
| Parameter | Phishing | Whaling |
|---|---|---|
| Target | The target is usually an organization or employees. | The target is a top executive who is in direct
contact with the organization’s CEO and high-value customers.
|
| Value | Phishing targets are high-yield. In personalized attacks, victims willingly compromise
extra-sensitive data. | Whaling yields immediate high-value results, considering the ranking of the
people involved. It may leak trade secrets.
|
| Example | An email stating that a specific vendor-related payment has failed
due to incomplete details, and a fake link is shared to retry the payment process.
| Sending a carefully crafted email that appears to be from
the organization’s CEO asking executives to share employee payroll details. |
Read more: Most common cyber attack vectors.
1. Phishing
Phishing is defined as any false messages, emails, or calls intended to fool people into installing malware, disclosing personal data, or giving money to hackers.
For example, consider a company employee who received a phishing attempt. The employee will receive a form message that looks to be from a company, presents a frequent or plausible issue, and requires immediate action, such as “Your account has been blocked, please use the link provided below to send information regarding your company”. The employee who visits the link will be sent to a fraudulent website that may steal their payment information.
Figure 2: Example of a phishing scam
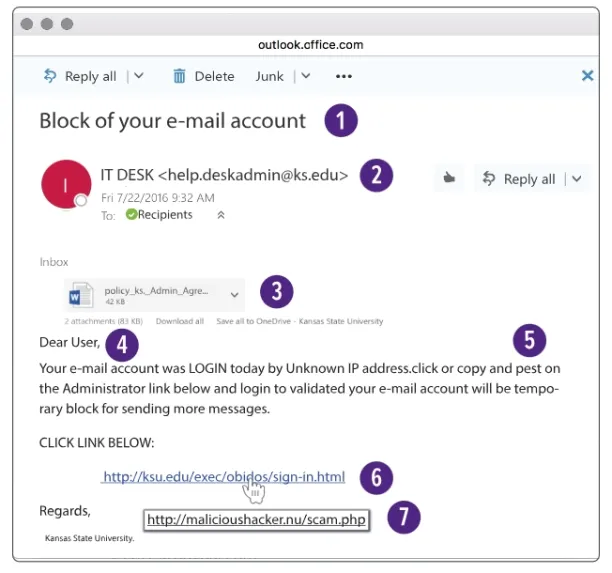
Source: Kansas State University2
- Urgent in tone.
- The sender’s name does not match the email address.
- Unexpected attachments.
- Generic greetings.
- Errors in spelling, grammar, and syntax.
- Fraudulent web addresses masquerading as authentic.
- The destination and link text do not match.
Spear phishing: Spear phishing refers to targeted phishing attacks that focus on a single individual or group of people within a company. These attacks are usually launched against mid-level executives who may authorize payment transactions or data transfers, such as accounts receivable executives and HR directors.
2. Whaling: phishing for the highest-value targets
Whaling, also known as CEO fraud or executive phishing, is a cyber threat that targets an organization’s high-profile employees. These assaults are specifically meant to mislead top executives, such as CEOs and CFOs, into disclosing sensitive data. The phrase whaling refers to the high status of these targets, who have extensive access to important data and financial assets.
A whaling attack seeks to persuade top executives inside a business to adopt measures that benefit the attacker for monetary gain, data loss, or other violent objectives. This may include:
- Transferring significant amounts of business funds to the attacker’s counterfeit accounts.
- Sharing private or sensitive information such as trade secrets, customer data, or usernames and passwords.
- Providing access to secure networks, systems, or databases.
- Accepting contracts or changing policies are examples of unlawful activities that might jeopardize the organization’s cybersecurity or operations.
The 3 major steps of whaling attacks are as follows:
1. Establishing the objective
The majority of whaling attacks are designed to deceive a high-ranking official into approving or directing a wire transfer to a financial account to steal substantial quantities of money from an organization. However, whaling attacks may also aim to achieve the following:
- Obtaining confidential data — Some attackers may aim to steal private data, such as payroll records for employees or the financial information of individual customers. Fraud targeting to obtain confidential data can also target business secrets, patents, and other private data.
- Stealing login information — Some cybercriminals will first launch an initial whale phishing attempt to obtain email credentials, and then begin a second whale phishing assault from an email account they have taken over to steal login information.
- Spreading malicious software — A small percentage of whale phishing attempts aim to deceive victims into opening malicious file attachments or visiting malicious websites to spread malicious software.
2. Selecting and analyzing the targets and senders
Whaling scammers conduct extensive research on their targets, senders, and the companies where they work to make the e-mails or messages they send seem genuine and persuasive. For example:
- A quote and payment request from the manufacturing partner’s CEO, for instance, could be sent by a hacker to the target business’s CFO to process payments.
- A cybercriminal wishing to obtain employee information could pretend to be the CFO and ask the vice president of HR for payroll details.
3. Executing the whaling attack
While launching the attack, the fraudster will send a convincing message (e.g. a message containing references to a particular endeavor or agreement).
Figure 3: Example of a whaling scam
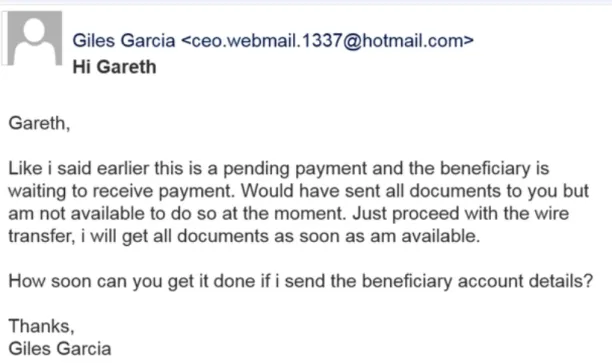
Source: CSO3
Note (whaling vs business email compromise (BEC): Whaling is occasionally confused with business email compromise (BEC), a sort of spear phishing attack in which an intruder sends the victim a fake email that looks to be from a colleague. BEC is not always whaling (since it commonly targets lower-ranking employees), and whaling is not typically BEC (because email is not always used), however several of the most significant whaling incidents include BEC attacks. For example:
- In 2015, the high-performance networking technology business lost $39 million due to a whaling attack. The San Jose-based business has only recovered a part of the amount.4
- In 2016, Snapchat was subjected to whaling violence when an executive fell for a CEO scam email and disclosed employee payroll data. Snapchat submitted the incident to the FBI and provided their employees with two years of complimentary identity theft insurance coverage.5
6 key differences between phishing and whaling
1. Knowing the target’s identity
In both cases, attackers are aware of the target’s identity.
- Phishing attackers know only a few elements of the target’s identity.
- Whaling attackers have unique and personalized insight into who they are focusing on and apply these insights to make the threat more credible and mislead their target into thinking they are a reliable person or organization. The information gathered goes much deeper into whaling and is implemented in more destructive manners. For example, Whaling attackers who present themselves as the CEO may seek images of a recent company party on social media and refer to the event to appear real.
2. The purpose of fraud
- Phishing attackers often seek to take control of any information or asset (intellectual property, login credentials) that has privileged access.
- Whaling attackers focus on gaining larger stakes usually by targeting a C-level executive. In rare circumstances, the hacker may be pursuing the victim’s credentials; however, whaling assaults tend to have a financial motivation to persuade the victim to transfer large sums of money or assets.
Read more: Role-based access control (RBAC), mandatory access control (MAC).
3. Status level of targets
- Phishing targets involve several non-specific targets.
- Whaling targets have extraordinarily high levels of user privileges, such as access to organizational money, approval systems, national trade secrets, patents, customer data, financial privileges, and other resources.
4. Attack type
- Phishing attacks are less organized and focus on obtaining any type of important data in the form of passwords, credit card numbers, usernames, and bank account details.
- Whaling attacks focus on a single potential target and launch a long-term social engineering effort. Over several weeks or even months, they build a channel of contact with the victim, gain their confidence with innocuous messages, develop credibility by repeating behaviors with no negative consequences, and ultimately scam them.
5. Use of business email compromise (BEC)
Business email compromise (BEC), exploits publicly accessible information on business user email addresses to mislead targets.
- Phishing campaigns use malicious email attachments, fake URLs, fake user-login pages, and other techniques rather than BEC.
- Whaling campaigns frequently employ BEC as a phishing method. During a BEC attack criminals submit an email message that looks to originate from a known origin, making a valid request, like in the following examples: A supplier with whom your organization routinely does business sends an invoice with a changed mailing address.
6. The organizational consequences
Successful whaling attacks often cost far more than phishing. Because spear phishing targets people with fewer privileges, the reward for hackers is smaller.
- Phishing may prompt organizations to review their data security and access privilege methods. Organizations may need to provide extensive cybersecurity education to all users who were affected by the incident.
- Whaling entails all of the phishing repercussions, and also penalties against C-level executives. Organizations might reprimand the executives or even replace them.
Phishing and whaling attack types
1. Impersonation
A typical whaling strategy is to mimic someone the target knows, such as a coworker, acquaintance, or family member. Attackers may impersonate a coworker and request personal data from other executives. Attackers may even mimic loved ones and request that individuals transmit money in response to a claimed emergency.
Figure 4: Example of cyber-criminals posing as a friend or family member
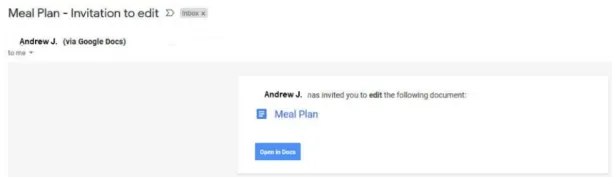
Source: Source: Sutcliffe 6
1.1 Fake president fraud
One type of impersonation is widely known as fake president fraud. The fake president fraud involves a criminal acting as a corporate manager and convincing an employee to transfer a substantial quantity of money straight to their account.
4 key elements of the fake president fraud are:
1. The ‘president’ initiates contact. A fake high-level executive, such as a C-level executive will contact the target employee. This communication is often made by email, frequently from a domain that appears to be the company’s, or through a ‘personal profile’.
2. The ‘president’ requests a wire transfer. The ‘president’ requests that the target send a substantial sum to a foreign bank account. The target may be told that the funds are for legal objectives, such as recent purchases, debt repayment, or vendor payments.
3. The ‘president’ enforces compliance. The target may raise concerns about unexpected requests or deviation from business practice. The ‘president’ uses psychological pressure to get the targets to believe the situation and comply with the request. Pressures can be influenced by several things, including:
- Authority—The criminal will emphasize their rank to persuade the target.
- Time pressure—Criminals may request an urgent transfer, leading targets to disregard protocol and avoid disclosing or verifying information before proceeding.
- Secrecy—The ‘president’ may use time pressure to emphasize the need to keep the arrangement secret for strategic or regulatory reasons. Sharing the secret with the target might boost their confidence and raise the likelihood of a successful move.
- The target initiates the transfer. The target will transfer funds to a criminal’s account.
Figure 5: A cyber-criminal acting as a manager or executive tries to deceive a target into opening a malicious file
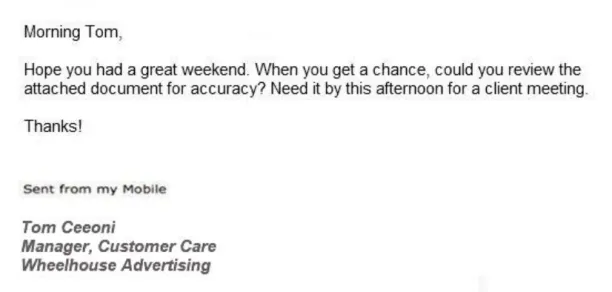
Source: Sutcliffe 7
2. Urgent requests
Criminals may use impersonation to persuade others to act quickly. These efforts are more likely to be responded to if emails look urgent or the target perceives a threat. Examples of things and whaling attacks that foster urgent requests include communications from upset managers, overdue payment notices, terminated registrations, or hacked accounts.
Figure 6: A cybercriminal mimicking Netflix with branded logos and clean-font e-mails
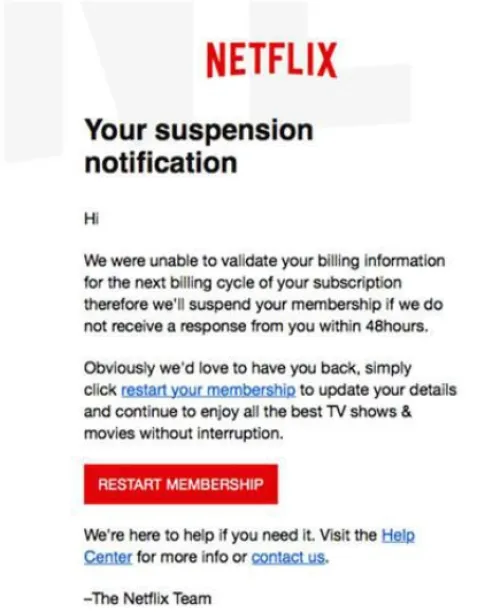
Source: Source: Sutcliffe 8
3. Unexpected contests, payments, and reimbursements
Phishing emails frequently use the promise of refunds, bank account changes, or tax refunds to attract victims. Criminals may even assert that you won or are qualified for a giveaway in more widespread phishing attacks. These kinds of unsolicited emails are typically an indicator of phishing attacks.
Defending against attacks
Cybersecurity awareness training: Because whaling targets human weaknesses, training employees is a critical line of protection against such attacks. Anti-phishing or whaling training can include:
- Providing instruction for employees on how to recognize questionable messages (checking message sender domains for fake website names).
- Giving tips for preventing oversharing on social media platforms.
- Implementing secure working practices, such as not opening spam files, verifying odd payments through an additional channel, calling suppliers to validate invoicing, and surfing straight to websites rather than clicking links within messages.
Multi-factor authentication: Using multi-factor authentication solutions may stop criminals from getting access to a user’s email account, regardless of whether they stole the user’s password and username.
Third-party cyber risk management: Phishing attacks may originate from a third-party domain; if third parties handle sensitive data on behalf of your company, they must adhere to the same restrictions as your business.
Cybersecurity software: No single security technology can completely prevent phishing or whaling, however, multiple tools can help to avoid or mitigate the harm caused by assaults.
- Email security systems, such as AI-powered anti-phishing applications, anti-spam programs, and encrypted email gateways, can identify and redirect risky spam emails.
- Antivirus software can assist with eliminating the spyware or malware that attackers may employ to gain access to target systems, perform research, spy on messages, or take authority over mailboxes. It can also assist in removing ransomware or virus infestations produced by phishing or whaling.
- System and software fixes can address technical problems typically used by phishers.
- Corporate security applications can help IT security professionals detect and monitor malicious traffic and network behavior associated with phishing and whaling attempts. Some of the applications are:
- SOAR (security orchestration, automation, and response)
- SIEM (security incident and event management)
- IDP (intrusion detection and prevention)
- EDR (endpoint detection and response)
- XDR (extended detection and response)
Read more: Cybersecurity risk assessment, cybersecurity best practices.
Future of phishing and whaling attacks
Phishing and whaling attack strategies will evolve with technological advancements. One notable advancement is the application of generative AI in phishing which improves the reality of standard tactics, such as emails and direct messages, by removing typos and using convincing writing styles. Thus, phishing and whaling communications will be more credible, creating a feeling of urgency that encourages targets to respond.
- AI detectors cannot distinguish whether a phishing or whaling email was produced by a chatbot or a person on almost three out of four occasions (~70%).
- Human-generated phishing and whaling efforts are becoming more difficult to detect, with a 25% increase in obfuscation tactics used in more than half (~55%) of phishing and whaling emails in 2023.
- Almost half (~45%) of phishing threat actors employ two obfuscation layers and less than one-third (30%) utilize only one.9
The substance of these attacks varies depending on the nature of the fraud, but the majority employ a combination of the following tactics.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. ”Internet Crime Report 2023“. Federal Bureau of Investigation. 2023. Retrieved April 1, 2024.
- 2. ”Phishing Scams“. Kansas State University. February 13, 2024. Retrieved April 1, 2024.
- 3. ”Whaling emerges as major cybersecurity threat“. CSO. April 21, 2016. Retrieved April 1, 2024.
- 4. ”Ubiquiti Networks victim of $39 million social engineering attack“. CSO. August 7, 2015. Retrieved April 1, 2024.
- 5. ”Snapchat leaks employee pay data after CEO email scam“. TheGuardian. February 29, 2016. Retrieved April 1, 2024.
- 6. ”Phishing-Attacks“. Sutcliffe Insurance. 2023. Retrieved April 1, 2024.
- 7. ”Phishing-Attacks“. Sutcliffe Insurance. 2023. Retrieved April 1, 2024.
- 8. ”Phishing-Attacks“. Sutcliffe Insurance. 2023. Retrieved April 1, 2024.
- 9. ”New report reveals that nearly three-quarters (71%) of AI detectors can’t tell if a phishing email has been written by a chatbot“. Egress. October 2, 2023. Retrieved April 1, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on


Comments
Your email address will not be published. All fields are required.