Third-Party Cyber Risk Management in 2024: 6 Best Practices
Organizations struggle to create resilience against third-party risks since 45% of them reported third-party-related interruptions in their business operations during the past two years,1 despite the ~15% growth in third-party cyber risk management (TPCRM) in 2023.2
Organizations need to improve their ability to manage third-party cybersecurity risk. This article covers what third-party cyber risk management (TPCRM) is and which methods can security leaders apply to adopt a centralized data-driven strategy to assess thousands of third parties.
What is third-party cyber risk management?
Third-party cyber risk management (TPCRM) is the process of discovering, evaluating, and controlling risks resulting from interactions with third parties.
TPCRM uses policies and mechanisms to ensure that third parties:
- Secure private information.
- Strengthen supply chain security.
- Comply with regulations.
- Prevent intrusions.
- Promote a healthy and safe work environment.
- Manage cyber incidents effectively.
Read more: Top 12 intrusion detection and prevention tools.
Why is third-party cyber risk management (TPCRM) important?
~55% of companies experienced a data breach caused by a third party. However, only ~50% responded that they keep an accurate record of all third-party access to their networks.3
This emphasizes the need to ensure that all third parties have and maintain an adequate degree of cybersecurity continuously. This may be accomplished using third-party security risk management (TPCRM), the cybersecurity component of your third-party risk management program.
What is a third-party risk?
Third-party risk refers to any risk posed to an organization by third parties in its environment or supply chain. Third parties are any group of people who have access to internal company or sensitive data, networks, or systems.
Typical third parties include:
- Suppliers (i.e. vendors)
- Partners
- Contractors
- Service providers
Common third-party risks include the following:
Cybersecurity risks: Risks that cause loss of privacy, reliability, or accessibility of information, data, or information (or control) infrastructure, and reflect the potential negative effects on company operations.4
Read more: Mandatory access control (MAC).
Financial/reputational risks: Risks that a third-party will harm your revenue or reputation. For example, if a supplier sends a damaged component to a company, the company’s reputation is jeopardized.
Operational risks: Risks that a third-party will disturb business operations. For example, if a software vendor is hacked, the company’s operational assets can get infected with malicious attacks.
Read more: OT network segmentation.
Legal, regulatory, and compliance risks: Risk that a third party will interfere with your compliance with legislation or regulations. For example, if a supplier violates labor or environmental rules, the company may still be held accountable for the violation. Outsourcing does not imply the end of responsibility.
Strategic risks: Risks that may cause an organization to fail to accomplish its strategic business goals solely due to a third-party provider.
Table: Enterprise risk registration template
| ID | Priority | Risk description | Risk category | Financial impact | Reputational impact | Mission impact | Likelihood | Exposure rating | Risk response type | Risk owner |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 3 | A social engineering attack on enterprise workforce leads to a
breach or loss
| Operational risk | OpEx (medium) CapEx (low) | High | Medium | High | High | ● Update corporate IT security training ● Implement phishing training service ● Update email security products per recommendations from IT risk council | CISO |
| 2 | 4 | A security event at a third-party partner results in data
loss or system outage
| Operational risk | OpEx (medium) CapEx (low) | High | High | Medium | Medium | ● Update procurement contract requirements to include protection, detection, and notification clauses ● Implement third-party partner assessment per CISO recommendations | Procurement |
| 3 | 10 | A flaw in product quality leads to reputational damage, reducing
sales
| Strategic risk | OpEx (medium) CapEx (medium) | High | High | Low | Low | ● Update the continuous improvement process ● Update external provider quality standards | Product development |
Source: NIST5
5 major changes in third-party risks during the last 3 years
1. Transition to centralization
Organizations are implementing common guidelines for third-party risk management initiatives while performing extra due diligence, including governance and reporting.
Most mature companies integrate all third-party kinds into one system, rather than examining them independently.
2. Switch to external resources for TPCRM preparation
TPCRM programs are increasingly using co-sourcing and contracted services to cut costs, improve efficiency, fill talent gaps, and adapt to changing demand. Organizations are turning to external resources to better understand risk.
- ~45% of organizations use third-party investigation to discover, analyze, and monitor subcontractor connections.
- In the next 2-3 years, ~45% of organizations aim to increase their usage of managed service providers, while ~60% are interested in growing their use of co-sourced partnerships.
3. Risk-tiering
Organizations prioritize critical third parties and implement additional restrictions based on financial effect and criticality as the main criteria for defining a critical third party.
Critical third parties are segregated for enhanced monitoring. Executives indicate that the most challenging aspect of reporting risk in third-party risk inventory is determining the impact of unpredictable external incidents.
4. Enhanced demand for data and technology
Adding automation, technology, and external data to the TPCRM process has improved.
- ~40% of organizations reported a greater understanding of their total third-party risk posture.
- In the next 2-3 years, ~40% of organizations aim to incorporate automation for improved reporting, while ~65% of them expect to combine external data sources and automation.6
5. The cyber attack surface has expanded
Organizations are paying far greater attention to their third-party cybersecurity posture and for a valid reason. The attack surface has grown significantly. Any organization that has access to a company network, whether in person (such as an IT vendor) or digitally (such as a software vendor), is a potential cyber attack vector, however, today’s hyperconnected corporate ecosystem requires companies to interact or have a connection with third parties.
- Vulnerable cloud attack surfaces have grown 600% annually in 2023.7
- In 2022, 1743 entities in the U.S. were affected by supply chain cybersecurity threats. This marks the highest recorded figure since 2017. The number of impacted companies rose by nearly 235% year on year in the most recent year studied.8
3 outcomes for effective third-party cyber risk management (TPCRM)
According to Gartner, successful governance of third-party cybersecurity risk is dependent on the security organization’s capacity to achieve these outcomes: 1) resource efficiency, 2) risk management and resilience, 3) influence business decision-making. However, most security organizations fail to be effective in two of the three outcomes, with only 6% of organizations being effective in all three (see figure below).
Figure: Organizations potential to execute three outcomes for third-party cyber risk management (TPCRM)
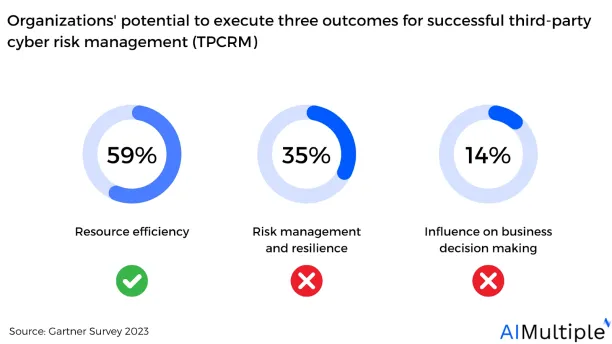
Source: Gartner9
6 best practices for managing third-party risk
To reduce the risk of a cybersecurity compromise caused by one of your third parties, organizations can implement a TPCRM program that will improve the efficiency and productivity of third-party interactions while decreasing risk.
1. Establish cyber risk management objectives
The first step in implementing TPCRM is to identify third-party risks that are consistent with the organization’s risk management program and risk assessment methodologies. A detailed picture of the organization’s third-party landscape necessitates the creation of a thorough inventory that distinguishes between third parties and identifies the measures required to maintain protection.
Mature firms develop a risk mapping that includes strategic, financial, reputational, regulation, operational, and cyber concerns. This inventory assists in identifying specific risks to consider when reviewing third-party connections and determining the level of risk that the company is prepared to accept.
2. Seek stakeholder commitment
TPCRM is only effective if all parties comply with it. Stakeholder support is crucial to ensuring that all parties work together to make the program a success. Organizations should incorporate all key stakeholders, especially risk and compliance, procurement, IT security, and business groups, and include them in the planning and implementation of the organization’s third-party risk management.
3. Form partnerships with business groups to monitor vendors
Third-party monitoring solutions assist organizations in assessing their security posture against third-party threats. To ensure that these tactics continue to be effective, organizations can examine and analyze them on an annual or more frequent basis. Monitoring tactics assist organizations in identifying and tracking high-risk partners and calculating the value and risk profile of the complete third-party portfolio.
Monitoring provides insight into the likelihood of a third-party delivery failure. Organizations can use these insights to statistically assess how third parties manage risks and gain assurance regarding the third party’s capacity to meet the organization’s policies and objectives.
4. Implement risk tiering
Each vendor has a unique level of risk. Depending on their criticality, organizations can determine which third parties have higher or lower priority.
Organizations often classify third parties into three tiers:
- Tier 1 High criticality and risk.
- Tier 2: Medium criticality and danger.
- Tier 3: Low criticality and risk.
Note: Most organizations prioritize Tier 1 vendor issues over lower-priority risks. These vendors necessitate a more stringent form of due diligence.
Organizations should also assess the impact on how they function if a third-party fails to provide a service. The level of interruption defines the danger to the third party.
The impact analysis should cover the following risks:
- What are the consequences when an individual makes information available to a third party without approval?
- What happens when an individual deletes or edits sensitive data without authorization?
- Which scenario prevents accessibility to the procurement department documents?
5. Launch the TPCRM program with continuous monitoring to enhance network visibility
A TPCRM program is an ongoing strategic initiative. After developing a vendor risk assessment methodology and working with third-party suppliers, partners or contractors should employ continuous monitoring to regularly review the risks that stakeholders pose to the organization.
Continual monitoring can enhance visibility for organizations to review and discover security and compliance issues in real-time, providing a consistent perspective of the third-party risk environment.
6. Deploy automation to streamline the TPCRM process
TPCRM initiatives that incorporate automated security risk assessments, external data providers, and cross-functional workflows (e.g., procurement, cyber risk, resiliency) improve third-party risk management and
Third-party cyber risk management from an executive viewpoint
Third-party risk tops the threat lists of executives. The ever-changing risk landscape (e.g. insider threats) motivates executives to carefully examine the strategies they take to stay focused on developing third-party risk issues.
Joseph Kelly, EY Oceania Third Party Risk Leader states that companies acknowledge the inherent risks associated with any third-party connection.
“The only method to eliminate third-party risk is to avoid interacting with them, which is unrealistic. So it’s more about, ‘How do you detect, manage, and mitigate the third-party risks?’ We’re transitioning from the era of identification to management and mitigation.” 10
Experts recognize that the risks are increasing since:
- Third-party risks were ranked as the 4th most important risk for 2024 by more than 1,000 senior executives; the same leaders ranked third-party risk as the 6th most important for 2034.11
- Nine out of 10 surveyed executives claim their organization has directly invested in its third-party cyber risk management program.12
Read more: Network audit, and top 10 insider threat management software.
For guidance on choosing the right tool or service, check out our data-driven lists of incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. ”Gartner Survey Finds 45% of Organizations Experienced Third Party-Related Business Interruptions During the Past Two Years“. Gartner. December 13, 2023. Retrieved March 19, 2024.
- 2. ”Gartner Forecasts Global Security and Risk Management Spending to Grow 14% in 2024“. Gartner. September 28, 2023. Retrieved March 19, 2024.
- 3. ”The State of Cybersecurity and Third-Party Remote Access Risk“. Ponemon Institute. 2022. Retrieved March 20, 2024.
- 4. ”Integrating Cybersecurity and Enterprise Risk Management (ERM)“. NIST. October 2020. Retrieved March 20, 2024.
- 5. ”Integrating Cybersecurity and Enterprise Risk Management (ERM)“. NIST. October 2020. Retrieved March 20, 2024.
- 6. ”2023 EY Global Third-Party Risk Management Survey“. EY. October 19, 2023. Retrieved March 19, 2024.
- 7. ”The 2023 State of Cyber Assets Report“. JupiterOne. 2023. Retrieved March 20, 2024.
- 8. ”Annual number of entities impacted in supply chain cyber attacks in the United States from 2017 to 2022“. Statista. February 22, 2023. Retrieved March 20, 2024.
- 9. ”Gartner Survey Finds 45% of Organizations Experienced Third Party-Related Business Interruptions During the Past Two Years“. Gartner. December 13, 2023. Retrieved March 19, 2024.
- 10. Joseph Kelly, EY Oceania Third-party Risk Leader.”2023 EY Global Third-Party Risk Management Survey“. EY. October 19, 2023. Retrieved March 19, 2024.
- 11. ”Executive Perspectives on Top Risks for 2024 and 2034“. Proviti. 2024. Retrieved March 19, 2024.
- 12. ”2023 EY Global Third-Party Risk Management Survey“. EY. October 19, 2023. Retrieved March 19, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on


Comments
Your email address will not be published. All fields are required.