UTM vs NGFW in 2024: Which One to Choose?
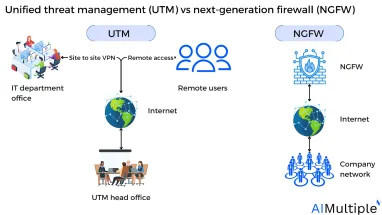
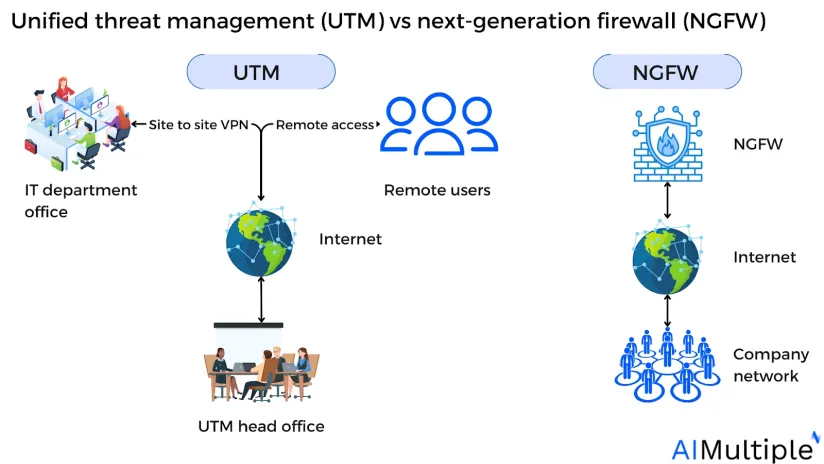
Figure 1: Unified threat management (UTM) vs next-generation firewalls (NGFW)
Network security is imperative for all organizations since 45% of experts see cyber incidents as the most feared source of commercial interruption.1
Next-generation firewalls (NGFWs) and unified threat management (UTM) software are two network security technologies that can offer an integrated cybersecurity risk management strategy for organizations to protect their vital assets against the most common cyber attack vectors.
However, security providers frequently use different definitions of UTMs and NGFWs, thus it is critical to understand the distinction between next-generation firewalls and UTMs to analyze which approach best aligns with your organization’s cybersecurity practices.
What is unified threat management (UTM)?
Unified threat management (UTM) is a method of information security in which single hardware or software integrates with security software (e.g. IPS tools, network security policy management software (NSPM)).
In 2003, numerous cybersecurity providers introduced an “all-in-one” tool to assist in managing the security configurations of increasing networks. Previously, companies had to deploy various devices and software, each tailored to perform a specific job, such as web filtering, antivirus protection, spam detection, and more. However, this strategy appeared to be difficult, complicated and expensive.
Figure 1: Unified threat management (UTM) can cover several domains
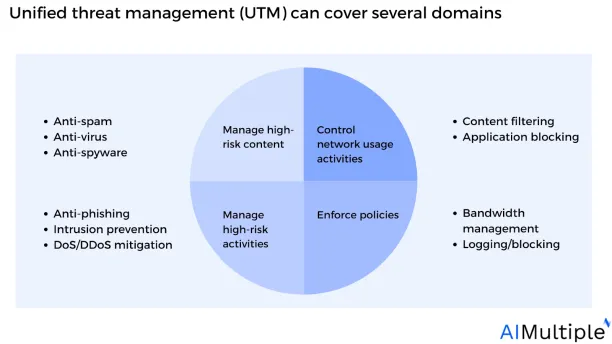
With the launch of UTM, organizations no longer had to manage different elements of network security deployed via different applications, each with its network security policies and rules; instead, they could utilize a single UTM firewall by combining numerous security services into a single appliance (see Figure 2).
In 2004, The word unified threat management (UTM) originated by the analyst company IDC.
Figure 2: Integration flow of security appliances and UTM
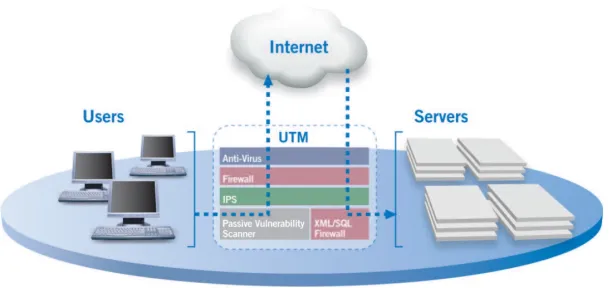
Source: Opus One2
UTM components were originally built as discrete solutions; but, when merged into a single system, their capabilities might extend. Some of the common features that UTM software often integrates with are:
- Firewall audit
- Intrusion prevention system (IPS)
- Data loss prevention (DLP)
- Network traffic monitoring system
- Antivirus
- Spam filter
- Network access control: Role-based access control (RBAC) and mandatory access control (MAC).
- Web-based content analyzer
- Virtual private network (VPN)
How does UTM Work?
A UTM solution detects vulnerabilities in an organization’s network using two inspection approaches:
- Flow-based inspections: Flow-based inspection, also referred to as stream-based inspection collects and scans the data transferred across the network to detect potential risks, such as viruses, intrusions, and hacking attempts.
To secure a private LAN from a public WAN, the UTM software forwards traffic and analyzes network packets following a sequence of procedures, as shown in the picture below.
Figure 3: Flow-based inspections
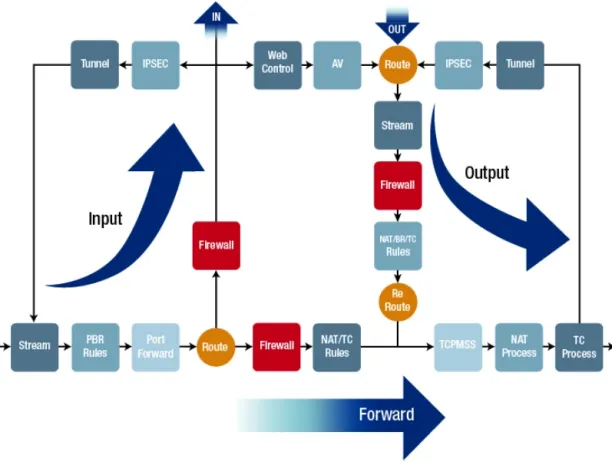
Source: Allied Telesis3
Figure 3 notes:
- IPSEC: IPSEC is a set of protocols for protecting communications between devices.
- TCP MSS: MSS is the maximum TCP (transport control protocol) segment size that a network-connected device may accept. MSS defines “segment” as the total length of the payload.
- PBR: Policy-based routing.
- TC: Traffic control.
- Proxy-based inspection: Proxy-based inspection is a network security approach that examines the contents of packets entering and exiting a network security device. Through proxy-based inspection network devices may operate as a proxy and reassemble the network content.
Proxy-based inspection employs an antivirus engine to scan stored data within the network devices and check it against known threat indicators which are stored in periodically updated database files (see Figure 4).
Figure 4: Proxy-based network device scanning
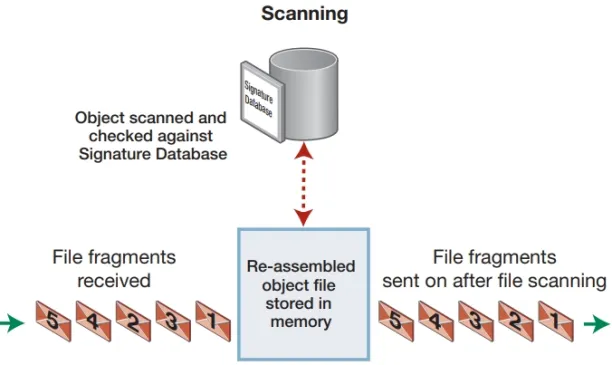
Source: Allied Telesis4
What is NGFW?
Next-generation firewalls (NGFW) combine traditional firewall technology with advanced capabilities such as anti-virus (AV), intrusion prevention systems (IPS), encrypted traffic inspection (ETI), and others. Its most notable feature is deep packet inspection (DPI)*.5
Network administrators can use an NGFW to create security zones for certain corporate tasks, such as marketing, sales, IT, and manufacturing. Alternatively, an NGFW may be used to create security using the standard three-zone strategy (public, private, and demilitarized zone or DMZ network security). A typical NGFW structure includes several network object definitions and hundreds of rules to regulate access across hosts, systems, zones, and the Internet.
*While traditional firewalls examine packet headers, deep packet inspection examines the contents within the packet itself, allowing users to more effectively identify, categorize, or block packets with risky data.
How does NGFW work?
NGFWs examine deep network traffic to determine where it is originating from. They can gather a larger amount of information about malicious traffic and embedded threats attempting to penetrate the network perimeter and access company data.
Key NGFW features:
Next-generation firewall requirements differ for each supplier, however, they often incorporate a mix of the following:
- Application awareness — filters traffic and applies complicated rules based on applications rather than just ports which allows companies to prohibit traffic from specific applications and keep more control over particular applications.
- Deep-packet inspection — examines the data contained in packets. Deep-packet inspection improves on old firewall technology, which just examines a packet’s IP header to establish its source and destination.
- Intrusion prevention system (IPS) — analyzes the network for harmful activity and prevents it when it occurs. This monitoring can be signature-based (matching behavior to signatures of recognized risks).
- External threat intelligence — provides organizations with information about potential security threats from external threat intelligence (e.g. open source blogs or industry-related analysis in web pages etc.) which primarily focuses on threats that exist outside of an organization.
In addition to these key characteristics, NGFWs may integrate antivirus and malware protection. They can also be built as a Firewall as a Service (FWaaS), which is a cloud-based firewall solution that enables businesses to streamline their IT infrastructure.
Read more: Firewall assessment.
UTM vs NGFW
Both technologies have various definitions on the market. The concepts of NGFW and UTM originally were offered by analyst organizations IDC and Gartner.
IDC defines UTM as a security appliance that includes a firewall, gateway, anti-virus program, and intrusion detection and prevention (IDS/IPS) or IPS tools.
Gartner defines an NGFW as one device that has an integrated IPS with deep packet scanning, traditional first-generation FW functions (network address translation (NAT), stateful protocol inspection, VPN, etc.), and the ability to identify and regulate network applications.
Since the buyers and sellers have used the phrases interchangeably. UTM can contain NGFW capabilities like application ID and control, while NGFW can include UTM capabilities like gateway antivirus software. The names are frequently used interchangeably since they both refer to a single device that has unified functions.
However, there are network-based security product categories that can be classified as NGFWs or UTMs, for example:
1. Application scope
- Unified threat management (UTM) products are all-in-one network security platforms designed to be simple. UTM tools mainly serve SMBs, not large-scale organizations.
- Next-generation firewall (NGFW) products have a broader application scope and aim to protect the networks of organizations ranging from SMBs to large-scale organizations.
2. Objective
- An UTM tool is responsible for scanning all computer systems and servers on a network, rather than just one. UTM tools follow and monitor all data transported over the network.
- NGFWs primary role is to check the computer’s incoming and outgoing data for harmful Trojan horses, spyware, and malware that might damage the system.
3. Features
- UTM solutions include first-generation firewalls and IPS functionalities, however, they do not provide application awareness and are not typically integrated into single-engine systems.
- NGFWs may include threat intelligence, mobile device security, data loss prevention, technologies that allow users to customize application control, and even certain firewall rule definitions.
4. Customization
- UTM technologies offer more standard policies, administration, and reporting tools that are easy to deploy and administer.
- NGFW technologies are suited for companies that seek to modify their security rules and prefer personalized reporting and control.
Which one to choose: UTM or NGFW?
Neither strategy is superior; nevertheless, numerous companies lack the time, money, and security knowledge necessary to manually create security policies and maintain a diverse set of appliances. UTM systems provide enterprise-level protection without the additional layer of management. This is especially valuable for small, medium-sized, or geographically spread companies that do not have specialized security or IT departments.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External links
- 1. “Allianz Risk Barometer 2023 – Rank 1: Cyber incidents“. Allianz. January, 2023. Retrieved April 3, 2024.
- 2. “Evaluating Unified Threat Management Products for Enterprise Networks“. Opus One. Retrieved April 5, 2024.
- 3. “Understanding the Next Generation Firewall and its Architecture“. Allied Telesis. 2020. Retrieved April 3, 2024.
- 4. ”Understanding the Next Generation Firewall and its Architecture“. Allied Telesis. 2020. Retrieved April 3, 2024.
- 5. “What Is a Firewall?“. Cisco. 2024. Retrieved April 3, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.