ZTNA or VPN in 2024: Which is Right for Your Business?
About half of U.S. workers say they have worked in remote settings where they needed authorized access to corporate networks.1
VPNs allow employees to remotely access corporate network resources from any device, however, giving remote access to a company network can be risky and can lead to breaches of sensitive data. At this point, Zero Trust Network Access (ZTNA) comes as an alternative cybersecurity solution to VPN.
This article demonstrates the main differences between ZTNA and VPN and discusses which cybersecurity solution is the most convenient for your business.
What is Zero Trust Network Access (ZTNA)?
ZTNA is based on the never trust and always verify approach, which signifies that all devices should have strict access control rules. ZTNA’s primary focus is to protect remote access to private applications, cloud, online services, data, and documents.
ZTNA treats all access as untrustworthy, therefore, every worker has to prove themselves as not a threat each time they want to access a network.
ZTNA’s main components are:
- User account authentication and authorization.
- Browser isolation against malware and other browser-based threats.
- Access policies include group membership, access behaviors, and suspicious indicators.
What is a VPN?
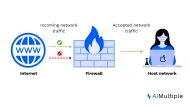
A VPN allows you to establish a secure link or tunnel between a device and a network. It works on protecting corporate resources by securing remote connectivity.
VPNs allow employees to send and receive information over the Internet using private networks. Only authorized parties can have access to data that gets transmitted through a virtual tunnel.
What are the differences between ZTNA and VPN?
Both ZTNA and VPN are security solutions that provide safe database connections through data and threat protection. However, there are a lot of differences between them:
- Framework comparison: VPN simply locks the front doors, so any party with the key can have access. On the other hand, ZTNA keeps all access out until they prove themselves as authorized for a certain action.
- Approach to security: VPNs use network-level access rather than application-level access. As a result, once an employee enters the VPN border, they will have full access to the system. ZTNA solution follows the opposite technique by rejecting entry permissions to all employees unless they are approved for a specific app they want to access. Thus, ZTNA eliminates hacking threats, reduces costly data breaches, and provides ultimate visibility for users’ activities.
- Workplace complexity: a VPN was designed for use when workers engage in offices using corporate devices. As remote work is becoming the new normal, employees increasingly use their devices for work, and using VPNs can be limited since ZTNA’s capability to control personal device access exceeds VPN’s potential to secure data access.
- Performance: With a VPN, it may take a longer time to provide access to apps using a private network. Conversely, ZTNA secures an immediate connection for web applications, reducing data loss risk.
Source: Perimeter 81
All these flaws make VPNs an outdated security solution for today’s work environments.
Further reading
- Top 3 Alternatives to Using a VPN
- Software Defined Perimeter: Definition, Importance & Use Cases
- Secure Access Service Edge: The New Norm for Cybersecurity
- Top 8 Cybersecurity Best Practices for Corporations
Please contact us if you have any additional information about cybersecurity solutions.
External Links
- 1. ”Remote Work Stable at Higher Rate Post-Pandemic“. GALLUP. September 15, 2023. Retrieved January 11, 2024.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on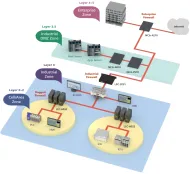
Comments
Your email address will not be published. All fields are required.