Cybersecurity

Prisma Cloud Alternatives in 2024 based on 2,000+ Reviews
With increasing numbers of remote workers migrating to off-site settings using cloud applications, operational workloads are stacking on networks, and the conventional network segmentation approach of building a security perimeter is no longer effective against evolving risks that may break network boundaries.
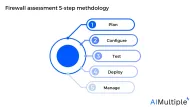
Firewall Assessment in 2024: 5-step Methodology
During the fourth quarter of 2023, data breaches exposed 8+ million records globally. Firewall assessment can help companies anticipate cyber risks and threats, detect alerts, and use a layered strategy to protect operational assets while also reducing the negative effects of data breaches.

Top 12 Intrusion Detection and Prevention Tools in 2024
Intrusion detection and prevention systems (IDPS) serve as critical filters to identify and mitigate malicious activities before they impact further security mechanisms or controls within a network. Positioned within the network traffic stream, an IPS operates actively to analyze and take action on the traffic between its source and destination.
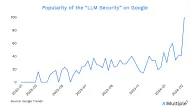
What are Top 10 LLM Security Risks & Why do They Matter? in '24
Based on the latest GenAI statistics, 71% of surveyed IT leaders express concerns about potential security vulnerabilities introduced by the implementation of generative AI. This forward-looking perspective underscores a growing interest in implementing security measures for GenAI tools, particularly large language models (LLMs).

Network Security Automation: Tips & Techniques in 2024
By 2025, the annual financial impact of cybercrime is expected to reach $10.5 trillion, underscoring the critical necessity for strengthened cybersecurity strategies. Relying on prevention technologies like antivirus and anti-malware software, alongside a firewall, was adequate for protecting against cyber threats.

Top 8 Network Segmentation Tools in 2024 Based on 500+ Reviews
Organizations typically operate within a combination of on-site, public cloud, and private cloud settings, each offering unique security features. The dynamic nature of cloud and hybrid environments complicates the application of static network segmentation strategies, which were better aligned with more stable, conventional network setups.

Top 5 Network Security Best Practices in 2024
In 2023, over 90% of organizations experienced at least one cyber threat or security breach, resulting in an average data breach cost of $4 million,. To prevent and manage these unfortunate and costly network security threats, here are some network security best practices for organizations: 1.

Compare 15 LLM Security Tools & Open-Source Frameworks in '24
Chevrolet of Watsonville, a car dealership, introduced a ChatGPT-based chatbot on their website. However, the chatbot falsely advertised a car for $1, potentially leading to legal consequences and resulting in a substantial bill for Chevrolet. Incidents like these highlight the importance of implementing security measures to LLM applications.
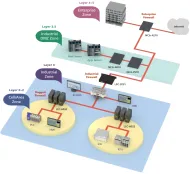
OT Network Segmentation in 2024: 4 Impacts & 5 Challenges
Figure 1: OT network segmentation Statistics show that the number of Internet of Things (IoT) devices is expected to nearly double, from ~15 billion in 2020 to more than 29 billion by 2030. The increased number of IT and OT systems expands the cyber attack surface.
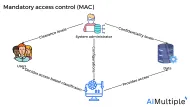
In-Depth Guide to Mandatory Access Control (MAC) in 2024
Figure 1: Mandatory access control (MAC) overview 1,500+ data breaches have occurred in the U.S. in 2022. Meanwhile, data attacks such as breaches, leaks, and exposure, affected 420+ million people that year.