Information Security

Top 5 Network Security Best Practices in 2024
In 2023, over 90% of organizations experienced at least one cyber threat or security breach, resulting in an average data breach cost of $4 million,. To prevent and manage these unfortunate and costly network security threats, here are some network security best practices for organizations: 1.

4 Ways to Improve Cybersecurity with URL Filtering in 2024
Despite its benefits, the internet can be dangerous to firms and employees if it is not monitored. Malware attacks can cost businesses both financially and non-financially (see Figure 1). Furthermore, having access to distracting internet platforms like social media can lead to employee productivity issues.

Top 4 Secure Web Login Best Practices for Corporations in 2024
Business workflows rely heavily on web applications as they: On the other hand, the internet is a dangerous environment where a cyberattack occurs almost every 10 seconds. Therefore, improving the security of digital platforms is critical for enterprises. This article will review the top 4 best practices that enhance online business security. 1.

Zero Trust Network Access (ZTNA) in 2024: Definition & Benefits
Compared to 2020, the number of cyber-attacks increased by 30% in 2021. Some cyberattack tactics have become even more prevalent. For example, the number of ransomware attacks doubled in 2021.

Secure Web Gateway in 2024: Definition, Benefits & Use Cases
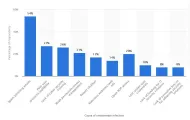
According to Accenture, the number of cyberattacks climbed by more than 30% in 2021 compared to 2020, reaching an average of 270 attacks per organization. Study indicates that approximately one successful breach occurs in nine attempts. As shown in Figure 1, successful cyberattacks can have financial consequences for enterprises and damage a company’s reputation.

In-Depth Guide Into Secure Multi-Party Computation in 2024
Data privacy and utility is a significant tradeoff for companies that want to utilize their data considering the prevalence of data breaches and regulations such as GDPR and CCPA. Secure multi-party computation is a method that can help businesses ensure the security of their sensitive data without undermining their ability to gain insights from it.

Zero-Knowledge Proofs: How it Works & Use Cases in 2024
As businesses collect a vast amount of customer data to gain insights, improve their products and services, and monetize their data assets, they can become vulnerable to cyber threats and data breaches. Breaches’ cost are rising every year, reaching ~$4.2M per breach, and as seen in Figure 1 they significantly harm businesses’ reputations and trustworthiness.

Privacy Sandbox: How it works & What will it bring in 2024?
Google launched “Privacy Sandbox” project, also called “effort”, “proposal” or ” initiative”, in 2019 while planning to say sunset third party cookies. For context, third party cookies are being retired since some users’ data have been misused via such cookies.
Ultimate Guide to Ransomware: Tools & Best Practices in 2024
In March 2021, CNA Financial, one of the largest insurance companies in the US, paid a $40M ransom after a cyberattack blocked access to the company’s network and stole its data.

Top 6 Data Security Best Practices for Organizations in 2024
Increasing and evolving insider threats and data privacy regulations such as GDPR and CCPA oblige businesses to pay greater attention to the security of their data. Data breaches are costly and harm business reputations. A proactive approach combined with insider threat management (ITM) software can be formulated by companies to prevent and manage data threats.