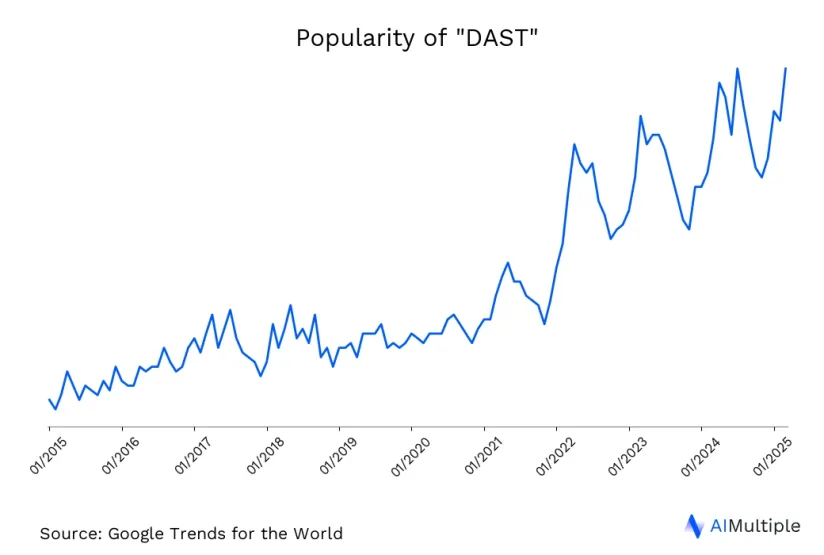
DAST’s ability to mimic real-world cyberattacks and expose vulnerabilities in real time makes it a valuable asset in the cybersecurity toolkit. As seen in the graph, the popularity of DAST has increased significantly in the last five years.
Considering that a significant portion of software attacks exploit the application layer 1 DAST’s focus on external testing becomes even more crucial. Learn how DAST integrates into DevSecOps, ensures compliance, addresses runtime vulnerabilities and more.
What is Dynamic Application Security Testing (DAST)?
Dynamic Application Security Testing (DAST) is a method used to identify security vulnerabilities in web applications. This methodology of testing applications externally allows DAST to simulate real-world attacks on an application, similar to the techniques a hacker might employ. For more information on the capabilities, see DAST tools.
In modern software development practices, particularly those following DevOps methodologies, DAST best practices and DAST tools can be integrated into continuous integration/continuous deployment (CI/CD) pipelines. This integration ensures ongoing security assurance throughout the application’s lifecycle.
To choose a DAST tool, visit the list of top DAST solutions.
Pros and Cons of DAST
| Pros of DAST | Cons of DAST |
|---|---|
| Mimics the actions of real attackers, testing the application’s defense against actual security threats. | Only detects issues identified vulnerabilities that are visible from an external perspective, missing deeper, internal vulnerabilities. |
| Can be used without access to the application’s source code. | Doesn’t provide specific insights into the source code or the exact cause of vulnerabilities. |
| Effective in finding vulnerabilities that only appear during the application security program’s operation. | Often finds vulnerabilities late in the development cycle, potentially with development teams increasing fix costs. |
| User-friendly and accessible for those without in-depth coding knowledge. | Can generate incorrect alerts or miss some vulnerabilities, also known as false positive/negatives. |
| Helps meet regulatory requirements that mandate dynamic testing. | Running the tests can slow down the application, especially in a live environment. |
How Does DAST Work?
Dynamic Application Security Testing (DAST) works by simulating external attacks on a web application to identify security vulnerabilities. Here’s an overview of how DAST typically operates:
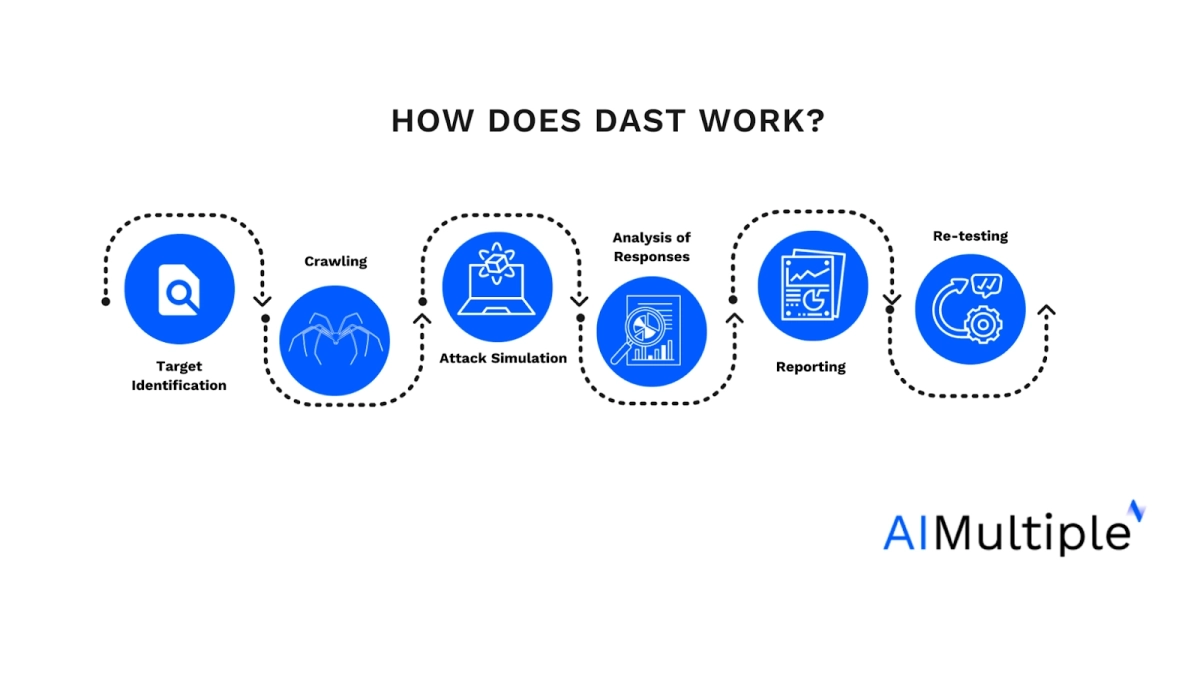
- Target Identification: Initially, the DAST tool needs to know what it is testing. This usually involves specifying the URL of the web application or API endpoints.
- Crawling: The DAST tool starts by crawling the application, much like a search engine. It navigates through the application’s web pages and functionalities, mapping out its structure and identifying the different inputs and endpoints it can test.
- Attack Simulation: Using the information gathered during crawling, the DAST tool simulates various attack scenarios. It inputs malicious data (such as SQL injection, XSS payloads, etc.) into forms, URL parameters, cookies, and headers to test how the application responds. Techniques includes:
- Fuzzing: Injecting unexpected data
- Parameter tampering: Modifying user inputs
- Session hijacking: Simulating unauthorized access
- Analysis of Responses: The tool analyzes the application’s responses to these simulated attacks. If the application returns error messages, behaves unexpectedly, or reveals sensitive information, the tool flags these as potential vulnerabilities.
- Reporting: After completing the tests, DAST tools generate reports detailing the vulnerabilities discovered. These reports often include the severity of each vulnerability, its location, and sometimes suggestions for remediation.
- Re-testing: Often, after vulnerabilities are fixed, the DAST tool is used again to verify that the security issues have been adequately addressed.
Top 7 DAST Use Cases
1-Integration with Development Lifecycle
DAST can be integrated into secure code during the later stages of the software development lifecycle, such as during testing or post-deployment. This helps ensure that security is maintained throughout the lifecycle of the application and that bugs are identified earlier and resolved easier.
Real-life example
Park ‘N Fly, a company providing various airport services in the United States, needed a DAST solution for about 10 internal and on-prem apps, a kiosk application at each location, and facility management system software. Invicti’s DAST solution was integrated into their existing environment, improving DevSecOps process efficiency. This integration provided Jira and Azure DevOps capabilities, allowing Park ‘N Fly to scan and fix new applications before reaching production, significantly reducing manual work.
Invicti’s automated features provided a security overview, enabling quicker prioritization and management of critical issues, effectively saving the equivalent of one full-time employee’s workload.2
2-Real-World Attack Simulation
DAST tools simulate real-world attacks on a web application, providing a practical assessment of its security posture. This approach helps identify vulnerabilities that might be exploited by malicious actors.
Real-life example
- Scenario: An e-commerce company wants to ensure that its website is secure against common web attacks like SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
- DAST Application: A DAST tool is deployed to scan the website while it is live. The tool simulates attacks by sending malicious inputs to the application’s forms and APIs.
- Outcome: The DAST tool identifies a SQL Injection vulnerability in the website’s search functionality. The company’s developers quickly patch the vulnerability, preventing potential data breaches.
3-Compliance and Regulatory Requirements
Many regulations and standards, such as the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), and the General Data Protection Regulation (GDPR), require regular security testing of applications that handle sensitive data. DAST helps organizations comply with these requirements by identifying vulnerabilities that could compromise data security.
DAST tests the effectiveness of security controls in a live environment. This is essential for compliance, as it provides empirical evidence that the deployed security measures are functioning as intended.
Real-life example
In compliance with regulations, including GDPR, Channel 4 was required to prove its data’s safety and security. This necessitated the implementation of strong security measures and technologies to guard against present and prospective risks. Consequently, the company was in search of an efficient and economical method to evaluate its security systems.
Channel 4 collaborated with Invicti to enhance its cybersecurity and streamline efficiency. Through this collaboration, they were able to decrease their yearly expenditure on penetration testing by about 60% in the first year, with further reductions in the subsequent year. Channel 4 implemented Invicti’s automated vulnerability scanning system, which facilitated ongoing and effective security evaluations of their online platforms 3
4-Comprehensive Coverage
DAST can test an application from the outside, exploring publicly available interfaces and endpoints. This allows it to find and identify vulnerabilities that might not be apparent through static analysis alone, such as issues with user authentication, session management, and other dynamic aspects of the application.
5- Continuous monitoring
Applications rely on hundreds of libraries which can be sources of vulnerabilities. Therefore, it is important to continuously scan applications for vulnerabilities.
Ease of use is important for continuous monitoring. They are generally easy to use and do not require access to the source code. This makes them a convenient option for security teams that might not have the time to continuously conduct security testing.
Real-life example
Polyfill is a dependency that more than hundred thousand web applications rely on to offer better services to older browser users. Its domain and GitHub repo were purchased and used to inject malware to users. DAST tools started highlighting this vulnerability quickly after it became known.4
6-Identification of Runtime Issues
Since DAST tests applications in their running state, it can identify issues that only appear during runtime. This includes problems with the application’s interaction with other systems, its use of third-party components, and its response to various types of input.
7-Complement to Other Testing Methods
DAST is often used in conjunction with other solutions to provide a more comprehensive view of an application’s security. Examples:
- Static application security testing (SAST) tools: While SAST analyzes the source code for potential vulnerabilities, DAST tests the application in its running state, offering a different perspective.
- Interactive application security testing (IAST) tools is similar to SAST but is focused on verifying identified vulnerabilities in an interactive manner.
- Software composition analysis (SCA) software scans open source libraries used in the project to identify supply chain vulnerabilities.
- Network and vulnerability scanning tools scan for open ports, outdated software, misconfigurations, and known security weaknesses.
How do application security tools differ?
DAST tools, vulnerability scanning tools, API security tools, and application security tools serve specific purposes in the broader context of cybersecurity, with some areas of overlap.
DAST tools specialize in testing the security of web applications while they are running, simulating external attacks to uncover vulnerabilities that are only apparent during operation.
Vulnerability scanning tools provide a broader service, scanning systems, networks, or applications for a variety of security issues, including weaknesses that might not be limited to the software itself but could involve configurations or outdated systems.
API security tools are specifically designed to protect APIs, which are critical interfaces between different software applications. These tools focus on security concerns unique to APIs, such as securing endpoints, authenticating and managing API calls, and ensuring data integrity during transmission.
Application security tools encompass a wide range of tools, including the above-mentioned types, and are aimed at securing applications throughout their lifecycle. This category includes tools and practices that address security at different stages—from development to deployment and maintenance.
These categories, however, do overlap:
- DAST tools are a subset of application security tools, specifically aimed at identifying vulnerabilities in live web applications through simulated external attacks.
- API security tools also fall under the broader umbrella of application security tools, but they focus specifically on the security of API interfaces, addressing unique challenges like endpoint security and authentication.
- Vulnerability scanning tools have a wider scope, encompassing security checks across entire systems, including networks and applications. They often include capabilities to identify vulnerabilities in web applications and APIs, thus overlapping with DAST and API security tools.
Limitations you should consider when using DAST
1-Limited Visibility into Internal Code
DAST only tests the exposed interfaces of an application. It cannot analyze the internal source of application code, so it might miss vulnerabilities that are not visible from an external perspective.
2-Late Discovery of Vulnerabilities
DAST is typically used in the later stages of development or even after deployment. This means vulnerabilities might be discovered late, making them more expensive and time-consuming to fix.
3-False Positives and Negatives
DAST can produce false positives (incorrectly identifying benign aspects of the application as vulnerabilities) and false negatives (failing to detect actual vulnerabilities). This can lead to unnecessary work or overlooked security risks.
4-Limited to Specific Types of Vulnerabilities
While DAST is effective at identifying specific vulnerabilities like SQL injection and cross-site scripting (XSS), it may be less effective at detecting more complex security issues like business logic flaws.
5-Performance Impact
DAST tests an application in its running state, meaning running DAST tools can impact an application’s performance. This needs to be carefully managed to avoid disrupting normal operations.
6-Difficulty in Identifying the Exact Source of Vulnerabilities
DAST can indicate that a vulnerability exists but often cannot pinpoint the exact location in the code. This can make troubleshooting and fixing issues more challenging.
7-Dependency on the Application’s Dynamic Behavior
The effectiveness of DAST can vary based on the specific dynamic behavior of the application being tested, potentially leading to inconsistencies in testing outcomes; this may hinder finding
application security vulnerabilities.
External Links
- 1. DDoS Attacks at the Application Layer: Challenges and Research Perspectives for Safeguarding Web Applications | IEEE Journals & Magazine | IEEE Xplore.
- 2. Park ‘N Fly Case Study | Invicti. Invicti
- 3. Channel 4 Case Study | Invicti. Invicti
- 4. Polyfill Supply Chain Attack: What To Do When Your CDN Goes Evil. Invicti

Comments
Your email address will not be published. All fields are required.