Information Security

What is Homomorphic Encryption? Benefits & Challenges (2024)
The increasing usage of cloud services and collaboration between companies to monetize data is raising concerns over data privacy. Regulations such as the General Data Protection Regulations (GDPR) aim to protect the privacy of consumers, and businesses pay serious fines in case of non-compliance. This creates a tradeoff between data privacy and utility for companies.

RPA for Cybersecurity in 2024: 7 Use Cases & Best Practices
It takes ~280 days to find and contain the average cyberattack which typically costs ~$4M. With the increasing volume of cyber attacks that organizations face every day, more business leaders are considering AI and automation solutions to manage threats.

Ultimate Guide to Federated Learning of Cohorts (FLoC) in 2024
As third party cookies are leaving our life, Google offers marketers Federated Learning of Cohorts (FLoC) so they can keep optimizing their ad spend. FLoC is a new tracking technology that is planned to be rolled out as third party cookies are banned by Google in 2023. FLoC uses federated learning principles.

Third Party Cookies in 2024: What Will Their Ban Change?
Third party cookies have been used to track website visitors for years. Collecting data from third party cookies provide insights into what visitors do on the websites and allow the companies to improve marketing and sales strategies. The use of third party cookies is changing possibly due to consumer reactions.

Explore Top 10 Privacy Enhancing Technologies & 3 Benefits in '24
Though data privacy legislation such as GDPR in the EU and CCPA in California are meant to prevent privacy breaches, consumer’s privacy is frequently invaded by hackers, companies and governments. Data leakages increase as businesses share consumers’ data with third-party companies in order to increase network visibility.
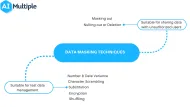
Top 8 Data Masking Techniques: Best Practices & Use Cases in '24
Given the increasing cyber threats and implementation of data privacy legislation like the GDPR in the EU or CCPA in the US, businesses need to ensure that private data is used as little as possible.

The Ultimate Guide to Cyber Threat Intelligence (CTI) in 2024
Data is the most valuable asset of most modern organizations. Organizations are rapidly deploying new technologies and devices that increase vulnerability points that malicious attackers may target. Organizations need to protect their data assets at a time when their attack surface is rapidly growing.

AI Security in 2024: Defense Against AI-powered Cyberattacks
Businesses can implement AI-powered security solutions into their systems to protect against online & offline security issues. Though AI is an effective solution to protect organizations from cyberattacks, it also enables attackers to launch complex, automated attacks.

In-Depth Guide to Managed Security Services in 2024
Data security has developed significantly for the last few years. Businesses now need to implement security services to prevent themselves from cybersecurity attacks, leakages, and frauds.

In-Depth Guide to Deception Technology: Definition & Benefits
Simple deception techniques, such as honeypots, which involves setting a trap for the attacker to lure them in, have been around since 2000s. New, AI-powered deception technology techniques enable companies to delay and identify cyber attackers to prevent and manage various cyber attacks.