Organizations typically operate within a combination of on-site, public cloud, and private cloud settings, each offering unique security features. The dynamic nature of cloud and hybrid environments complicates the application of static network segmentation strategies, which were better aligned with more stable, conventional network setups. Traditional network segmentation approaches usually depend on the manual setup and oversight of firewall regulations. To overcome these obstacles, organizations may also embrace more sophisticated segmentation strategies by using microsegmentation tools and the Zero Trust framework.
This article explores leading network segmentation tools, highlighting their unique features to assist organizations in choosing the best network segmentation software tailored to their unique requirements.
Top network segmentation tools
| Providers | Number of reviews* | Average score (5-point scale)* | Main Features |
|---|---|---|---|
| Tufin | 109 | 4.2 | Policy-driven automation Visibility across hybrid environments |
| Cisco Secure Workload | 9 | 4.2 | Automated microsegmentation Flexible deployment options |
| VMware NSX | 73 | 4.4 | Network virtualization Distributed Firewall |
| Illumio | 12 | 4.5 | Role-based access control lists Communication visualization |
| AlgoSec | 157 | 4.5 | Cloud-native application protection platform Network security policy management |
| Faddom | 67 | 4.7 | Network discovery & mapping |
| Akamai Guardicore Centra | 48 | 4.1 | Breach detection and response Policy-based segmentation |
| Check Point CloudGuard Network Security | 102 | 4.2 | Multi-layered security controls Consistent policy enforcement |
*Data was obtained from review platforms such as G2, Gartner, TrustRadius, and Capterra.
Read more: Network segmentation examples, network segmentation examples.
1. Tufin
Tufin is a network security platform hosted in the cloud, specializing in the management of network security policies. It enables the integration of network security management with the protection of cloud services across a hybrid virtual network. This platform offers a variety of tools and solutions aimed at assisting organizations in the automation of their security policies, such as network segmentation. Tufin can be implemented in various environments, including on-site, entirely in the cloud, or through a hybrid approach that blends on-site and cloud elements.
The network security solution is well-suited for businesses looking to automate the implementation of network segmentation or microsegmentation, minimizing manual labor and the potential for human error.
Key features of Tufin Network Segmentation Tool:
- Visibility: Tufin offers insight into network traffic and security settings by directing all packets to their intended destinations or preventing their passage. This solution can be installed on-site or utilized as a cloud-based SaaS offering.
- Automated network discovery & traffic flow mapping: The vendor uses network management tools to identify the all connected network devices and servers that make up a network and the connections between them. After detecting the devices, including routers, switches, servers, and workstations, the network segmentation software creates a network topology map. It shows how devices are interconnected and relationships between them.
- Automatic policy interpretation: Without requiring manual intervention, the process understands, analyzes, and applies security policies across various network components.
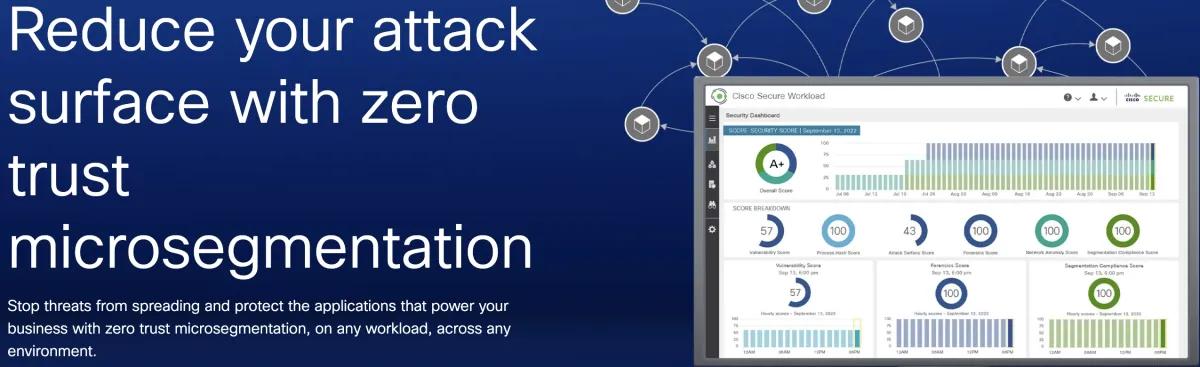
2. Cisco Secure Workload
Cisco Secure Workload, formerly known as Cisco Tetration, is a zero-trust microsegmentation solution that provides protection for workloads across various environments, including on-premises data centers, public clouds, and private clouds.
Cisco Secure Workload enables organizations to segment their network into finer, more distinct security zones. It is ideal for organizations aiming to protect multi-cloud environments and data centers, as well as for businesses that need detailed management of traffic within data centers and between cloud workloads.
Key features of Cisco Secure Workload:
- Micro-Segmentation: Provides security teams granular control over devices and an organization’s entire network infrastructure. Micro-segmentation network segmentation strategy allows for more precise control of traffic and more tailored security posture.
- Flexible deployment options: Cisco Secure Workload offers Software as a service (SaaS) and hardware-based appliance models. The SaaS package allows organizations to reduce the need for on-premises hardware maintenance. For organizations that require on-premises solutions, the network segmentation solution can be deployed on a dedicated physical or virtual appliance.
- Zero Trust Segmentation: It is a cybersecurity approach that operates on the premise, ensuring that each access request is authenticated and authorized.
- Network security alerts: When potentially malicious activities are detected within a network, network security systems produce notifications. These alerts serve to safeguard network resources, prevent data breaches, security threats, and protect sensitive data.
3. VMware NSX
VMware NSX is a platform for software-defined networking (SDN) and security, offering a range of security capabilities including micro-segmentation and network access management. It delivers a virtualized networking layer, decoupled from the underlying physical infrastructure.
NSX employs sophisticated threat prevention mechanisms like intrusion detection systems (IDS/IPS), Sandboxing, and network traffic analysis/network detection and response (NTA/NDR) to safeguard against harmful threats and ransomware attacks.
Key features of VMware NSX Network Segmentation Tool:
- L2-L7 Network Stack: Refers to the layers 2 to 7 in the OSI (Open Systems Interconnection) model, where each layer is tasked with a distinct function in the management of network communications.
- Distributed Firewall: Implements firewall capabilities and rules with precision across various network segments. In contrast to conventional, centralized firewalls that primarily protect the network’s outer edge, distributed firewalls are integrated throughout the network’s infrastructure. This method enables a more adaptable and thorough approach to network security.
- Multi-Site Networking and Security: This method encompasses the planning, deployment, and oversight of networking infrastructure and security protocols across various geographic locations.
4. Illumio
Illumio offers a cloud-based platform that specializes in Zero Trust Segmentation, enabling a security model adaptable to a range of environments including on-premise data centers, and both private and public clouds. Its Adaptive Security Platform (ASP) leverages the workload context to apply consistent security policies, regardless of the computing environment.
The network segmentation software is designed to map out all communications between workloads and devices and implement detailed segmentation policies to manage these communications.

Key features of Illumio Network Segmentation Tool:
- Zero-trust micro-segmentation: This approach combines the principles of Zero Trust (never trust, always verify) with the practice of micro-segmentation (dividing the network into smaller segments). The network segmentation software uses microsegmentation technique to break down cloud environments into segments, helping security teams reduce the attack surface and the violation of security policy.
- Communication visualization: Illumio network segmentation solution enables organizations to visualize all communication and network traffic flows between workloads and network devices.
- Continuous monitoring: Constant monitoring of IT infrastructures and networks is crucial for identifying potential security risks, operational inefficiencies, or regulatory non-compliance. By adopting a continuous monitoring strategy, organizations can significantly shorten the time required to resolve issues, enabling swift actions to mitigate them. This proactive approach not only enhances system security but also ensures smoother, more reliable operations
- Role-based access control (RBAC) lists: Role-based network access control provides resources based on the roles assigned to users. This process simplifies permission management and identifies access violations.
5. AlgoSec
AlgoSec is a network security software company, using intelligent automation to manage security policy management across diverse network environments. Their platform facilitates the implementation of security policies throughout hybrid networks, encompassing cloud services, software-defined networking (SDN), and traditional on-premises infrastructure.

Key features of AlgoSec Network Segmentation Tool:
- Cloud-native Application Protection Platform (CNAPP): AlgoSec implements CNAPP strategy to identify configuration and infrastructure-as-a-service (IaaS) network risks.
- Compliance with industry regulations: The tool automates the verification of compliance with regulatory standards and produces reports that affirm adherence to such regulations. It also implements network segmentation policies throughout a hybrid infrastructure.
- Multiple deployment models: The platform provides a variety of deployment options, including on-premises, cloud-based, and hybrid environments to cater to diverse IT infrastructure needs.
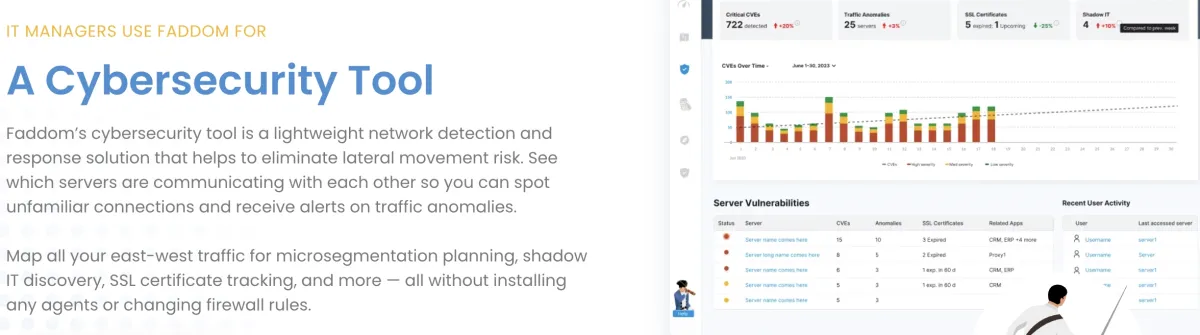
6. Faddom
Faddom is an IT asset documentation platform that offers network discovery capabilities. It focuses on Application Dependency Mapping (ADM), delivering insights for ensuring compliance and aiding in the transition of data centers and cloud migrations through the detailed mapping of application structures.
Faddom’s IT Infrastructure Mapping tool identifies and visually represents an organization’s IT infrastructure components, including servers and storage devices, enabling a thorough understanding and management of IT assets.
Key features of Faddom Network Segmentation Tool:
- Microsegmentation planning: Microsegmentation is a network security strategy that divides a network into smaller, distinct zones to enhance control over data flow. This approach is instrumental in defending against the unauthorized spread of threats within a network by limiting the pathways available for lateral threat movement.
- Network mapping: Network mapping, or network virtualization, involves identifying and illustrating the various components and connections within a network. This process helps in visualizing both the physical and the virtual aspects of networks, highlighting how different devices and services are interconnected. It provides a comprehensive view of the network’s structure, including its devices, connections, and how each element relates to the others.
- Network discovery: The network discovery process plays a crucial role for network administrators by enabling the identification and connection of devices within a network. This first step is essential for both mapping and tracking the network’s infrastructure, thereby enhancing the management of the entire network system.
- Vulnerability (CVEs) detection: CVE detection involves recognizing and cataloging cybersecurity vulnerabilities and exposures that have been publicly disclosed. This process entails maintaining a list of known security vulnerabilities affecting software or hardware. Each vulnerability listed is allocated a distinct CVE ID, facilitating uniform monitoring and discussion across different security platforms and systems.
7. Akamai Guardicore Centra
Akamai Guardicore Segmentation is a network segmentation platform designed to enhance network security through advanced segmentation. It is available both as a SaaS offering and a network appliance, catering to diverse environments like data centers, multiclouds, and endpoints.
Akamai’s network segmentation solutions use software-defined networking and micro-segmentation to effectively block unauthorized lateral movements within networks, ensuring granular control over individual processes.

Key features of Akamai Guardicore Network Segmentation Tool:
- Data collection methods: Guardicore Centra employs a diverse method for gathering data from cloud service providers, including agent-based sensors, network-based data collectors, and virtual private cloud (VPC) flow logs. This collected data undergoes processing and contextualization through an automated labeling process. Guardicore Centra’s labeling procedure integrates with the organization’s existing data sources like configuration management databases.
- Dynamic visual map: It offers a real-time graphical depiction of the network infrastructure, constantly refreshed to reflect any changes. This dynamic visual map offers administrators an intuitive way to swiftly detect new devices or security risks as they arise.
- Policy-based segmentation: It involves dividing a network into separate segments according to predetermined rules and policies. This approach monitors the performance of the network segmentation policy and enables organizations to customize their network security protocols to adhere to specific compliance standards.
8. Check Point CloudGuard Network Security
CloudGuard Network Security is a cloud-native security platform, providing threat protection and automated security for cloud networks. It allows administrators to enforce network segmentation policies, including network firewalls and other security measures.
Key features of CloudGuard Network Segmentation Tool:
- Automated network security supports: Supports IaC, CI/CD practices, automation of network security processes using APIs across different segments of a network to ensure continuous compliance.
- Unified security management: Unified Security Management (USM) provides a comprehensive view of an organization’s security posture by integrating security technologies, such as intrusion prevention systems (IPS), legacy firewalls, and vulnerability scanners.
- Multi-layered security controls: Multi-layered security involves the deployment of various security measures across different points in the IT infrastructure, specifically tailored for virtual data centers and Network Function Virtualization (NFV).
What is a network segmentation tool?
A network segmentation tool is network security software or hardware that divides a network into smaller distinct segments or subnetworks. This allows teams to improve network security, performance, and management by segmenting network traffic and restricting access to designated sections of the network.
Important security software to combine with network segmentation tools
Network security audit tools: Identify threats, vulnerabilities, and malicious activity to help companies mitigate cyber attacks and follow compliance with regulations.
NCCM software: Monitor information about your organization’s network devices by documenting network device configurations.
DSPM vendors: Provide network visibility into where to find sensitive data, who has access to it, and how it has been used across the cloud.
Network security policy management solutions (NSPM): Protect network infrastructure using firewalls and security policies against all threats.
SDP software: Deliver a software-defined perimeter (SDP) across the cloud to determine who gets access to what resources.
Further reading
- Top 10 Microsegmentation Tools
- Top 10 Insider Threat Management Software
- Microsegmentation: What is it? Benefits & Challenges
For guidance on choosing the right tool or service for your organization, check out our data-driven research and lists of microsegmentation tools and zero trust networking software.

Comments
Your email address will not be published. All fields are required.