Top 7 Free USB Blocking Software in 2024
Data loss prevention software utilizes USB blocking software in order to prevent data breaches resulting from data exfiltration through USBs and removable storage devices. Control over peripheral devices such as USBs includes whitelisting and blacklisting USBs, authorizing only read access, and authorizing on the basis of predefined policy rules. For more on USB blocking key features
If you are looking for a USB blocker to be deployed on a limited number of devices with limited capabilities, here is a comparative table for Top free USB blocking software with features, limitations, and compatibility with operating systems.
For enterprise-level USB blocking software tools that are tailored with encryption features, can be deployed on a larger network of devices, and have compatibility with multiple operating systems Top USB blocking software comparison
For device control software that includes USB blocking tools Top 10 device control software programs on the market
Top Free USB blocking software products compared
Comparative table on limitations & OS compatibility
| Product | License | Compatibility | Limitations of free edition |
|---|---|---|---|
| USBGuard | open source | Linux | n/a |
| USBSecure by Lugrain | proprietary | Windows | full functionality with limited PCs (5) & users (10) |
| USB Block by NewSoftwaresNet | proprietary | Windows | full functionality with limited trials (25) |
| Windows USB Blocker by SecurityXploded | proprietary | Windows | n/a |
| Pen Drive Locker /Unlocker by installWhat | proprietary | Windows | n/a |
| USB Lockit | proprietary | Android&Windows | n/a |
| USB Lock RP by Advanced Systems International | proprietary | Windows | full functionality with limited PCs (5) |
Notes
- Open-source products are available on GitHub.1
- Proprietary products are available on the provider’s website.
- The software products are arbitrarily sorted.
Comparative table on differentiating features
| Product | Device white/blacklisting | Read-only mode | Policy enforcement |
|---|---|---|---|
| USBGuard | ✅ | ❌ | ✅ |
| USBSecure by Lugrain | ✅ | ❌ | ✅ |
| USB Block by NewSoftwaresNet | ✅ | ❌ | ❌ |
| Windows USB Blocker by SecurityXploded | ❌ | ❌ | ❌ |
| Pen Drive Locker /Unlocker by installWhat | ✅ | ✅ | ❌ |
| USB Lockit | ❌ | ❌ | ❌ |
| USB Lock RP (demo mode) by Advanced Systems International | ✅ | ✅ | ✅ |
Differentiating features
For more on USB blocking key features
- Multi-OS compatibility: Integration with established operating systems with Windows, macOS, and Linux.
- Device white/blacklisting: Allowing and denying access to specific devices of choice or as defined in the policy.
- Read-only mode: Allowing for only reading data on USB devices.
- Policy enforcement: Configuring devices in accordance with user access and device based rules defined in the policy.
Products & features
The description of the extra features of the free USB blocking software that are not included in the main features is provided below.
1. USBGuard on GitHub
- USB white/blacklisting based on policy enforcement based on daemon computing, meaning the program runs in the background without needing an active controller.
- GUI interface is available.
- C++ programming language based API is available.
2. USBSecure by Lugrain
- Applicable on Bluetooth devices, Thunderbolt drives, FireWire ports, eSATA devices, SD cards, floppy disks, and CD/DVDs, based on configured rules.
3. USB Block by NewSoftwaresNet
- Applicable on external drives, SDs, MMCs, memory sticks, CDs, DVDs, HDs, Blu-ray discs, network drives, and network computers, based on configured rules.
4. Windows USB Blocker by SecurityXploded
- Blocking and unblocking USB devices except USBs used for wireless keyboards and mouse.
5. Pen Drive Locker/Unlocker by installWhat
6. USB Lockit
- Locking and unlocking USB devices on other devices through password authentication on the application interface.
- It encrypts data on the USB with AES 256-bit.
7. USB Lock RP by Advanced Systems International
- USB white/blacklisting based on policy enforcement.
- Alerting and notifications are enabled when a USB device is detected.
- Read-only mode for configured USB devices.
- A notification log is available.
- File transfer encryption and monitoring are supported.
USB blocking and data loss prevention (DLP)
Data loss caused by unauthorized access to network devices, or physical losses is forcefully prevented by data loss prevention (DLP) software that utilizes backing up data, encryption of data and endpoints, user authentication, and device control policy enforcement.
Device control makes sure removable storage devices such as USB devices, SD cards, and other removable media are used in accordance with the access rules defined in security policies.
Incidents centered around USB devices
Incidents that take endpoints as subjects are caused by security vulnerabilities resulting from weak encryption, weak authentication, an unsecured connection to the network, and a lack of security programs such as antivirus, firewall, network monitoring, and endpoint security.
Figure 1. Categories of incidents that involve USB devices
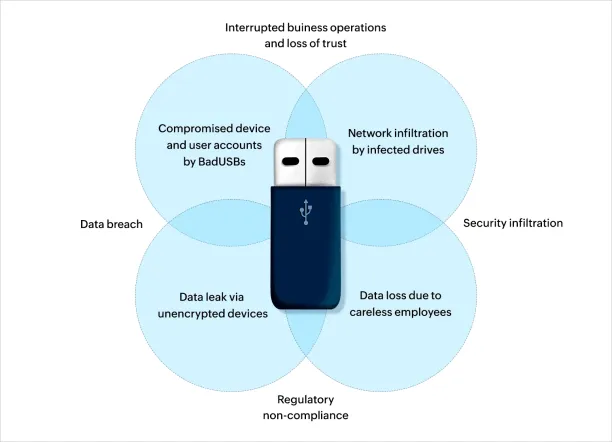
Source: ManageEngine Blog. 2
Historical examples of USB attack-led data breaches
Here are 2 historical examples that center around data exfiltration orchestrated by USB sticks:
1. Stuxnet Worm attack (2010)
The Stuxnet worm, discovered in 2010, was designed to target industrial control systems, particularly those used in Iran’s nuclear program. It spread via USB drives, exploiting vulnerabilities in Windows systems to infiltrate and sabotage uranium enrichment centrifuges.3
2. Edward Snowden leaks (2013)
In 2013, former NSA contractor Edward Snowden leaked classified documents revealing the extent of global surveillance programs conducted by the United States and its allies. Snowden used a USB drive to download and exfiltrate sensitive information from NSA systems. 4
Figure 2. List of malware that exploit USBs and exfiltrate sensitive data
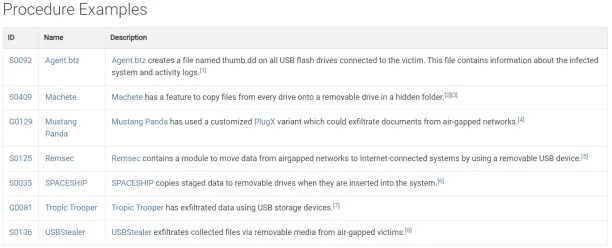
Source: MITRE ATT&CK. 5
Further reading
- Top 5 Alternatives for Digital Guardian Endpoint DLP
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. “USB Guard”. GitHub. Retrieved April 25, 2024.
- 2. “How do USB security risks affect an organization?”. ManageEngine Blog. Retrieved April 22, 2024.
- 3. “THE REAL STORY OF STUXNET”. IEEE Spectrum. Retrieved April 22, 2024.
- 4. “How Snowden did it”. NBC News. Retrieved April 22, 2024.
- 5. “Exfiltration Over Physical Medium: Exfiltration over USB”. MITRE ATT&CK. Retrieved April 22, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.