Firewall Audit

Top Firewall Management Tools in 2024: Analysis & Comparison
Ensuring robust network security is vital for businesses of all sizes to reduce costs of data breaches, which on a global scale exceed $4 million on average according to cyber security statistics. Businesses need firewall management tools to ensure the security and integrity of their sensitive data. Top 11 firewall management tools Table 1.

Firewall Integration of Top Management Services in 2024
Firewalls play a crucial role in safeguarding networks against cyber threats by controlling incoming and outgoing network traffic based on predetermined security rules. Firewall management services ensure consistent security policies, adherence to compliance, and effective threat management across an organization’s network infrastructure.
Firewall Management: Challenges and 8 Best Practices in 2024
Firewalls are the cornerstone of network security, acting as gatekeepers that regulate traffic and protect against cyber threats. Effective firewall management is crucial for maintaining a resilient network security. This article analyzes various aspects of firewall management, including the importance, key components, and best practices.

Firewall Audit Logs: Analysis and 6 Steps for Improvement in 2024
Firewall logging is essential for monitoring, analyzing, and auditing network traffic to detect potential security threats and attacks at an early stage. In the realm of cybersecurity, the management and analysis of firewall audit logs play a pivotal role in fortifying network defenses and upholding regulatory standards.

Key Components of Firewall Compliance: Guidance in 2024
The anticipated cost of cyber attacks globally was projected to reach nearly $10 trillion in 2024. The average worldwide cost of a data breach is ~$5 million. To avoid these costs, ensuring robust network security is paramount for organizations. Conducting comprehensive firewall audits is one of the cornerstone strategies for fortifying network security.
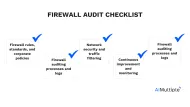
15+ Components of a Detailed Firewall Audit Checklist in 2024
Firewall audits are critical for maintaining network security and ensuring compliance with industry standards and regulatory requirements. Firewall audit software plays a crucial role by offering automated tools to scrutinize and manage firewall rules, configurations, and the overall security posture.
Top 3 Zscaler Alternatives in 2024: User Review Based Analysis
Zscaler is a provider of cloud security solutions, specializing in enterprise-level cloud security services. The data security company has offerings on secure internet access, secure remote access, digital experience, data protection and posture control. This article aims to provide a comprehensive analysis of Zscaler internet access and its alternatives.

Top 7 Open Source Firewall Audit Tools in 2024: Analysis & Comparison
Ensuring robust network security is paramount for businesses of all sizes. Open source firewall audit tools offer solutions for assessing and managing firewall configurations, rules, and policies. However, mid-market and enterprises companies may explore closed source firewall audit software for more comprehensive solutions.

Top 3 Skybox Security Alternatives: User Review-Based Analysis in 24
Skybox Security operates in the cybersecurity industry, which is expected to reach $250 billion by 2028. Skybox specializes in managing attack surfaces, vulnerabilities, threats, and security policies. However, user reviews express dissatisfaction with the product’s lack of Microsoft Azure integration, bugs, implementation difficulty, and frequent updates.

5 Firewall Best Practices for SMEs and Large-Enterprises in '24
Firewalls play a crucial role in safeguarding networks against cyber threats, and implementing firewall best practices is essential for robust security. Organizations in search of firewall audit software may find valuable insights in this article on firewall audit software comparison.