Analysis of Top 5 Network Change Management Software in 2024
Network change management software (NCMS) plays a vital role in maintain optimal performance, security, and compliance, offering a robust set of tools and features designed to streamline network configuration and change management processes.
This article analyzes the top 5 network change management software based on differentiating features.
You may also explore NCMS’
in the following sections.
Comparison of top 5 network change management software
Table 1. Comparison of top 5 NCMS
| Tool | User Rating* | Audit trail | Configuration automation | Incident management |
|---|---|---|---|---|
| Tufin Orchestration Suite | 4.3 out of 100 reviews | ✅ | ✅ | ✅ |
| ManageEngine Network Configuration Manager | 4.5 out of 80 | ❌ | ✅ | ❌ |
| ServiceNow Configuration Management Database | 4.5 out of 20 reviews | ❌ | ❌ | ✅ |
| AWS Config | 4.4 out of 72 reviews | ✅ | ✅ | ❌ |
| SolarWinds Network Configuration Management | 4.6 out of 50 reviews | ❌ | ✅ | ❌ |
*compiled using publicly available and verifiable data sourced from B2B review platforms.
Disclaimer: ❌signifies that the AIMultiple team couldn’t find public evidence about a specific feature.
NCMS included in the table:
Each vendor included in the table offers compliance management services alongside various other cybersecurity solutions. Compliance management involves continuously monitoring and evaluating systems to guarantee adherence to industry standards, security protocols, and corporate or regulatory mandates.
1. Tufin Orchestration Suite
The Tufin Orchestration Suite is a comprehensive NCMS solution that provides compliance management, audit trail creation, configuration automation, and incident management. By leveraging this tool, organizations can effectively manage network changes, maintain a robust audit trail for accountability, automate configuration tasks to save time and effort, and promptly address incidents for uninterrupted operations.
Figure 1. Shows change management dashboard of Tufin Orchestration Suite
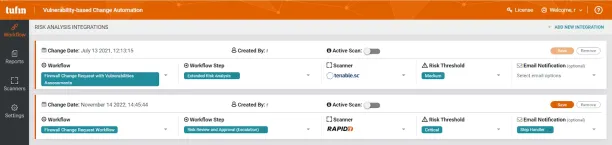
Source: Tufin1
2. ManageEngine Network Configuration Management
ManageEngine Network Configuration Management offers strong capabilities in compliance management and configuration automation. While it lacks an audit trail feature and incident management capabilities, it empowers organizations to ensure compliance with regulations, automate configuration changes, and optimize network performance efficiently.
Figure 2. Shows ManageEngine compliance and automation management dashboard
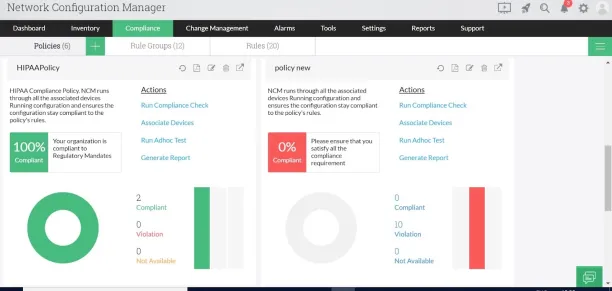
Source: ManageEngine2
3. ServiceNow Configuration Management Database
ServiceNow Configuration Management Database (CMDB) focuses on compliance management but does not provide network change management features for audit trail creation or configuration automation. However, it offers incident management capabilities, allowing organizations to manage configuration changes, track compliance, and respond effectively to incidents impacting the network.
4. AWS Config
AWS Config provides robust capabilities in compliance management, audit trail creation, and configuration automation. While it lacks incident management features, it enables organizations to ensure compliance with regulations, maintain detailed audit trails, automate configuration changes, and optimize network configurations within the AWS ecosystem.
5. SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager (NCM) offers compliance management and configuration automation functionalities. Although management features in SolarWinds NCM does not include an audit trail feature or incident management capabilities, it allows organizations to manage network changes effectively, automate configuration tasks, and enhance network performance.
Figure 3. Shows SolarWinds Network Configuration Manager’s dashboard
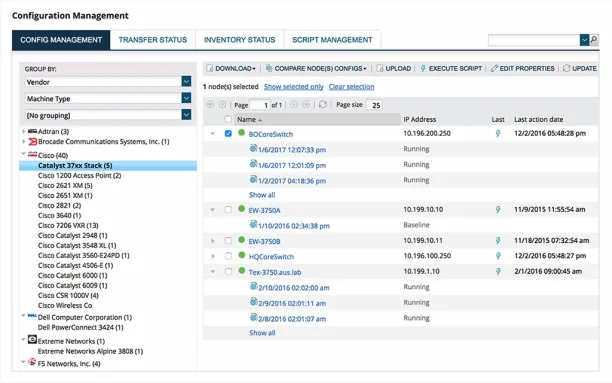
Source: SolarWinds3
Understanding Network Change Management Software
Network management configuration change software is designed to automate and streamline the process of implementing configuration changes across network devices. Each NCMS solution offers unique capabilities, ranging from compliance management to configuration automation, catering to diverse network management needs. By leveraging these tools effectively, organizations can optimize their network operations, reduce human errors, and enhance overall network performance and security.
Differentiating features of network change management tools
1. Audit trail
Figure 4. Shows change management audit trail of Tufin ORchestration Suite
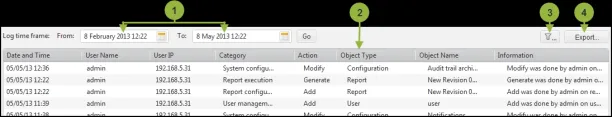
Source: Tufin4
An audit trail is essential for transparency, accountability, and troubleshooting in network change management. NCMS, with comprehensive audit trail capabilities, provides detailed records of all configuration changes, including who made the change, when it was made, and the nature of the change. This feature aids in tracking and analyzing changes, ensuring proper documentation, and facilitating compliance audits.
2. Configuration automation
Efficient network change management configuration automation is a game-changer in managing complex networks with numerous devices and configurations. NCMS, with advanced configuration automation capabilities, streamlines the deployment of configuration changes, reduces manual errors, and saves time and effort managing configuration tasks.
3. Incident management
In the event of network incidents or anomalies, effective incident management capabilities are crucial for swift identification, response, and resolution. NCMS, with incident management functionalities, provides real-time alerts, monitoring, and reporting to track network issues, minimize downtime, and optimize network performance.
5 main steps of network change management
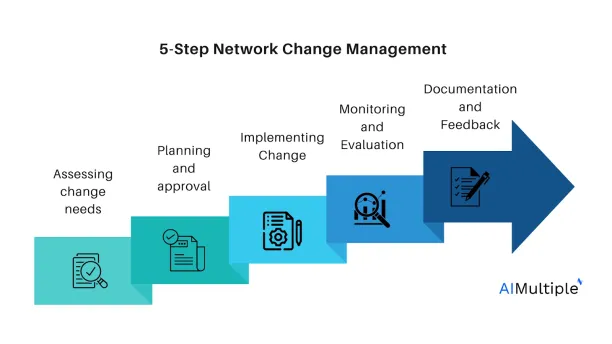
This section summarizes the key steps of the network change management process and how they contribute to organizational success.
1. Assessing change needs
The change management process begins with assessing the need for change. This involves identifying areas within the IT infrastructure or codebase that require modification or improvement. Network configuration change management software plays a vital role in this step, providing tools to monitor changes, track time alerts, and ensure compliance with regulations.
2. Planning and approval
Once the need for change is identified, the next step is to plan the change and seek approval. Change management tools help in automating the network change process, minimizing manual effort, and reducing the risk of errors. Automated backups and configuration backups ensure that changes can be reverted if necessary, providing a safety net during the change implementation phase.
3. Implementing change
After obtaining approval, the change is implemented following the established change management process. Network configuration managers facilitate this step by providing features like bulk deployments, dynamic multi-vendor network support, and monitoring compliance assessment reports. These capabilities streamline the implementation process, reduce downtime, and ensure zero interruption to the network system.
4. Monitoring and evaluation
Once the change is implemented, it is crucial to monitor its impact and evaluate its effectiveness. Change management tools offer features for monitoring and managing configuration changes, providing insights into performance metrics, security vulnerabilities, and change monitoring compliance assessments. This continuous monitoring helps in identifying any issues or bottlenecks early on and taking proactive measures to address them.
5. Documentation and feedback
Documentation plays a vital role in the change management process. Tools for network change management enable organizations to track who made configuration changes, maintain detailed logs of changes, and provide context and transparency throughout the process. This documentation not only ensures accountability but also facilitates knowledge sharing and continuous improvement.
Main benefits of NCMS
1. Efficient configuration management
One of the primary functions of NCMS is network configuration management. This involves managing configurations of various network devices like routers, switches, firewalls, and servers. With NCMS, IT teams can automate configuration tasks, ensuring accuracy, consistency, and adherence to predefined standards. Centralizing configuration management reduces the time and effort required to manage configuration changes across the network.
2. Streamlined change management process
NCMS facilitates a structured approach to network change management, covering planning, implementation, and monitoring of changes. Configuration change software (CCS) is a key component of NCMS, enabling organizations to track configuration changes, ensure compliance with regulations and security policies, and recover quickly from configuration errors. Change management tools like allow real-time change monitoring, alerts for unauthorized modifications, and maintain an audit trail of modifications.
3. Enhanced security and compliance
Security is a major concern in the digital ecosystem. NCMS enhances network security by ensuring secure device configurations, free from vulnerabilities, and compliance with industry regulations and standards like DISA STIG, NIST, FISMA, PCI DSS, and HIPAA. NCMS automates configuration backups, monitors compliance, performs bulk deployments, and provides detailed compliance assessment reports, reducing human errors that could introduce security gaps or compliance violations.
4. Operational efficiency and control
NCMS empowers organizations to automate network changes, reducing potential human errors that could cause downtime or interruptions. Standardized procedures and workflows in NCMS help IT teams determine compliance with security policies, implement changes seamlessly, and maintain operational continuity. The flow of network configurations is managed effectively, ensuring minimal interruptions and proactive responses to potential issues.
FAQ
What is network change management?
Network change management involves standardizing how organizations implement alterations to their networks, aiming to minimize disruption to existing systems when making necessary adjustments to network devices.
Further Reading
- Top 10 Network Security Policy Management Solutions (NSPM) [2024]
- Key Components of Firewall Compliance: Guidance in 2024
External Links
- 1. Tufin Orchestration Suite. Tufin. Accessed: 26/April/2024.
- 2. Network Configuration Manager. MAnageEngine. Accessed: 26/April/2024.
- 3. Network Configuration Manager. SolarWinds. Accessed: 26/April/2024.
- 4. Tufin Forum. Tufin. Accessed: 26/April/2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.