Analysis of Top 7 Network Security Automation Tools in 2024
Cybercrime is projected to have an annual financial impact of $10.5 trillion by 20251. Organizations face constant challenges in defending their network infrastructure against these potential threats.
Security teams are tasked with managing a myriad of security tools, analyzing security events, responding to incidents, and ensuring overall security posture. To alleviate these complexities and bolster defense mechanisms, network security automation tools have emerged as essential assets for modern security operations.
Top 7 network security automation tools
Network security automation tools are essential to keep up with rapidly growing cyber threats.
Table 1. Key feature comparison of the security automation tools
| Software | Network Analysis* | IDS | IPS | SOAR |
|---|---|---|---|---|
| Tufin Orchestration Suite | ✅ | ✅ | ✅ | ✅ |
| SolarWinds Network Configuration Manager | ❌ | ❌ | ❌ | ✅ |
| ManageEngine Log360 | ✅ | ✅ | ✅ | ✅ |
| NetBrain Next-Gen | ✅ | ✅ | ✅ | ❌ |
| Backbox | ❌ | ❌ | ❌ | ❌ |
| AppViewX ADC+ | ✅ | ✅ | ✅ | ❌ |
| AlgoSec Fireflow | ❌ | ✅ | ✅ | ✅ |
*may be provided by other products of the platform
Table 2. Market presence comparison of the security automation tools
| Software | User Ratings* | Number of Employees** | Free Trial | |
|---|---|---|---|---|
| Tufin Orchestration Suite | 4.3 out of 100 reviews | 482 | ❌ | |
| SolarWinds Network Configuration Manager | 4.6 out of 50 reviews | 2,522 | ✅ (30 days) | |
| ManageEngine Log360 | 4.5 out of 22 reviews | 275 | ✅ (30 days) | |
| NetBrain Next-Gen | 4.5 out of 20 reviews | 348 | ❌ | |
| Backbox | 3.9 out of 31 reviews | 30 | ✅ (2 days) | |
| AppViewX ADC+ | 4.7 out of 14 reviews | 287 | ❌ | |
| AlgoSec Fireflow | 4.5 out of 219 reviews | 498 | ❌ |
*Based on data from leading B2B review platforms
**Based on data from LinkedIn
Disclaimer: ❌ means that the AIMultiple team couldn’t identify public evidence about a specific feature.
Transparency statement: Vendor with links to their websites is sponsor of AIMultiple.
Every vendor listed in the table provides compliance management services along with a range of other cybersecurity solutions. Compliance management entails ongoing monitoring and assessment of systems to ensure compliance with industry standards, security protocols, and corporate or regulatory requirements.
You may explore details on key features of network security automation tools in the following sections.
1. Tufin Orchestration Suite
This suite offers comprehensive network analysis capabilities, empowering security engineers to gain deep insights into their existing security infrastructure. It also prioritizes automation efforts by focusing on zero-touch automation, allowing for efficient and automated processes. Additionally, it provides IDS and IPS functionalities, ensuring proactive threat detection and response. Tufin provides a demo option for interested users.
User reviews
Tufin‘s compatibility with various firewalls and network devices offers flexibility and convenience, allowing users to manage different brand devices within a single platform2.
Figure 1. A user review on Tufin
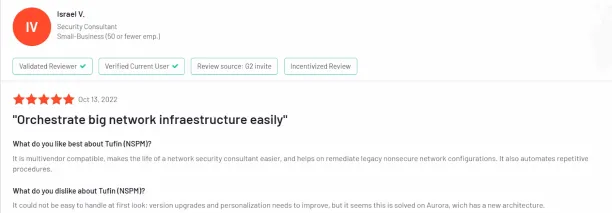
The network topology feature allows security personnel to understand permitted and restricted traffic, even without direct access to firewalls, enhancing overall security awareness3.
The complexity of Tufin‘s licensing system is a concern for users, especially smaller customers, who suggest a more flexible and streamlined approach would improve user experience4.
2. SolarWinds Network Configuration Manager
SolarWinds’ tool focuses on network configuration management but lacks features such as network analysis, zero-touch automation, IDS, and IPS. It may suit organizations seeking basic configuration management tools. While it offers a 30-day free trial, it doesn’t provide a demo option.
User reviews
Users appreciate SolarWinds’s compliant inventory management, ensuring adherence to internal equipment management policies and facilitating accurate asset tracking within the network5.
Several users have reported slowness in the Orion platform, especially with additional modules and nodes, highlighting the need for performance optimization to improve user experience6.
Figure 2. A user review on SolarWinds Network Configuration Manager
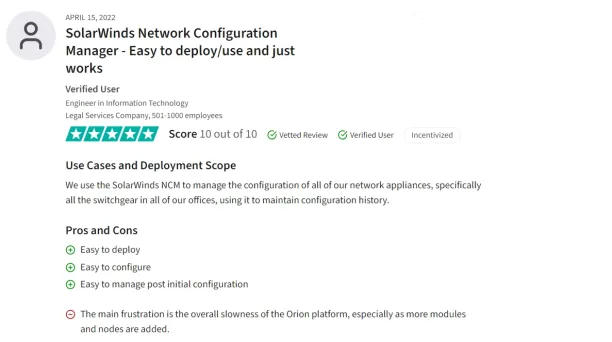
Users express a need for enhanced support for multiple vendors and non-Cisco devices within the software, suggesting the inclusion of more vendor-specific equipment profiles and features to broaden its usability in various network environments7.
3. ManageEngine Log360
ManageEngine Log360, as a security automation tool, facilitates network cybersecurity operations and threat detection with network analysis, IDS, and IPS capabilities. It offers a 30-day free trial option.
User reviews
This tool allows automatic configuration backups across network devices, ensuring data security both onsite and offsite. The solution offers incremental scheduling for high data availability, even across different network environments8.
Figure 3. A user review on ManageEngine
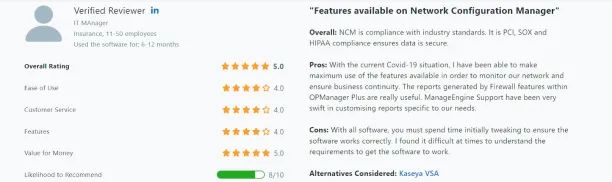
The pricing of the product is competitive, making it an affordable solution for organizations9.
There are occasional reports of Log360 causing system slowdowns, especially on Mac systems, and interfering with end-user tasks10.
4. NetBrain Next-Gen
Offering network analysis and IDS features, NetBrain Next-Gen empowers security engineers to monitor and detect threats efficiently but lacks IPS features. It also provides a demo for organizations to explore its capabilities.
User reviews
Users appreciate that the software offers dynamic mapping, real-time path analysis, and protocol-level troubleshooting, providing insights into network traffic flow and performance11.
Some users find the cost of NetBrain to be relatively high, suggesting that discounts for Tier 1 users would be beneficial12.
Users have experienced occasional slowdowns in system performance, suggesting improvements in speed and responsiveness13.
Figure 4. A user review on NetBrain Next-Gen
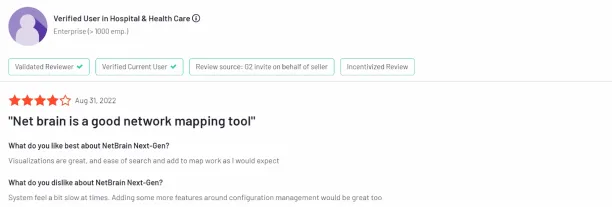
5. Backbox
Backbox focuses on security automation without offering network analysis, IDS, and IPS capabilities. Its automation platform can streamline cybersecurity operations and response efforts. Backbox provides a 2-day free trial and a demo option.
User reviews
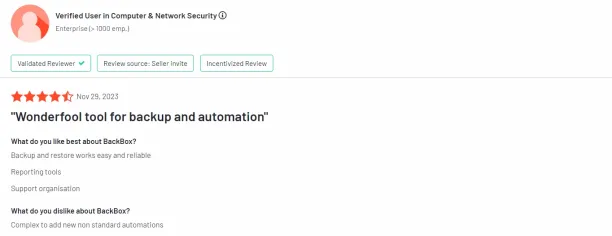
According to reviews, BackBox’s automation capabilities are highly effective, enabling tasks like backups and firmware updates on firewalls to be scheduled and executed seamlessly, improving operational efficiency for security analysts.
Some users express the complexity of adding new non-standard automation in BackBox, requiring additional customization and configuration, which may pose challenges for users looking to implement advanced automation tasks14.
Figure 5. A user review on BackBox
6. AppViewX ADC+
Figure 6. Dashboard of AppViewX ADC+
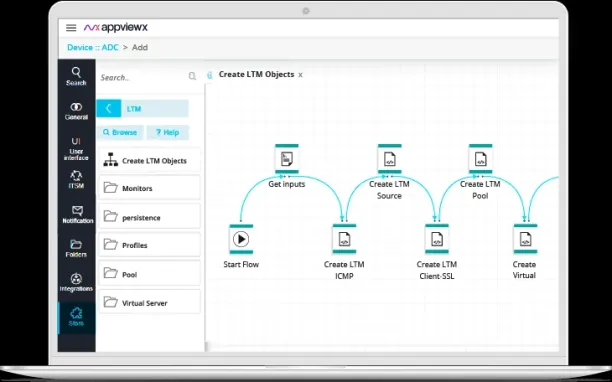
Source: AppView15
AppViewX ADC+ is a security automation tool that offers a comprehensive suite of network security automation tools, including network analysis, zero-touch automation, IDS, and IPS. It enables security teams to automate security processes, detect threats, and fix vulnerabilities efficiently. ADC+ provides a demo option but doesn’t offer a free trial.
User reviews
AppViewX ADC+ can manage various vendor network products, offering flexibility and the ability to add features as needed16.
The interface is perceived as unclear and not very intuitive, leading to a learning curve for users, especially those in non-technical roles17.
7. AlgoSec Fireflow
AlgoSec Security Fireflow focuses on IDS, and IPS capabilities, making it a valuable tool for automating security tasks and managing security incidents effectively. However, it lacks a network traffic analysis feature. AlgoSec Security Fireflow also provides a demo for users to experience its key features and advanced analytics.
User reviews
Reviews point to an appreciation of automation, streamlining complex tasks like managing firewall policies and identifying obsolete rules, thus enhancing operational efficiency and reducing human error18.
Figure 7. A user review on AlgoSec FireFlow

Algosec’s user interface can be complex, with a steep learning curve for users not well-versed in network security or firewall management, potentially leading to misconfigurations or delays in policy implementation19.
Key features of security automation tools
1. Network analysis
It is a fundamental feature of network security automation tools, providing deep insights into network traffic, patterns, and anomalies. By leveraging network analysis capabilities, security analysts can detect unauthorized access, abnormal behaviors, and potential security breaches, allowing them to take proactive measures to mitigate risks and secure the network perimeter.
2. Intrusion detection system
IDS plays a critical role in identifying and alerting security teams about suspicious activities, unauthorized access attempts, and potential security threats within the network. Integrating IDS into security orchestration tools enables automated security systems, threat detection, real-time alerts, and rapid response to security incidents, thereby enhancing overall security stance and reducing response times.
3. Intrusion prevention system
IPS complements IDS by not only detecting but also actively preventing malicious activities and cyber attacks. Security orchestration tools with IPS capabilities can automatically block or quarantine suspicious traffic, enforce security policies, and mitigate security risks in real-time, ensuring proactive defense against cybersecurity threats and maintaining a robust security posture.
4. Security orchestration, automation, and response

SOAR platforms integrate enterprise software, automate repetitive tasks, orchestrate incident response workflows, and leverage threat intelligence feeds to enhance security operations.
With SOAR, security teams can automate repetitive security tasks, streamline incident response processes, and orchestrate complex security operations. This capability not only enhances operational efficiency but also enables proactive threat hunting, incident investigation, and remediation, ultimately strengthening the organization’s overall security stance.
3 main benefits of network security automation tools
1. Streamlined security operations
Network security automation tools streamline cybersecurity operations by automating repetitive tasks, workflows, and processes. This enables security teams to focus on strategic initiatives, threat analysis, and proactive threat hunting, rather than being bogged down by manual, time-consuming tasks. By automating security processes, organizations can achieve operational efficiency, reduce human error, and enhance overall productivity within the security operations center (SOC).
2. Proactive vulnerability management
Security automation tools facilitate proactive vulnerability management by automating vulnerability scans, assessments, and remediation processes. This allows organizations to identify and address security vulnerabilities before they can be exploited by malicious actors. By automating vulnerability management, businesses can strengthen their security posture, reduce exposure to cyber threats, and ensure compliance with industry regulations and best practices.
3. Rapid threat detection and response
One of the primary advantages of security automation tools is their ability to detect and respond to cyber threats in real-time. These tools leverage threat intelligence feeds, advanced analytics, and automated investigation of threats to identify suspicious activities, security incidents, and potential breaches promptly. By automating threat detection and response, businesses can minimize downtime, contain security incidents swiftly, and mitigate the impact of cyber attacks.
4. Business continuity and risk management
Network security automation tools contribute to business continuity and risk management efforts by automating risk assessments, compliance checks, and security audits. By automating risk management processes, organizations can identify, prioritize, and mitigate potential threats, thereby safeguarding critical assets and maintaining operational continuity.
Types of network security automation tools
1. SOAR platform integration
SOAR platforms integrate different security tools, automate repetitive tasks, orchestrate incident response workflows, and leverage threat intelligence to enhance security operations. Security automation platform enables a security team to streamline incident detection, prioritize alerts, automate response actions, and collaborate effectively within the security operations center (SOC).
2. Threat intelligence platforms
Threat intelligence platforms gather, analyze, and disseminate actionable threat intelligence feeds to security analysts. These tools enable organizations to stay informed about the latest cyber threats, trends, and indicators of compromise (IOCs), empowering them to proactively detect and respond to potential security incidents.
3. Vulnerability management tools
Vulnerability management tools identify, assess, and remediate vulnerabilities in network devices, applications, and systems. These tools play a crucial role in proactive threat mitigation by scanning for known vulnerabilities, prioritizing remediation efforts, and ensuring compliance with security best practices and industry standards.
4. Endpoint security solutions
Endpoint security solutions focus on protecting endpoints, such as computers, mobile devices, and servers, from cyber threats. They include features like endpoint detection and response (EDR), antivirus, anti-malware, and device management capabilities. These solutions detect and respond to endpoint incidents, prevent unauthorized access, and safeguard sensitive data, contributing to comprehensive cybersecurity defense.
How to choose the right cybersecurity automation tool?
1. Network traffic analysis
An effective cybersecurity automation tool should offer robust network traffic analysis capabilities. It should be able to monitor, analyze, and detect anomalous patterns in network traffic, helping identify potential security threats and vulnerabilities. Look for tools that provide deep packet inspection, behavior-based analytics, and real-time visibility into network activity for detecting threats and enhancing response capabilities.
2. IDS and IPS functionality
Ensure that the cybersecurity automation tool integrates IDS and IPS functionality seamlessly. IDS is essential for detecting suspicious activities and incidents, while IPS plays a crucial role in blocking and mitigating identified threats. Choose a tool that offers both IDS and IPS capabilities, with customizable rule sets, threat intelligence integration, and automated response mechanisms.
3. SOAR capabilities
A modern cybersecurity automation tool should include Security Orchestration, Automation, and Response (SOAR) capabilities. SOAR platforms enable organizations to orchestrate security systems, enhance workflow automation, automate incident response processes, and integrate disparate network security automation tools and technologies into a unified platform. Look for SOAR features such as playbook automation, case management, threat intelligence integration, and automated response actions to streamline security operations and improve overall efficiency.
4. User-friendly interface and reporting
Ease of use and comprehensive reporting capabilities are essential factors when choosing a cybersecurity automation tool. The tool should have an intuitive user interface, easy configuration options, and robust reporting features to provide actionable insights into incidents, threats, and vulnerabilities. Look for tools that offer customizable dashboards, real-time alerts, and detailed analytics to facilitate informed decision-making and proactive threat management.
FAQs
Why do you need cybersecurity automation tools?
Network security automation tools are essential for modern organizations to effectively detect, respond to, and mitigate cybersecurity threats. They improve operational efficiency, reduce incident response times, enhance threat visibility, and strengthen overall cybersecurity resilience.
What are signs that an organization needs security automation?
Businesses may require network security automation if they experience continuous security breaches, overloaded security teams managing numerous alerts, encounter evolving and complex cyber threats, and struggle to achieve complete network transparency due to dispersed network structures and data volumes that surpass traditional monitoring capabilities.
Further Reading
- Top Firewall Management Tools in 2024: Analysis & Comparison
- Key Components of Firewall Compliance: Guidance in 2024
External Links
- 1. 2023 Official Cybercrime Report. Esentire. Accessed: 03/May/2024.
- 2. Tufin Reviews. G2. Accessed: 03/May/2024.
- 3. Tufin Reviews. G2. Accessed: 03/May/2024.
- 4. Tufin Reviews. G2. Accessed: 03/May/2024.
- 5. SolarWind Reviews. Trustradius. Accessed: 03/May/2024.
- 6. SolarWind Reviews. Trustradius. Accessed: 02/May/2024.
- 7. SolarWind Reviews. Gartner. Accessed: 02/May/2024.
- 8. ManageEngine Reviews. Capterra. Accessed: 02/May/2024.
- 9. ManageEngine Reviews. Capterra. Accessed: 02/May/2024.
- 10. ManageEngine Reviews. Gartner. Accessed: 02/May/2024.
- 11. NetBrain Reviews. G2. Accessed: 02/May/2024.
- 12. NetBrain Reviews. G2. Accessed: 02/May/2024.
- 13. NetBrain Reviews. G2. Accessed: 02/May/2024.
- 14. BackBox Reviews. G2. Accessed: 02/May/2024.
- 15. AppViewX ADC+. AppView. Accessed: 02/May/2024.
- 16. AppViewX ADC+ Reviews. Gartner. Accessed: 02/May/2024.
- 17. AppViewX ADC+ Reviews. G2. Accessed: 02/May/2024.
- 18. AlgoSec Reviews. G2. Accessed: 02/May/2024.
- 19. AlgoSec Reviews. Trustradius. Accessed: 02/May/2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.