Top 7 Alternatives To Burp Suite For Application Security Testing
Burp Suite is a dynamic application security testing (DAST) solution offered by PortSwigger that is used for testing the security of web applications. Web application security scanner (DAST), also known as web vulnerability scanners or dynamic application security testing (DAST) solutions can be automated or manual.
In this article, we will examine the automated dynamic security testing solutions available as alternatives to Burp Suite.
Best Burp Suite alternatives based on 800+ reviews in 2024
| Vendors | Total number of reviews* | Average score** | Starting price | Free trial |
|---|---|---|---|---|
| Acunetix by Invicti | 146 | 4.3 | Custom | 15-day |
| Astra Pentest | 78 | 4.6 | $5,999/yr | N/A |
| Checkmarx DAST | 54 | 4.2 | Custom | Available*** |
| ManageEngine Vulnerability Manager Plus | 181 | 4.4 | $695/yr | 30-day |
| Rapid7 DAST | 10 | 4 | Custom | Available*** |
| Tenable Web App Scanning | 160 | 4.5 | €6470/yr | 7-Day |
| Veracode DAST | 218 | 4.2 | Custom | 14-day |
Table notes (Vendors listed alphabetically):
- Total number of reviews*: Review data is gathered from leading B2B review platforms.
- Average score**: The average rating is calculated on a scale of 5, with reviews sourced from leading B2B review platforms.
- Available***: Although a free trial is offered, specific details about its duration are not disclosed on the vendor’s website.
1. Acunetix by Invicti
Invicti is a web application security scanner for web applications, designed to uncover potential vulnerabilities across websites, web services, and web apps. Invicti provides both enterprise and standard plans. The enterprise version caters to multiple users and offers a web application security solution, whereas the standard version is designed for on-site use as a desktop web vulnerability scanner.
The standard plan is tailored for hands-on professionals such as security engineers, penetration testers, and developers, typically scanning fewer than 50 websites. On the other hand, Invicti Enterprise operates on a browser-based cloud platform, eliminating the need for purchasing, licensing, installing, or maintaining any hardware or software. The capacity of Invicti Standard is confined by the hardware it operates on, and it is intended to scan a limited number of applications concurrently. Invicti Enterprise, being a cloud-hosted web vulnerability scanner, offers virtually limitless resources by leveraging the infrastructure of Amazon’s Cloud (AWS).
Features:
- Automated proof-based scanning: The scanner is designed to eliminate false positives in web application security scanning by providing proofs of concept for each security vulnerability it detects, ensuring that the reported vulnerabilities are not mistaken identifications.
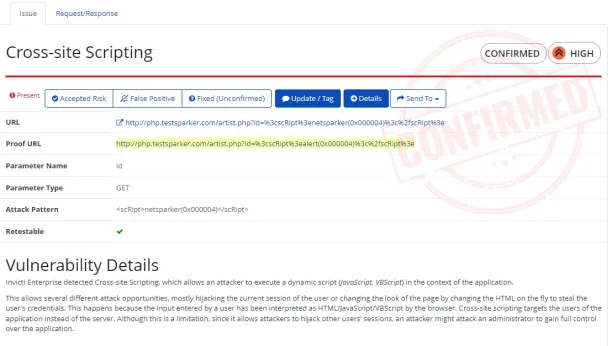
Source: Invicti’s proof-based scanning technology
- Various deployment choices: Invicti offers a scalable solution suitable for both on-premises and cloud installations. The cloud module of Invicti includes integrated tools for enterprise workflows, allowing for the simultaneous scanning of numerous web applications.
- Continuous Integration (CI) integration: Integrate with CI systems such as Jenkins, Travis CI, and CircleCI, enabling the inclusion of automated security checks within the CI workflow.
2. ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is a cross-platform vulnerability management and compliance tool that not only identifies web vulnerabilities but also includes integrated features for vulnerability remediation. It offers functionalities such as patch management, asset tracking, web server assessments, and configuration audits.
There are three versions available: the free edition, which allows management of up to 25 endpoints; the professional edition, designed for devices within a local area network (LAN); and the enterprise edition, intended for devices distributed across a wide area network (WAN). It accommodates both Windows and Linux platforms.
Features:
- Continuous scanning: ManageEngine has built-in patching feature to remediate security vulnerabilities instantly. ManageEngine’s vulnerability assessment tool regularly scans an organization’s network and other web assets to identify and assess possible vulnerabilities.
- Patch management: After identifying and evaluating network vulnerabilities, patch management helps businesses safeguard their systems from recognized vulnerabilities and exploits. ManageEngine provides cross-platform patching capabilities, enabling users to oversee and apply patches for Windows, Mac, and Linux systems, including servers, laptops, desktops, virtual machines.
- Zero-day vulnerability mitigation: Zero-day vulnerability mitigation involves safeguarding software or hardware against unknown vulnerabilities, known as “zero-day” vulnerabilities, which are not yet publicly recognized. ManageEngine Vulnerability Manager Plus assists businesses in fortifying their systems and applications against zero-day vulnerabilities.
ManageEngine scans the internet for information on emerging security threats. When details about zero-day or publicly disclosed vulnerabilities emerge, this information is verified and incorporated into the central vulnerability database. This updated information is then synchronized with the Vulnerability Manager Plus server, ensuring that organizations have the latest data to protect against these common vulnerabilities.
- Built-in remediation: Built-in remediation enables a system or software to not only identify issues and vulnerabilities but also to automatically resolve these vulnerabilities, eliminating the necessity for manual intervention.
3. Tenable Web App Scanning
Tenable Web Application Scanning is a dynamic application security testing (DAST) tool designed to assist organizations in detecting vulnerabilities within web applications. This intelligent web application scanner addresses critical vulnerabilities, including those outlined in the OWASP Top 10, such as SQL injection and cross-site scripting (XSS). Tenable WAS is offered as a cloud-based service and has also been integrated into the on-premises Tenable Security Center, providing flexible deployment options.
Features:
- Continuous delivery/continuous deployment (CI/CD): Tenable Web App Scanning can be incorporated into the workflows of continuous integration and continuous deployment (CI/CD) pipelines, enabling automated security assessments of applications throughout their deployment stages.
- Scheduled and recurring scans: This functionality enables organizations to automate their security assessment process by configuring automated scans to take place at predetermined times or at regular intervals.
4. Astra Pentest
Astra Pentest specializes in vulnerability scanning, emphasizing penetration testing and vulnerability assessments tailored for web applications, APIs, and cloud infrastructures. Astra Pentest integrates with different platforms, including GitLab, Jenkins, Bitbucket, Azure, and CircleCI.
Features:
- Scan logged-in pages: Astra Pentest offers features for session management and supports the addition of custom headers, making it suitable for scanning logged-in pages.
- Scan PWA/SPAs apps: Astra Pentest’s scanner can identify vulnerabilities in Progressive Web Apps (PWAs) and Single-Page Applications (SPAs).
- Different vulnerability scan types: Astra Pentest provides three different vulnerability scanning modes: Automated Scan, Vetted Automated Scan, and Manual Pentest.
The Automated Scan, included in all plans, offers basic scanning capabilities. The Vetted Automated Scan builds on this by including all features of the Automated Scan but adds a layer of review, where security engineers assess the final report. The Manual Pentest is the most comprehensive, combining an automated vulnerability scan with vetted results and a manual penetration test conducted by security experts.
5. Rapid7 DAST
Rapid7’s InsightAppSec is a Dynamic Application Security Testing (DAST) solution that automates the security testing of web applications. InsightAppSec provides attack templates to address vulnerabilities listed in the 2013 and 2017 OWASP top ten web security risks.
Features:
- Universal translator: It is designed to understand the different protocols, formats, and development technologies used in mobile and browser-based applications.
- Attack replay: This functionality allows developers to confirm vulnerabilities on their own by replaying the HTTP traffic that was used to detect them.
- Scheduled scans: InsightAppSec’s scan scheduling feature allows organizations to schedule their security scans during maintenance periods or low-traffic times.
6. Checkmarx DAST

Checkmarx DAST (Dynamic Application Security Testing) enables organizations to identify vulnerabilities in live applications. Checkmarx One is designed for modern cloud-based development, operating exclusively as a cloud-delivered service. It does not offer support for Linux-based systems. For user interface localization, Checkmarx One offers English, which is the default setting, as well as Korean and Traditional Chinese.
Features:
- API security: Checkmarx has integrated API Security into its solution, providing an overall view of an organization’s entire API inventory. This feature automatically identifies vulnerabilities and risks associated with APIs, eliminating the need for manual API definition or registration. Checkmarx’s API Security feature supports web frameworks across multiple programming languages like Flask and Django, Java’s Spring framework, Node.js using Express, and C# with ASP.NET Web API.
- Security testing tools: Checkmarx is part of the Checkmarx One platform, providing a unified solution for both static (SAST) and dynamic (DAST) application security testing.
7. Veracode DAST

Veracode DAST is a security tool designed to detect vulnerabilities in web applications by testing them in their operational environment, including when they are live in production.
Features:
- Real-time attack simulation: Veracode DAST simulates real-world cyberattacks, mimicking the techniques of malicious actors to uncover vulnerabilities. This thorough simulation involves running full scans on the target URLs, which, although critical for identifying security weaknesses, could potentially impact the performance of the applications being tested. Therefore, it is important to ensure that scans are conducted only on URLs.
- Dynamic analysis: This feature allows security teams to crawl web application URLs or API endpoints to understand links, text, form fills, and other page elements.
Further reading
- Top 5 Alternatives to Tenable Nessus in 2024 with 700+ Reviews
- 8 Best Rapid7 Alternatives in 2024 Based on 1400+ Reviews
If you have further questions, reach us:

Comments
Your email address will not be published. All fields are required.