10 API Security Best Practices: Why are they essential in ‘24?
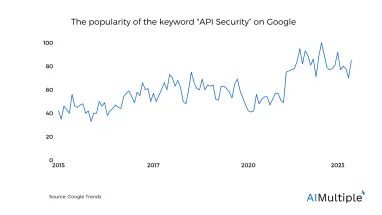
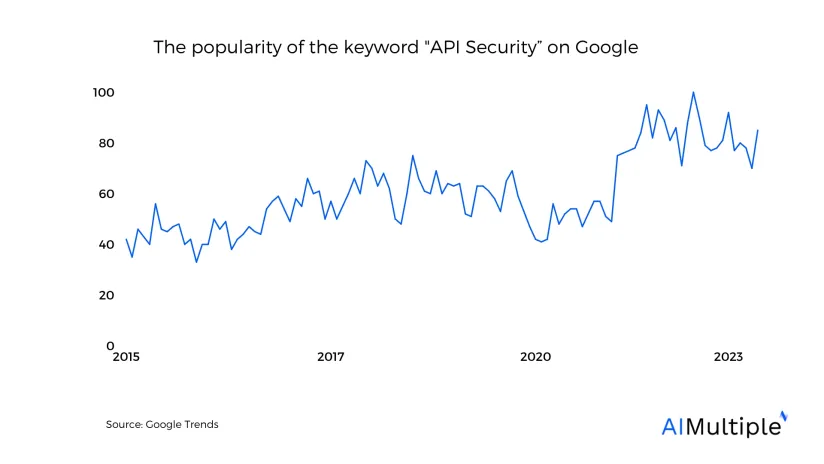
Application Programming Interfaces (APIs) have become the backbone of software communication and integration. They allow different software systems to exchange data and functionality easily and efficiently.
However, as the use of APIs expands, so does the potential for security vulnerabilities. Ensuring the security of APIs is crucial to protect sensitive data and maintain the integrity of software systems. This article explores API security best practices, providing a guide to safeguarding digital assets.
10 API security best practices
1. Authentication and Authorization
Authentication
Authentication is the process of verifying the identity of a user or system attempting to access an API. It is the first line of defense in API security, ensuring that only legitimate users can access it. Implementing strong authentication mechanisms is crucial. One common method is using API keys, which are unique identifiers assigned to each user. Another approach is employing OAuth, an open-access delegation standard commonly used for token-based authentication.
Authorization
Authorization occurs after authentication and determines what resources a user can access and what actions they can perform. Implementing proper authorization ensures that a user has the necessary permissions to perform a specific action. Role-based access control (RBAC) is a popular model that assigns permissions to roles rather than individual users, simplifying user permissions management.
2. Implementing Zero-Trust Architecture
Implementing Zero-Trust Architecture is a strategic approach to cybersecurity that operates under the principle “never trust, always verify.” Unlike traditional security models that assume everything inside an organization’s network can be trusted, the zero-trust model treats all users and devices inside and outside the network as potential threats. This approach requires strict identity verification for every person and device attempting to access resources on the network, regardless of their location.
Key Components of Zero-Trust Architecture
- Strict User Verification: Users must be authenticated and authorized before accessing applications and data. This often involves multi-factor authentication (MFA) to ensure that the user is who they claim to be.
- Least Privilege Access: Users are granted the minimum level of access—or permissions—needed to perform their tasks. This limits the potential damage from a compromised user account or insider threat.
- Microsegmentation: The network is divided into small, secure zones to maintain separate access for separate parts of the network. This prevents an attacker from moving laterally across the network if they gain access to one part.
- Continuous Monitoring: The zero-trust model relies on continuous monitoring of the network and user behavior to detect and respond to anomalies in real-time. This helps identify potential threats and mitigate them promptly.
- Device Security: Ensuring that all devices accessing the network are secure and meet the organization’s security standards is crucial. This includes managing device health and updating software to protect against vulnerabilities.
3. Regular Security Audits and Testing
Continuous monitoring and testing of APIs can identify vulnerabilities before they are exploited. Conducting regular security audits and employing automated tools to scan for vulnerabilities are crucial practices. Penetration testing, where ethical hackers attempt to exploit vulnerabilities in the API, can also provide valuable insights into potential security weaknesses.
4. API Gateway Implementation
An API Gateway is a central entry point for all API calls, enhancing API security through a unified interface. This practice is a central component of API management. This setup enables efficient management of security policies, such as authentication, authorization, and threat protection, across all APIs. It simplifies the security architecture, making monitoring and enforcing compliance with security standards easier. Additionally, an API Gateway can provide rate limiting and encryption, further securing API access and data transmission
For example, consider a company offering various online services, each with its own APIs for user management, payment processing, and content delivery. Instead of securing each API individually, the company implements an API Gateway as a single entry point for all API traffic.
5. Data Encryption
Data encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) using an encryption algorithm and a key. This ensures that even if the data is intercepted or accessed without authorization, it cannot be understood without the corresponding decryption key. Encryption can be applied in two main contexts:
- Data in Transit: Protecting data as it moves across networks, such as when accessing a website, sending an email, or transferring files. TLS is a common method for encrypting data in transit.
- Data at Rest: Securing data stored on devices or in databases, such as files on a hard drive or records in a database. Encryption methods vary depending on the storage medium and the level of security required.
6. Transport Layer Security (TLS)
TLS is a cryptographic protocol that provides secure communication over a computer network. When applied to web traffic, it is known as HTTPS (HTTP Secure). TLS establishes an encrypted connection between a client (e.g., a web browser) and a server, ensuring that all data transmitted is secure and private.
This process involves the exchange of digital certificates to verify the parties’ identity and using encryption algorithms to protect the data from eavesdropping, tampering, or forgery by third parties. TLS protects sensitive information during transmission, such as login credentials, personal information, and payment details.
7. Input Validation
Input validation is the process of ensuring that all data sent to an API is correct and meaningful. Validating inputs helps to prevent common security threats such as SQL injection, cross-site scripting (XSS), and other injection attacks. Implementing strict input validation checks, such as type, length, format, and range checks, can significantly reduce the risk of malicious data compromising the API or the underlying systems.
8. Rate Limiting and Throttling
Rate limiting and throttling are techniques used to control the amount of traffic an API can handle over a specified period. These practices prevent abuse and ensure that the API remains available and responsive for all users. By limiting the number of requests a user can make, APIs can mitigate the risk of denial-of-service (DoS) attacks and ensure fair usage among consumers.
9. Error Handling
Proper error handling is essential for maintaining the security and reliability of an API. Exposing too much information in error messages can give attackers insights into the underlying architecture or potential vulnerabilities. It is important to implement generic error messages that inform the user of the error without revealing sensitive information. Logging errors for internal review can also help identify and mitigate potential security issues.
10. API Versioning
API versioning refers to the practice of managing changes to an API over time. As APIs evolve, their structure, functionality, or behavior changes could break their compatibility with existing clients or applications. To manage this, APIs are versioned. Common versioning strategies include:
- URI Versioning: Including the version number in the API’s URI, such as /api/v1/resource.
- Parameter Versioning: Specifying the version as a request parameter, like /api/resource?version=1.
- Header Versioning: Including the version information in HTTP headers allows the URI to remain unchanged.
API versioning enables developers to introduce new features, fix bugs, and make improvements while maintaining support for existing clients. It provides a clear framework for transitioning between different versions of an API, ensuring that applications continue to function smoothly even as the API evolves.
Why are API security practices important in 2024?
API (Application Programming Interface) security best practices are increasingly important to consider in 2024 due to several evolving factors and trends in the technology and cybersecurity landscapes:
Proliferation of APIs
With the digital transformation accelerating across industries, APIs are becoming the backbone of software development, enabling applications to communicate with each other. The sheer number of APIs in use increases the potential attack surface for cyber threats.
Complexity of API Ecosystems
Modern applications often rely on microservices and cloud-based services, leading to complex API ecosystems. This complexity can introduce vulnerabilities if not properly managed, making robust security practices essential.
Sophisticated Cyber Threats
Cyber threats are becoming more sophisticated, with attackers exploiting vulnerabilities in APIs to gain unauthorized access, steal sensitive data, or disrupt services. Ensuring APIs are secure helps mitigate these risks.
Regulatory Compliance
There is a growing emphasis on data protection and privacy regulations globally, such as GDPR in Europe and CCPA in California. Compliance requires secure handling of personal data, for which APIs are often the conduit, necessitating stringent API security measures.
Increased Reliance on Third-party APIs
Many organizations rely on third-party APIs for critical functionalities. Ensuring the security of these external APIs is crucial to protect the integrity and security of the overall system.
Internet of Things (IoT) Expansion
The expansion of IoT devices, which often communicate through APIs, introduces new vulnerabilities. Securing these APIs is vital to protect against attacks that could compromise not only data but also physical security.
API-specific Attacks
Certain types of attacks are specifically aimed at APIs, such as DDoS (Distributed Denial of Service), man-in-the-middle attacks, and injection attacks. Awareness and mitigation of these threats are essential components of API security best practices.
Shift to API-first Strategies
As more businesses adopt an API-first approach in their digital strategy, ensuring the security of these APIs becomes a primary concern for protecting business assets and customer data.
What are the types of API cyberattacks?
Injection Attacks
These occur when an attacker sends malicious data to an API, tricking it into executing unintended commands. SQL injection, command injection, and cross-site scripting (XSS) are examples of malicious code or queries being injected into an API request.
Broken Authentication
Attackers exploit flaws in authentication mechanisms to impersonate legitimate users. This can involve compromising tokens and keys or exploiting implementation flaws to gain unauthorized access.
Sensitive Data Exposure
APIs that improperly protect sensitive data can lead to exposure. This might occur through inadequate encryption, exposing too much data in responses, or flaws in data access controls.
Man-in-the-Middle (MitM) Attacks
In these attacks, the attacker intercepts communications between the client and the API server to eavesdrop or alter the exchange data, often in unencrypted or poorly secured connections.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks overwhelm an API with a flood of requests, rendering it unavailable to legitimate users. This can be particularly damaging for APIs that are critical to the operation of web services or applications.
Broken Access Control
This occurs when attackers exploit flaws in access control mechanisms to access unauthorized functionality or data. For example, an attacker might manipulate API requests to access other users’ data or privileged functions.
Security Misconfiguration
This broad category includes any security setting that is misconfigured or left insecure, potentially exposing the API to attacks. This can include unnecessary HTTP methods, verbose error messages containing sensitive information, or improperly configured CORS settings.
Cross-Site Request Forgery (CSRF)
In CSRF attacks, an attacker tricks the victim’s browser into sending unauthorized requests to an API on behalf of the victim, often without their knowledge, potentially leading to unauthorized actions.
API Abuse
This involves the legitimate use of an API in a way that is unintended by the API provider, such as excessive use of an API that leads to service degradation or leveraging an API to gather data in bulk for malicious purposes.
Logic Flaws
These are vulnerabilities unique to the business logic of an API, where an attacker manipulates legitimate operations in unintended ways to achieve malicious outcomes. This might involve bypassing workflow sequences or exploiting flawed business logic to escalate privileges or access data.
Further Reading:
- “API Statistics for Understanding API Landscape”
- “API Security Testing: Benefits, Automation & Challenges”
- “API Management in 2024: Top 3 Benefits & 4 Use Cases”
- “Top API Management Tools with Their Features”
- “Top Application Security Tools”
If you have further questions, reach us:


Comments
Your email address will not be published. All fields are required.