8 Best Rapid7 Alternatives in 2024 Based on 1400+ Reviews
Rapid7 is a cybersecurity company known for its array of security solutions, including SIEM (Security Information and Event Management), cloud security, vulnerability management, threat intelligence, dynamic application security testing, and SOAR (Security Orchestration, Automation, and Response).
This article will explore top Rapid7 alternatives whose offerings include Dynamic Application Security Testing (DAST), also known as web vulnerability scanners, as a key service. These vendors also specialize in vulnerability management and cloud security solutions.
Top Rapid7 alternatives: Comparison table
An effective web vulnerability scanner is the one that detects the most vulnerabilities in your web applications with a minimal number of false positives and false negatives.
| Vendors | Starting price | Free trial | Number of reviews* | Average rating* |
|---|---|---|---|---|
| Invicti | N/A | Available | 259 | 4.6 |
| Astra Security | $1,999/year | N/A | 132 | 4.8 |
| Intruder | $1,920/year** | 14-day | 159 | 4.8 |
| Tenable Nessus | $5,990/year | 7-day | 435 | 4.5 |
| Cobalt | $8,500/year*** | N/A | 97 | 4.7 |
| Probely | €980 / year | 14-day | 19 | 4.8 |
| Burp Suite | $3,600/year | Available | 110 | 4.8 |
| Qualys | N/A | Available | 268 | 4.5 |
* Ratings are based on B2B review platforms such as G2, Capterra and TrustRadius.
** Intruder starter price covers 1 application and 1 infrastructure license.
*** $8500: Cobalt starter package includes one user role, allows for the testing of up to 40 dynamic pages, and includes up to 75 endpoints.
Reasons to look for top alternatives to Rapid7
- Pricing: The starting monthly cost for Rapid7’s DAST (Dynamic Application Security Testing) solution is $175 per application. This pricing can be expensive for small to medium-sized enterprises (SMEs) or startups operating on limited budgets. These organizations might look for more affordable alternatives that provide comparable features.1
- Threat discovery: Some users have mentioned that the Rapid7 DAST solution mostly struggles to detect high vulnerabilities, and there is room for enhancement in its threat discovery capabilities.2 3
- False positives and negatives: Some users reported encountering both false positives and false negatives in their scan results.4
1. Invicti
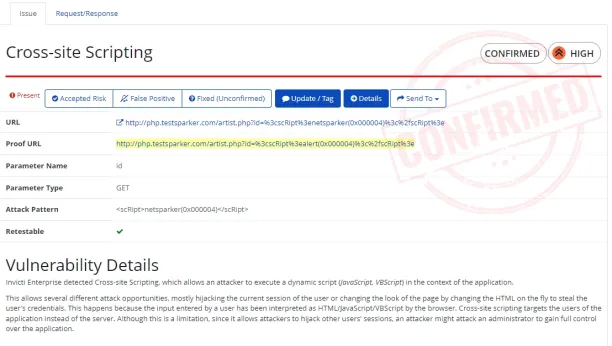
Invicti, previously known as Netsparker, is a dedicated application security testing platform. Its security solutions are designed to seamlessly integrate with an organization’s existing software development lifecycle (SDLC), enhancing its overall cloud security posture management.
Invicti offers two main plans: enterprise and standard. The enterprise plan is suitable for multiple users and provides a comprehensive vulnerability assessment. In contrast, the standard plan is designed for individual use as a desktop web vulnerability scanner.
The standard plan is ideal for professionals such as security engineers, penetration testers, and developers who typically scan fewer than 50 websites. While the Standard plan operates on-site, the enterprise version operates on a browser-based cloud platform, eliminating the need for hardware or software purchases, licenses, installations, or maintenance.
Main features:
- Proof-based vulnerability scanning: Confirms the existence of vulnerabilities by exploiting them in a read-only environment. – proving they are real flaws, and not false positives.
- Different deployment choices: Invicti provides a range of deployment options, accommodating both on-premises and cloud-based environments. In its cloud offering, Invicti includes integrated tools that enhance enterprise workflows, enabling concurrent scanning across multiple web applications.
2. Astra Security
Astra Pentest focuses on vulnerability scanning, specifically targeting penetration testing and vulnerability assessments designed for web applications, APIs, and cloud environments. The service is compatible with several platforms, including GitLab, Jenkins, Bitbucket, Azure, and CircleCI. Astra Pentest services offer three distinct scanning modes:
- Automated Scan: Available in all service plans, this mode provides basic scanning capabilities to quickly identify common cyber attacks.
- Vetted Automated Scan: This mode includes everything in the Automated Scan but adds a crucial review step. Here, security engineers evaluate the results, enhancing the reliability of the findings.
- Manual Pentest: The most thorough option, combining automated scanning with vetted results and an extensive manual penetration test carried out by expert security teams.
Main features:
- Continuous VAPT: Astra’s VAPT (Vulnerability Assessment and Penetration Testing) feature combines expert manual and automated pentesting to ensure a thorough examination of the security posture of web applications.
- Scan logged-in web pages: This feature enables organizations to handle session management and allow for the addition of custom headers, which are essential for scanning pages that require user login.
3. Intruder
Intruder provides a scanning solution that identifies a wide range of security vulnerabilities. It checks for over 75 web-layer issues like SQL injection and cross-site scripting, more than 140,000 infrastructure vulnerabilities, including remote code execution flaws, and other security misconfigurations, such as weak encryption settings.
Intruder’s capabilities include Dynamic Application Security Testing (DAST), as well as API and infrastructure scanning, helping in identifying and resolving more vulnerabilities.
Main features:
- Automated compliance solutions: Intruder offers automated integrations with compliance platforms such as Vanta and Drata.
- Scan single page applications (SPAs): This solution allows users to navigate and interact with complex client-side scripts.
- Smart recon: Determines the number of your systems that are active and need a scanning license. It ensures resources are not wasted scanning targets that are not exposed to the internet.
4. Tenable Nessus
Tenable provides network scanning solutions specifically aimed at assessing network vulnerabilities. Its Nessus tool is capable of detecting outdated or vulnerable versions of web servers and widely-used open-source platforms. Additionally, Nessus offers testing for a range of security vulnerabilities, including cross-site scripting (XSS), SQL injection, and remote file inclusion (RFI).
Main features:
- Scan single page applications: The solution is suitable for the dynamic nature of Single Page Applications (SPAs), can interact with and execute JavaScript dynamically.
- Continuous deployment (CI/CD) pipelines: Tenable Web Application Scanning can be integrated into the continuous integration and continuous deployment (CI/CD) pipelines, allowing for the detection and remediation of potential security vulnerabilities early in the development process.
- Scheduled scans: Setting up automated scans that occur at specific times or on a regular basis, helping organizations ensure consistent security checks without the need for manual initiation.
5. Cobalt

Cobalt is a cloud-based security platform that offers security services such as Penetration Testing as a Service (PTaaS). They provide a DAST scanner that incorporates Dynamic Application Security Testing and Penetration Testing as a Service.
Main features:
- Manual pentests: Manual penetration test (pentest) relies on the expertise of the tester to identify and assess security weaknesses that automated tools might miss.
- Flexible web asset scanning: Perform authenticated or unauthenticated scans on an ad-hoc or scheduled basis.
6. Probely

Probely offers a Dynamic Application Security Testing (DAST) solution that allows organizations to detect vulnerabilities in web applications and APIs. It can scan both traditional web applications and modern single-page applications (SPAs). Probely’s pricing model offers unlimited scans and employs a usage-based system where costs depend on the amount of scan time utilized.
Main features:
- Customizable scanning settings: They provide two methods for scanning web assets: scheduled and partial scanning. Scheduled scanning automates security checks at predetermined times, while partial scanning focuses on specific parts of an application instead of the entire application during each scan.
- Headless-Chrome based spider: This functionality allows organizations to simulate human interactions within a web application by engaging in activities such as clicking on links and correctly filling out forms. It enhances the handling of JavaScript applications by monitoring events, and it also supports advanced web technologies, including shadow DOM, and pushState.
7. Burp Suite

Burp Suite is a well-known tool in the application security industry. The web vulnerability scanning capabilities of Burp Suite are exclusively available in its Professional and Enterprise editions.
Main features:
- Built-in browser: Allows users to alter every HTTP request that it processes.
- Embedded browser: Features an integrated Chromium browser that runs JavaScript within the targeted application. The scanner is capable of interpreting and analyzing any client-side JavaScript it encounters during its operations.
- OAST: Includes the out-of-band application security testing (OAST) feature to detect vulnerabilities that are not detectable through standard testing methods, such as blind or asynchronous vulnerabilities.
8. Qualys
The Qualys Web Application Security Scanner (WAS) is a cloud-based tool that forms part of the broader offerings of the Qualys Cloud Platform. It helps organizations identify coding problems early by integrating with CI/CD pipelines in platforms like Azure and GitHub.
Main features:
- Scanning of Swagger-based Representational State Transfer (REST) APIs: Qualys WAS conducts scans of Swagger-based Representational State Transfer (REST) APIs and Simple Object Access Protocol (SOAP) web services, utilizing the Swagger specification to test REST APIs.
- Postman support: It allows users to group related requests into a file known as a Postman Collection, which can be shared with others. With the introduction of Postman Collection support in Qualys WAS, users have the ability to configure their API scans using these collections.
- Browser recorder: Qualys Chrome extension (available for free to all users) enables users to record web browser activity and save the scripts for automated testing tasks. These scripts can be replayed in Qualys WAS, helping the scanning engine to navigate complex authentication procedures.
If you have further questions, reach us:
External Links
- 1. Rapid7 Review G2
- 2. Rapid7 Review Gartner
- 3. Rapid7 Review G2
- 4. Rapid7 Review Gartner

Comments
Your email address will not be published. All fields are required.