Network Segmentation vs Microsegmentation in 2024: 6 Key Differences
Network security statistics show that ~90% of organizations have reported at least one data breach or cyber incident in 2022.
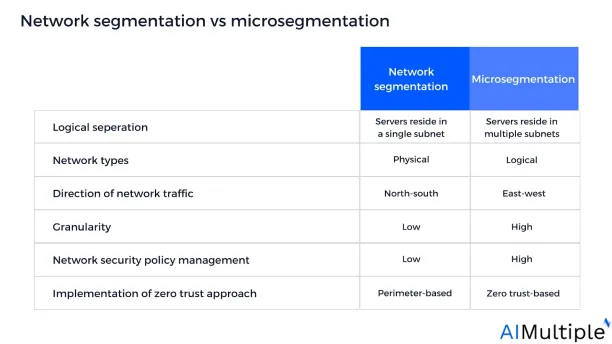
Organizations may enforce network segmentation or microsegmentation technologies by dividing their network into sub-parts to govern, manage, and prevent data breaches or cyber incidents. However, choosing the most suitable technology for your organization might be challenging since both approaches offer several distinct features. Network segmentation enforces traditional castle-to-moat policies that leverage firewall rules at network boundaries; microsegmentation creates security zones that can be configured down to the host (computer) level across individual subnets.
We recommend enterprises and cloud-native businesses embrace microsegmentation while SMEs and mid-market companies with limited network security budgets may start off only with network segmentation.
Figure 1: Network segmentation vs microsegmentation
Network segmentation vs microsegmentation: How to choose & what to use?
Enterprises (e.g. Fortune 1000, global banks, leading insurance companies, and enterprise SaaS) with complex network security use cases are recommended to adopt microsegmentation. Traditional network segmentation methods might not be effective for large organizations with numerous network security use cases since these tools are not built for highly granular, application-level security permissions.
Cloud-native: Organizations that use several software, cloud, and SaaS platforms are recommended to adopt microsegmentation technologies. These organizations are more vulnerable to cloud-related threats and need to secure application workloads at a high granular server-to-server level.
SMEs: Traditional perimeter-based network segmentation is an easy-to-implement solution for organizations that:
- Require overarching security for their entire infrastructure without detailed application-level or agent-based policy configurations.
- Have less complex networks with low-security needs.
- Have limited technical labor.
- Have limited network security budgets.
If you want a more detailed answer than these high level recommendations, these parameters can help determine the right approach for your company:
- Business scope: Implementing microsegmentation across core business areas can significantly reduce the lateral flow of a ransomware attack.1Companies with numerous branches and departments seeking may choose microsegmentaton to enhance intra-network traffic.
- Level of security needed: Organizations with high network security needs such as Fortune 1000, global banks, insurance companies, or multinational corporations (MNCs) may select microsegmentation technologies to use finer-grained management and application-level security.
- Level of granularity needed: Microsegmentation provides far more granular control and is significantly more effective to implement and administer at scale. Large-scale private or public companies may use microsegmentation to execute strong network traffic control.
- Level of identity-based zero trust security needed: The zero trust model employs the “never trust, always verify” principle rather than defending the network perimeter. This ensures that only verified users can access specific content. Companies that need rigid identity verification for employees and devices may implement microsegmentation with zero trust architecture.
- Level of granularity needed: Microsegmentation provides far more granular control and is significantly more effective to implement and administer at scale. Large-scale private or public companies may use microsegmentation to execute strong network traffic control.
- Network complexity: 35% of IT specialists say that network complexity is an obstacle they encounter when segmenting their network.2Organizations with less complex networks may utilize traditional network segmentation.
- Number of network components: Companies that use several hardware, software, cloud, or SaaS platforms across their network can use microsegmentation to eliminate unnecessary network zones. For example, a CISO of a 300-employee company states that microsegmentation enhanced network visibility in their organization, enabling them to identify and eliminate 15 no-longer-needed zones with license costs.3
- Scope of network security policy configurations: Network security policy management statistics show that the rate of all cyber incidents caused by security misconfigurations is 35%. Companies with thousands of complex security rules and firewalls might leverage microsegmentation technologies to manage misconfigurations at scale.
- Scope of network traffic: Organizations with extensive east-west data transfer within the internal network may select microsegmentation technologies to divide their data centers or cloud environment into logical units.
- Numbers of employees: Companies with hundreds of employees may choose microsegmentation technologies since microsegmentation allows host-level segmentation that enables administrators to set user-based rules.
- Number of network components: Companies that use several hardware, software, cloud, or SaaS platforms across their network can use microsegmentation to eliminate unnecessary network zones. For example, a CISO of a 300-employee company states that microsegmentation enhanced network visibility in their organization, enabling them to identify and eliminate 15 no-longer-needed zones with license costs.3
- Financial budget: Microsegmentation integration with a security stack is expected to cost between $40K to $100K on average.4Companies with lower finances and older infrastructure may choose network segmentation technology.
- Skilled labor availability: ~40% of IT specialists state that lack of skills and expertise for segmentation is their main issue for implementing microsegmentation.5Companies with low-skilled labor or resources may select network segmentation since segmenting physical network VLANS and access control lists requires less technical knowledge compared to developing logical microsegments.
Read more: Microsegmentation tools, network security audit tools, SDP software.
6 key differences between network segmentation and microsegmentation
1- Logical separation
- Network segmentation — creates security zones across VLANs, it cannot restrict server-to-server connectivity inside a VLAN. This is because all the application servers reside on a single subnetwork.
- Microsegmentation — creates security zones per device in data centers and cloud environments. Microsegmentation isolates workloads individually.
Figure 2: Comparison between network segmentation and microsegmentation – using VLANs –
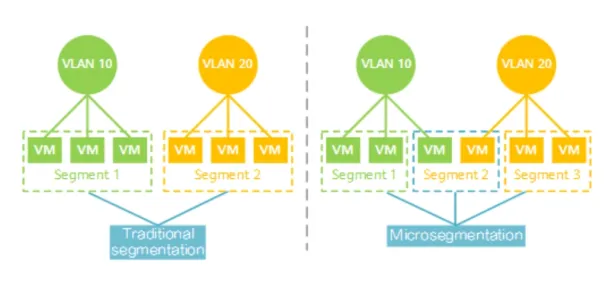
Source: Huawei6
2- Network types
- Network segmentation — leverages physical segmentation by dividing hardware into separate zones.
- Microsegmentation — leverages logical segmentation in both on-premises data centers and cloud computing deployments — any place where workloads run. Servers, virtual machines, containers, and microservices can all be segmented with logical microsegmentation.
3- Direction of network traffic
- Network segmentation — is designed for north-south traffic (client-server data flows between data centers).
- Microsegmentation — is designed for east-west traffic (server-to-server data flows between applications).
How can network segmentation secure north-south traffic?
Network segmentation divides the north-south traffic by using VLANs (virtual local area networks), and firewalls to provide an extra layer of defense for user and information protection.
This approach divides the network into smaller networks and isolates devices, servers, and applications from the rest of the network. For example, network traffic from host B to host C is filtered by the initial network barrier (the perimeter in the figure).
Figure 3: North-South traffic on a graphical representation
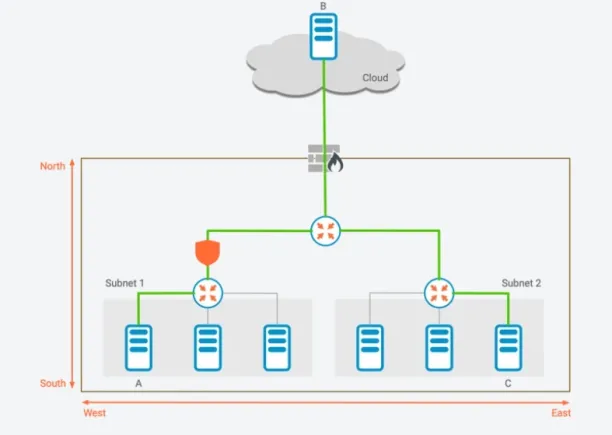
Source: Zentera7
How can microsegmentation secure east-west traffic?
Microsegmentation can deliver an agent-based east-west traffic deployment that secures applications in the operating system. For example, east-west traffic can be secured by dividing data centers into logical units (such as host A and host D shown below), and network administrators can create separate security policies for each.
Figure 4: East-West traffic on a graphical representation
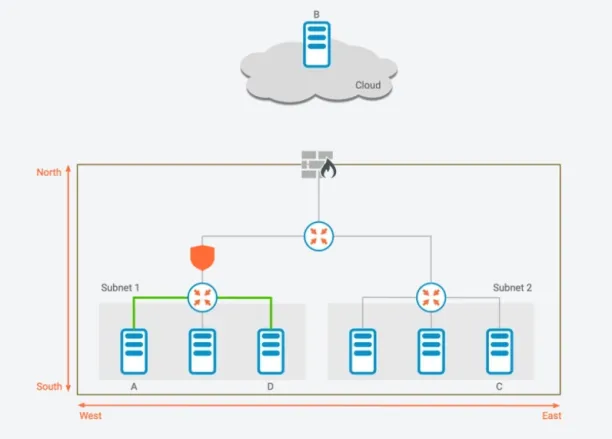
Source: Zentera8
4- Granularity
- Network segmentation uses a perimeter-based segmentation that requires each network zone to have its internet connection, physical wiring, and a firewall. This sort of division is based on trust, with everything inside trusted and anything external not. There are limited constraints on internal resources, which typically function across a flat network with low internal network segmentation.
- Microsegmentation provides highly granular levels in a network, down to isolating individual workloads* (as opposed to isolating applications, devices, or networks).
*Workload: Any program or application that uses some amount of memory and CPU.
5- Network security policy management
- Network segmentation lacks detailed network security policies or guidelines for the entire network resources to manage critical tasks such as access control, verification, and risk assessment.
- Microsegmentation enforces network security policies overarching the whole network and its resources, encompassing all endpoints and devices. This allows organizations to grant or deny access to network functions based on risk evaluations in response to user behavior and activities.
Read more: Network security policy management, network security policy management solutions.
6- Implementation of zero-trust approach
- Network segmentation is focused on trust-based perimeter protection for north-south traffic, presuming that east-west movement in data centers is safe.
- Microsegmentation enables zero-trust technology that separates the data center network into smaller security zones which allow increased control over data traffic.
Pros & cons of network segmentation and microsegmentation
Network segmentation
Pros
- Simple network traffic management: Provides simple hardware firewalls for managing north-south traffic.
Cons
- Low granularity: It can be difficult to achieve granular access standards. Since application servers may reside in the subnets.
- No zero-trust approach: Network segmentation approach is built on trust, stating that each network element within the network perimeter is secure, however, trusting users and devices within a hypothetical “corporate perimeter” or users and devices connected via a VPN is insufficient.
- Weak protection against laterally moving threats: Network segmentation provides only perimeter protection for north-south traffic, making network segmentation an inefficient approach against lateral moving threats such as advanced persistent threats (APTs). APT is a stealthy threat vector that moves laterally and gains unauthorized access to a computer network.
Microsegmentation
Pros
- Reduced attack surface: The granularity of control over security zones allows for more specific security policies and procedures, and better control over security threats.
- Transparent view of network infrastructure: Smaller segmented zones provide precise insights into various network components (e.g. routers, devices, machines).
- Lower risk pivoting attacks: The granularity of the policies and firewall rules enabled by microsegmentation makes it easier to regulate these unexpected traffic kinds.
- Stronger operational efficiency: Microsegmentation uses software-defined networking (SDN) technologies and virtualization, lowering initial hardware costs and simplifying management by centralizing policy enforcement and control, resulting in increased operational efficiency compared to traditional network segmentation.
- Zero trust network access (ZTNA) technology: Microsegmentation may apply the zero trust architecture by providing stringent access controls (e.g. mandatory access control, RBAC) and constant verification, reducing the risk of insider attacks.
Cons
- Complex network management: Identifying and setting the appropriate microsegments and network security policies can be challenging, especially in an ever-changing data center.
- High agent dependency: Some microsegmentation systems require installing additional software agents on each virtual machine (VM), leading to intricacy.
- Increased need for micromanagement: Microsegmentation can lead to micromanagement. This may occur if administrators segment several network zones each with different components. Highly granular segmentation increases the workload for security and operations teams while providing little extra benefits. It necessitates additional network obstacles and is more likely to result in bottlenecks.
What are network segmentation examples?
Segmentation is accomplished using firewalls, virtual local area networks (VLANs), and software-defined networking (SDN).
- VLAN segmentation: VLAN segmentation divides networks into VLANs or subnets. VLANs are tiny network segments that interconnect hosts virtually. Subnets use IP addresses to divide the network into segments that are interlinked by networking devices.
- Firewall segmentation: Firewall segmentation places firewalls within a network or data center to establish internal zones that separate operational regions, limiting attack surfaces and blocking threats from propagating outside the zone. One example may be separating marketing applications from accounting.
- Software-defined networking (SDN) segmentation: SDN segmentation is a microsegmentation method in which an administrator controls networks using software such as an API (application programming interface).
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. ”The State of Segmentation 2023”. Akamai. 2023. Retrieved April 23, 2024.
- 2. ”The State of Segmentation 2023”. Akamai. 2023. Retrieved April 23, 2024.
- 3. ”Building A Business Case for Microsegmentation Part |: Put Zero Trust At The Core“. AIRGAP, a Zscaler Company. 2024. Retrieved April 24, 2024.
- 4. ”Building A Business Case for Microsegmentation Part |: Put Zero Trust At The Core“. AIRGAP, a Zscaler Company. 2024. Retrieved April 23, 2024.
- 5. ”The State of Segmentation 2023”. Akamai. 2023. Retrieved April 23, 2024.
- 6. ”What Is Microsegmentation?”. Huawei. October 22, 2021. Retrieved April 21, 2024.
- 7. ”Mastering Micro-Segmentation: Understanding North-South vs. East-West Strategies”. Zentera. April 12, 2024. Retrieved April 21, 2024.
- 8. ”Mastering Micro-Segmentation: Understanding North-South vs. East-West Strategies”. Zentera. April 12, 2024. Retrieved April 21, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.