Top 10 Cyberhaven Competitors & Alternatives in 2024


Cyberhaven is a popular name in cybersecurity offering solutions such as DLP software and insider threat management, but some shortcomings were identified during AIMultiple’s analysis of over 1,000 user reviews on Cyberhaven. We recommend reviewing its top alternatives before buying or renewing a Cyberhaven product license. We compare Cyberhaven’s top DLP alternatives since that is its key offering.
Comparison of Cyberhaven DLP alternatives
Table 1. Cyberhaven DLP alternatives
| Vendor | # of Reviews* | User Rating* | Pricing | Free Trial | Supported OS | Deployment Options*** |
|---|---|---|---|---|---|---|
| Endpoint Protector by CoSoSys | 147 | 4.5 | N/A | ✅ | Windows Mac Linux Thin client** | On-premise VDI SaaS |
| Trellix DLP (McAfee) | 1,792 | 4.2 | $73 – $170 /month | ✖ | Windows Mac | On-premise |
| Acronis Cyber Protect | 674 | 4.3 | N/A | ✅ 30-day trial | Windows Mac Linux | SaaS |
| Sophos Intercept X | 312 | 4.5 | N/A | ✅ | Windows Mac Linux Unix | On-premise VDI SaaS |
| Safetica DLP | 244 | 4.6 | N/A | ✅ 30-day trial | Windows Mac Linux | On-premise SaaS |
| Teramind DLP | 197 | 4.6 | N/A | ✅ | Windows Mac Linux | VDI SaaS |
| Symantec DLP by Broadcom | 189 | 4.3 | N/A | ✖ | Windows Mac | On-premise VDI SaaS |
| Digital Guardian Endpoint DLP | 144 | 3.9 | N/A | ✖ | Windows Mac | SaaS |
| Proofpoint Information Protection | 95 | 4.5 | N/A | ✅ | Windows Mac | SaaS |
| Microsoft Purview DLP | 92 | 4.6 | ~$153 /month | ✅ 3-month trial | Windows Mac | SaaS |
| Cyberhaven DLP | 30 | 4.8 | N/A | ✖ | Windows Mac Linux | VDI SaaS |
Inclusion criteria for the Table
* Data source: Leading B2B review platforms.
** Thin client support: A lightweight software layer specifically designed to manage a network-based computing environment.
*** Cloud deployment is offered by all products. VDI: Virtual desktop infrastructure.
Requirements for inclusion in the Table:
- Relevance of their offerings
- Total user reviews: 50+
- 100+ employees
Sorting: Vendors with links to their websites are sponsors of AIMultiple and are listed at the top. The remaining products are ranked based on their total number of reviews.
Cyberhaven overview
Cyberhaven is a cybersecurity company based in Palo Alto, California. It was founded in 2016 and focuses on providing data loss prevention (DLP) solutions. On its website, it lists data detection and response programs with the following features:
- Data loss prevention
- Insider risk management
- Cloud data security
Shortcoming
Our analysis of user reviews from leading review platforms identified some drawbacks and shortcomings to using Cyebrhaven’s platform, which might lead its customers to consider its alternatives. This section summarizes those shortcomings:
1. Software alert errors
The DLP solution requires effort to set up custom policies. It triggers individual alerts for each policy met rather than consolidating them by severity. Additionally, the DLP tool occasionally misattributes alerts to the last active URL instead of the relevant one.1
2. Lack of support
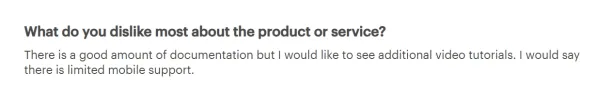
Customers indicated that there is a lack of tutorial videos available for the onboarding process and limited mobile support.2
3. Lack of API endpoints
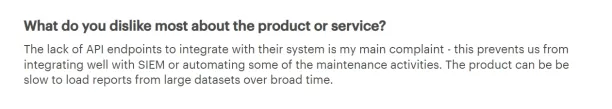
The DLP solution by Cyberhaven has a lack of API endpoints, which hinders integration with systems like SIEM and automation of maintenance tasks. Additionally, the product loads reports slowly when handling large datasets over extended periods.3
Detailed analysis of the top 3 alternatives
This section offers some pros and cons of the top 3 alternatives of Cyberhaven based on reviews analyzed from leading review platforms.
1. Endpoint Protector by CoSoSys
Endpoint Protector by CoSoSys, which has now joined Netwrix, is one of the most suitable alternatives to Cyberhaven DLP because it provides a data protection product among other data security solutions. Its offerings include device control, content-aware protection, enforced encryption, and eDiscovery, as outlined on its website. Based in North Carolina, Endpoint Protector claims to deliver a competitive advantage with its holistic approach to protecting sensitive data.
Pros
1. Effective device control
According to various user reviews, Endpoint Protector’s device control features are one of the best in the market.4 5
2. Supported operating systems
Compared to Cyberhaven and other alternatives, Endpoint Protector’s solution supports a broader range of operating systems, including Thin Clients. This extensive compatibility allows businesses to secure a wide variety of devices and platforms.
3. Software functionality
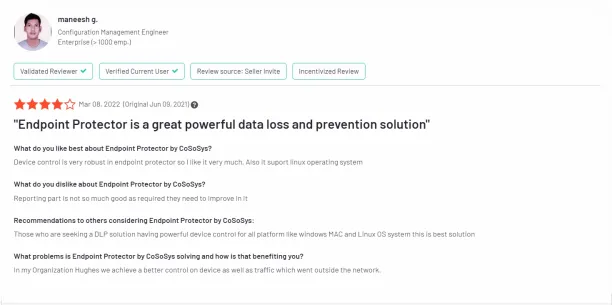
A user review liked Endpoint’s DLP software for its granularity, effective group administration, quick updates, and its panic mode.6
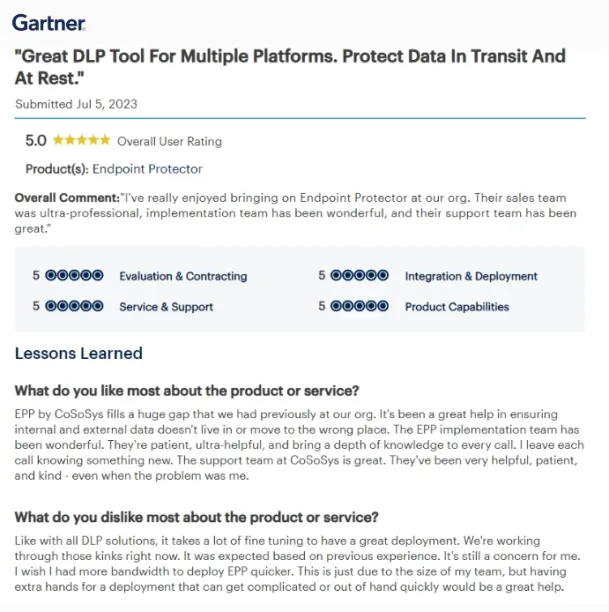
4. Implementation team and customer support
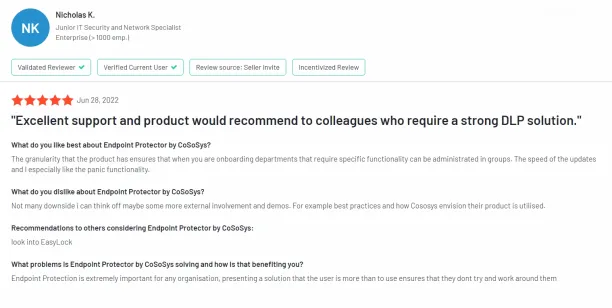
Its DLP solution is detailed, and customer support is helpful. The review also states that even though deployment requires some effort, the implementation team makes the process easy.7
Cons
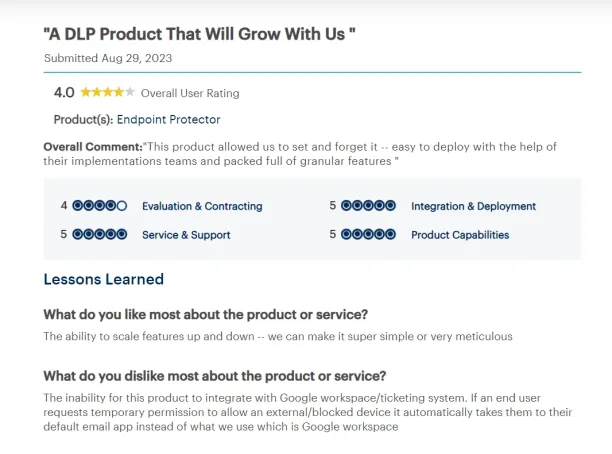
1. Integration with Google Workspace
The review points out that the product cannot integrate with Google Workspace and ticketing systems. When users seek temporary access for a blocked or external device, it redirects them to their default email app instead of Google Workspace, which is used by the reviewer’s organization.8
2. File sharing
The review acknowledges the product’s positive features but points out some issues. Firstly, there are frequent false positives in file-sharing alerts from a specific application, occurring even when the user isn’t logged into the application. Secondly, there is a discrepancy between the activities performed by users and the activities that are logged by the system.9
2. Trellix DLP (McAfee)
Based in Texas, Trellix was founded in 2022 following the merger of McAfee Endpoint Security and FireEye. Trellix is also a suitable alternative to Cyberhaven DLP since it also claims to offer data loss prevention solutions, among other cybersecurity products. Trellix is currently owned by Symphony Technology Group. We analyzed numerous user reviews from leading review platforms to identify some pros and cons.
Pros
1. Easy to configure
Security products are often complex to set up, which can be challenging for companies with small teams. Trellix is user-friendly and doesn’t require extensive configuration, making it a good choice for teams without a dedicated expert.10
2. Many features
Trellix’s DLp product offers a variety of features, including customizable reporting options.11
Cons
1. Missing features
The Linux version lacks certain features found in the Mac and Windows versions, including malware protection. The reporting tool is quite basic and offers limited options for generating custom reports. Additionally, the pricing might be considered higher than that of competitors.12
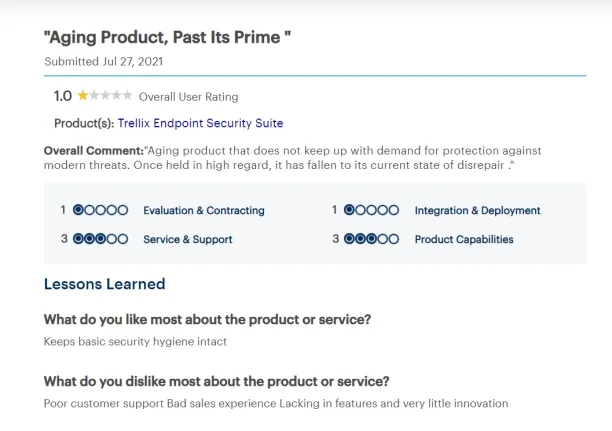
2. Falling performance
The advanced endpoint detection product has aged and struggles to meet the demand for protection against emerging security threats. While it was once highly esteemed, its effectiveness and condition have notably declined.13
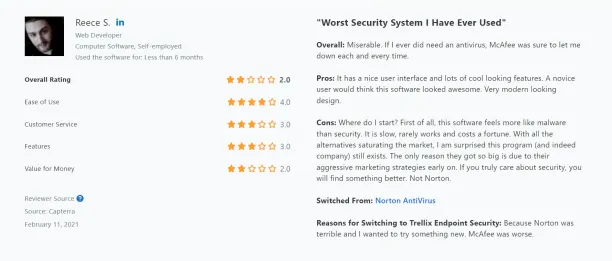
3. Expensive and slow
According to a review, Trellix’s product operates slowly, often fails to function correctly, and is quite expensive compared to other solutions. With so many better alternatives available, it’s surprising that this software and its company are still in business. Their success seems largely due to aggressive early marketing. Those serious about security should consider other, more effective options. Norton is not recommended.14
3. Acronis Cyber Protect
Founded in 2003 and headquartered in Switzerland, Acronis is another suitable alternative for Cyberhaven since it claims to specialize in data protection and cybersecurity solutions for sectors like IT, telecommunications, healthcare, and education.
Pros
1. User friendly
A customer who used its DLP solution stated that Acronis’s platform is easy-to-use for experienced professionals.15
Cons
1. Expensive and complex
A customer stated that Acronis’s platform is complex for inexperienced users and expensive for SMEs & SMBs.16
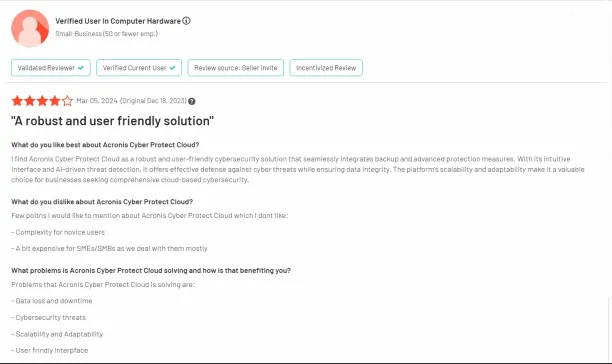
2. Limited configuration
Some customers faced challenges with the compatibility of its EDR and data protection solutions since they only support Windows.17
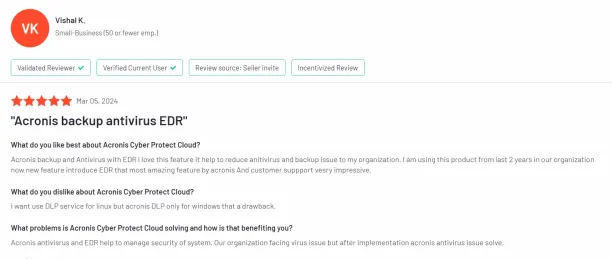
3. Complex UI and documentation
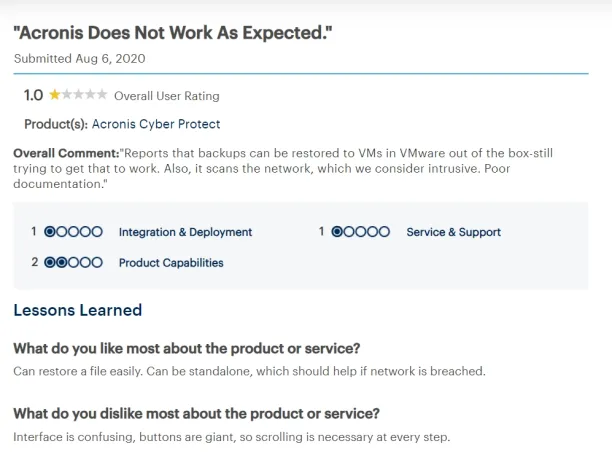
Some customers state that its interface is confusing, its network scanning feature is intrusive, and its documentation is poor.18
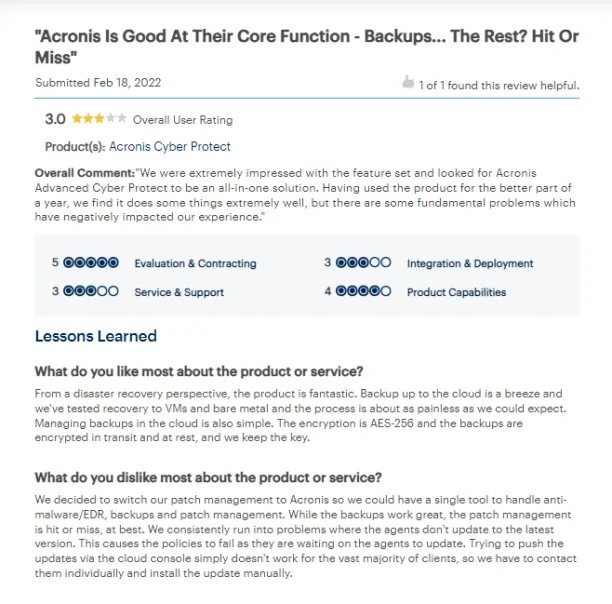
4. Patch management issues
After using the product for nearly a year, some customers encountered several fundamental issues with the tool’s patch management and updates that adversely affected their overall experience with the software.19
FAQs for Cyberhaven alternatives
-
Why use a DLP software like Cyberhaven?
1. Protecting sensitive data
Data loss prevention (DLP) software is essential for protecting sensitive data within an organization. It uses advanced user data classification, sensitive data discovery, and entity behavior analytics to identify and protect critical business data from unauthorized access and breaches. DLP tools help classify sensitive data, whether structured or unstructured, and use continuous monitoring to prevent data leaks. By incorporating data protection regulations into its operations, DLP software ensures that enterprises comply with legal requirements, thereby strengthening their data security posture management. This type of software is crucial for infrastructure and security managers who are tasked with maintaining the integrity and confidentiality of sensitive data.
2. Enhancing data security
By monitoring sensitive data and user behavior, DLP software plays a vital role in insider risk management. It utilizes user behavior analytics and monitoring to detect and respond to suspicious activities, helping to prevent malicious user behavior that could lead to data breaches. Data loss prevention DLP tools offer response capabilities, such as network access control and automated data discovery, which help in immediately addressing any security or compliance event. For businesses that operate across multiple cloud providers, DLP software provides tools to manage data risks effectively, monitor data exfiltration, and protect cloud data assets, thereby enhancing overall data security and protecting against cloud data compromise.
3. Compliance and data management
DLP software is instrumental in helping businesses meet data protection regulations by offering advanced data protection and sensitive data management solutions. With features like automated data discovery and extended data retention capabilities, these tools help centralize data protection and data management, making it easier to audit user behavior, manage user access, and log files. Whether dealing with native cloud data stores or multiple data stores across various environments, DLP tools help in accurate data discovery and expand tracking capabilities, which are essential for maintaining compliance with evolving data protection standards. These capabilities enable organizations to deliver data protection services more efficiently, ensuring that all sensitive information is adequately secured against potential data leaks and data leakage incidents. -
What is DLP?
Data Loss Prevention (DLP) is a strategic approach to ensuring that sensitive data, such as critical business data or personal employee data, is not lost, misused, or accessed by unauthorized users. DLP solutions are crucial in protecting sensitive data by monitoring, detecting, and blocking data leaks or breaches. These systems help organizations comply with data protection regulations and improve their data security posture by classifying and protecting both structured and unstructured data.
Further reading
- Tackling Critical Data Protection Challenges
- Top 10 LLM DLP Best Practices
- Top 7 AI DLP Best Practices with Case Studies
If you need further help in finding a vendor or have any questions, feel free to contact us:
External resources
- 1. Cyberhaven negative review 1. G2. Accessed: 01/May/2024.
- 2. Cyberhaven negative review 2. Gartner. Accessed: 01/May/2024.
- 3. Cyberhaven negative review 3. Gartner. Accessed: 01/May/2024.
- 4. Endpoint Protector’s strong device control review 1. G2. Accessed: 01/May/2024.
- 5. Endpoint Protector’s strong device control review 2. G2. Accessed: 01/May/2024.
- 6. Endpoint Protector by CoSoSys customer review 1. G2. Accessed: 01/May/2024.
- 7. Endpoint Protector by CoSoSys customer review 2. Gartner. Accessed: 01/May/2024.
- 8. Endpoint Protector by CoSoSys negative customer review 1. Gartner. Accessed: 01/May/2024.
- 9. Endpoint Protector by CoSoSys negative customer review 2. Gartner. Accessed: 01/May/2024.
- 10. Trellix positive review 1. Gartner. Accessed: 01/May/2024.
- 11. Trellix positive review 2. Gartner. Accessed: 01/May/2024.
- 12. Trellix negative review 1. Gartner. Accessed: 01/May/2024.
- 13. Trellix negative review 2. Gartner. Accessed: 01/May/2024.
- 14. Trellix negative review 3. Capterra. Accessed: 01/May/2024.
- 15. Acronis positive customer review 1. G2. Accessed: 01/May/2024.
- 16. Acronis negative customer review 1. G2. Accessed: 01/May/2024.
- 17. Acronis negative customer review 2. G2. Accessed: 01/May/2024.
- 18. Acronis negative customer review 3. Gartner. Accessed: 01/May/2024.
- 19. Acronis negative customer review 4. Gartner. Accessed: 01/May/2024.

Comments
Your email address will not be published. All fields are required.