As businesses collect a vast amount of customer data to gain insights, improve their products and services, and monetize their data assets, they can become vulnerable to cyber threats and data breaches. The cost of breaches is rising every year, reaching ~$4.2M per breach.
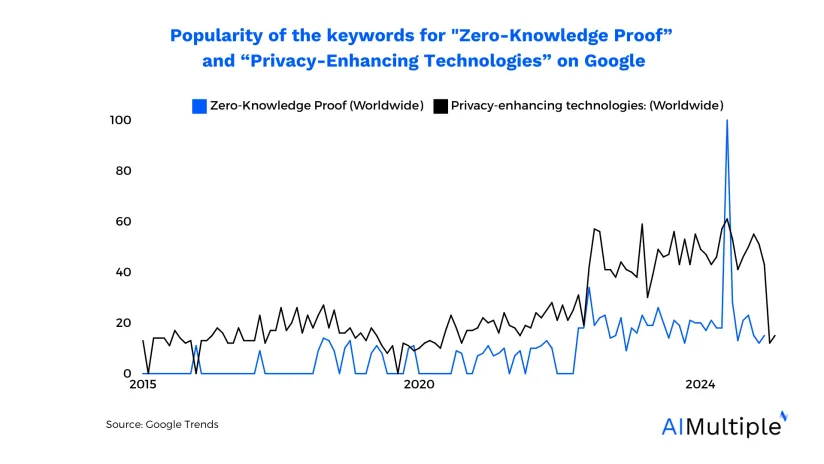
Privacy-enhancing technologies (PETs) such as zero-knowledge proofs (ZKPs) provide ways for businesses to protect their sensitive data. We describe the functioning of ZKP and examples of its application in this article to assist executives in strengthening their organization’s cybersecurity posture.
What are zero-knowledge proofs (ZKPs)?
A zero-knowledge proof (ZKP), also called a zero-knowledge protocol, is a mathematical technique to verify the truth of information without revealing the information itself. The method was first introduced by researchers from MIT in a 1985 paper.1 ZKPs allow one party (the prover) to prove to another party (the verifier) that they know a certain piece of information (such as a password or a solution) without revealing any details about that information.
How do zero-knowledge proofs work?
ZKPs have three essential properties:
1. Completeness: If the statement is true, an honest prover can convince an honest verifier of this fact.
2. Soundness: If the statement is false, no dishonest prover can convince the honest verifier that the statement is true, except with a very small probability.
3. Zero-Knowledge: If the statement is true, the verifier learns nothing other than the fact that the statement is true. In other words, no additional information about the proof or underlying data is leaked.
We can explain ZKPs with an example. Suppose you (the prover) have a color-blind friend (the verifier) who cannot distinguish a green and a red ball from each other (have zero knowledge about whether the balls are different colors). You need to prove that the colors of the balls are different but your friend needs something more than your words to be convinced. A ZKP method for this problem would be like this:
1. Setup:
You (the prover) have two balls, one red and one green, but your color-blind friend (the verifier) cannot distinguish between them. You need to prove that the balls are different colors without revealing which is red or green.
2. Commitment:
Your friend holds both balls, one in each hand, and shows them to you. Since you are not color-blind, you can clearly tell which ball is red and which is green. Your friend then hides the balls behind their back, keeping track of which ball is in which hand.
3. Challenge:
Your friend either switches the balls between their hands or keeps them in the same position, and then presents them to you again. Without revealing which ball is red or green, you must tell if they switched the balls or not.
4. Response:
Since you can distinguish the colors, you easily tell if the balls were switched and give your answer.
5. Verification:
Initially, your friend thinks you might just be guessing, as there’s a 50% chance of being right by chance. But after repeating the test multiple times, the probability of guessing correctly every time becomes very low. This convinces your friend that the balls are indeed different colors, even though they still cannot tell which is red or green.
What are some applications and use cases of zero-knowledge proofs?
Blockchain
The transparency of public blockchains such as Bitcoin and Ethereum enable public verification of transactions. However, it also implies little privacy and can lead to deanonymization of users.2 . Zero-knowledge proofs can introduce more privacy to public blockchains.
Real-Life Example
For instance, the cryptocurrency Zcash is based on Zero-Knowledge Succinct Non-Interactive Argument of Knowledge (zk-SNARK), a type of zero-knowledge cryptographic method. 3 . Another example is Zero-Knowledge Scalable Transparent Argument of Knowledge (zk-STARK), which is used in the Ethereum blockchain and provides privacy and scalability.
Finance
Zero-knowledge proofs (ZKPs) enhance financial privacy by verifying transactions without revealing amounts or identities. They are crucial for privacy-focused cryptocurrencies and secure financial systems. ZKPs also aid regulatory compliance, allowing institutions to prove adherence to KYC and AML without exposing sensitive data. Additionally, they improve auditing by ensuring report accuracy without disclosing transaction details.
Real-life Example
ING uses ZKPs that allow customers to prove that their secret number lies in a known range.4 . For example, a mortgage applicant can prove that their income is in the admissible range without revealing their exact salary.
Online voting
In online voting, zero-knowledge proofs (ZKPs) can ensure the integrity and privacy of the voting process. Voters can prove that their vote has been cast and counted correctly without revealing their vote’s content. This preserves anonymity while ensuring that each vote is legitimate and that no voter can cast multiple votes. ZKPs also provide transparency by allowing voters to verify that the election outcome is correct, all while protecting voter identities and preventing tampering, making online voting both secure and private.
Authentication
In authentication, zero-knowledge proofs (ZKPs) allow users to prove they know a password or possess a credential without transmitting the password or revealing the credential itself. This enhances security by preventing sensitive information from being exposed to potential attackers, even if the communication channel is compromised. ZKPs can be used in password-less login systems, where users authenticate without ever sharing their secret data, reducing the risk of breaches, phishing, or replay attacks, and making the overall process more secure and privacy-preserving.
Machine Learning
ZKPs can allow the owner of a machine learning algorithm to convince others about the results of the model without revealing any information about the ML model itself. 5 For instance, a model provider can prove that a model was trained on specific data without revealing the dataset itself, which is crucial in industries with sensitive information like healthcare or finance.
Similarly, ZKPs can allow a party to prove that a machine learning algorithm has been correctly applied without exposing the algorithm or its inputs, enabling secure collaboration and verifiable computation without compromising proprietary or confidential data.
What are the different types of zero-knowledge proofs?
There are two main types of zero-knowledge proofs:
- Interactive zero-knowledge proofs: In this type of ZKPs, the prover and the verifier interact several times. The verifier challenges the prover who provides replies to these challenges until the verifier is convinced.
- Non-interactive zero-knowledge proofs: In this type of ZKPs, proof delivered by the prover can be verified by the verifier only once at any time. This type of ZKPs requires more computational power than interactive ZKPs.
What are the challenges of zero-knowledge proofs?
- No 100% guarantee: Even if the probability of verification by the verifier while the prover is lying can be significantly low, ZKPs don’t guarantee that the claim is valid 100%. As demonstrated above, the probability of a prover lying decreases in each iteration of the ball-picking process, but it can never reach zero. Thus, zero-knowledge proofs aren’t actual proofs in a mathematical sense.
- Computation intensity: Algorithms used are computationally intense as they require many interactions between the verifier and the prover (in interactive ZKPs), or require a lot of computational capabilities (in non-interactive ZKPs). This makes ZKPs unsuitable for slow or mobile devices.
For more on data privacy and information security, you can check our other articles:
- Privacy Enhancing Technologies (PETs) & Use Cases.
- Top 9 Cybersecurity Best Practices for Corporations.
- Top 6 Data Security Best Practices.
- In-depth Guide to Zero Trust Paradigm & Zero Trust Architecture.
If you have other questions about zero-knowledge proofs or other privacy-enhancing technologies, we can help:
External Links
- 1. Goldwasser, S.; Micali, S.; Rackoff, C. (1989), “The knowledge complexity of interactive proof systems” (PDF), SIAM Journal on Computing, 18 (1): 186–208.
- 2. Prosecutors Trace $13.4M in Bitcoins From the Silk Road to Ulbricht's Laptop | WIRED. WIRED
- 3. What are zk-SNARKs? - Z.Cash. Z.Cash
- 4. What does blockchain mean to ING? • ING.
- 5. Zero-Knowledge Proofs for Machine Learning | Proceedings of the 2020 Workshop on Privacy-Preserving Machine Learning in Practice.

Comments
Your email address will not be published. All fields are required.