Based on our DLP review benchmark, user reviews & feature comparisons, here are the top 10 USB Blocking Software alternatives. See why we selected them by following the links below:
- Endpoint Protector for strong device control
- Trellix Endpoint DLP
- SafeticaONE Protection DLP
- Symantec Endpoint DLP
- Microsoft Intune for easy Microsoft 365 ecosystem integration.
- ThreatLocker Storage Control
- Forcepoint DLP
- GTB Endpoint Enterprise DLP
- Fortra Digital Guardian Endpoint DLP
- ManageEngine Device Control Plus
Unmanaged devices increase data breach risk. Control over devices, including USBs, is key to effective cybersecurity.
See top USB blocking software with key features such as USB encryption, content inspection, and reporting capabilities:
Top USB blocking software comparison
Features
| Product | USB encryption | Content inspection | Reporting |
|---|---|---|---|
| Endpoint Protector by CoSoSys | ✅ | ✅ | ✅ |
| Trellix DLP Endpoint Complete | ✅ | ✅ | ✅ |
| Safetica | ❌* | ✅ | ❌* |
| Symantec Data Loss Prevention | ✅ | ✅ | ✅ |
| Microsoft Intune API | ❌* | ❌* | ✅ |
| ThreatLocker | ❌ | ✅ | ✅ |
| Forcepoint DLP Data Loss Prevention | ✅ | ✅ | ✅ |
| GTB Technologies DLP | ❌* | ✅ | ✅ |
| Fortra's Digital Guardian | ❌* | ✅ | ✅ |
| Device Control Plus by ManageEngine | ❌* | ✅ | ✅ |
*available if third-party integrations support the solution.
See the definitions for common and differentiating features.
User ratings & reviews
| Product | Average score* | Number of employees** |
|---|---|---|
| Endpoint Protector by CoSoSys | 4.5 out of 160 reviews | 132 |
| Trellix DLP Endpoint Complete | 4.4 out of 319 reviews | 3,300 |
| Safetica | 4.7 out of 263 reviews | 88 |
| Symantec Data Loss Prevention | 4.3 out of 156 reviews | 13,212 |
| Microsoft Intune API | 4.0 out of 163 reviews | 244,900 |
| ThreatLocker | 4.8 out of 178 reviews | 475 |
| Forcepoint DLP Data Loss Prevention | 4.3 out of 76 reviews | 1,939 |
| GTB Technologies DLP | 4.3 out of 16 reviews | 67 |
| Fortra's Digital Guardian | 3.7 out of 63 reviews | 204 |
| Device Control Plus by ManageEngine | 4.8 out of 6 reviews | 4,000 |
*Based on the total number of reviews and average ratings (on a 5-point scale) from leading software review platforms.
**The number of employees is gathered from publicly available resources (i.e., LinkedIn).
Ranking: Vendors with links are sponsors and listed at the top. Other products are ranked based on their total number of reviews.
If you are looking for free USB blocking software, see free alternatives to USB blocking software.
Top 10 USB blocking software analyzed
1. Endpoint Protector
Pros
- USB whitelisting/blacklisting: Some users like the ability to categorize USB devices.
- Granular access control: Our tests proved that Endpoint Protector enables granular access control for over 30+ kinds of devices. Administrators can set access rights based on devices (see our DLP review for more on Endpoint Protector’s DLP capabilities).
- USB encryption: It encrypts data on USB devices with EasyLock. Additionally, you can enable automatic encryption.
- Ease of use: We discovered that the application was simple to operate, with helpful explanations in the menu.
Cons
- Log reports: Some users claim that log reports need to be more detailed.
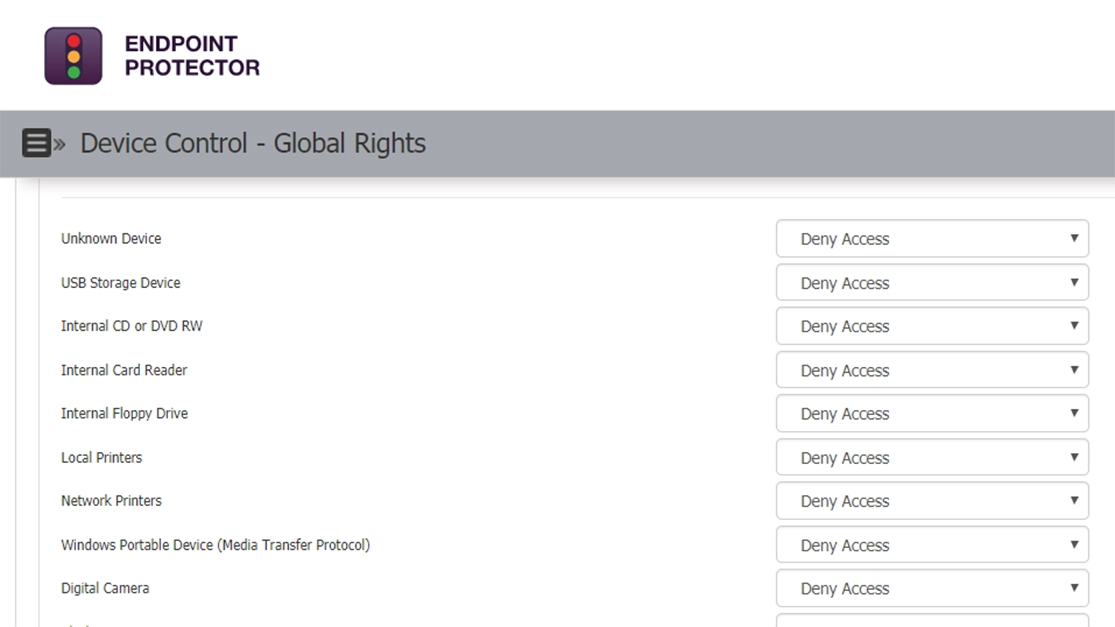
Choose Endpoint Protector for a comprehensive USB and device control solution.
2. Trellix DLP Endpoint Complete
Pros
- Policy management: Users are comfortable with applying policies.
Cons
- Ease of use: Multiple reviewers find it hard to get used to.
3. SafeticaONE Protection DLP
Pros
- USB connection security: Reviewers are happy with the product’s ability to maintain secure USB connections.
Cons
- Operating system support: Users claim that the product does not support Linux operating systems.
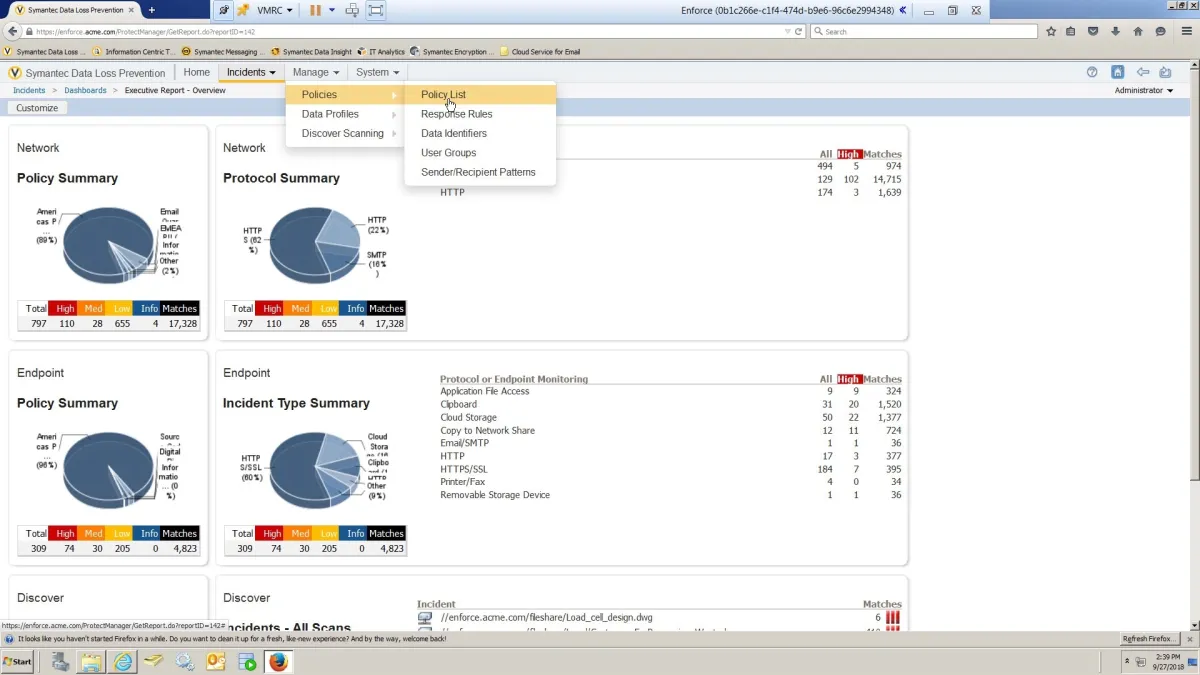
4. Symantec Endpoint DLP
Pros
- USB monitoring: The reviewer likes the product’s USB monitoring capabilities.
Cons
- Configuration management: Multiple reviewers claim the configuration is cumbersome for databases, so 3rd party tools had to be downloaded.
5. Microsoft Intune
Pros
- Compliance, device management, & data protection: The user is satisfied with the product’s compliance management, device management, and overall data protection functionalities.
Cons
- Reporting: Multiple reviewers have stated that Microsoft Intune is not sufficient for reporting, and they opt for Microsoft Configuration Manager.
6. ThreatLocker Storage Control
Pros
- USB whitelisting/blacklisting: Reviewers are happy with the product’s USB access control availability, such as blocking USBs.
Cons
- Ease of use: Multiple reviewers find keeping track of the application hard.
7. Forcepoint DLP
Pros
- Content detection& classification: The reviewer praises the product’s content inspection features, such as protecting sensitive data.
Cons
- Deployment: The deployment process was claimed to be cumbersome for the reviewer.
8. GTB Endpoint Enterprise DLP
Pros
- DLP: Most reviewers are satisfied with the product’s functionalities, such as content inspection and monitoring.
Cons
- Ease of use: Multiple reviewers have stated that the product is not easy to use at first because of the steep learning curve it creates.
9. Fortra Digital Guardian Endpoint DLP
Pros
- Scalability & reporting: The reviewer praises the product’s scalability and reporting capabilities.
Cons
- Ease of use: Multiple reviewers describe the use as challenging.
Source: G2
10. ManageEngine Device Control Plus
Pros
- File access control & ease of use: The product is easy to deploy and helpful in managing file access permissions.
Cons
- User interface: UI is claimed to be not user-friendly and needs further improvements.
USB drop attacks
Malicious software is intended to be distributed through a planned cybercrime called USB drop attacks. Virus-laden USB drives are placed close to the computer area, where people inadvertently connect them to PCs. According to Statista, data from 2021 shows that ca. 30% of companies experienced 11 to 50 malicious USB drop attacks.1
Security firm Mandiant discovered in 2023 that a China-based group named UNC53 carried out USB drop attacks and targeted 180 organizations in crowd-trafficked locations, such as airport cafes and printing service shops around the world.2
What is USB blocking software?
USB blocking software, also known as USB port control software or USB device management software, is a type of application used to monitor and manage the use of USB devices connected to a computer or network. This software allows administrators to control and restrict the usage of USB ports and devices for security and compliance reasons.
USB blocking software key features
1. Access control: The software enables administrators to set permissions for specific users or user groups regarding the use of USB devices. This could include allowing read-only access, read-and-write access, or blocking access to USB ports completely.
2. Logging and monitoring: USB blocking software typically logs all USB device activities, including device insertion and removal, file transfer events, and attempts to use unauthorized devices. This helps administrators track USB usage and identify potential security breaches.
3. Policy implementation: Administrators can create and implement policies governing USB usage across the organization. These policies may include restrictions on certain types of USB devices, time-based access controls, or compliance requirements.
4. Data Loss Prevention (DLP): Some USB blocking software includes DLP features to prevent sensitive data from being copied to unauthorized USB devices. This may involve content inspection, encryption, or preventing specific file types from transferring via USB.
5. Remote management: The ability to manage USB device policies and monitor activities remotely across multiple computers or endpoints is a common feature of USB blocking software.
See how our DLP review takes these features into account.
Why do you need USB blocking software?
USB blocking software is often used for security purposes in organizations or environments where controlling access to USB ports is necessary. Here are some reasons why USB blocking software may be needed:
1. Preventing data theft: USB ports can transfer sensitive data outside the organization’s network. By blocking USB ports, organizations can prevent unauthorized users from stealing or copying confidential information.
2. Compliance requirements: USB blocking software can help organizations maintain compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) or the General Data Protection Regulation (GDPR).
3. Monitoring and auditing: Monitoring and auditing functionalities allow administrators to track USB usage and identify potential security risks or policy violations.
Common features of USB blocking software
We selected the vendors that deliver:
- Access control: Set user-specific permissions for USB device usage.
- Logging and monitoring: Automatically record all USB activities.
- Policy management: Enforce organization-wide policies for USB usage.
- Data loss prevention (DLP): Integrate features like content inspection and encryption.
- Remote management: Manage policies and monitor devices across networks.
Differentiating features of USB blocking software
- Encryption for USBs: Data on USBs is encrypted with encryption algorithms like AES (Advanced Encryption Standard) or third-party encryption software such as BitLocker or FileVault.
- Content inspection: Analyzing data to identify sensitive or confidential information and categorizing data according to its sensitivity level. For example, the system prevents the dislocation of acknowledged and identified sensitive data.3
- Reporting: Reporting helps administrators monitor compliance with policies by generating reports that highlight any violations or exceptions.
FAQ
-
How does USB blocking software enhance data security and prevent data loss?
USB blocking software plays a critical role in data security by blocking USB ports and restricting the use of personal USB devices and other removable devices. It helps safeguard sensitive data from being transferred without permission, preventing data leaks and potential breaches. Key features such as automatic encryption, USB encryption, and data loss prevention ensure that confidential information remains protected even if a flash drive or other storage device is lost or stolen. This software also generates reports on USB activity, enabling organizations to monitor file transfers and maintain robust endpoint security.
-
Can USB blocking software manage and monitor various types of external devices?
Modern USB blocking solutions offer comprehensive device management features, allowing administrators to control USB port access for all connected USB devices. They can set detailed access permissions for specific devices, monitor USB activity, and generate reports on file transfers and hardware IDs. This level of USB device control helps block untrusted devices and unwanted users and supports endpoint protection by ensuring that only trusted devices are allowed, thereby reducing the risk of malware infection and unauthorized data transfers.
-
How is USB blocking software integrated into an operating system, and what are its key features?
USB blocker software can be seamlessly deployed as part of your endpoint security solution, integrating directly with your operating system. Its key features include locking or restricting USB ports, enforcing access permissions with a master password, automatic encryption of USB storage devices, and content inspection to identify sensitive data. Additionally, it offers robust reporting capabilities that track USB activity, helping organizations generate detailed reports for compliance and audit purposes. This comprehensive approach to USB device control and data protection prevents unauthorized access and ensures both personal and professional data security.
Further reading
- Top 10 Hexnode Alternatives
- In-Depth Forcepoint DLP Review
- Top 10 Device Control Software
- Top 10 RMM Software




Comments
Your email address will not be published. All fields are required.