Since nearly half of all cybersecurity breaches involve web applications1 , web application firewall (WAF) solutions play a critical role in protecting digital systems. That’s why we provide summary of:
Hands-on experience results with WAF solutions
Ranking: Tools are ranked according to their average mitigation rate aggregated across all tested attack vectors: injection, broken-access, and vulnerable & outdated components.
For further details, read the methodology of our benchmark.
Disclaimer: The benchmark results are based on Cloudflare’s free tier, along with the trial versions of Imperva and Barracuda.
Cloudflare WAF
We use Cloudflare’s free plan for basic protection against external threats. Although configuration options are limited, the free plan remains a reliable, zero-cost alternative to paid WAFs for basic traffic filtering.
Key capabilities include:
- Filtering inbound traffic using default and custom rules.

- Support for up to 5 custom expressions and associated actions (e.g., Block, Challenge).
- Basic bot management via Bot Fight Mode.
Limitations:
- The security analytics dashboard is minimal and lacks depth.
- Limited visibility into attack vectors and traffic breakdowns.
Performs well in mitigating Broken Access Control and Security Misconfiguration attacks.
Imperva WAF
We evaluated the trial version of Imperva App Protection. The solution provides layered traffic and security telemetry, including:
- Real-time and historical data on WAF-triggered events
- Traffic analytics (by country, client type, bandwidth over time)
- Breakdown of attack types and trends
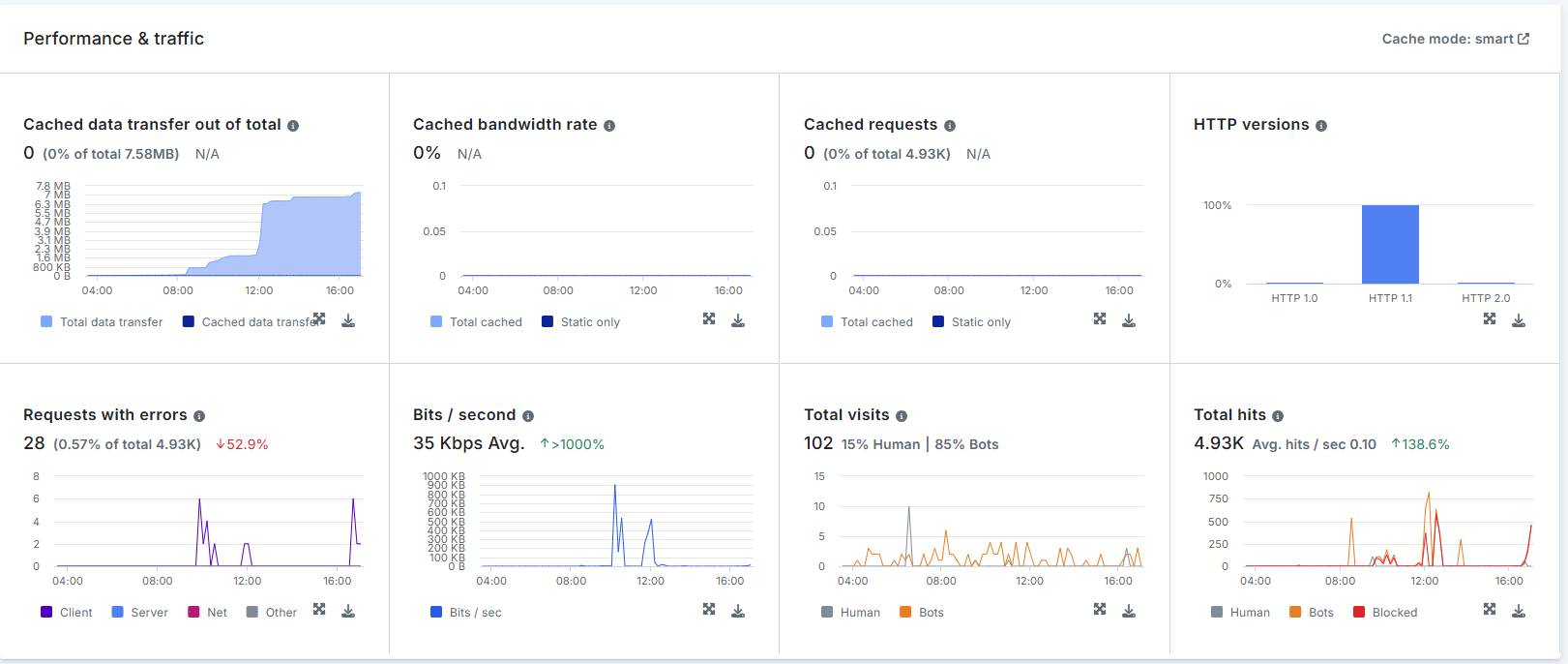
- Security policy actions include ignore, alert only, block request, block user, and block IP.
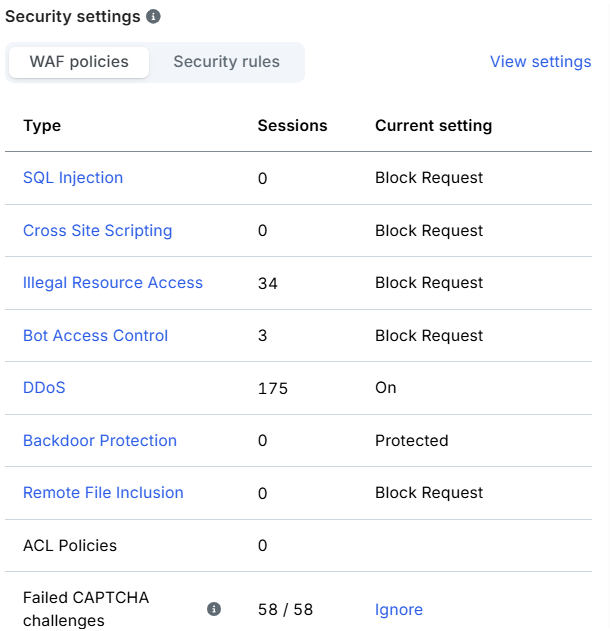
Limitations:
- There is a delay in how quickly attack data appears on the dashboard.
Imperva performed best among the three platforms we experienced in stopping attacks on outdated or vulnerable components, with a 93% success rate.
Barracuda Web Application Firewall
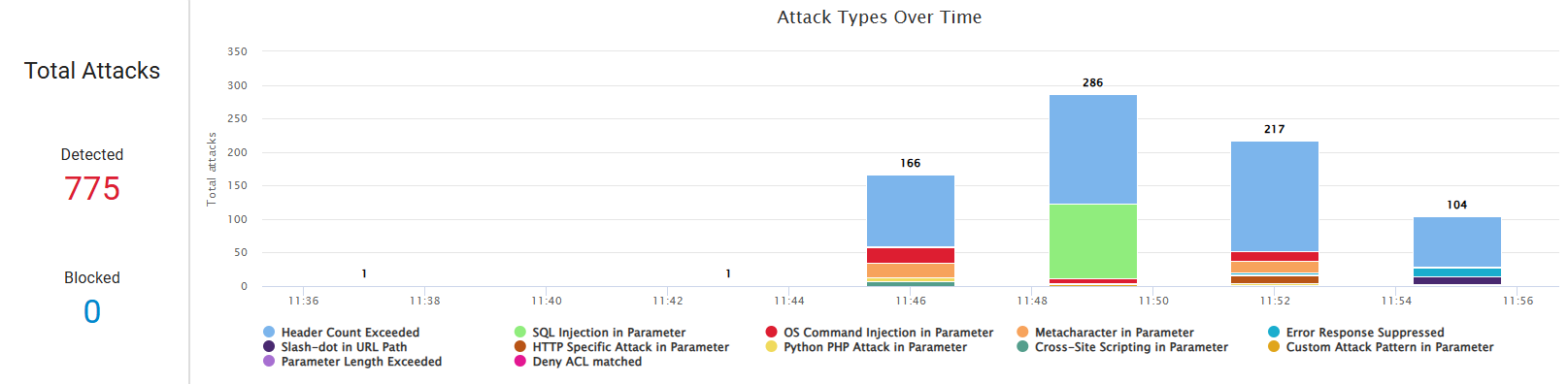
Trial version of Barracuda Application Protection is utilized in our benchmark. Barracuda’s WAF offers a clear, easy-to-use dashboard. It gives quick access to event data, faster than other tools we tested.
The Barracuda WAF offers:
- Low latency in threat detection and alerting, enabling near real-time visibility into new security events.
- Granular threat analytics, including categorical classification of detected attacks, allowing for improved threat assessment and incident response..
- Users can customize the menu by adding or removing components, allowing quicker access to frequently used features.
- Barracuda WAF lets users set detailed limits for incoming web requests, including limits on the number of cookies and the maximum length of header values.
The platform outperforms other three platforms in the injection attacks with a 91% mitigation rate.
Methodology of our WAF benchmark
To compare these tools, we used OWASP ZAP—a testing tool that simulates attacks on websites. We created a test site and targeted it with common web threats. These threats come from the OWASP Top 10, a list of the most serious web application security risks. 2 We chose one of the most common attacks: broken access control, injection, and vulnerable and outdated components. They include:
A01:2021 – Broken access control
- Path Traversal
- .env Information Leak
- .htaccess Information Leak
- Directory Browsing
- Source Code Disclosure – /WEB-INF Folder
- Cloud Metadata Potentially Exposed
A03:2021 – Injection
- SQL Injection – MySQL
- SQL Injection – Hypersonic SQL
- SQL Injection – Oracle
- SQL Injection – PostgreSQL
- SQL Injection – SQLite
- SQL Injection – MsSQL
- Remote OS Command Injection
- Server Side Code Injection
- XPath Injection
- CRLF Injection
- Server Side Include
- Cross-Site Scripting:
- Cross Site Scripting
- Cross Site Scripting
A06:2021 – Vulnerable and Outdated Components
- Spring4Shell
- Log4Shell
The effectiveness of the WAF was evaluated based on whether the WAF successfully identified the malicious payload and blocked the request, typically returning an HTTP 403 Forbidden status code, verified through the WAF provider’s security event logs/dashboard. Each tool’s ability to detect and block these threats was evaluated based on the mitigation rate.
Comparison of top 10 WAF solutions
Table 1. Feature comparison
| Tools | Zero-day protection | Rate-limiting types |
|---|---|---|
| FortiWeb | ✅ | header |
| Microsoft Azure WAF | ❌ | header |
| Imperva WAF | ❌ | IP |
| Cloudflare WAF | ✅ | IP |
| AWS WAF | ❌ | IP |
| Fastly Next-Gen WAF | ❌ | header |
| Radware Cloud WAF | ✅ | N/A |
| Barracuda Web Application Firewall | ✅ | IP |
| F5 BIG-IP Advanced WAF | ✅ | N/A |
| HAProxy Enterprise WAF | ✅ | N/A |
Table 2. Market presence and pricing comparison
| Tools | User Review | Free trial | Free version |
|---|---|---|---|
| FortiWeb | 4.4 out of 16 reviews | ❌ | ❌ |
| Microsoft Azure WAF | 4.3 out of 21 reviews | ✅ | ❌ |
| Imperva WAF | 4.8 out of 42 reviews | ✅ | ❌ |
| Cloudflare WAF | 4.6 out of 778 reviews | ❌ | ✅ |
| AWS WAF | 4.4 out of 55 reviews | ✅ | ❌ |
| Fastly Next-Gen WAF | 4.8 out of 76 reviews | ✅ | ✅ |
| Radware Cloud WAF | 4.1 out of 14 reviews | ✅ | ❌ |
| Barracuda Web Application Firewall | 4.3 out of 19 reviews | ✅ | ❌ |
| F5 BIG-IP Advanced WAF | - out of - reviews | ❌ | ❌ |
| HAProxy Enterprise WAF | 4.8 out of 132 reviews | ❌ | ❌ |
FortiWeb
FortiWeb is a web application firewall that protects critical web applications and APIs from both common and advanced threats, including bots, DDoS attacks, and zero-day exploits. It uses machine learning to detect unusual behavior, reduce false alarms, and cut down on manual work. FortiWeb also helps with API security by automatically discovering them and applying tailored protection policies without slowing down legitimate traffic..
- Uses two layers of AI to learn each application’s behavior.
- Offers hardware‑based acceleration for faster traffic inspection.
Microsoft Azure WAF
Azure Web Application Firewall provides built-in defenses against attacks at both the app and network edge. It uses regularly updated rule sets to detect threats, reduce false positives, and support compliance needs. With easy deployment, centralized management, and detailed security logs, it helps teams monitor risks and maintain secure operations.
- Agentless design—no extra software to install on your servers.
- Enforces rules at scale through Azure Policy across all resources.
- Feeds data into Azure Monitor and Microsoft Sentinel for built‑in analytics.
Imperva WAF
Imperva Web Application Firewall defends against attacks like SQL injection and cross-site scripting, while keeping false alarms low. It works across cloud, on-premises, and hybrid setups, adapting to both new and older systems. Built-in machine learning and global threat updates help teams spot and respond to real threats faster.
- Imperva Cloud WAF protects web applications and APIs in the cloud with automatic rules and simple setup, reducing manual work for your team.
- Imperva WAF Gateway secures older, complex apps that can’t move to the cloud, using smart threat detection and flexible rule settings.
- Elastic WAF fits into any system setup and protects modern apps directly within your environment, working smoothly with DevOps tools.
Cloudflare WAF
Cloudflare WAF protects web applications from threats, including zero-day attacks, by using global threat intelligence and machine learning. It can automatically block emerging threats in real time and offers easy setup with minimal management. The WAF uses both managed and custom rules to defend against common attacks like SQL injection, malware uploads, and credential stuffing.
- Deploys in a few clicks with zero extra tools or services.
- Blocks threats at the network edge before they reach your origin servers.
AWS WAF
AWS WAF helps protect your web applications from common online threats by filtering traffic before it reaches your system. It comes with preconfigured rules to block attacks like SQL injection, cross-site scripting, or large volumes of requests from a single source. You can also set up custom rules and monitor suspicious activity using built-in tools like IP reputation checks and traffic analysis.
- Auto‑deploys rules via AWS CloudFormation templates.
- Sets up a honeypot to trap and deflect bot attacks.
Fastly Next-Gen WAF
Fastly Next-Gen WAF protects web apps and APIs from both common and complex threats, like bots, account takeovers, and API abuse. It works wherever your apps are—on the edge, in the cloud, or on-prem—without needing a lot of setup or tuning. With clear reporting, fast alerts, and flexible deployment options, it helps teams spot and stop attacks quickly.
- SmartParse inspects request context without manual tuning.
- NLX reputation feed learns from thousands of distributed agents.
- Supports out‑of‑the‑box GraphQL and gRPC API inspection.
Radware Cloud WAF
Radware Cloud WAF adjusts to changing threats in real time and offers simple, clear insights into unusual activity. It supports a wide range of setups, including hybrid and cloud environments, and keeps protections up to date without adding extra work for in-house teams.
- Combines a block‑first (“negative”) model with AI‑driven behavioral protection.
- SecurePath™ architecture lets it plug in anywhere as an API‑based service.
- Correlates events across modules for a unified web application attack narrative.
Barracuda Web Application Firewall
Barracuda Web Application Firewall helps protect websites, APIs, and mobile apps from common and advanced cyber threats. It works with cloud services, offers bot protection, and adapts easily to fast-changing DevOps environments. With clear dashboards and built-in automation tools, it also simplifies security tasks and gives teams better control over app traffic and access.
- Built‑in application delivery (load balancing, routing, caching) speeds apps up.
- Offers unlimited DDoS protection as an optional add‑on.
F5 BIG-IP Advanced WAF
As one of the web application firewall solutions, F5 BIG-IP Advanced WAF uses behavioral analytics and machine learning to detect and respond to threats, including application-layer attacks and automated bots. It supports modern API protocols and helps manage security through flexible deployment and integration with DevOps workflows. Sensitive data is protected at the application layer, and configurations can be automated using declarative APIs.
- In‑browser data encryption shields sensitive fields from malware.
- Behavioral analytics identify and stop layer‑7 DoS attacks.
- “Security as code” through simple, declarative APIs.
HAProxy Enterprise WAF
HAProxy Enterprise WAF claims to offer reliable protection against common application attacks like SQLi and XSS. It uses machine learning and threat intelligence to detect threats with minimal impact on performance. The system is designed for easy management and low latency, helping organizations maintain security without complex configurations.
- HAProxy Fusion control plane for multi‑cluster, multi‑cloud orchestration
Features of web application firewalls
Rate limiting: controlling excessive requests
Rate limiting is a key feature in many WAF solutions used to manage how often a client—such as a user, bot, or application—can send requests to a server. It helps protect web applications from being overwhelmed by malicious or accidental spikes in traffic.
Why it matters
Rate limiting is often used to stop:
- DDoS attacks, where attackers flood systems with requests
- Brute force login attempts, which try endless combinations to gain access
- API abuse, when attackers or bots scrape data or overload systems
By setting limits on how many HTTP requests can be made in a given time, WAFs can delay or block traffic that behaves abnormally. This makes it harder for bad actors to succeed without disrupting legitimate traffic.
Types of rate limiting
- IP-based rate limiting
Limits the number of requests from a specific IP address.
✅ Useful for DDoS protection and bot mitigation
❌ Less effective when attackers rotate IP addresses - Header-based rate limiting
Controls requests based on HTTP headers like User-Agent or X-Forwarded-For.
✅ Helpful for API protection, especially when different apps share the same IP
❌ Can be tricked if headers are spoofed
Example in action:
An online service uses a cloud-based WAF to restrict each IP to 20 requests per minute. A second rule limits traffic per user-agent header to 500 requests per hour. This dual-layer approach blocks scraping bots and prevents service degradation while allowing real users to browse freely.
Zero-day protection
While rate limiting handles how often requests are made, zero-day protection focuses on what’s inside those requests.
Zero-day threats exploit web application vulnerabilities that haven’t been patched or even discovered yet. These are especially dangerous because traditional security tools may not recognize the attack pattern.
Modern WAF systems use an adaptive security engine that inspects web requests in real time. These engines learn from evolving threats and can block suspicious behavior even if the specific threat is new.
Key capabilities of zero-day protection:
- Analyzes payloads for anomalies
- Uses machine learning to spot attack patterns
- Blocks attempts like remote file inclusion, SQL injection, and more, even if not seen before
- Reduces false positives by adjusting detection based on context
Core WAF features
All the WAF solutions in the table include these three core WAF features.
Blocking
Blocking is one of the most basic but powerful WAF features.
It automatically stops traffic that matches known attack patterns or violates set rules.
- Types of blocking:
- IP blocking – blocks specific IPs or IP ranges.
- Geo-blocking – restricts access from certain countries.
- Header filtering – blocks suspicious requests based on HTTP headers.
Blocking helps stop known threats before they reach your app. It reduces the risk of damage or data loss.
Custom rules
Custom rules let security teams set up their own conditions to allow or block traffic.
You can write rules based on IP addresses, URLs, request methods, or even keywords in the request.
- Why it matters: Every application is different. Custom rules let you fine-tune protection based on what your app needs.
- Example: You can block requests that try to upload files with risky extensions like .exe or .php.
Custom rules are useful when you need control beyond what standard WAF rules offer.
OWASP top 10 protection
Most WAFs offer built-in protection against the OWASP Top 10 – a list of the most serious web application risks.
The most current version includes:3
- Broken access control: Users can access things they shouldn’t. Found in most apps.
- Cryptographic failures: Weak or missing encryption. Leads to data leaks.
- Injection: Untrusted input tricks the system. Includes SQL and XSS.
- Insecure design: Flaws in how the app is planned. Hard to fix later.
- Security misconfiguration: Unsafe settings or defaults. Very common.
- Vulnerable components: Using outdated libraries with known flaws.
- Auth failures: Problems with login or sessions. Still a big risk.
- Integrity failures: Apps trust updates or codes without checking them.
- Logging failures: No alerts or records when attacks happen.
- SSRF (Server-Side Request Forgery): The App makes unsafe internal requests. It can be serious.
By covering these threats, WAFs help reduce the most common security gaps in web apps.
How WAF solves security issues
Web Application Firewalls (WAFs) provide web application security by detecting and blocking malicious traffic in real time. They work in two main ways:4
Signature-based detection
This method relies on known attack patterns, or “signatures.” When a request matches one of these patterns, the WAF blocks it. This is fast and effective against known threats like SQL injection or cross-site scripting.
Behavior-based detection
This approach uses machine learning to understand what “normal” traffic looks like. It then flags anything unusual, even if it’s a new or unknown type of attack. Techniques include classification algorithms, neural networks, and decision trees.
Hybrid detection
Many modern WAFs use both methods together. This helps catch both known and new (zero-day) attacks. Hybrid models offer:
- Speed, from signature-based detection.
- Flexibility, from behavior-based detection.
- High accuracy, by reducing false positives and false negatives.
FAQs
What is WAF?
A web application firewall (WAF) is a security tool placed in front of web applications. It checks incoming and outgoing web traffic (HTTP) to detect and block harmful activity. A WAF works independently of the web app itself and can be either software or hardware. It protects web apps from attacks by applying security rules, especially when the app has weak or outdated code.
External Links
- 1. Web Application Firewall | Barracuda Networks. Barracuda
- 2. OWASP Top Ten | OWASP Foundation.
- 3. OWASP Top 10:2021.
- 4. Shaheed, A., & Kurdy, M. B. (2022). Web application firewall using machine learning and features engineering. Security and Communication Networks, 2022(1), 5280158.


Comments
Your email address will not be published. All fields are required.