We analyzed pricing plans, technical specs, and performance metrics from four major vendors—Cerberus FTP, IBM Aspera, Serv-U, and Thru—based on real-world file transfer scenarios and created MFT benchmark.
File transfers are used in ~50% of system integrations. Managed File Transfer (MFT) technologies offer a reliable alternative to traditional FTP and HTTP protocols.
We listed solutions with features that go beyond basic file transfer protocols by incorporating security measures, compliance tracking, and workflow automation to ensure data is safely transferred.
Comparison of Top MFT Solutions
| MFT Products | Ratings* | Free Trial |
|---|---|---|
| JSCAPE MFT by Redwood | 4.6/5 based on 122 reviews | ✅ for 7 days |
| Cerberus FTP Server | 4.5 based on 130 reviews | ✅ for 25 days |
| GoAnywhere MFT by Fortra | 4.7/5 based on 367 reviews | ✅ for 30 days |
| Stonebranch | 4.5/5 based on 85 reviews | N/A |
MOVEit | 4.5/5 based on 515 reviews | ✅ for 30 days |
| ActiveBatch | 4.6/5 based on 330 reviews | ✅ for 30 days |
| Serv-U by Solar Winds | 4.3/5 based on 224 reviews | ✅ for 14 days |
| Thru MFT by Dell Boomi | 4.5/5 based on 102 reviews | ✅ for 30 days |
| Aspera by IBM | 4.4/5 based on 51 reviews | ✅ for 30 days |
*Ratings are based on Capterra, Gartner, and G2.
Sorting: The vendors are listed in order of their number of reviews, except for sponsors with links, which are listed at the top.
Selection criteria:
- Employee Count: Products need to be produced by companies with more than 300 employees.
- References: For a proven track record, products need at least a Fortune 500 reference.
Top 8 Managed File Transfer (MFT) solutions analyzed
JSCAPE
JSCAPE by Redwood is a managed file transfer (MFT) solution that serves the healthcare, financial services, retail, and government industries.
Key features:
- Protocol Support: This module handles a variety of protocols, including SFTP, FTP/S, AS2, HTTP/S, and WebDAV, ensuring compatibility across different systems.
- Platform Compatibility: It operates on multiple operating systems, including Windows, Linux/UNIX, Solaris, and MacOS X, and can be deployed on-premises, in the cloud, or as a SaaS solution.
- No File Type Restrictions: Transfers any file type, including large EDI files like XML, without size limitations.
- Audit and Compliance: This service provides full audit trails of user and administrative activity, supporting compliance with HIPAA, PCI DSS, SOX, GDPR, and more.
- JSCAPE Triggers: Allows automation of file transfer and business processes without the need for custom scripting, enhancing operational efficiency and SLA fulfillment.
Choose JSCAPE for an enterprise-grade MFT solution with multi-OS support.
Cerberus FTP Server
Cerberus FTP Server enables organizations to achieve cost-effective file transfers thanks to its:
- Affordable pricing
- Support for compliance with standards like HIPAA and GDPR
- Features like audit trail generation
Key Features:
- Security: It supports encryption for data in transit and at rest, offers features like two-factor authentication (2FA), virus scanning integration, and rogue transfer detection to ensure secure file transfers.
- Automation and Integration: It includes robust automation options for scheduling transfers and event triggers and integrates with Active Directory, LDAP, and cloud storage providers, making it suitable for complex workflows.
- User Management: Cerberus FTP provides flexible user account and permission management, allowing businesses to configure file access and manage user groups efficiently.
Choose Cerberus FTP server for a cost-effective, Windows-based MFT software.
GoAnywhere MFT
GoAnywhere Managed File Transfer (MFT) is a software solution by Fortra. It is designed to streamline and secure data exchange between systems, employees, customers, and trading partners.
For more, read: What is managed file transfer by GoAnywhere?
Key Features:
- Security & Compliance: It supports protocols like SFTP, FTPS, HTTPS, and AS2. It offers FIPS 140-2 validated encryption and detailed audit trails to meet compliance standards, including GDPR, HIPAA, and PCI DSS.
- Automation & Workflow: Provides a browser-based interface for designing workflows, scheduling tasks, and automating file transfers without scripting.
- Deployment Flexibility: Available for on-premises, cloud, and hybrid environments.
- Integration Capabilities: Features connectors for cloud services (e.g., AWS, Azure) and applications like Salesforce and SharePoint
Stonebranch
Stonebranch offers a workload automation solution that enables companies to organize, automate, and synchronize IT tasks through a single integrated platform. It simplifies the management of workflows across multiple platforms and applications, even when data is stored in disparate locations. Its user-friendly drag-and-drop interface enables users to create workflows and manage the entire organization’s workload with ease.
Key features:
- Command Center-Style Platform: Enables users to manage and monitor the entire IT environment from a single interface, facilitating seamless execution of changes and system restoration without disruption.
- SaaS and On-Premise: The solution can be deployed as a cloud-based service or on-premises, giving flexibility to meet specific organizational needs and preferences.
- Data Pipeline Orchestration: Supports large-scale data operations, ensuring efficient management of complex data workflows.
- Stonebranch Integration Hub: Provides access to a community-driven source of integration blueprints, allowing users to extend functionality and customize integrations.
- Low-Code User Interface: Enables users to create and manage workflows with an intuitive drag-and-drop interface, reducing the need for complex scripting.
MOVEit
MOVEit Managed File Transfer (MFT) is a software solution designed to manage, view, and control all file transfer activities within an organization. MOVEit MFT provides a secure and compliant way for organizations to exchange sensitive data internally and externally with business partners, customers, or employees.
Read: Top 5 MOVEit Alternatives Based on 800+ Reviews
Key Features:
- End-to-End Encryption: Ensures secure file transfers with encryption both at rest and in transit.
- User Access Controls: Implements granular permissions and multi-factor authentication.
- Audit & Reporting: Offers comprehensive logging and reporting tools to support compliance and troubleshooting.
- Cloud Integration: Supports integrations with various cloud storage providers and services.
ActiveBatch
ActiveBatch is a workload automation platform that streamlines managed file transfer (MFT) processes. It supports protocols such as FTP and SFTP, enabling users to schedule and manage file transfers across various systems and environments.
With features such as automated retries, error handling, and real-time monitoring, ActiveBatch reduces the need for manual intervention and ensures secure, reliable data movement.
It is a suitable solution for organizations seeking to automate and centralize their complex file transfer workflows.
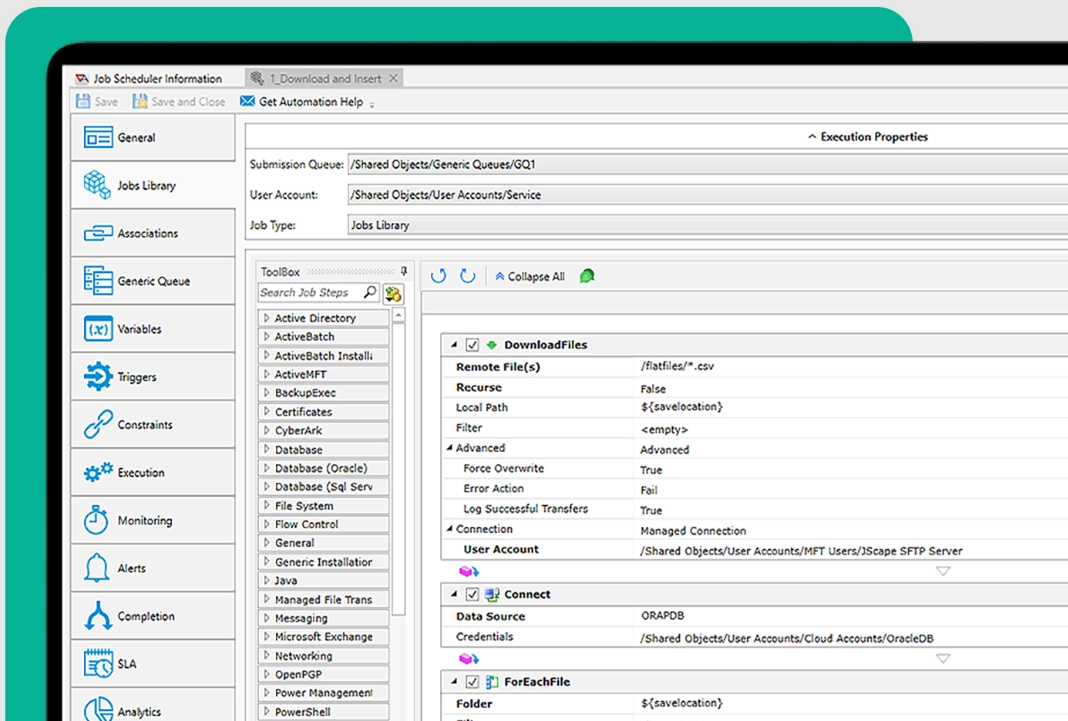
Source: ActiveBatch Automation Dashboard
Key Features:
- Integrated Jobs Library: Offers pre-built Job Steps for common file operations like MoveFile, CopyFile, For-Each-File, and IfFile, allowing for easy construction of file transfer workflows.
- Super REST API: Enables integration with other MFT solutions for managing scheduled and ad hoc file transfers.
- Business Applications: These are compatible with Microsoft’s application suite, ERP systems, BPM, and BI tools.
- Data Warehousing: Works with a variety of data systems, including the Hadoop Ecosystem, SAP, Microsoft SQL Server, Oracle Databases, Informatica, and IBM.
- IT Infrastructure: Supports both on-premises data centers (Windows, UNIX, IBM iSeries, AS/400) and cloud environments like VMware, Amazon EC2, and Microsoft Azure.
- Event-Driven Architecture: Advanced scheduling features streamline high-volume and complex data transfers.
- Automation Features: Includes parallel transfer capabilities, automatic restarts, and built-in checks for file authentication to improve SLAs.
Solarwinds Serv-U
Serv-U is a file transfer protocol (FTP) server software that facilitates secure file transfers over the Internet or within a private network.
Key Features:
- Security: Provides secure file transfer with encryption and firewall protection.
- Customization: Customizable web interfaces for branded user experiences.
- Integration: Can integrate with Active Directory and LDAP for user authentication.
Globalscape EFT
Globalscape Enhanced File Transfer (EFT) is a robust managed file transfer (MFT) solution designed to securely automate and manage enterprise data transfers. It offers a modular architecture, allowing organizations to customize features according to their specific needs.
- Modular Architecture: Allows customization with modules for advanced workflows, auditing, and compliance.
- Security Features: Includes antivirus scanning, data loss prevention, and encryption.
- Compliance Support: Assists in meeting standards like SOX, HIPAA, and PCI DSS.
- Automation: Facilitates automated file transfers and event-driven workflows.
Thru MFT by Dell Boomi
Thru Managed File Transfer (MFT) is a software solution designed to securely manage, send, and receive files within and outside an organization.
Key Features:
- Cloud Integration: Connects with various cloud storage services for seamless operations.
- Technical Features: Flexible external storage, though node setup can be intricate. Improved error messaging is needed.
- Performance: Comparable to on-prem FTP servers, strong real-world metrics.
- Storage Provisioning: It does not provide its own storage; it relies entirely on the resources the users supply.
- Anti-Virus Feature: Good anti-virus capability is integrated into the system.
IBM Aspera
IBM Aspera Managed File Transfer (MFT) is a solution that facilitates the secure, fast, and reliable transfer of large files and data sets across wide area networks. This product integrates Aspera’s patented FASP (Fast and Secure Protocol) technology with features typically found in managed file transfer solutions, like automation, monitoring, and control over file transfers.
Key Features:
- High-Speed Transfers: This method utilizes the FASP protocol to achieve high-speed data transfers, regardless of file size or network conditions.
- Security: Provides robust security features, including encryption and user authentication.
- Integration: Offers APIs and SDKs for integration with existing workflows and applications.
How do you choose the right MFT tool for your business?
If you need to share files:
- with a few parties,
- Non-confidential data: Use free versions of cloud file transfer services like Files.com.
- confidential data: Paid versions of cloud file transfer services offer a cost-effective solution. However, these bring on 3rd party cybersecurity risk
- highly valuable confidential information: On-prem solutions like GoAnywhere MFT minimize 3rd party cloud related risks.
- with tens of different parties (e.g. remote locations of your business), business-critical, confidential data of
- low volume (e.g. up to 1 TB): SaaS MFT solutions like Aspera provide easy maintenance and volume-based pricing
- high volume: On-prem MFT solutions like Solarwinds Serv-U or Cerberus MFT can help save costs but bring on maintenance and update tasks to the tech team.
MFT Benchmark 3 Vendors Comparison
See how we calculated these prices for the given data transfer volumes, excluding software maintenance/upgrade costs:
Pricing
| Provider | Pricing Model | Estimated Cost for 500 GB Transfer |
|---|---|---|
| Cerberus | Per Server | $1,499 |
| IBM Aspera | Pay-as-you-go | $475 |
| Serv-U | Per Server | $3,192 |
| Thru | User-Based | $645 |
Scenario 1: 500 GB File Transfer
- Data Transfer Volume: 500 GB/month
- Number of Parties: 5
Cerberus FTP:
Pricing: Starting at $1,499 annually for Professional Edition.
For transferring 500 GB between 5 parties:
- Fixed Cost: The cost remains $1,499 regardless of the data volume.
IBM Aspera:
For transferring 500 GB:
- Pay-as-you-go: The cost would be 500 GB * $0.95/GB = $475.00.
- Standard Plan: Even though the plan is for 1 TB, the full annual cost of $717.60 applies.
Serv-U:
Pricing: The cost starts at $3,192 per server for unlimited concurrent sessions.
For transferring 500 GB between 5 parties:
- Fixed Cost: The cost remains $3,192 regardless of the data volume.
Thru:
Thru offers custom pricing based on specific requirements.
For transferring 500 GB:
- Annual Cost: $645/month * 12 = $7,740 per year.
Observations
Among the options compared here, IBM Aspera’s pay-as-you-go plan is the most cost-effective option for businesses transferring 500 GB of data per month, costing them $475.00 annually. This plan is especially best suited for businesses that require scalability and cost control, but no persistent high-throughput needs.
IBM Aspera Standard Plan, costing $717.60 per year, becomes economical at around 1 TB of monthly data volume, offering additional features and fixed billing to heavy users.
Serv-U Managed File Transfer, at $3,192 per server per year, is more expensive but worth the cost to organizations operating within extremely regulated industries.
Thru, costing an annual fee of $7,740, is the most expensive reviewed option. It is priced to serve large companies that need advanced file sharing and integration features, though the cost might be prohibitive to smaller companies.
Alternatively, Cerberus FTP Server offers an entry-level price of $1,499 annually for its Professional Edition, and it is, therefore, an economical solution for businesses that need simple secure file transfer capabilities and moderate user and session requirements.
Scenario 2: 2000 GB File Transfer
- Data Transfer Volume: 2000 GB/month
- Number of Parties: 10
| Provider | Monthly Cost | Annual Cost |
|---|---|---|
| Cerberus | $125 | $1,499 |
| IBM Aspera | $3,696 | $44,352 |
| Serv-U | $266 | $3,192 |
| Thru | $645 | $7,740 |
Cerberus FTP:
$3,299 annually for Enterprise Edition, but customized enterprise solutions are available for high-volume needs.
IBM Aspera:
For 2000 GB/month, using the “Advanced” plan might be necessary as it includes higher transfer volumes with additional features.
2000 GB/month is 24 TB/year. Therefore, the cost is 24 TB * $1,848/TB = $44,352 per year, or $3,696 per month
Serv-U:
$3,192 per server for unlimited concurrent sessions
For transferring 2000 GB between 10 parties:
Fixed Cost: $3,192 annually, regardless of data volume
Thru:
For transferring 2000 GB:
Annual Cost: Estimated at $645/month * 12 = $7,740 per year
Observations
For transferring 2000 GB of data monthly between 10 parties, the following observations and recommendations are made:
For most organizations, Serv-U Managed File Transfer at $3,192 annually offers the best value with its security features and cost-effectiveness. However, if the need for flexibility and scalability is paramount, Thru, at $7,740 annually, is a strong contender. For very high-volume and complex requirements, IBM Aspera’s Advanced Plan at $3,696 per month is recommended despite its higher cost.
Methodology
The methodology for the Managed File Transfer (MFT) benchmark follows a structured approach to ensure accurate, repeatable, and meaningful results. The details are outlined below:
Benchmark Environment:
Hardware and Network Specifications:
- CPU: 4 x 2.90 GHz
- Memory: 8 GB
- Network: 12.5 Gbit
- Disk Size: 256 GB
- Disk IOPS: 16,000
- Disk Throughput: 10,000 MiB/s
| Region | Min Speed (MB/s) | Average Speed (MB/s) | Max Speed (MB/s) |
|---|---|---|---|
| Ireland | 2 | 80 | 103 |
| Mumbai | 1 | 78 | 106 |
| Sao Paulo | 1 | 80 | 108 |
| North California | 1 | 78 | 94 |
| Singapore | 1 | 88 | 108 |
Observations:
- High Fluctuation: Across all regions, there is a notable fluctuation in speed, indicating that network performance can be highly variable depending on the time of day, network load, and other factors.
- Network Bottlenecks: The minimum speeds recorded (1 MB/s) suggest that network bottlenecks or other issues can significantly impact transfer performance, particularly for larger files or during peak times.
- Infrastructure Dependence: Regions like Singapore show higher average speeds, highlighting the importance of robust infrastructure for achieving consistent performance in MFT solutions.
5 key capabilities of managed file transfer software
AIMultiple identified top Managed File Transfer (MFT) solutions along with the key features that they provide:
- Security features which include end-to-end encryption, secure file transfer protocols (e.g., SFTP, HTTPS), and compliance with regulatory standards like GDPR, HIPAA, or PCI
- Compliance with industry-specific regulations by providing detailed audit trails, logging user activities, and generating comprehensive reports
- Automating file transfers and integrating with existing systems (e.g., ERP, CRM, cloud services)
- A simple and intuitive UI and a responsive support service.
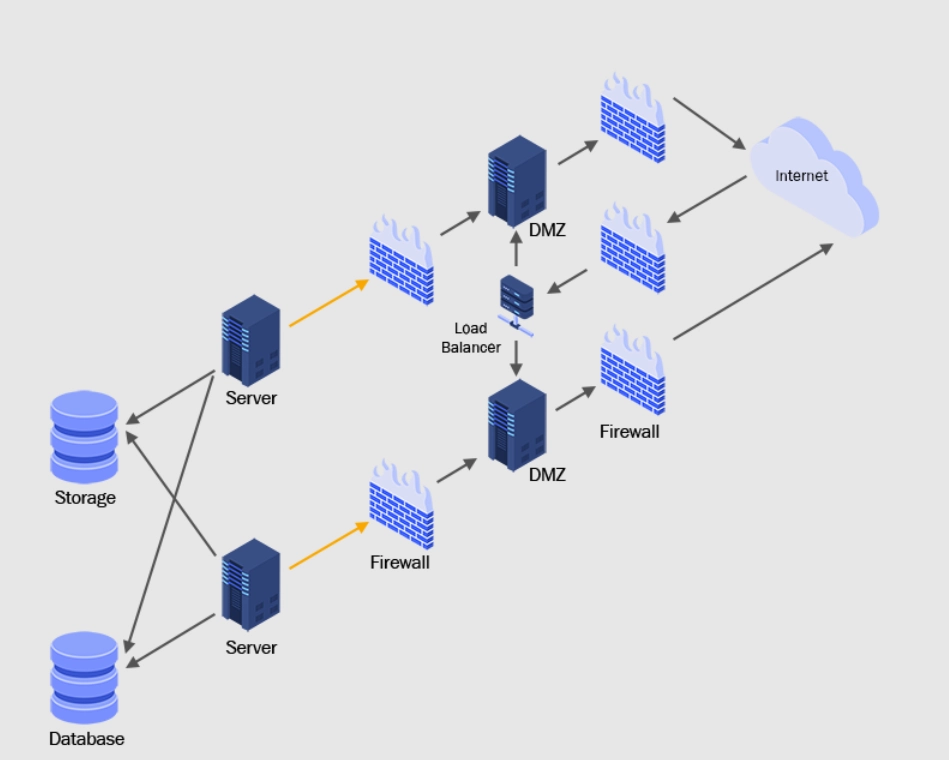
Figure 1: A MFT tool infrastructure.
1- Data security
When selecting a managed file transfer tool, data security is a crucial consideration. It ensures that sensitive data is safeguarded during transmission and storage. This sensitive data can include personally identifiable information (PII) or sensitive personal information (SPI). Protecting such information is crucial for all industries, particularly in healthcare and finance. To protect sensitive information, file transfers can need to be secure and follow the rules such as:
- HIPAA (Health Insurance Portability and Accountability Act).
- PCI-DSS (Payment Card Industry Data Security Standard).
- GDPR (General Data Protection Regulation)
- SOX (Sarbanes-Oxley Act).
Hence, when looking for a managed file transfer solution, it’s important to consider whether the tool offers strong security features such as:
- Authentication: This feature ensures that only authorized people can access the files.
- Digital signing: This feature checks a file’s authenticity and ensures it has not been changed.
- Encryption: This feature can encrypt files and the network used to transmit files. Encryption converts plaintext into unreadable ciphertext using a cryptographic key. Encryption can provide security for data during transfer, ensuring unauthorized parties cannot read the data.
2- Secure file transfer automation
Almost all companies transfer files over computer networks. However, some organizations, like retail businesses, can need automated file transfers for third-party audits and security.
Automation helps businesses set rules for handling different types of files and schedule file transfer. When looking at MFT tools, consider capabilities such as:
- Rule-based file handling: This feature allows you to establish rules for handling different files, such as automatically encrypting certain files or sending a notification when a specific file type is transferred. Rule-based file handling can be set up for:
- Files with certain keywords or phrases in the file name or content.
- Files that are larger or smaller than a specified size.
- Specific IP addresses or email addresses send or receive files.
- Specific file kinds, such as DOC, JPEG, MP4, PDF, etc.
- Files are delivered at a specified time of day or weekday.
- Scheduling: This feature enables you to schedule file transfers for a specific day and time, ensuring that files are transferred at the desired time.
3- Secure file transfer: Transfer protocol support
It is important to evaluate the tool’s support for different transfer protocols, such as standard and secure protocols, as different organizations can have different transfer protocol needs. For example, for B2B file transfer, AS2 can be preferred.
Standard protocols
- FTP: FTP is a network protocol that transfers files from one server to another across a TCP-based network, such as the Internet.
- HTTP: HTTP is a data transmission protocol used on the Internet. It serves as the cornerstone of the World Wide Web, transferring data from web servers to web browsers.
Additionally, secure transfer protocols are essential when transferring sensitive files.
Secure transfer protocol support
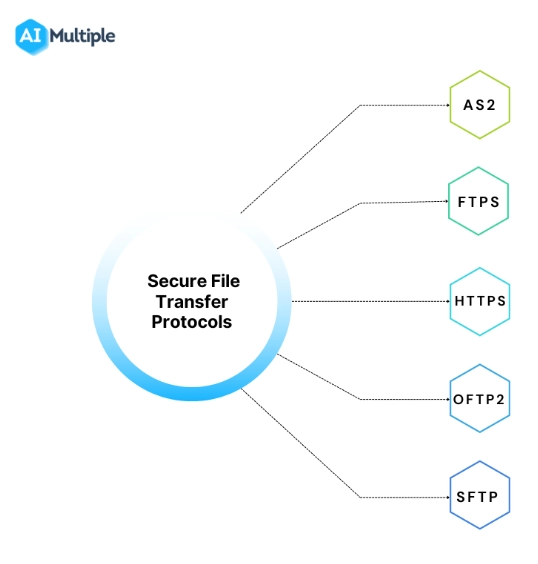
- AS2 (Applicability Statement 2): AS2 is a protocol for transferring data over the Internet safely. It is widely used in the retail and manufacturing industries for safe EDI (Electronic Data Interchange) document exchange.
- FASP (Fast and Secure Protocol): Aspera created FASP, a proprietary file transmission protocol. It is intended to transport large data across long distances at high rates. It combines TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) to achieve optimal transfer efficiency.
- FTPS (FTP Secure): FTP is an extension to FTP that provides functionality for the cryptographic protocols Transport Layer Security (TLS) and Secure Sockets Layer (SSL). It enables the safe transfer of files across a network.
- HTTPS (HTTP Secure): HTTPS is an HTTP extension that provides functionality for the cryptographic protocols Transport Layer Security (TLS) and Secure Sockets Layer (SSL). It enables secure data communication via the Internet.
- OFTP2 (Odette File Transfer Protocol version 2): OFTP2 is a secure file transfer standard used in the automotive and logistics industries. It is built on the OFTP (Odette File Transfer Protocol) standard and includes advanced security features like digital signing and encryption.
- SCP (Secure Copy Protocol): SCP is a secure file transfer protocol that sends and receives files from a remote server. SSH (Secure Shell) can be used for encryption and authentication.
- SFTP (Secure File Transfer Protocol): SFTP is an encrypted variant of FTP. It secures file transfers over the Internet using the SSH (Secure Shell) protocol.
4- Error handling and recovery
When choosing a controlled file transfer tool, it is important to think about how to handle and recover from errors. These features ensure that the file transfer process can continue even if something goes wrong. When assessing MFT software, check for the following features:
- Error handling: This functionality enables the utility to detect and handle file transfer processes automatically.
- Recovery: This feature enables the software to recover from failures and automatically continue the file transfer operation.
- Resumable transfers: This feature allows resuming automatically stopped file transfer processes.
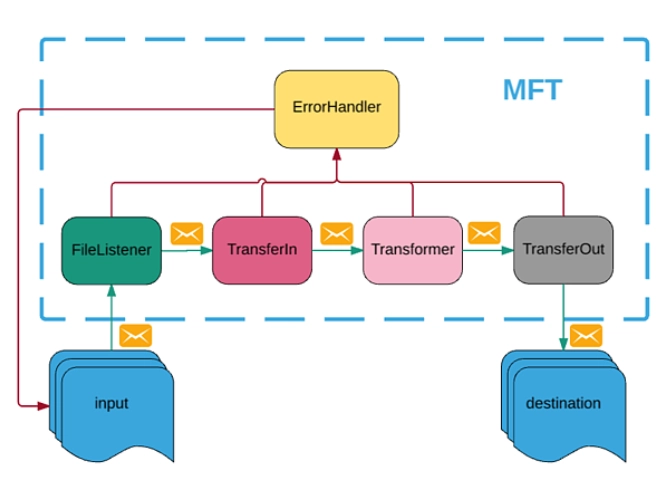
Figure 3. An MFT software error handler architecture. Upon failure, the MFT tool transfers the file to the error folder at any step in the workflow.
5- Management and monitoring
Management and monitoring let administrators set policies and permissions and keep an eye on and control all file transfers. When judging MFT tools based on their management and monitoring capabilities, look for features like:
- Alerts and notifications: The system sends alerts when certain scenarios occur, such as when a file transfer fails and/or a threshold is met.
- Central management console: Administrators can use this function to view and manage all file transfers from a single location.
- Reporting and analytics: This feature allows for extensive tracking and reporting of all file transfers, which is beneficial for compliance and auditing.
Disclaimers
- Prices for MFT tools are not shown in the table since vendors can provide customized quotations.
- IBM Sterling File Gateway was considered during the screening, but we could not have been able to access documentation on the company’s website.
- Seeburger BIS (Business Integration Suite) is not included in the list. We could not find funding or revenue information from reliable sources such as Crunchbase.
- We may have overlooked some MFT software that met the screening criteria. Please post a comment if this is the case, and we will consider adding them.
Emerging Trends in MFT
- Cloud-Native MFT Solutions: The shift toward cloud-native architectures enables greater scalability, flexibility, and integration with other cloud services.
- Enhanced Security Measures: With the increasing prevalence of cyber threats, MFT solutions incorporate advanced security features, such as zero-trust models and AI-driven threat detection.
- Integration with Business Applications: Modern MFT tools seamlessly integrate with enterprise applications (e.g., ERP, CRM) to streamline workflows.
- User-Friendly Interfaces: Emphasis on intuitive interfaces and dashboards to improve user experience and reduce the learning curve
Further reading
MFT solutions rely on proxies to route data between different stakeholders. If you are looking for a company that provides rotating and static proxies, check out proxy providers.

Comments
Your email address will not be published. All fields are required.