Web scraping helps organizations to collect data from web sources, including social media platforms and e-commerce sites. The collected data enables individuals and businesses to make data-driven decisions and improve their services.However, the web scraping process can present different web scraping challenges such as CAPTCHAs, IP filtering, and rate limits. Using a proxy server is at the top of web scraping best practices because it keeps the scraper protected and anonymous.
In this article, we explore in detail how proxy servers work, their types, and how to use them for web scraping. We also examine the top proxy service providers along with their key features.
The top proxy service providers for web scraping
| Vendors | Free trial | PAYG plan | Supported proxy types |
|---|---|---|---|
| Bright Data | 7-day | ✅ | 4 |
| Smartproxy | 14-day money-back | ✅ | 4 |
| Oxylabs | 7-day | ✅ | 4 |
| Webshare | 10 free proxies | ❌ | 3 |
| Nimble | 7-day | ❌ | 1 |
| NetNut | 7-day | ❌ | 4 |
| SOAX | 3-day trial for $1.99 | ❌ | 4 |
To better understand proxy service provider landscape, check out top 10 proxy service providers.
Supported proxy types:
- Bright Data: Residential, datacenter, mobile, ISP (Static Residential Proxies)
- Smartproxy: Residential, datacenter, mobile, ISP
- Oxylabs: Residential, datacenter, mobile, ISP
- Webshare: Residential, datacenter, ISP
- Nimble: Residential
- SOAX: Residential, datacenter, mobile, US ISP
- NetNut: Residential, datacenter, mobile, ISP
How does a proxy server work?
A proxy is an intermediary server between the user and the target website. The proxy server has its own IP address, therefore when a user makes a request to access a website via a proxy, the website sends and receives the data to the proxy server IP which forwards it to the user.
- Web scrapers use proxies to hide their identity and make their traffic look like regular user traffic.
- Website owners use proxies to improve security and balance internet traffic.
- Web users use proxies to protect their personal data or access websites that are blocked by their country’s censorship mechanism.
What are the different types of proxy servers?
There are many types of proxy servers that individuals and organizations use. Depending on the position of the proxy server relative to the internet user, proxy server types include:
Forward proxy
A forward proxy is an intermediary that the user or group of users puts forward between themselves and any server. It allows the users to make requests to websites according to the administration’s internet use policies. Therefore, some requests may be denied (e.g. accessing personal social media accounts from work servers)
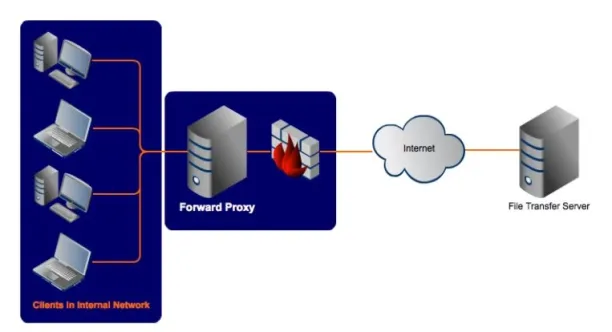
What types of IPs are used by forwarding proxy servers?
There are 3 main proxy IP types:
- Datacenter IPs: IPs of servers housed in data centers
- Residential IPs: IPs of private residences in specific zip codes/regions
- Mobile IPs: IPs of mobile devices
Since residential and mobile IPs are most likely to be legitimate users, these are the most coveted IPs by web scrapers. However, they are harder to acquire.
For guidance in choosing the right residential proxy service, check out Top 10 Residential Proxy Providers.
Reverse proxy
A reverse proxy server is positioned at the web servers’ end. It intercepts requests from the user to access the web data and either accepts or denies access depending on the organization’s bandwidth load. This allows websites to not be overloaded with Denial of Service (DoS) attacks.
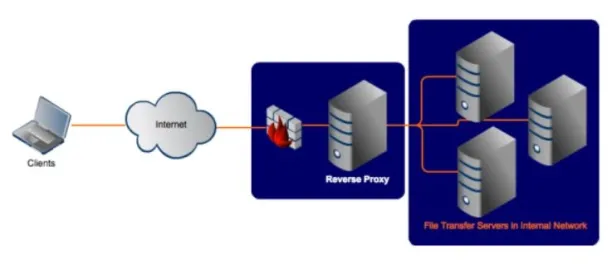
For more information on proxy server types, see our in-depth guide to proxy server types.
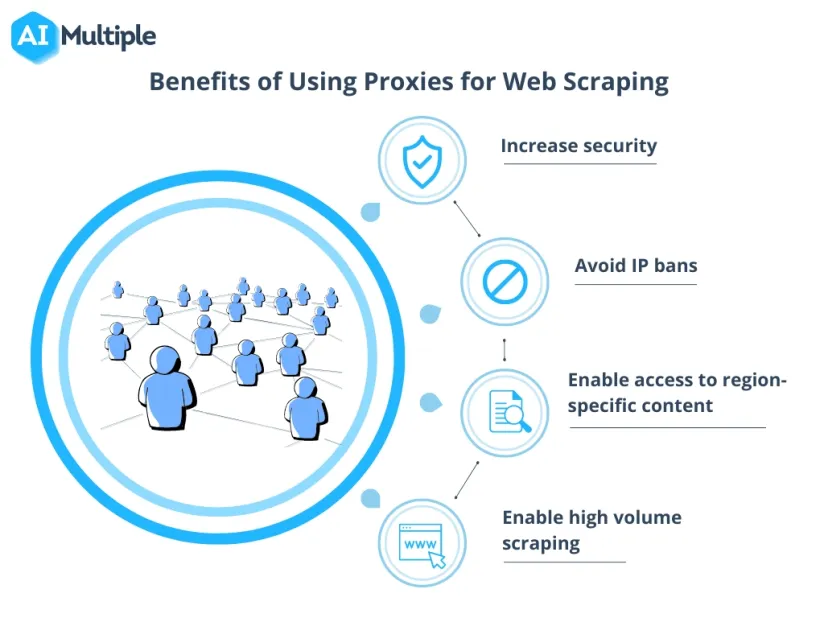
Benefits of using proxies for web scraping
Businesses use web scraping to extract valuable data about industries and market insights in order to make data-driven decisions and offer data-powered services. Forward proxies enable businesses to scrape data effectively from various web sources.
Benefits of proxy scraping include:
Increased security
Using a proxy server adds an extra layer of privacy by hiding the user’s machine IP address.
Avoid IP bans
Business websites set a limit to the amount of crawlable data called “Crawl Rate” to stop scrapers from making too many requests, hence, slowing down the website speed. Using a sufficient pool of proxies for scraping allows the crawler to get past rate limits on the target website by sending access requests from different IP addresses.
Enable access to region-specific content
Businesses who use website scraping for marketing and sales purposes may want to monitor websites’ (e.g. competitors) offering for a specific geographical region in order to provide appropriate product features and prices.
Using residential proxies with IP addresses from the targeted region allows the crawler to gain access to all the content available in that region. Additionally, requests coming from the same region look less suspicious, hence, less likely to be banned.
Enable high volume scraping
There’s no way to programmatically determine if a website is being scraped. However, the more activity a scraper has, the more likely its activity can be tracked. For example, scrapers may access the same website too quickly or at specific times every day, or reach not directly accessible webpages, which puts them at risk of being detected and banned. Proxies provide anonymity and allow making more concurrent sessions to the same or different websites.
How many proxies are needed?
The number of proxy servers needed to achieve the mentioned benefits above can be calculated with this formula: Number of proxies = number of access requests/crawl rate
The number of access requests depends on
- Pages the user wants to crawl
- The frequency with which a scraper is crawling a website. For example, a website could be crawled every minute/hour/day
And crawl rate is limited by the requests/user/time period that is allowed by the target website. For example, most websites allow only a limited number of requests/users within a minute to differentiate human user requests from automated ones.
How to set up your proxy management?
There are two aspects to setup:
- The software to route requests to different forward proxies
- The forward proxies that will make the requests from target websites
In-house vs. outsourcing proxy
In-house proxies ensure data privacy and give full control to the involved engineers. However, building an in-house proxy is time-consuming, and requires an experienced engineering team to build and maintain the proxy solution. Therefore, most businesses choose to use off-the-shelf proxy solutions.
Web scraping proxy types
Here’s a list of the web scraping proxy vendors depending on the IP type. Some vendors provide multiple types of IP proxies:
Datacenter proxies
Datacenters are assigned with multiple IP addresses which web scraping requests can use alternately. Datacenter IPs are faster than residential IPs, hence datacenter proxies provide a significant benefit for web scraping.
Feel free to read our in-depth guide on datacenter proxies to learn more about why you need data proxies.
Residential proxies
Residential proxies leverage the IP address of individuals and rotate between different individuals in order to send web scraping requests from different origins. If a web scraping service has a large pool of residential IP addresses, it is possible to scrape a website from any country, state, and city, providing the precision of scraping the required configuration of the website.
Read 4 Ways to Gain Competitive Edge With Residential Proxies to explore more on how companies can leverage residential proxies to accelerate their growth.
Mobile proxies
Mobile proxies work very similarly to residential proxies, allowing carrier and geography-specific queries. Mobile proxies also face fewer challenges from the scraped website since they skip blocks like captcha verification that is commonly found in web counterparts.
For more on proxies
If you want to learn more about web scraping and how it can benefit your business, feel free to read our articles on the topic:
- Top 10 Proxy Service Providers for Web Scraping
- Datacenter vs. Residential Proxies: Which to Choose?
Also, don’t forget to check out our sortable/filterable list of proxy service / server.

Comments
Your email address will not be published. All fields are required.