Cybersecurity
![How AI transforms Cybersecurity: Real-Life Examples [2025]](https://research.aimultiple.com/wp-content/uploads/trends/66f54b024eeb7-190x128.png.webp)
How AI transforms Cybersecurity: Real-Life Examples [2025]
By leveraging machine learning, advanced analytics, and automation, AI enables businesses to enhance their security posture, identify vulnerabilities, reduce response times, and allocate resources more efficiently. However, AI should also be seen as a double-edged sword as the cyber threats are also evolving due to developments in network security and generative AI.
List of the best SOC (Security Operations Center) Tools ['25]
An effectively equipped SOC team holds significant importance in countering cybersecurity threats and promptly addressing security incidents. A Security Operations Center (SOC) team uses a range of security tools, methodologies, and protocols to identify and prevent security incidents.

Analysis of Top 7+ Open Source Firewall Management Tools
It is crucial for businesses to prioritize robust network security to mitigate the substantial costs associated with data breaches, averaging over $4 million globally, according to cybersecurity statistics. To safeguard the firewall security and integrity of their sensitive data, businesses rely on firewall security management services.
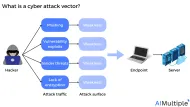
Most Common Cyber Attack Vectors in 2025
Network security statistics reveal that the cyber attack disruption levels have surged by 200% from 2019 to 2024, compared to a 4% increase from 2011 to 2016. The rise of cyber attacks is alarming since damage to information systems can harm processes, assets, individuals, and organizations.
Top 3 Open Source Firewall Audit Tools Compared in 2025
Open source firewall audit tools let IT teams see how their firewalls are set up, spot weak points, and learn how to fix them, without spending much. However, mid-market and enterprise companies may explore closed-source firewall audit software for more comprehensive solutions.
Top 6 IDS/IPS & Open Source Alternatives in 2025
At its core, intrusion detection and prevention systems (IDPS) monitor networks for threats, alert administrators, and prevent potential attacks. We previously explained real-life use cases of AI IPS solutions.
Top 8 Network Segmentation Tools in 2025
Organizations typically operate within a combination of on-site, public cloud, and private cloud settings, each offering unique security features. The dynamic nature of cloud and hybrid environments complicates the application of static network segmentation strategies, which were better aligned with more stable, conventional network setups.

Compare Top 20 LLM Security Tools & Free Frameworks
Chevrolet of Watsonville, a car dealership, introduced a ChatGPT-based chatbot on their website. However, the chatbot falsely advertised a car for $1, potentially leading to legal consequences and resulting in a substantial bill for Chevrolet. Incidents like these highlight the importance of implementing security measures to LLM applications.

100+ Network Security Statistics in 2025
Network security is essential to maintain strong organizational resilience and understand network security use cases. Discover 100+ current network security data points derived from expert evaluation and market analysis: 1-Key network security statistics 1.
Vulnerability Testing: Use Cases, Importance & Process ['25]
With cyber threats becoming more common, it’s crucial for organizations to increase their defenses proactively. One of the key strategies in achieving security is through vulnerability testing.