Traditional firewalls, which perform simple port and protocol inspection, are less capable than next-generation firewalls (NGFWs) in preventing cyber incidents. NGFWs go beyond simple port and protocol inspection by:
- inspecting the data in network packets
- and integrating microsegmentation tools to leverage application-level inspection
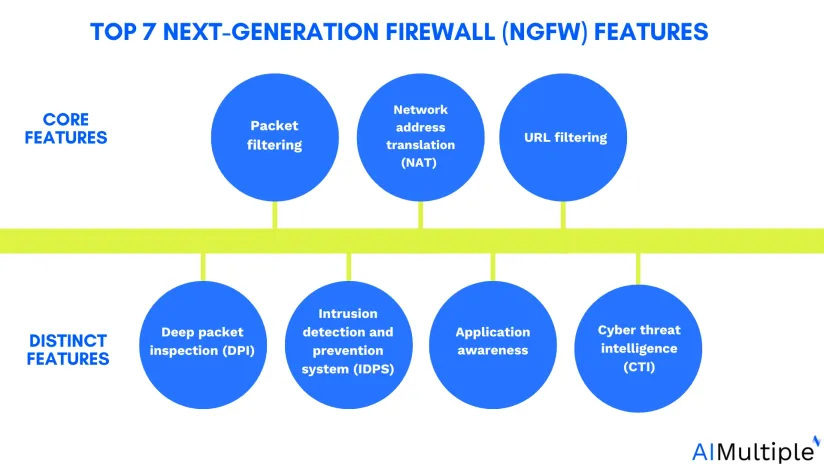
Learn what is a next-generation firewall (NGFW) and its top 7 features:
1. Packet filtering
Packet filtering examines the Internet Protocol (IP) addresses of the source, ports, and protocols connected with each packet — by analyzing where each packet originated, where it travels, and how it will travel there. Firewalls use this assessment to allow or deny packets, blocking out those that are not allowed.
Figure: Packet filtering across Layer 3 Internet protocol (IP) network
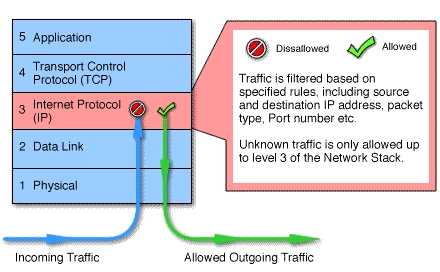
Source: ResearchGate1
For more, check out open source NGFW.
2. Network address translation (NAT)
Network address translation (NAT) converts one or more local private Internet Protocol (IP) addresses into public IP addresses to allow multiple local devices and hosts to connect to the Internet. NAT secures private networks via a router or firewall.
3. URL filtering
Uniform resource locator (URL) filtering is a system that allows companies to limit the websites and material that their employees can access. Users are prohibited from viewing specified websites and from utilizing corporate resources, such as computers or network bandwidth.
The URL filtering restricts employees from viewing websites that could disrupt the organization’s operations, such as sites that could be high-risk, damaging, or related to cyber-attacks.
Read more: Role-based access control (RBAC), mandatory access control (MAC).
4. Deep packet inspection (DPI)
Deep packet inspection (DPI) is a comprehensive tool for analyzing and monitoring network traffic. It is a type of packet filtering that detects, identifies, categorizes, and routes or stops packets delivering certain data or coding loads that traditional packet filtering cannot identify.
NGFWs integrated with deep packet inspection (DPI) capabilities can check data at transmission control protocol (TCP), internet protocol (IP), and application layers (from top to bottom). This helps see which application information is being routed.
Figure: Deep packet inspection
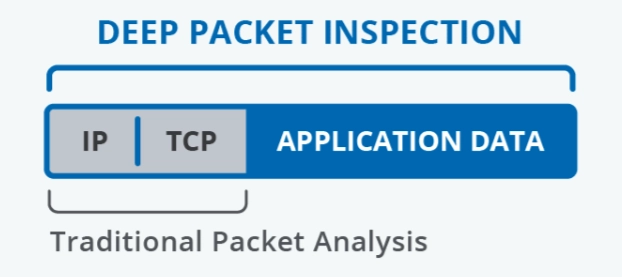
Source: Apcon2
5. Intrusion detection and prevention system (IDPS)
NGFWs can detect potential cyber attack vectors (e.g. third-party cyber risks) based on particular action patterns or abnormalities and subsequently block suspicious traffic on the network. These capabilities are known as intrusion detection services (IDS), intrusion prevention systems (IPS), or intrusion detection and prevention (IDP) tools.
6. Application awareness
NGFWs identify applications regardless of port, protocol, or IP address. This allows for granular control over application usage.
7. Cyber threat intelligence (CTI)
Cyber threat intelligence (CTI) is evidence-based information regarding digital attacks compiled and analyzed by cyber security specialists.
NGFWs may receive and respond to threat intelligence feeds from outside sources. For example, NGFWs with threat intelligence features can leverage an IPS signature detection or digital footprint by analyzing the most recent malware signatures to detect and block risky IP addresses that are used to launch attacks.
Read more: Firewall assessment.
What is a next-generation firewall (NGFW)?
A next-generation firewall (NGFW) is an integrated system stage that connects a standard firewall with other network security filtering capabilities.3
Figure: Next-generation firewall (NGFW) workflow
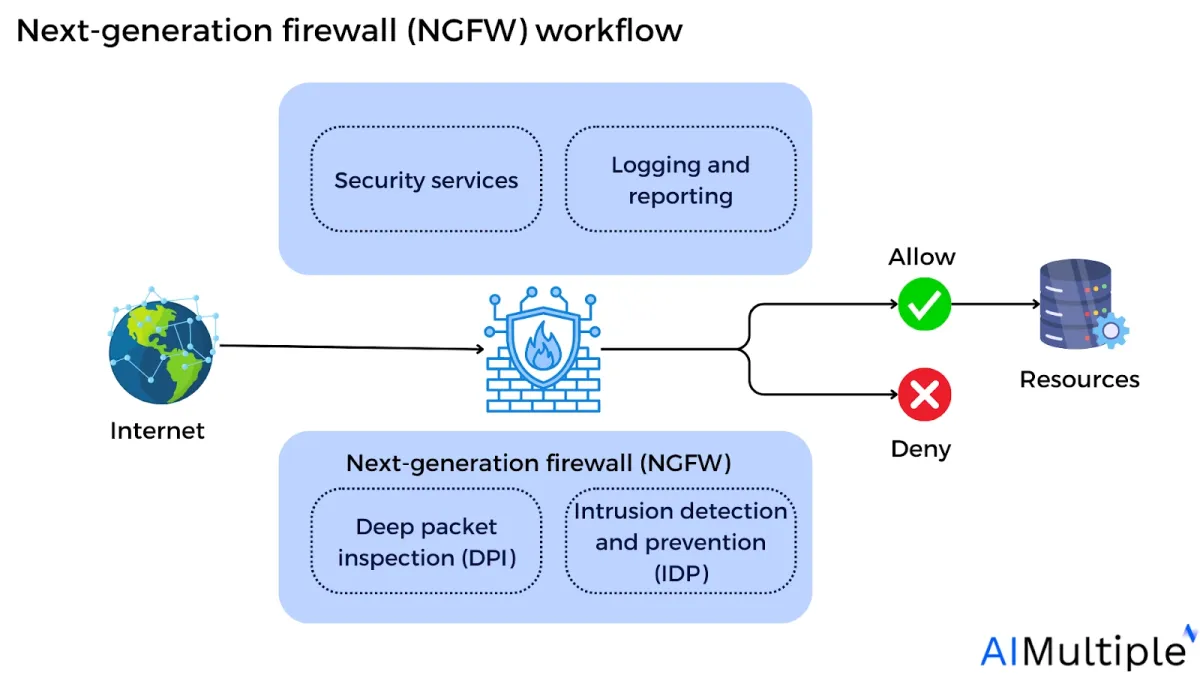
NGFWs capabilities
1. Traditional firewall functions
NGFW must support typical firewall functions such as packet filtering, network address translation (NAT), and URL filtering.
2. Application detection and monitoring capabilities
NGFWs should provide application awareness, application-specific security policies, and bandwidth control.
Traditional stateful inspection firewalls only work at Layers 2–4 and do not inspect packet contents. The NGFW may inspect the information at Layers 2 through 7, enabling network visibility and control (e.g. network audit controls) over network resources.
Figure: Open systems interconnection (OSI) Layers
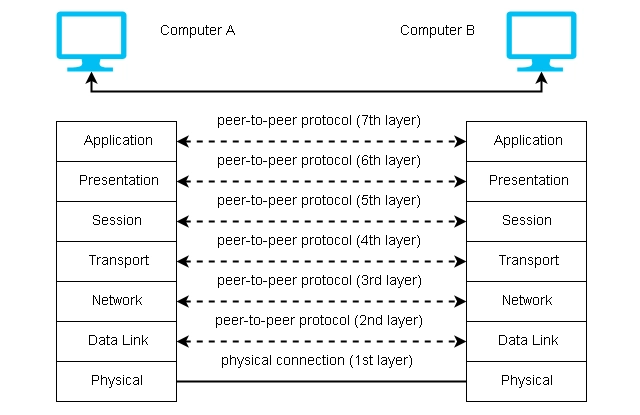
Source: NotesforMSc4
3. Intrusion prevention system support
The NGFW must support and connect the intrusion prevention system (IPS) function with firewall capabilities. Gartner highlights greater integration is needed across the IPS and firewall rather than simple linking in NGFWs.5
For example, a firewall needs to be able to self-update and transmit network security policies when the integrated IPS detects malicious traffic.
Figure: Next-generation firewall (NGFW) with integrated intrusion prevention system (IPS) and application controls
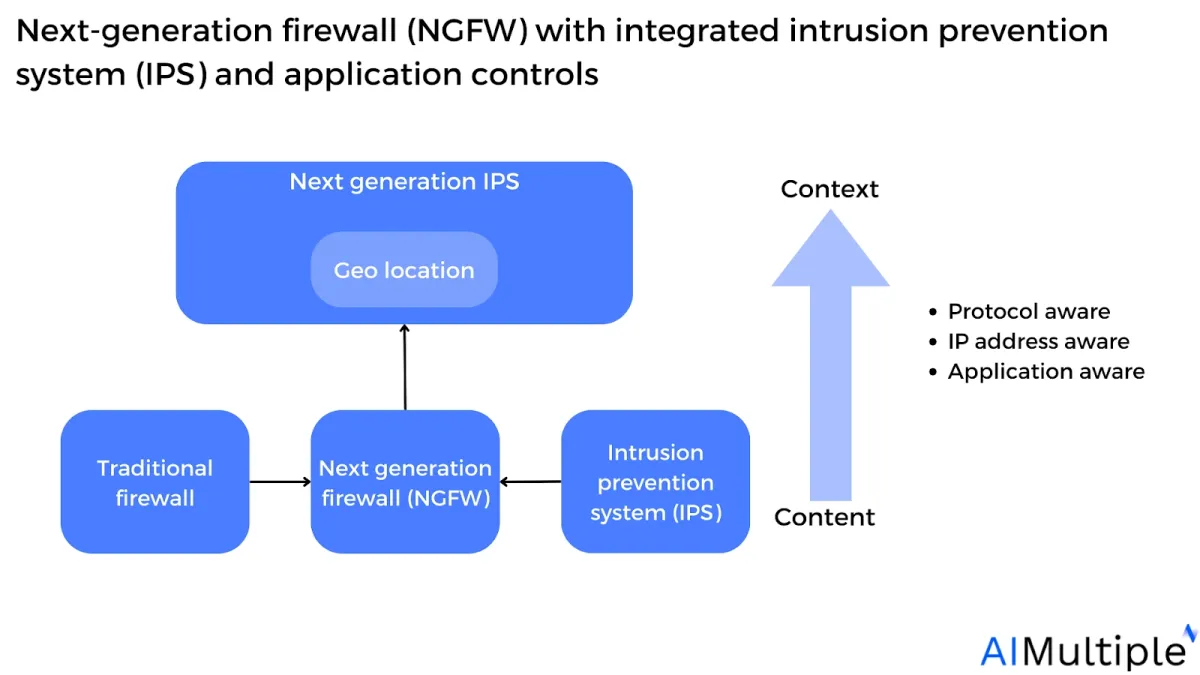
4. Leveraging external IT intelligence
NGFW can use knowledge provided by other IT systems about users, locations, vulnerabilities, and network resources.
For example, to control problems caused by segment-based network security controls (e.g. microsegmentation, DMZ network security) scenarios, the NGFW can be linked with a user microsegmentation tool that enforces granular access based on network security policies.6
Traditional firewalls vs NGFWs
Traditional firewalls use port/protocol inspection and blocking to secure company networks at the information transport layers (Layers 2 and 4 of the OSI model).
Next-generation firewalls (NGFW) are more intelligent. They may filter packets depending on application (Layer 7 of the OSI model), making more precise distinctions that are significantly more effective than classic firewalls’ conventional techniques.
NGFWs also rely on outside information to identify threats. This dynamic, adaptive methodology enables them to detect and defend against complex threats (e.g. insider threat management).
The bottom line:
To differentiate between traditional and next-generation firewalls, Gartner defines an NGFW as a deep-packet inspection firewall that goes beyond port/protocol inspection and blocking by integrating application-level inspection, intrusion prevention, and bringing knowledge from outside the firewall.7
Table: Comparison of next-generation firewalls vs. traditional firewalls
| Capability | Traditional firewall | Next generation firewall | Advantages of next-generation firewall (NGFW) |
|---|---|---|---|
| Inspection* | Stateless | Stateful | Blocks traffic more effectively. |
| Visibility | Basic, only lower TCP/IP layers | Deep, includes all TCP/IP layers | Provides a more granular analysis of traffic. |
| Services | Basic | Complex | In addition to packet filtering, it provides unified threat management (UTM) features including antivirus, content filtering, and IDS/IPS. |
| Protection | Limited | Enhanced | Identifies, prevents, and reports a broad spectrum of attacks. |
* Stateful inspection involves examining packets in context to ensure that they are part of a legal network connection.
Similarities between traditional firewalls and NGFWs
Traditional firewalls and NGFWs serve similar purposes of securing an organization’s system and information resources.
Some of the similarities include:
- Static packet filtering squares packets at system network interfaces based on rules, ports, or domains.
- Dynamic packet filtering verifies the reliability of each firewall connection.
- Network address translation (NAT) applies reconfiguration of the IP addresses in packet headers.
- Virtual private networks (VPNs) to maintain private network security while accessing the internet or other open networks.
- Port address translation enables mapping numerous devices on a LAN to a single IP address.
The future of NGFWs
New threat circumstances and changing company and information technology (IT) operations will prompt network security administrators to explore NGFW capabilities during their next firewall update cycle.
- NGFW and IPS markets are merging, particularly in enterprise boundary-specific deployment scenarios where the NGFW is encroaching on the market for standalone IPS technologies.
- Most large-scale organizations (~%40) are expected to acquire next-generation firewalls.8
Thus, large companies are expected to replace existing traditional firewalls with NGFWs as growing bandwidth requirements and a rising number of successful cyber attacks necessitate firewall upgrades.
To learn more about NGFWs, check out NGFW case studies with use cases.
Further reading
- UTM vs NGFW
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- Top 5 NGFW Use Cases with Case Studies
- AI Firewall vs NGFWs : Detailed Analysis & Comparison
External Links
- 1. ResearchGate - Temporarily Unavailable.
- 2. Complete Network Visibility | Deep Packet Inspection | APCON.
- 3. ”Next Generation Firewall- A Review“. International Journal of Computer Science and Information Technologies. 2016. Retrieved March 26, 2024.
- 4. Open Systems Interconnection (OSI) Model. E-Books
- 5. ”Next Generation Firewall- A Review“. Gartner. October 12, 2009. Retrieved March 26, 2024.
- 6. ”Next Generation Firewall- A Review“. Gartner. October 12, 2009. Retrieved March 26, 2024.
- 7. Definition of Next-generation Firewalls (NGFWs) - IT Glossary | Gartner.
- 8. ”2022 Cyberthreat DefenseReport“. Cyber Edge Group. November 2022. Retrieved March 26, 2024.


Comments
Your email address will not be published. All fields are required.