It is crucial for businesses to prioritize robust network security to mitigate the substantial costs associated with data breaches, averaging over $4 million globally, according to cybersecurity statistics. To safeguard the firewall security and integrity of their sensitive data, businesses rely on firewall security management services.
If you are
- working at an enterprise, explore closed source firewall management software for more comprehensive solutions.
- working at an SME or the company is just starting its network security journey without a budget, see open source firewall management tools, their key features such as IPS and benefits:
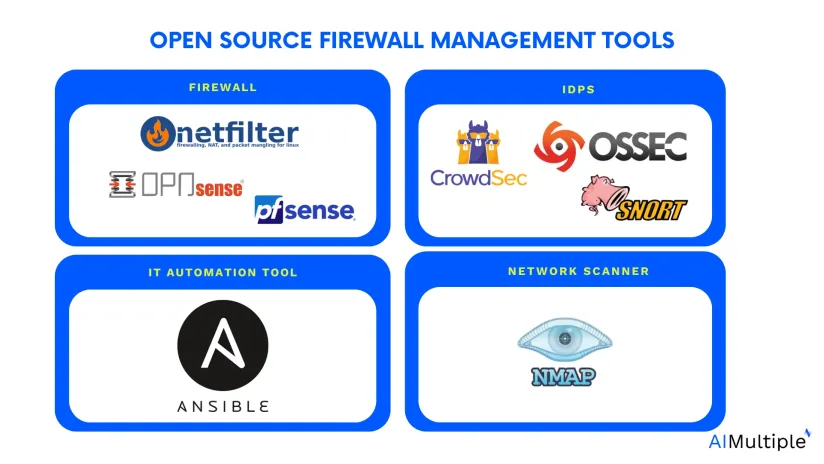
Top 8 open source firewall management software
| Tool | GitHub Stars | User Rating* | IPS | IPS Platform | Type | Platform Compatibility |
|---|---|---|---|---|---|---|
| Ansible | 61K | 4.4 out of 183 reviews | ✅ | Snort | IT automation tool | Windows, MacOS, Linux |
| Nmap | 9K | 4.7 out of 87 reviews | ❌ | – | Network scanner | Windows, MacOS, Linux |
| CrowdSec | 8K | 4.7 out of 87 reviews | ✅ | CrowdSec | IDS, IPS | Windows, Linux |
| pfSense | 5K | 4.6 out of 289 reviews | ✅ | Snort | Firewall | Windows, MacOS |
| OSSEC | 4K | 4.6 out of 10 reviews | ✅ | OSSEC | IDS | Windows, MacOS, Linux |
| Snort | 2K | 4.2 out of 28 reviews | ✅ | Snort | IDS, IPS | Windows, Linux |
| IPFire(Netfilter) | less than 1K | – | ✅ | Suricata | Firewall | Windows, Linux |
| OPNsense | less than 1K | – | ✅ | Suricata | Firewall | MacOS |
*Based on data from B2B review platforms
You may explore details regarding
in the following sections.
Disclaimer: ❌ means that the AIMultiple team couldn’t identify public evidence about a specific feature..
Inclusion criteria: Each vendor listed in the table provides intrusion detection and open source firewall management services in addition to other cyber security solutions. An intrusion detection system (IDS) is a critical component of firewall tools, enabling the detection of unauthorized network access, security breaches, and suspicious activities within the network infrastructure. It is a vital component for detecting and alerting potential security threats.
Ranking is determined by the GitHub stars.
1. Ansible
Ansible, with its extensive GitHub stars and user reviews, plays a vital role in firewall security management. Although primarily known for configuration management, Ansible integrates with Snort for IPS capabilities, helping in firewall configurations and efficient network security policy management of firewalls across Windows, MacOS, and Linux platforms.
Figure 1. Shows how Ansible security policy management software works
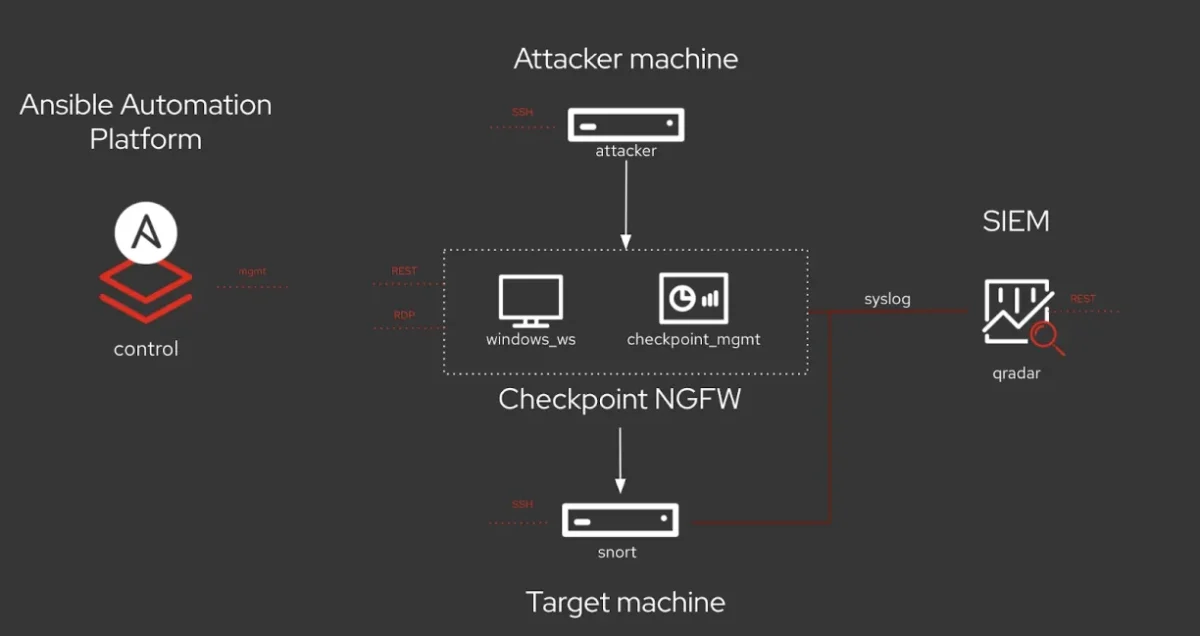
Source: Ansible1
2. NMap
Nmap, renowned for its network scanning capabilities, lacks IPS functionalities but remains a crucial tool for network security assessments. It aids in identifying potential security threats, performing regular security audits, and optimizing firewall rulesets for a secure network environment across Windows, MacOS, and Linux systems.
3. CrowdSec
CrowdSec, functioning as both an intrusion detection system (IDS) and intrusion prevention system (IPS), offers robust protection against cyber threats. It specializes in managing firewall policies and rules, optimizing firewall rulesets, and ensuring effective threat management. Its compatibility with Windows and Linux platforms makes it a versatile choice for organizations prioritizing network security.
Figure 2. Shows how CrowdSec firewall management system works
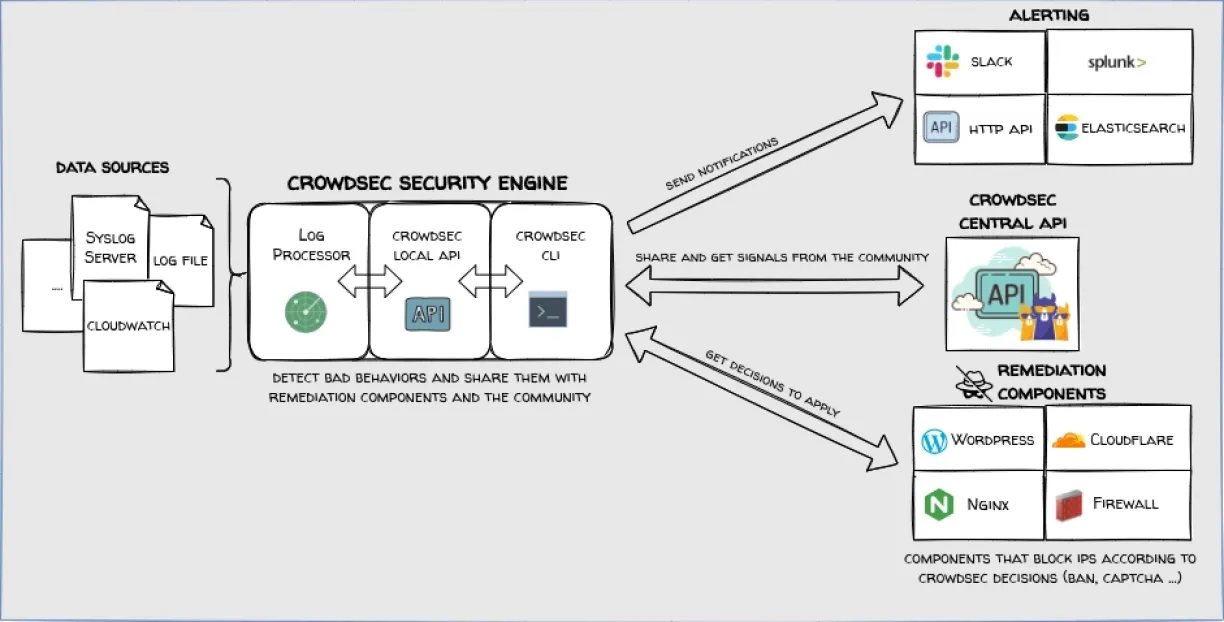
Source: CrowdSec2
4. Pfsense
With a solid user rating and GitHub stars, pfSense is a popular choice for firewall management. It boasts compatibility with Windows and MacOS, making it accessible to a wide range of users. Its permissive license and support for the Snort IPS platform contribute to its effectiveness in network security.
5. OSSEC
OSSEC helps improve security by tracking changes on devices and adjusting firewall rules as needed. It also helps fine-tune policies and runs regular checks to spot risks early. Its support for Windows, MacOS, and Linux platforms ensures a secure network environment across diverse IT infrastructures.
6. Snort
Snort, a widely recognized open source IDS/IPS tool, excels in intrusion detection and prevention capabilities. With strong GitHub stars and user ratings, Snort enhances firewall security through proactive threat management, deep packet inspection, and effective firewall rule management across Windows and Linux systems.
7. IPFire (Netfilter)
IPFire is a secure firewall management center. It, powered by the Netfilter firewall software, prioritizes strong protection and network security. It offers capabilities for managing firewall policies and rules, optimizing firewall rulesets, and conducting regular firewall security audits. Its compatibility with Windows and Linux platforms makes it a versatile choice for organizations seeking comprehensive security solutions.
8. OPNsense
OPNsense, despite its limited GitHub presence, offers valuable firewall management features and compatibility with Suricata for IPS functionalities on MacOS.
Figure 3. Shows how to enable IPS functionalities on OPNsense firewall management software
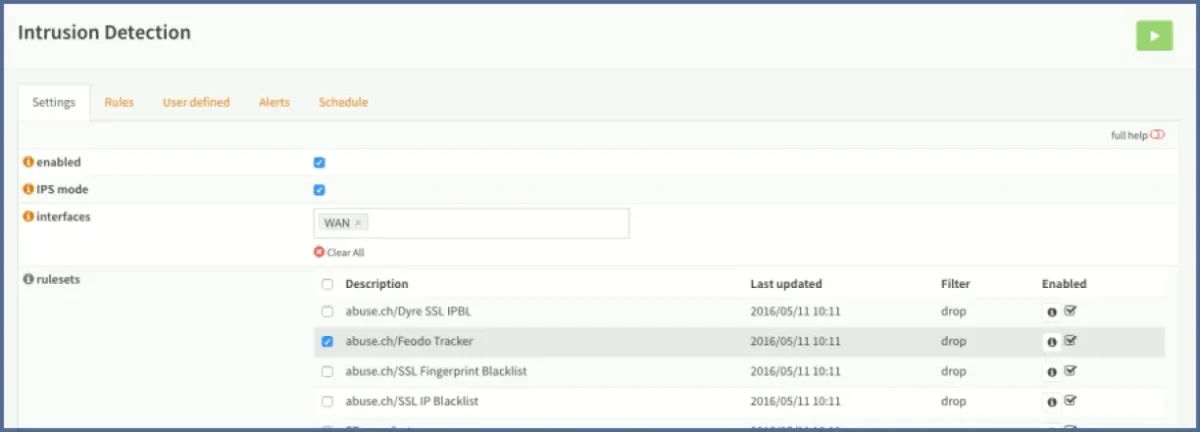
Source: OPNsense3
It simplifies firewall management tasks, allowing network administrators to implement effective firewall rule administration and optimize firewall configurations for enhanced security and network performance.
Figure 4. shows OPNsense firewall management software’s dashboard
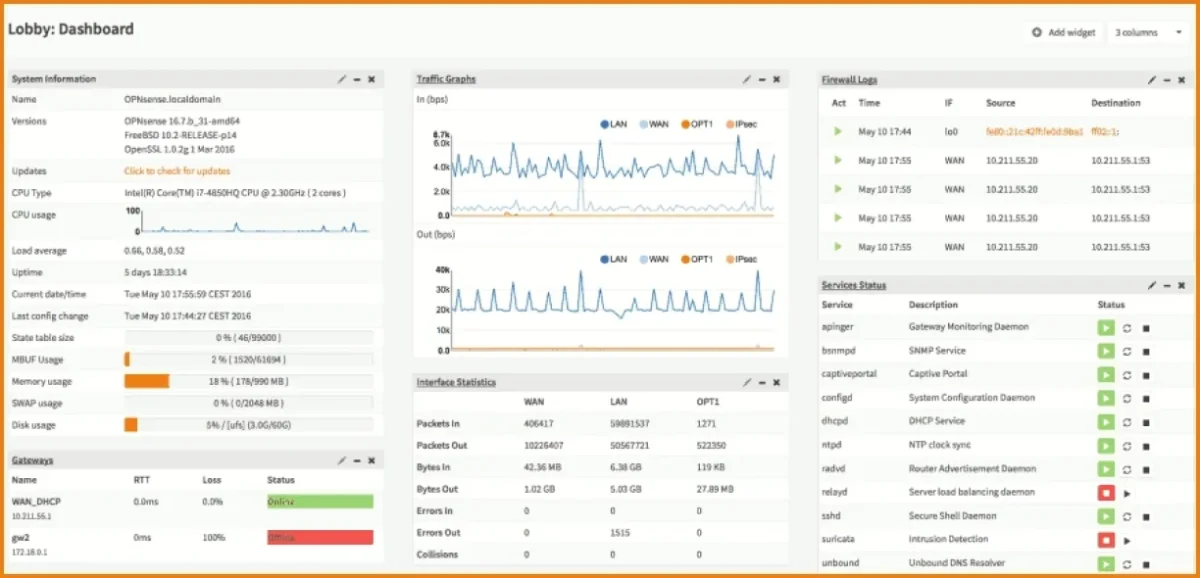
Source: OPNsense4
Exploring open source firewall management tools
At the core of open source firewall management software is the focus on network security. These tools empower network administrators and security teams to configure firewall rules, manage network traffic, and conduct regular security audits to detect and mitigate potential threats effectively.Open source firewall tools let teams manage security without expensive licenses. Paired with features like intrusion prevention systems (IPS), they not only spot threats—they stop them before harm is done.
Key features for selecting the right firewall software
Intrusion prevention system (IPS)
An IPS goes beyond detection by actively preventing potential threats and malicious activities, enhancing overall network security. It blocks suspicious activities identified by the IDS.
Figure 5. Shows the differences between IDS and IPS
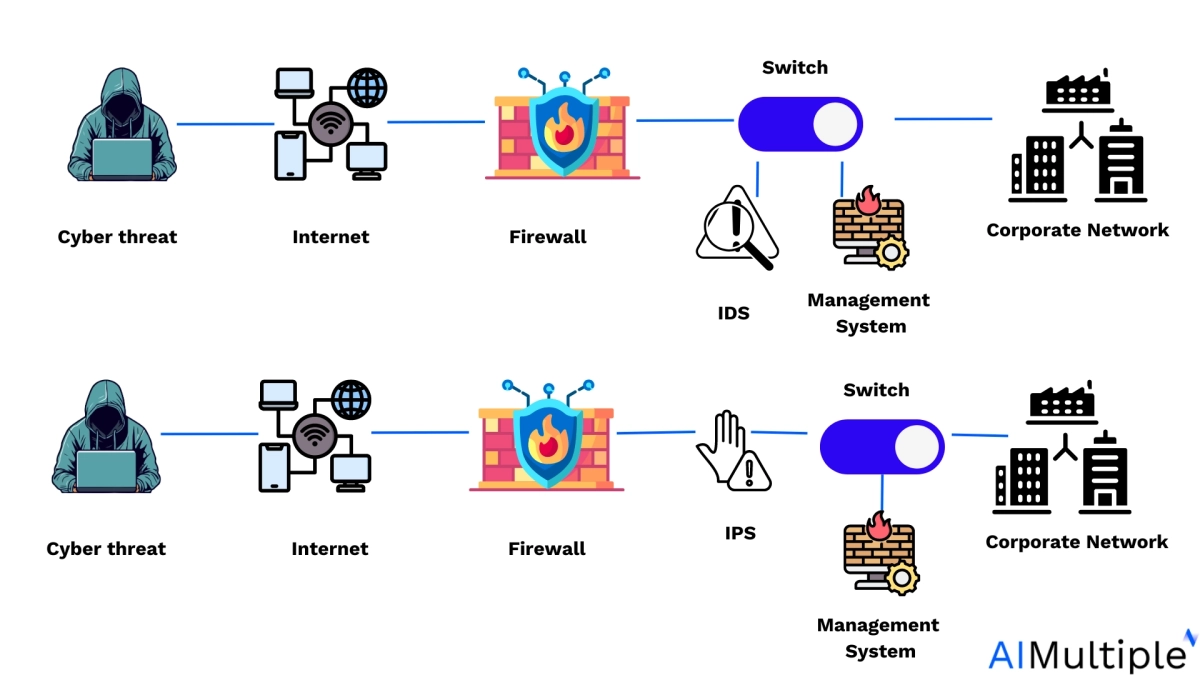
Source: Wallarm5
IDS detect potential threats and alert administrators, while IPS actively prevent cyber attacks by taking appropriate action upon detection.
IPS platform
The IPS platform is the foundation for effective threat prevention and mitigation, supporting robust security policies and real-time threat response.
CrowdSec: It uses a community-driven approach, where authorized users contribute and share detection rules based on real-time threat intelligence and collective security incidents6 . CrowdSec emphasizes crowd-sourced threat intelligence and behavioral analysis to detect and block malicious activities effectively.
Snort: Snort utilizes a signature-based rule set, where predefined signatures are used to identify known threats based on patterns and behaviors. It primarily focuses on real-time packet inspection and signature-based detection to identify and block malicious network traffic.
OSSEC: It employs a combination of signature-based rules, anomaly detection, and log analysis to detect and respond to security events. OSSEC focuses on host-based intrusion detection (HIDS), monitoring system logs, file integrity checking, and rootkit detection.
Suricata: Suricata features a multi-threaded rule engine with support for signature-based rules, protocol analysis, and emerging threat detection. It emphasizes high-speed security and traffic analysis, protocol analysis, and the detection of complex threats like zero-day exploits and evasion techniques.
Firewall management type
Configuration management: Businesses choose this type of firewall management solution for efficient management and optimization of firewall configurations, ensuring security policies are accurately enforced.
Network scanner: Selected for its capability to scan and identify vulnerabilities within the network, aiding in proactive threat detection and prevention.
Intrusion detection system (IDS): Intrusion detection systems are favored for their ability to detect and alert on suspicious activities within the network, enhancing threat detection capabilities.
Intrusion detection system (IPS): Intrusion prevention systems are selected to actively block identified security breaches, providing an added layer of defense against malicious activities.
Firewall: Firewall solutions are fundamental for businesses to establish secure boundaries, control inbound and outbound traffic, and enforce security policies to protect sensitive data and resources.
Platform compatibility
Ensuring open source firewall management software are compatible with the organization’s IT infrastructure, including Windows, MacOS, Linux, and network devices, is essential for seamless integration and effective firewall security management.
8 Benefits of open source firewall management solutions
1. Cost effectiveness and community support
Open source firewall security management software provides cost-effective solutions by offering robust security features without the high licensing fees of proprietary software. Additionally, they often benefit from a collaborative community that continuously improves and updates the software, ensuring enhanced security and functionality over time.
2.Network security reinforcement
Open source firewall management software empower security administrators and security teams to strengthen network security by implementing effective firewall rules and security policies. These tools enable the management of traditional firewalls and next-generation firewalls, ensuring comprehensive protection against cyber threats.
3.Efficient firewall management
Proper firewall management is essential for regulating network traffic, optimizing firewall rulesets, and conducting regular security audits. Open source firewall tools let teams manage settings and security from one place. They make it easier to spot problems and apply changes quickly across the network.
4.Robust security firewall policies
With open source security management software, organizations can define and enforce robust security firewall policy tailored to their specific needs. These tools facilitate the creation of next-generation firewalls policies, incorporating features like deep packet inspection, intrusion prevention, and stateful firewalls to combat advanced threats effectively.
5.Comprehensive threat detection
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) are vital components of open source firewall security management software, enabling the detection and prevention of unauthorized network access and malicious activities. These tools utilize deep packet inspection and threat management techniques to identify and block suspicious network traffic.
6.Centralized management and reporting
Open source firewall management solutions offer centralized management capabilities, allowing security administrators to monitor firewall changes, analyze firewall logs, and generate compliance reports. This centralized approach streamlines firewall management tasks and ensures network security policy management and regulatory requirements.
7.Optimized firewall configurations
Effective firewall management involves optimizing firewall performance and configurations to mitigate firewall security risks and prevent data breaches. Open source firewall management tools provide graphical user interfaces (GUIs) for configuring firewall rules, resolving conflicting configurations, and managing virtual appliances like proxy firewalls and web proxies.
8.Secure network connectivity
Open source firewall management tools automate firewall rule administration to help organizations secure network connectivity, authorize legitimate users, and block unauthorized access attempts. These tools facilitate the implementation of global rules, packet filtering, and destination IP address restrictions to safeguard network resources.
Further reading
- Firewall Integration of Top Management Services
- Firewall Audit Logs: Analysis and 6 Steps for Improvement
- Top 7 Open Source Firewall Audit Tools: Analysis & Comparison
FAQs
What is a management firewall?
A management firewall focuses only on protecting admin tools and control panels. It blocks unwanted access to places like remote settings and system dashboards, helping keep network operations safe and compliant. It helps secure these critical network management functions by controlling access and ensuring that only authorized personnel can make changes or access sensitive network components.
What does a firewall manager do?
A firewall manager is responsible for overseeing the configuration, compliance standards, deployment, monitoring, and maintenance of firewall systems within an organization’s network. Overall, a firewall manager plays a critical role in safeguarding network infrastructure, preventing cyber threats, and maintaining a secure network environment.
External Links
- 1. Red Hat Ansible Security Automation Guide | Red Hat Ansible Automation Platform | 2.2 | Red Hat Documentation.
- 2. Introduction | CrowdSec.
- 3. OPNsense Features OpenVPN, Proxy, IPS, QoS, CARP, Netflow, More...
- 4. OPNsense Features OpenVPN, Proxy, IPS, QoS, CARP, Netflow, More...
- 5. What is an Intrusion Prevention System (IPS)❓.
- 6. CrowdSec. CrowdSec. Accessed: 25/April/2024.



Comments
Your email address will not be published. All fields are required.