Open source firewall audit tools let IT teams see how their firewalls are set up, spot weak points, and learn how to fix them, without spending much. However, mid-market and enterprise companies may explore closed-source firewall audit software for more comprehensive solutions.
Explore the key players in open source firewall audit tools, providing a comprehensive overview of their features, benefits and drawbacks:
Comparison of software
| Vendor | User Rating* | Number of Reviews* | License | Platform Compatibility** |
|---|---|---|---|---|
| Nmap | 4.6 | 121 | Strongly protective | MacOS, Linux |
| CrowdSec | 4.7 | 89 | Permissive | Linux |
| OpenVas | 4.3 | 62 | Strongly protective | MacOS, Linux |
*Data was obtained from review platforms such as G2, Gartner, TrustRadius, and Capterra.
** All analyzed software packages are compatible with Windows
Inclusion criteria: Only vendors with over 10 reviews across all review platforms were considered.
Ranking: The companies are ordered based on the total count of reviews.
Read more: Network security audit tools.
1. Nmap
Nmap is an open source firewall audit software for network discovery, mapping, and security auditing, available for free. Its key functionalities encompass port scanning, detecting unknown devices, evaluating security vulnerabilities, and pinpointing network problems.
This tool attempts to identify firewall rules using an IP TTL expiration method called firewalking. This open source firewall audit software identifies a vulnerability in firewalls that utilize helpers to dynamically open ports for protocols like FTP and SIP.
Nmap, developed by Gordon Lyon, is written in Lua and distributed under the GPL-2 license. It is compatible with Windows, MacOS, and Linux platforms.
User reviews
Pros
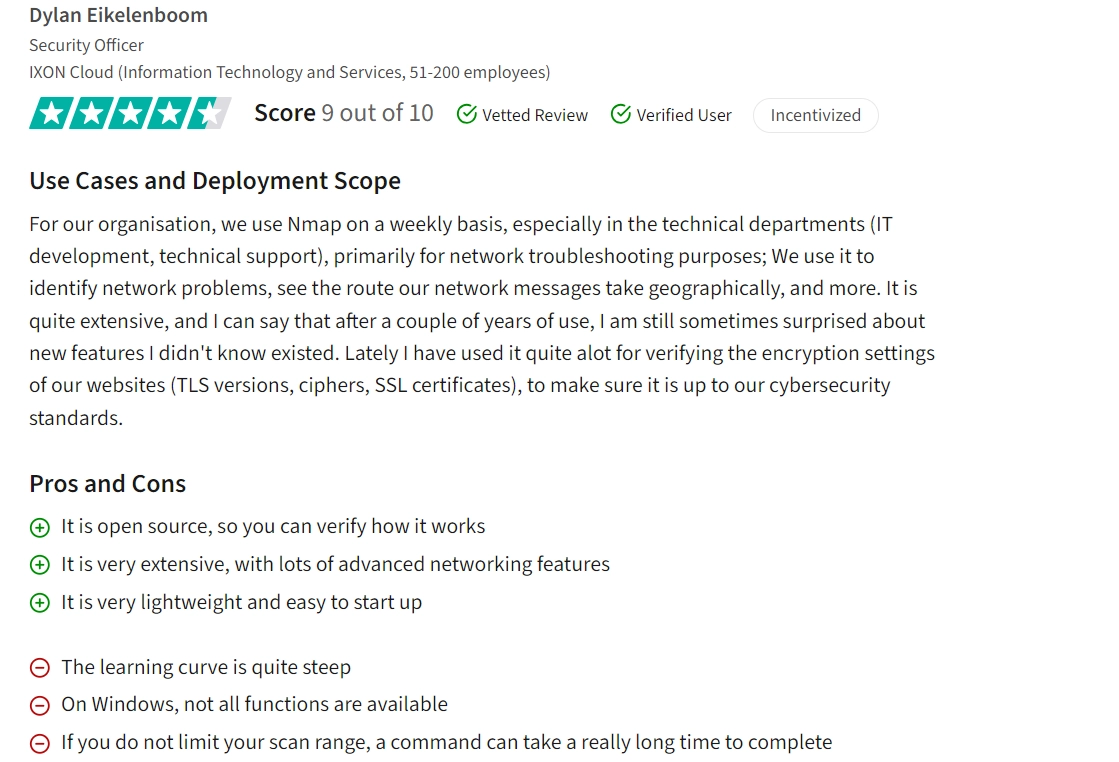
Nmap has garnered positive feedback for its user-friendly interface and effective vulnerability scanning capabilities. Users appreciate its simplicity in selecting targets and conducting scans, particularly for identifying open ports, services running on them, and potential vulnerabilities requiring patching.
The tool’s lightweight nature, advanced networking features, and real-time topology view are also highlighted as strengths.
Figure 1. A user review on Nmap
Cons
Users review also point out some areas for improvement, such as the readability of scan results, limited functionality on Windows, potential slowdowns with certain scan profiles, and the need for automated updates and patch installations1 .
Performing scans without proper range limitations is criticized since it can result in long command execution times, affecting overall efficiency.
2. CrowdSec
CrowdSec is an open-source security solution designed to identify and block aggressive behaviors that could compromise system security. It promotes community collaboration by notifying all members whenever an IP is blocked, allowing them to take proactive measures.
CrowdSec is developed in Go programming language and licensed under MIT. It is compatible with Windows and Linux platforms.
User reviews
Pros
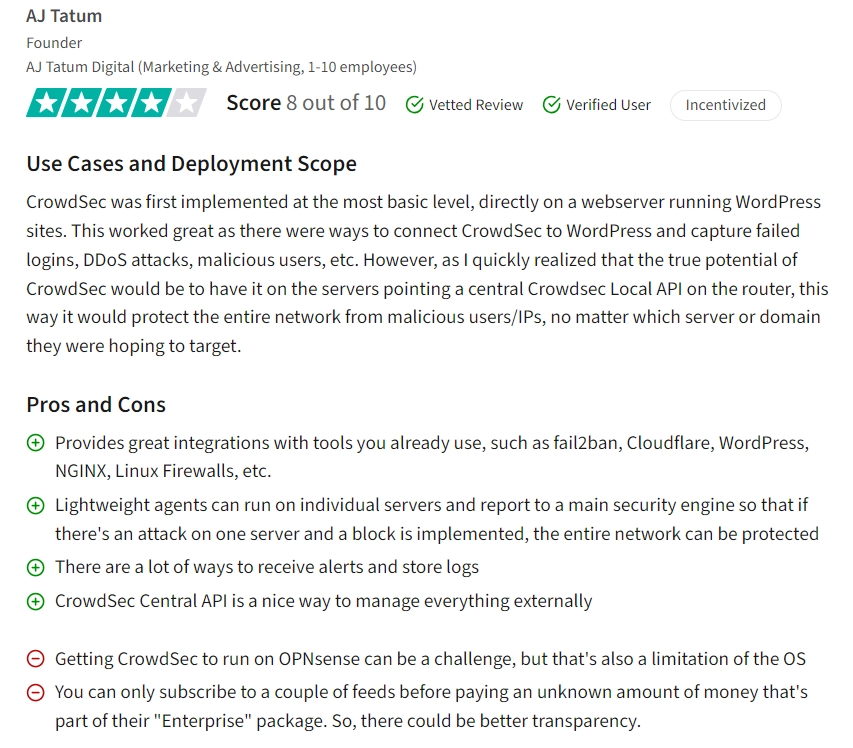
Users praise CrowdSec for integrating well with various tools like fail2ban, Cloudflare, WordPress, NGINX, and Linux Firewalls, enhancing overall network security2 . It also provides flexibility in attack remediation, allowing users to apply tailored responses based on the severity of the security risk.
Figure 2. A user review on CrowdSec
Cons
Reviews point to challenges that may arise when running CrowdSec on OPNsense due to OS limitations, requiring additional effort for implementation. Open source CrowdSec is claimed not to address more sophisticated threats or adequately cover well-configured servers since it predominantly focused scenarios on protecting against scanners, brute force attacks, and bots.
3. OpenVas
OpenVAS helps teams find security gaps early, so they can fix issues before they turn into bigger problems. The solution claims to be particularly useful for non-profit organizations seeking compliance with standards such as HIPAA and PCI. It can be used to test/audit the vulnerabilities of firewall rules and the services or applications behind them.
OpenVas, developed by Greenbone, is written in C and distributed under the GPL-2 license. It is compatible with Windows, MacOS, and Linux platforms.
User reviews
Pros
Users appreciate OpenVAS’ accuracy in finding vulnerabilities, especially when compared to other tools, and value its open source nature that allows for plugin customization. The crawler feature and result presentation are commended for their usefulness in managing security issues effectively3 .
Cons
Some users find the user interface (UI) of OpenVAS to be outdated compared to other tools, suggesting improvements for better visual representation and device-specific threat information. Like many vulnerability scanners, OpenVAS may generate false positives at times, highlighting the ongoing need for tool refinement and accuracy validation.
Figure 3. A user review on OpenVAS

Key features
When it comes to choosing the best firewall audit tool, several key factors warrant consideration to ensure optimal functionality and alignment with organizational needs. Here are essential aspects to evaluate:
1. License
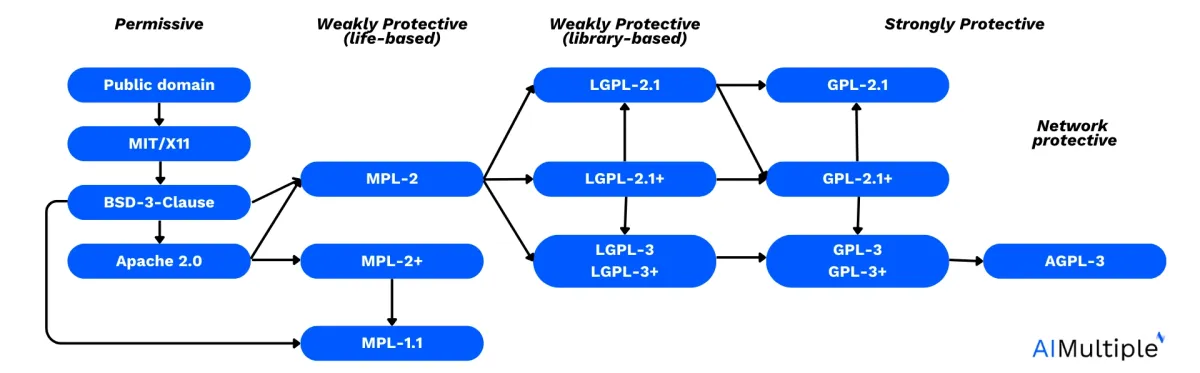
Source: David A. Wheeler (2007)4
Another aspect that you need to choose best firewall audit software for your organization is the license of the tool. The software’s license determines its usage rights, redistribution policies, and whether it aligns with organizational requirements and compliance standards.
Understanding license compatibilities is essential for developers, as it enables them to make informed decisions about incorporating third-party code into their projects while complying with legal requirements and fostering collaboration within the open-source community.
Apache 2.0 is known for its permissive nature, allowing users to modify and distribute derivative works under certain conditions. GPL-2, GPL-2+, and LGPL-2.1 are licenses that prioritize open-source principles, requiring derivative works to also be open source and adhere to specific distribution terms.
MIT is another permissive license, granting users the freedom to use, modify, and distribute software with minimal restrictions, making it compatible with a wide range of projects and licenses.
2. Platform compatibility
Considering the platform compatibility of the software ensures seamless integration with existing infrastructure, network devices, and cloud service providers. Compatibility with Windows, MacOS, Linux, and other operating systems is crucial for widespread deployment and management convenience.
Reasons to use open source firewall audit tools
1. Continuous compliance
Firewall audit tools open source enable regular firewall audits, ensuring adherence to regulatory standards like PCI DSS and GDPR and fostering a secure network environment.
2. Enhanced security management
Through detailed security audit reports and customizable audit capabilities, open-source firewall auditing solutions empower network security teams to proactively identify and address vulnerabilities, bolstering network security posture.
3. User-friendly interface
With intuitive user interfaces and customizable reports, open source firewall auditing tools offer a seamless user experience, simplifying the management of firewall configurations.
Benefits and drawbacks of working with open source firewall audit tools
Benefits
1. Cost-effectiveness
Open source software is typically free to use, eliminating licensing fees and reducing overall costs associated with firewall audit software procurement. This cost-effectiveness is particularly beneficial for organizations with limited budgets or those seeking cost-efficient solutions without compromising on quality.
2. Customizability and flexibility
One of the key strengths of open source firewall audit tools lies in their customizability. Users have the freedom to modify and adapt the source code according to their specific firewall configurations, network security policies, and compliance requirements. This level of flexibility allows organizations to tailor the tool to their unique security management needs, ensuring a more robust and tailored approach to firewall auditing.
3. Community support and collaboration
Open source projects thrive on community-driven support and collaboration. Users can leverage the collective expertise and contributions of a diverse community of developers, security professionals, and enthusiasts.
This collaborative environment fosters continuous improvement, innovation, and the rapid development of new features and functionalities, enhancing the overall quality and effectiveness of open source firewall audit tools.
4. Transparency and security assurance
The transparency of open source firewall audit tools provides organizations with greater visibility into the tool’s codebase, security mechanisms, and data handling practices. This transparency fosters trust and confidence in the tool’s security posture, as users can independently review and audit the source code for vulnerabilities, compliance with security standards, and adherence to best practices.
Additionally, the open nature of the software allows for timely security updates and patches, further bolstering network security and resilience against emerging threats.
5. Integration and compatibility
Open source firewall audit tools are designed to integrate seamlessly with a wide range of network infrastructures, firewall devices, security controls, and cloud service providers. This compatibility ensures smooth integration into existing security architectures, simplifying deployment, management, and monitoring processes.
Moreover, open source tools often support various industry-standard protocols and formats, facilitating interoperability and data exchange with other security tools and management platforms.
Drawbacks
1. Limited support
While open source communities can offer valuable assistance and resources, the support may not always be as comprehensive or timely as what closed source firewall vendors provide. This can be a concern for organizations that require immediate assistance with complex firewall configurations, troubleshooting security incidents, or resolving technical issues promptly.
2. Complexity
While customization allows organizations to tailor firewall configurations and security policies according to their specific needs, it can also lead to complexity, especially for users with limited technical expertise.
Configuring and managing open source firewall audit tools effectively may require a deeper understanding of network security principles, firewall policies, and audit processes, which may not be easily accessible to all users.
3. Integration challenges
Compatibility issues with cloud service providers, network infrastructure, or other security tools may require additional development efforts or workaround solutions, adding complexity to the implementation process. Organizations need to carefully evaluate the compatibility of open source firewall audit tools with their existing infrastructure and assess the level of effort required for seamless integration.
FAQ
How much do firewall audit software tools typically cost?
Generally, open-source firewall audit tools are available for free or at a relatively low cost, as they are community-driven and do not involve licensing fees.
On the other hand, proprietary firewall audit tools may have pricing structures that include one-time licensing fees, subscription models based on monthly or annual payments, or usage-based pricing for cloud-based solutions. It’s essential to research and compare different firewall audit tools to determine the most suitable option based on your organization’s needs and budget.
Can firewall audit software automatically recommend optimizations to firewall rules based on industry best practices?
Firewall audit software can automatically recommend optimizations to firewall rules based on industry best practices. These recommendations are often generated through the analysis of network traffic patterns, security policies, and known vulnerabilities.
By leveraging machine learning algorithms and rule-based engines, open source firewall audit tools can identify redundant or ineffective rules, detect potential security gaps, and propose optimizations to enhance the overall security posture of the network.
These recommendations may include suggestions such as:
Removing redundant or unused firewall rules to reduce complexity and improve performance.
Consolidating overlapping rules to streamline firewall policy management.
Identifying and addressing overly permissive rules that may expose the network to security risks.
Implementing rule optimizations based on specific compliance requirements, such as PCI DSS or HIPAA.
Prioritizing critical rules or traffic for more effective threat prevention and mitigation.
Security software to combine with open source firewall audit tools
Network security audit tools: Identify threats, vulnerabilities, and malicious activity to help companies mitigate cyber attacks and follow compliance with regulations.
NCCM software: Monitor information about your organization’s network devices by documenting network device configurations.
DSPM vendors: Provide network visibility into where to find sensitive data, who has access to it, and how it has been used across the cloud.
Network security policy management solutions (NSPM): Protect network infrastructure using firewalls and security policies against all threats.
SDP software: Deliver a software-defined perimeter (SDP) across the cloud to determine who gets access to what resources.


Comments
Your email address will not be published. All fields are required.