The market for next generation firewalls (NGFWs) is rapidly expanding, with an anticipated compound annual growth rate of ~11% between 2023 and 2028, increasing from $5 billion to $8.6 billion.1 As organizations seek advanced security solutions to combat evolving cyber threats, NGFWs are becoming essential.
This article examines the top 5 NGFW use cases, highlighting their critical role in modern network security and providing some case studies.
If you are looking for cost effective NGFW solutions, you may read open source NGFW.
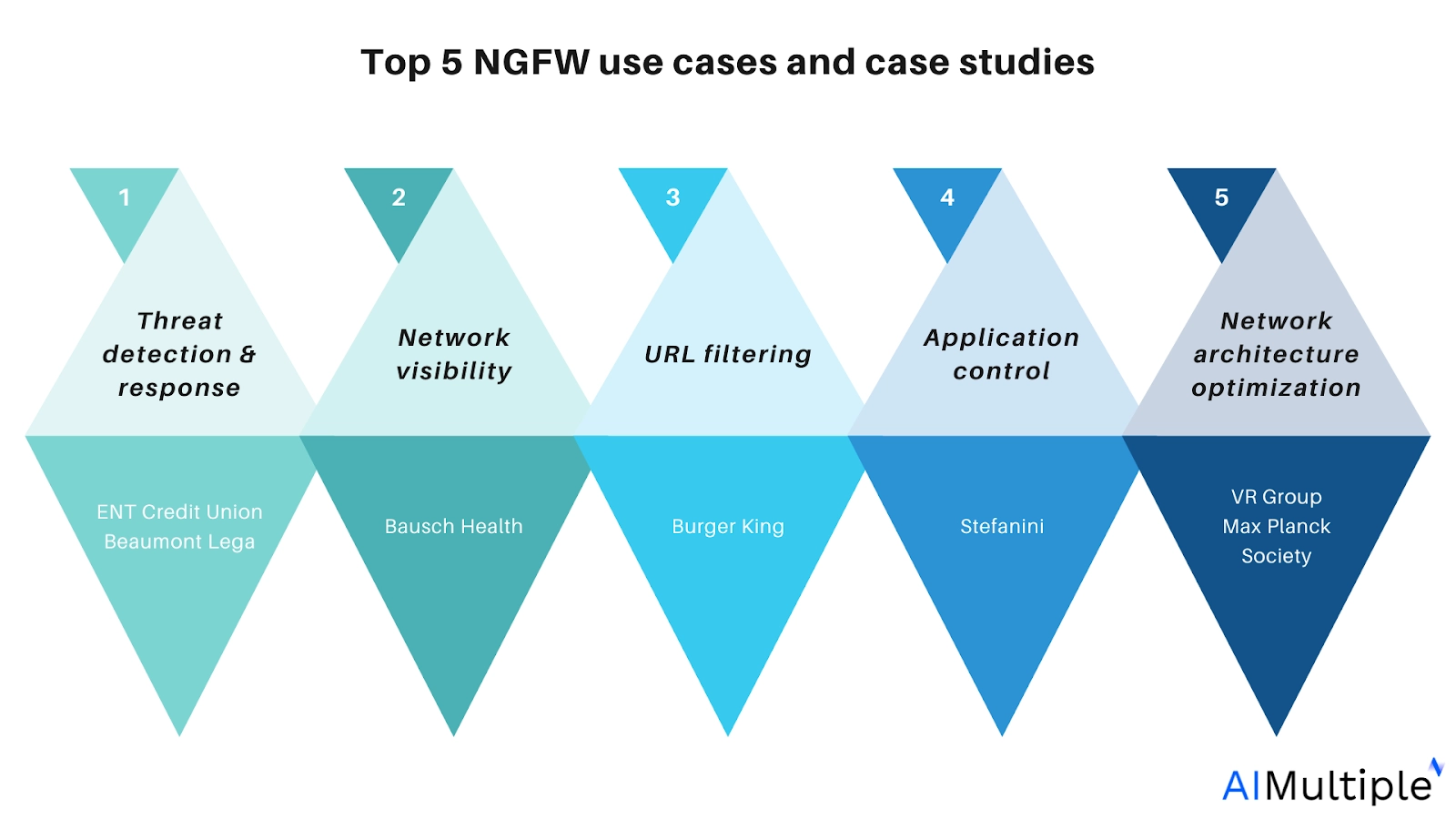
Top 5 NGFW use cases and case studies
NGFWs’ ability to offer application awareness and granular controls allows companies to manage complex threats, network traffic and network architecture, and also enable application control and URL filtering.
1. Security threat detection and response
Unlike a traditional firewall, which relies mainly on stateful inspection, a next generation firewall incorporates integrated intrusion prevention systems (IPS) and advanced malware protection. This combination allows NGFWs to inspect network traffic using deep packet inspection firewalls to identify and block malicious traffic.
Threat intelligence feeds enhance the capability to detect unknown threats, ensuring organizations can protect their networks from complex threats.
1.1. Software as a service (SaaS) security
Next Generation Firewalls (NGFWs) significantly enhance SaaS security by
- providing granular application control, advanced threat detection, and data protection
- enforcing strict access policies to ensure that only authorized users can access specific SaaS applications.
- integrating identity awareness and centralized management, NGFWs monitor and secure data flow, preventing unauthorized access and data breaches
- utilizing deep packet inspection (DPI) and threat intelligence feeds, NGFWs safeguard against advanced malware and zero-day threats
1.2. Internet of Things (IoT) security
NGFWs secure IoT devices by
- offering device identification, traffic analysis, and intrusion prevention capabilities
- enabling the segmentation of IoT devices into secure zones to reduce the attack surface and limit access to critical network resources
- monitoring network traffic and detecting anomalies, NGFWs provide early threat detection and prevent malicious activities targeting IoT devices
- Enforcing security policies and secure communication protocols, NGFWs ensure the integrity and confidentiality of data transmitted by IoT devices
ENT Credit Union case studies on security threat detection and response
ENT Credit Union, a financial services company, provides an example of the capabilities of a next generation firewall in network security by detecting and responding to advanced threats. With over $5.7 billion in assets and 355,000 members, ENT needed improved visibility into east-west traffic to detect anomalies and potential attackers.
By deploying NGFW, ENT gained advanced threat detection capabilities, including zero-day attack protection and integrated SSL encryption. This solution provided greater visibility into network traffic, accelerated threat detection and remediation, and increased operational efficiency, ensuring the protection of their members’ information.2
Beaumont Legal case studies on security threat detection and response
Beaumont Legal, a UK law firm specializing in financial services, needed to protect clients’ financial information and comply with industry cybersecurity standards.
By deploying NGFW, the firm achieved over 99.99% network uptime and internet availability, improving visibility and control over network activity. This setup ensured regulatory compliance, enhanced threat detection, and supported more billable hours, thereby increasing business opportunities.3
2. Network visibility
NGFWs provide full visibility into network traffic, surpassing the limitations of traditional firewalls. They analyze network packets and offer insights into various traffic types, from data center operations to web applications. This visibility extends to remote users and virtual machines, ensuring comprehensive monitoring and control.
Bausch Health on case study on network visibility
Bausch Health, a medical manufacturing company, needed advanced threat prevention and real-time visibility into network activity. NGFW helped the company to maximize visibility and protection across all locations. By deploying NGFWs, Bausch achieved increased throughput capability, robust feature sets for device management, and enhanced visibility into threats.4
3. URL filtering
Next generation firewalls incorporate URL filtering to enhance security compliance and content filtering. By inspecting internet protocol (IP) addresses and web traffic, NGFWs can block access to malicious or inappropriate websites. This capability is crucial for protecting users from malware attacks and maintaining a secure network perimeter.
URL filtering also supports secure SD-WAN deployments by ensuring that only legitimate web traffic reaches the network.
Burger King case study on URL filtering
Facing the end of life for its existing WAN appliances, Burger King deployed NGFWs to manage over 1,000 network points centrally. This deployment included URL filtering to block connections to malicious websites, enhancing network security.
The centralized management and URL filtering capabilities ensured secure connectivity from restaurants to headquarters, reduced downtime, and provided significant cost savings on operational and capital expenditures.5
4. Application control
Next Generation Firewalls provide robust application control, enabling organizations to manage and regulate the use of web applications. NGFWs with application awareness can identify and control specific applications within the network traffic, ensuring that only authorized applications are used.
Unlike traditional firewalls, which primarily focus on IP addresses and port numbers, NGFWs can identify and manage applications regardless of the port, protocol, or encryption used.
Next generation firewall for application control is essential for protecting the network perimeter, especially in environments with remote users and virtual machines accessing corporate resources. This application control enables organizations to enforce policies based on the specific application, user, and context. This level of control helps in mitigating risks associated with shadow IT and unauthorized application use.
Stefanini case study on application control
Stefanini, a provider of innovative IT solutions, relies on innovative technology and strong partnerships to enhance competitiveness and protect intellectual property and client data.
To protect brand value and reputation and defend against next-generation threats, Stefanini deployed NGFWs. These firewalls provide advanced protection for the network perimeter and internal networks, enabling application control, advanced identity awareness, and granular policy definitions.6
5. Network architecture optimization
NGFWs contribute to improved network efficiency by managing and prioritizing traffic types based on security policies. This ensures that critical services and applications receive the necessary bandwidth and protection, enhancing overall network performance.
VR Group case studies on network architecture
To ensure secure, high-speed connectivity for trains moving at over 200 km/h, VR Group adopted NGFWs with a cloud-based, zero-touch deployment. This approach allowed remote configuration of firewalls for each train, reducing overhead costs and enhancing reliability through load balancing across three mobile operators.
The NGFWs also provided high bandwidth and real-time data collection, optimizing network performance and improving customer scheduling updates.7
Max Planck Society case studies on network architecture
Max Planck Society, a research institution, was faced with a lack of centralized management for its existing firewall. The institution adopted NGFW after a collaborative review by IT administrators from participating institutes. The deployment streamlined the security of traffic across four research institutions, offering centralized management and comprehensive functionality.
This implementation successfully blocked millions of IP addresses and thousands of malicious web addresses weekly, reduced planned downtime, and provided substantial cost savings and improved uptime. 8
FAQs
What is a next-generation firewall?
A next generation firewall is a component of the third generation of firewall technology. It combines the capabilities of a conventional firewall with advanced network device filtering functions, such as an application firewall utilizing in-line deep packet inspection (DPI) and an intrusion prevention system (IPS). If you want to learn more about NGFWs, read to learn NGFW features.
What are the challenges of NGFWs?
NGFWs have challenges such as increased complexity, configuration difficulties, and potential performance bottlenecks. To address these issues, organizations need skilled professionals to manage and optimize NGFWs while staying updated on cybersecurity trends and best practices, ensuring a robust and secure network infrastructure.
What are the differences between traditional firewalls and NGFWs?
Traditional firewalls use port/protocol inspection and blocking at Layers 2 and 4 of the OSI model, which was effective for simpler networks. However, with the complexity of modern cloud-based networks and advanced cyber threats, this approach is no longer sufficient.
Next-generation firewalls (NGFWs) filter packets based on applications at Layer 7, offering more precise and effective threat detection. They incorporate external threat intelligence and perform deep-packet inspection, integrating application-level inspection and intrusion prevention. This dynamic and adaptive methodology allows NGFWs to defend against modern threats more effectively than traditional firewalls.
Further Reading
- Analysis of Top 4 Open Source NGFW Based on Features
- UTM vs NGFW: Which One to Choose?
- Top 8 Next-Generation Firewall (NGFW) Features
- AI Firewall vs NGFWs : Detailed Analysis & Comparison
External Links
- 1. Focus On The Biggest Security Threats Not The Most Publicized.
- 2. For complete view of network traffic, ENT Credit Union Gains East-West Network Traffic Visibility with Check Point Next Generation Firewalls. Check Point. Accessed: 21/May/2024.
- 3. Beaumont Legal | Forcepoint.
- 4. Bausch Health Case Study Firewall Deployment - Tesrex.
- 5. Whoops! 404 Error..
- 6. Whoops! 404 Error..
- 7. VR Group Customer Story | Forcepoint.
- 8. Joint Network Center (GNZ) | Forcepoint.


Comments
Your email address will not be published. All fields are required.