Network security statistics reveal that cyber-attacks affected 350+ million individuals in the U.S. In this article, we explore network security use cases and real-world examples , from detecting insider threats to managing privileged access.
| # | Use case | Case study |
|---|---|---|
| 1 | Automated insider threat detection and prevention | Netskope — Automated 200+ daily workflow |
| 2 | Centralized log management | LaBella Associates — Gained better insight into critical file servers |
| 3 | Abnormal user access detection | Leading Media Company — Detected external user access |
| 4 | Cloud-based identity management | B. Braun — Managed access to cloud applications |
| 5 | Malicious network traffic monitoring & analysis | Micron21 — Monitored and analyzed network traffic |
| 6 | Privileged access management (PAM) | Regional Healthcare Business — Streamlined privileged access control |
For more on network security:
- Learn which technologies they could use to prevent cyber attack vectors,
- Evaluate network security software based on realistic use cases.
1. Automated insider threat detection and prevention
Insider threat detection and prevention solutions identify who has legitimate network access and who utilizes it to damage the organization.
Business challenges
- Spotting malicious insiders: Malicious insiders are responsible for ~40% of all reported security incidents.1 It is difficult for security systems to distinguish between legitimate and malicious activities, since these threat actors already have internal access to organizational systems and data.
- Dynamic user behavior: User behavior can change frequently based on work assignments, projects, or personal factors, complicating the detection of anomalies. Organizations with hundreds of workflows may not display user activities while responding to security incidents.
How automated insider threat detection and prevention helps
Insider threat detection systems (e.g. IPS tools) can identify changes in user data and send alerts or display graphical insights to security teams, hence organizations can be aware of their network activity.
Read more: AI network security.
Case study: Netskope
Netskope is a worldwide cybersecurity company serving over 2,000 customers.
Challenges
Netskope aimed to gain precise insights into user activities that may indicate high-risk insider threats.
- Lack of automation while responding to insider threats: Netskope used a manual technique that required at least five employees, 10 tools, and 90 minutes of labor time to respond to each security inquiry.
- Lack of user behavior insights: Netskope needed real-time and precise insights into user actions (e.g. clicking a link, creating an account) that might indicate insider threats.
Solutions and outcome
Netskope deployed a security information and event management (SIEM) for real-time data analysis, providing visibility into insider threat behavior.
- Insider threat detection: Netskope detected insider data leakage early by automating 200+ daily workflow operations.
- Increased network visibility: The SIEM implementation helped Netskope to evaluate historical insider data and track user activity during insider threat investigations.
- Data monitoring: Netskope leveraged cloud SIEM’s content management feature to identify data downloads. This enables Netskope to visualize malicious attempts to exchange data with personnel or competitors.2
2. Centralized log management
Log management is crucial in various IT and business functions, providing valuable insights and enabling several use cases including threat detection, business intelligence, and network monitoring.
Business challenges
- Volume: Large IT systems create a large amount of log data, making it difficult to maintain and evaluate manually.
- Complexity: Logs are created from many sources and formats, making it challenging to aggregate and analyze them.
- Security: Logs include important information such as user passwords and network architecture, thus they need to be protected from unauthorized use.
How centralized log management helps
Log management enables simple analysis and security correlation. Centralizing your logs can help you improve your mean time to detection (MTTD) and mean time to resolution (MTTR) for application bugs and security breaches.
Case study: LaBella Associates
LaBella Associates is a full-service engineering firm headquartered in New York, with over 1,500 architects, and employees operating across 30 locations.
Challenges
- Lack of data visibility: LaBella required a log management system to monitor its sensitive file servers, provide access history reports, and use other critical data for forensic investigation in data breaches. Read more: Data breach incident response.
- Lack of log visibility: LaBella Associates’ manager stated that they needed a solution that keeps records of file system activity and monitors user logon and logoff activities to detect anomalies.
- Manual login activity searches: LaBella Associates’ manager stated to monitor file system or login activities they had to visit each file server and manually scan for logs, which was time-consuming.
Solutions and outcome
LaBella Associates deployed a security information and event management (SIEM) solution with log management features to control logs across domains.
- Strong log management: LaBella Associates’s IT security team could gain information on who logged critical file servers to do log forensics when a breach occurred.
- Effective access management: LaBella Associates could display illicit group policy modifications made by employees and contractors with access to the internal network. Read more: Network security policy management.
- Increased domain security: The company identified edited or edited logs on the domain controller.
- Streamlining log investigations: LaBella Associates eliminated the laborious procedure of identifying and determining who performed group membership changes. 3
3. Abnormal user access detection
Abnormal user access detection, also known as outlier user access detection, is identifying user access data points that depart from what is normal, standard, or anticipated, rendering them inconsistent with the remainder of a dataset. Network security statistics reveal that ~70% of cyber attacks against businesses start with compromised credentials. Therefore evaluating user behavior is crucial.
Business challenges
- High data volume and variety: Large volumes of data from various sources (weblogs, application logs, network traffic, etc.) need to be processed and analyzed.
- Real-time data flows: Detecting anomalies or patterns in real-time requires high processing power and efficient algorithms. Organizations that lack automation might bypass outlier access data points in their workflows.
- Complex user interactions: Users interact with systems in complex ways that are difficult to model and predict. This makes anomalies uncommon and difficult to detect.
How abnormal user access detection helps
Incident response tools can identify possible user breaches by analyzing unsuccessful login attempts (see Figure 1).
Figure 1: Detecting abnormal user access in a dataset
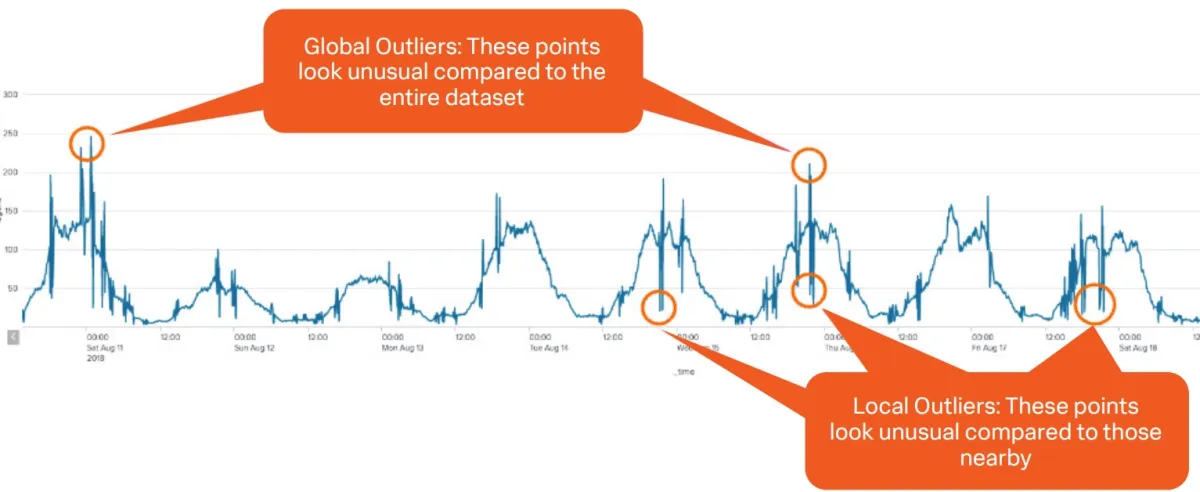
Source: Splunk4
Case study: A leading media company
A leading media company aims to detect anomalies to protect sensitive information from most common cyber attack vectors in multiple companies’ data sets.
Challenges
- High third-party risk: The company relying on third-party providers for services increases security vulnerabilities.
- Insider threats: The company had unique challenges with insider threats due to media employees required to access sensitive information and technology.
Solutions and outcome
The media company deployed user and entity behavior analytics (UEBA) software to detect anomalies by comparing current behavior against the established baselines.
- User and entity behavior analytics (UEBA): The company leveraged UEBA to detect suspicious activities in real-time and identify user behavior anomalies that may suggest security risks.
- Enhanced network visibility: The company gained better insight into its security posture by monitoring and analyzing user behavior, network traffic, and system activities.
- Advanced threat prevention: The Company’s security team monitored unusual behavior and anomalies detecting and alerting on targeted attacks, and identifying sophisticated threats like malware.5
4. Cloud-based identity management
Cloud-based application security is an approach to protect applications hosted in cloud environments from potential security threats and vulnerabilities.
Business challenges
- Lack of visibility: Organizations with several cloud services are accessible outside of corporate networks and via third parties, can lose track of who has access to their data.
- Multitenancy: Companies with multiple client infrastructures stored in public cloud environments are more vulnerable to malicious attackers, since client infrastructures may infect your hosted services as secondary harm.
- Access management and shadow IT: Organizations that enable unfiltered access to cloud services from any device or location might lose control over access points across cloud environments. For example, organizations with IT systems deployed by external parties will have low control over device access management. This will increase shadow IT and might cause attackers to bypass network limitations.
- Compliance: Organizations that are not actively monitoring and recording cloud security, face considerable governance and compliance risks when handling customer data.
How cloud-based identity management helps
- Flexible security configurations: Cloud platforms allow for flexible security configurations that can be quickly adjusted as requirements change. For example, security teams can dynamically adjust firewall rules based on real-time threat intelligence. Read more: Threat intelligence platforms.
- Regular security updates: Cloud security providers (CSPs) regularly update organizational infrastructure to protect against the latest threats. For example, CSPs can execute automatic patching of cloud infrastructure to mitigate known vulnerabilities.
- Advanced security features: Cloud service providers (CSPs) offer advanced security features such as encryption, identity and access management (IAM), and threat detection that can be challenging to implement on-premises. This can help organizations to use built-in encryption services to protect data at rest and in transit. For example, security teams can use IAM to simplify user access by enabling a single set of credentials to access multiple applications.(employees using their corporate login credentials to access email, HR systems, and project management tools, etc.).
- Reduced capital expenditure: By leveraging cloud services, organizations can reduce the capital expenditure associated with purchasing and maintaining on-premises security hardware. For example, organizations can use cloud-based firewalls and security gateways instead of investing in expensive physical hardware.
Case study: B. Braun
B. Braun is a healthcare company located in Germany with 60,000+ employees. B. Braun aimed to improve security, ensure compliance, and manage access to solid data in a hybrid IT environment.
Challenges
- High employee turnover causing complex access management: B. Brauons employee landscapes are continually changing due to job changes, turnover, and new hires.
- Manuel data handling: B. Braun’s manual processes slowed down the creation and deletion of user accounts. This caused an elevated risk of unauthorized data access, and failing to meet data security regulations.
- Digital transformation: B. Braun sought an identity management system to promote digital transformation. Thus the company needed a solution that communicates to on-premise infrastructure and cloud services such as Office 365.
Solutions and outcome
B. Braun in Germany automated identification and access management to improve security.
- Ensured appropriate access for the right people: B. Braund leveraged automated account creation and termination. For example, consider the HR department entering new hire information (name, position, department, start date). The IAM solution helped the company to automatically create user accounts for the new hires across various systems, such as Active Directory (AD), email system, and file storage.
- Enhanced access control: The deployment improved compliance with data security rules, reducing the risk of unauthorized use. For example, the IAM system assigned user a role based on their job function within the finance department:
- Finance manager: Full access to all financial reports, transactions, and administrative functions.
- Accountant: Access to daily transaction records, but not to administrative settings.
- Digital user access notifications: B. Braun connected its on-premises infrastructure with cloud services like Office 365. Employees understood the access status of their requests.6
5. Malicious network traffic monitoring & analysis
Malicious network traffic analysis monitoring & can help companies in identifying abnormal or suspicious activities within network traffic that may indicate a security threat or attack.
Business challenges
- Complexity and volume of data: Network traffic data can be massive, comprising millions of packets and connections per minute. Analyzing this vast amount of data in real-time or near-real-time requires scalable and efficient detection algorithms and infrastructure.
- Variability in traffic patterns: Legitimate network traffic patterns can vary widely based on time of day, user behavior, and application usage. Distinguishing between normal variations and genuinely malicious patterns requires sophisticated anomaly detection techniques.
- Encryption and privacy concerns: Increasing use of encryption (e.g., HTTPS, TLS) in network communications obscures packet contents, making it challenging to inspect traffic for malicious payloads or patterns.
How malicious network traffic monitoring & analysis helps
Malicious network traffic monitoring & analysis features can quickly identify abnormal or suspicious behaviors within network traffic. Organizations can use network security audit tools or network monitoring tools that can identify surges in the network or port traffic. These systems can:
- Monitor network security for potential data exfiltration.
- Analyze proxy communications to identify outliers.
- Detect attack vectors including distributed denial-of-service (DDoS) attacks, botnet activity, and malware.
Case study: Micron21
Micron21 is a data center distributor located in Melbourne.
Challenges
- Massive network and bandwidth: As Micron21’s network grew and the quantity of bandwidth used rose, it became increasingly difficult to evaluate and categorize traffic patterns.
- Fragmented data sources: Micron21’s data is scattered across multiple systems, departments, and platforms, making it difficult to get a unified view.
Solutions and outcome
Micron21 deployed a network security solution to monitor their network.
- Network traffic analytics: Micron21 began analyzing vent histories, traffic logs, and accessible analytical data.
- Network monitoring based on IP groups: Micron 21 allows its clients to log on and examine their traffic inside their IP group, delivering information on the network metrics passing via the client’s IP range.7
6. Privileged access management
Privileged access management (PAM) refers to the practices and technologies used by organizations to secure and control access to privileged accounts, which have elevated permissions and access privileges within IT systems and networks.
Business challenges
- High volume of accounts: Organizations might maintain dozens or even hundreds of privileged accounts to allow administrators to do critical duties. These privileged credentials pose a significant security risk since they can be exploited by their owners or hijacked by intruders due to a lack of access control and visibility.
- Access control: Ensuring only authorized users have access to privileged accounts and these users have the minimum level of access necessary for their roles.
- Visibility: Keeping track of all privileged accounts, including those created by default, manually, or by applications.
- Access provisioning and de-provisioning: Without automated workflows or a privileged access management (PAM) solution organizations will have difficulties ensuring timely provisioning and de-provisioning of privileged accounts to avoid unauthorized access.
How assigning privileged account assessment helps
Assigning privileged permissions for users, business processes, and systems can right-size access controls. This will enforce the least privilege and limit access rights for users to the absolute minimum, mitigating the damage caused by external and internal threats.
Read more: Role-based access control (RBAC), RBAC use cases, RBAC examples.
Case study: A regional healthcare business
A regional healthcare business with over 8,000 employees in California.
Challenges
- Accumulation and over-provisioning of privileges: As the employees in the companies expand their job roles, they take on new duties and privileges while maintaining access to earlier ones. This causes over-inherited privileges.
- Inconsistent and outdated information regarding users, accounts, assets, and credentials: The company had multiple backdoors for attackers, including ex-workers who still have access to corporate accounts.
Solutions and outcome
The organization deployed a privileged access management (PAM) tool and audited Secure Shell (SSH) connections between UNIX and Linux environments to enhance user access controls.
- Robust privileged access controls: The deployment streamlined the implementation of complicated job changes, such as disabling access when privileged individuals leave the business.
- Policy-based rules: The company created rules that enabled policy-based access to privileged accounts.
- Privileged session management (PSM): The company automatically checked out privileged credentials from a safe and audited all sessions.8
Also, check article on network automation use cases.
Key cyber security software to maintain secure business processes
- Microsegmentation tools: Segment a network into granular forms and apply security policies based on each network zone. Read more: Microsegmentation use cases.
- Network security audit tools: Identify vulnerabilities, and malicious behavior to assist businesses in mitigating cyber-attacks.
NCCM software: Identify and record network device settings; detect, audit, and alert on changes. - DSPM vendors: Enable network insight into sensitive data locations, access levels, and use throughout the cloud. Read more: DSPM use cases.
- Network security policy management solutions (NSPM): Develop policies and procedures to protect an organization’s network and data from illegal access, use, disclosure, and interruption.
- SDP software: Hide Internet-connected infrastructure (servers, routers, etc.) so that external parties and attackers cannot see it, whether hosted on-premise or in the cloud.
- Firewall audit software: Provide visibility into your firewall’s current access and connections.
- Network traffic analyzers (NTA): Collects and analyzes network flow data to give insight into traffic volume, type, and network device performance.
Further reading
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. Tessian is Now Proofpoint | Proofpoint US.
- 2. ”Automating insider threat monitoring”. Netspoke. February, 2023. Retrieved June 26, 2024.
- 3. LaBella leverages Log360 to enhance its security posture.
- 4. Security Use Cases Enhanced by AI and ML - Thanks | Splunk.
- 5. ”Leading Media Company“. LinkShadow. Retrieved June 26, 2024.
- 6. ”A cure for legacy access management ills“. One Identity. Retrieved June 26, 2024.
- 7. Securing Datacenter Using NetFlow Analyzer - A case study .
- 8. IAM Healthcare Case Study : Deploying an Integrated PAM and IGA Solution - Integral Partners. Integral Partners LLC




Comments
Your email address will not be published. All fields are required.