During my career, I have participated in many PCI-DSS processes across various sectors. I have categorized PCI-DSS v3 into three phases, from the simplest points to the most advanced, to help companies achieve PCI-DSS certification.1
I have compiled some of the essential software types and best practices to fulfill part of these requirements for data protection efficiently. PCI-DSS compliance involves balancing the people, process, and technology triangle by deploying various hardware and software solutions, along with implementing cybersecurity measures such as:
- GRC
- DLP
- Vulnerability management incl. log/patch management & pen-testing
- Privileged access management (PAM)
- Encryption and tokenization
For other regulations:
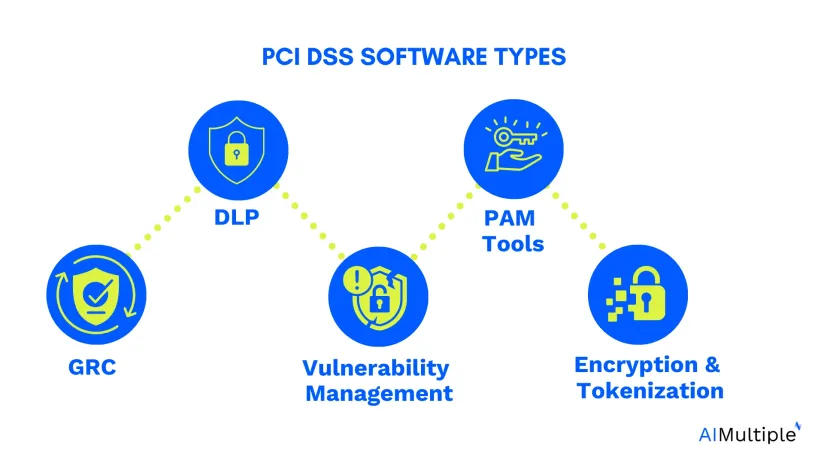
Here are the 5 types of software you will need:
1. Governance, risk, & compliance (GRC) tools
GRC tools are essential for orchestrating and managing the various compliance, risk management, and governance processes required by PCI DSS. These tools help organizations automate compliance workflows, manage risk assessments, and maintain audit trails, which are vital for ensuring ongoing adherence to PCI DSS requirements.
GRC platforms enable organizations to centralize and streamline the documentation, testing, and remediation efforts necessary for PCI DSS compliance, making it easier to manage complex security frameworks and regulatory requirements.
Here are the best closed and open-source GRC tools on the market:
| Closed-Source Tools | Closed-Source Features | Open-Source Tools | Open-Source Features |
|---|---|---|---|
| Archer Insight (RSA Archer) | – Risk exposure calculations – Risk quantification – Pre-built models – Enterprise risk management | Open-AudIT Community | – Automated network discovery – Software/hardware inventory – Configuration management – Compliance reporting |
| AuditBoard | – Automated content generation – Reporting dashboards – Automated audit | ZenGRC | – Policy management – Risk assessment – Control monitoring – Audit management – Collaboration features |
| IBM OpenPages | – Integrated risk management – Regulatory compliance – Policy management – Reporting and analytics | OpenGRC | – Risk assessment – Policy management – Incident management – Compliance monitoring – Customizable workflows |
More research on GRC:
2. Data loss prevention (DLP) software
You can not be PCI DSS compliant without having a comprehensive data loss prevention solution in your business covering the network, cloud, and endpoint. This software not only helps prevent unauthorized access or leakage of critical data but also ensures that your business adheres to regulatory standards, along with GDPR, thereby minimizing the risk of breaches and maintaining customer trust.
In addition to the crucial best practices of DLP and data classification, it is important to identify risks for business departments and define ‘data’ for each department. This process will help build more robust DLP policies tailored to each department, significantly enhancing the protection of the organization.
Here are the top DLP vendors on the market that cover PCI DSS compliance:
| DLP Software | # of Reviews | User Rating | Pricing | Free Trial (in days) |
|---|---|---|---|---|
| Endpoint Protector by CoSoSys | 160 | 4.5 | – | ✅ |
| Trellix DLP | 1,792 | 4.2 | – | ✅ 60 |
| Acronis Cyber Protect | 705 | 4.5 | $53 | ✅ 30 |
| Sophos Intercept X | 480 | 4.5 | – | ✅ 30 |
| Safetica DLP | 263 | 4.7 | $54 | ❌ |
3. Vulnerability management & pen-testing tools
Vulnerability scanning & management are vital for identifying and mitigating security weaknesses in systems handling cardholder data. These tools are essential for fulfilling PCI DSS requirements related to maintaining a secure network (Requirements 6 and 11).
Regular vulnerability scans and penetration tests help organizations identify and fix potential threats and vulnerabilities before exploitation. Log and patch management ensure systems stay updated and monitor for suspicious activities. These practices detect anomalies, prevent breaches, and maintain regulatory compliance, strengthening overall security and reducing cyberattack risks.
Vendors:
- Penetration or pen-testing
- Invicti
- PortSwigger Burp Suite
- Rapid7 Nexpose
- Qualys
- Tenable.io
- SIEM solutions for log management
- Splunk Enterprise
- LogRhythm SIEM
- IBM (Palo Alto) QRadar
- Patch Management solutions
- ManageEngine Patch Manager Plus
- NinjaOne
Our recommendations
As part of PCI-DSS compliance, organizations must hire third-party, independent penetration testing services with full coverage of internal and external networks. A PCI-DSS Qualified Security Assessor (QSA) reviews the penetration test report along with all other necessary requirements of PCI-DSS for the company to check if requirements are fulfilled fully or partially at the end of the first audit cycle.
4. Privileged access management (PAM) tools
Privileged access management (PAM) software is crucial to ensure that only authorized personnel have access to payment-related data, in compliance with PCI DSS requirements. These tools help organizations enforce strong access control measures (Requirement 7), ensuring that the user’s access to sensitive data is restricted based on the principle of least privilege.
They also play a key role in managing user identities, implementing multi-factor authentication (MFA), and maintaining detailed access logs. Most of these tools also have screen recording features for auditing purposes.
Top vendors on the market:
| Vendor | Type of Solution | Free Trial | # of Employees |
|---|---|---|---|
| Okta | Identity Management PAM MFA | ✅ | 8,148 |
| CyberArk | Access Management PAM Identity Management MFA | ❌ | 3,596 |
| Ping Identity | Identity Management Access Management MFA | ✅ | 1,829 |
| Delinea | PAM Identity Management MFA | ✅ | 1,121 |
| Duo Security | Access Control MFA Identity Management | ✅ | 589 |
- The vendors are ranked based on the number of employees (on LinkedIn).
- Vendors with more than 500 Employees were selected.
5. Encryption & tokenization solutions
Encryption and tokenization are fundamental to protecting cardholder data as mandated by PCI DSS. Encryption solutions convert sensitive data into an unreadable format, ensuring that even if data is intercepted, it remains inaccessible without the appropriate decryption keys. Tokenization replaces sensitive data with unique identifiers (tokens) that are unusable by attackers.
These technologies address PCI DSS requirements related to data protection (Requirements 3 and 4) and are critical in securing data at rest and in transit.2
Vendors:
- Thales CipherTrust
- Vormetric Data Security
- Protegrity
Best practices to implement these solutions
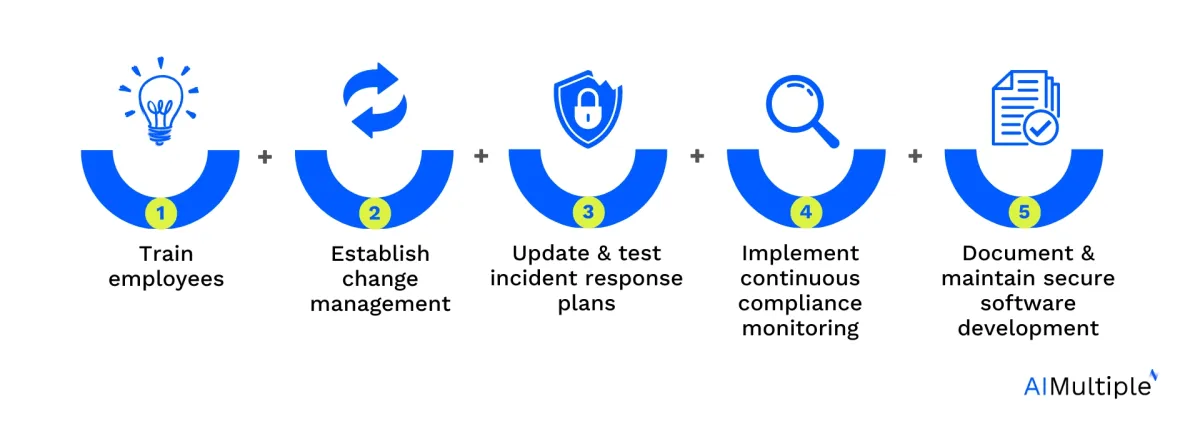
To effectively achieve and maintain PCI DSS compliance, companies should focus on implementing process-related changes that enhance their security posture. Here are key process-oriented best practices:
1. Train employees on PCI DSS security controls
Regularly train staff involved in handling payment card data on PCI DSS requirements, security controls, and best practices. This includes educating them on detecting and mitigating risks such as malicious software and unauthorized access, ensuring that human factors don’t compromise the company’s PCI DSS compliance efforts.
Training platforms:
- PCI Security Standards Council (PCI SSC) Training Programs: Offers a range of courses tailored to PCI DSS, including on-site and online options for comprehensive education on compliance.
- SANS Institute: Provides in-depth security and compliance training, including specific modules on PCI DSS compliance, focusing on real-world applications and threat mitigation.
2. Establish change management
Implement a formal change management process to ensure all modifications to systems, applications, and network configurations are reviewed, tested, and approved before deployment. This prevents unauthorized changes that could compromise PCI DSS compliance and the security of cardholder data.
3. Regularly update and test incident response plans
Develop and maintain an incident response plan tailored for potential data breaches involving cardholder data. Regularly test the plan through cyber drills to ensure your team can respond effectively, minimizing the risk of non-compliance with PCI DSS requirements.
4. Implement continuous compliance monitoring
Set up processes to continuously monitor PCI DSS compliance, including automated tracking of key compliance metrics and regular internal audits. Use PCI compliance software and tools to identify and address issues in real-time, ensuring ongoing protection of sensitive cardholder data.
5. Document and maintain secure software development practices
Integrate secure coding standards into your software development lifecycle (SDLC) and regularly review them to address emerging threats. This helps ensure that all software handling cardholder data is developed and maintained in compliance with PCI DSS standards, reducing the risk of data breaches.
FAQs
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a vital framework for businesses handling payment systems, ensuring the protection of payment data throughout its lifecycle. To achieve PCI DSS certification under version 4.0, a company must meet 370 to 500 requirements.
Who needs PCI DSS compliance?
All merchants that accept card payments and handle, store, or transmit payment information, regardless of their business size or transaction volume, must comply with PCI DSS requirements to work with major payment card companies. PCI DSS is designed to ensure that merchants take the necessary steps to protect cardholder data and prevent fraud. Failure to comply can result in significant penalties, increased transaction fees, or even the loss of the ability to process card payments.
Why is hardware documentation important for PCI DSS compliance?
Hardware documentation provides detailed records of device configurations, physical security controls, and access permissions. This evidence is essential to prove that systems handling cardholder data are securely set up and maintained, meeting PCI DSS requirements.
How does hardware documentation support PCI DSS compliance software?
Compliance software leverages hardware documentation to automate the collection of audit evidence, track configuration changes, and ensure continuous monitoring. This streamlines the compliance process and helps quickly identify potential security gaps.
Further reading
- 12+ Best Data Loss Prevention (DLP) Software
- Tackling Critical Data Protection Challenges
- DLP in Banking: Best Software & Practices
If you need further help in finding a vendor or have any questions, feel free to contact us:
External resources
- 1. PCI Security Standards Council – Protect Payment Data with Industry-driven Security Standards, Training, and Programs. PCI Security Standards Council
- 2. PCI DSS Quick Reference Guide. PCI Security Standards.

Comments
Your email address will not be published. All fields are required.