Source: IC31
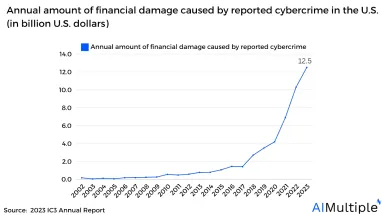
Network security statistics show that the monetary damage caused by cybercrime reported to the U.S. increased by around 21% in 2023, reaching a historical high of $12.5 billion.
Micro segmentation tools may assist companies in:
- leveraging fine-grained security controls,
- and dividing network zones with customized policies down to the application level to decrease the risk of cybercrime.
See the top 7 real-life micro segmentation examples with stories from diverse industries:
1. California Department of Water Resources
The California Department of Water Resources (CDWR) regulates water delivery networks and offers flood protection, inspection, and management services across the state with ~3,500 employees.
Challenges
- Managing high-volume communication: CDWR had large volumes of data throughout daily operations, hence their IT team needed a granular solution that separates hardware, software, and cloud environments to divide massive communication flows.
- Physical hardware imposed security limitations: The organization possessed low operational agility since it had to support up to 5,500 servers, and 2,600 applications. CDWR needed a software-defined solution to segment its network zones across thousands of endpoints.
- Lack of network security automation: CDWR indicated that they suffered from a lack of automation. This resulted in inefficiencies in delivering customized micro segmentation policies across layers and apps on their multi-site data centers with several suppliers.
Read more: Network security automation tools, micro segmentation in cloud.
Solutions and outcome
The California Department of Water Resources (DWR) changed and triggered its multi-tenant data center with new micro segmentation technologies.
- Decreased service delivery time: Due to the high volume of network communication the service delivery was slow-paced and manual feeding was required. With micro segmentation, the company divided its business units into zones, each with its communication flow, which decreased service delivery time from 5 days to 30 minutes.
- Enhanced operational agility with OT network segmentation: Day-to-day operations were complex and operational agility was low. Micro segmentation enabled administrators to segment operational technology and create automated policies for certain user groups that use specific infrastructure. For example, after setting a software-defined perimeter (SDP) for the pipeline facility machines, administrators could create an automated policy stating that only CDWR pipeline operators can modify facility data center information during work hours.2
Read more: SDP software.
2. Frankfurter Bankgesellschaft
Frankfurter Bankgesellschaft is a Zurich-based Swiss private bank with a Frankfurt subsidiary. The cooperation also provides private financial services under contract to Sparkassen-Finanzgruppe, Germany’s largest retail banking network.
Challenges
- Highly heterogeneous network environment: The bank’s infrastructure was highly heterogeneous, with equipment from several manufacturers, causing a lack of reliability and simplicity in network security. For example, the bank was operating on a network of three web proxies from three separate manufacturers. As a result, their administrators had to set up, test, and troubleshoot in three different areas. This made the system more error-prone and less secure.
- Separated IT communication: Frankfurter Bankgesellschaft had separate IT divisions in Zurich and Frankfurt that could not share a communication platform or a consistent network architecture.
- Emerging compliance laws: The Swiss Financial Market Supervisory Authority (FINMA) began to tighten its audits of banks’ IT systems, enforcing rigorous new data and privacy protection rules. Thus, Frankfurter Bankgesellschaft had to follow strict compliance for auditing each supervisory area in the bank.
Solutions and outcome
Frankfurter Bankgesellschaft partnered with one data center micro segmentation cloud workload protection provider and one system integrator to deploy and simplify network security, integrate infrastructure, and comply with FINMA’s new standards.
- Centralized management: With the newly deployed server and application-centric network architecture, the bank could create its data centers (server, network, and storage) as an interconnected system from a single source.
- Increased workspace protection: Micro segmentation and network monitoring provided increased lateral security, protecting the bank’s internal applications against workload-level vulnerabilities (e.g. exploitation of remote services, lateral tool transfers, and service session hijacking). This enabled the bank to secure traffic across applications, identify vulnerabilities, and flag anomalies in their workspace.
- Enabled an application-centric network infrastructure: With the legacy systems the bank was utilizing static IP addresses, however, with the new micro segmentation implementation the administrators started to use application-centric infrastructure (ACI) interfaces with their firewall architecture via API that dynamically change the rules that allow these systems to communicate using a risk-based approach.
- Freed up engineers: With the new automation capabilities the bank has allowed its engineers to focus on engineering rather than administration.
- Adhering to FINMA laws: The new solution assisted the bank in undertaking due diligence examinations of their cloud services, which include:
- A summary of the regulatory landscape to provide context.
- A checklist that outlines the concerns to be solved and aligns internal application services with regulatory requirements.3
3. Flex
Flex is a manufacturing supplier that provides technology, supply chain, and industrial solutions to various sectors and end markets spanning a global workforce in 30 countries.
Challenges
- Old cybersecurity systems: Flex previously depended on standard firewalls to secure its networks. As cyber threats got more complex, the corporation saw the need for advanced cybersecurity capabilities (e.g. intrusion prevention, URL filtering, and sandboxing) to get more granular access control over their network.
- Remote access controls: Flex needed to improve remote access controls for worldwide locations using regional data centers and cloud services.
Read more: Mandatory access control, role-based access control (RBAC).
Solutions and outcome
Flex collaborated with a network and security partner to roll out the platform and migrate from older solutions. Flex secured internal network traffic and isolated network resources based on certain conditions and with context.
- Supported zero trust architecture with micro segmentation: Prevented intruders from moving laterally across the network with the zero trust strategy. This ensured that confidential company information could only be accessed under specific conditions. For example, customer data and intellectual property stored in company servers can only be accessed by company CISOs and administrators.
- Separated remote users and operational infrastructure: With the new deployment, Flex applied micro segmentation practices integrated by analyzing network threats and filtering risky URLs from company machinery. As a result, the company secured remote access standards for 20,000 people in seven days, preventing malware from transmitting from home users to the operational network.
- Enhanced network security automation: The new micro segmentation vendor helped Flex to leverage automation solutions required to optimize operations and decrease human error. For example, engineers could respond quickly to threats without constantly improving the rules and monitoring the network around the clock.4
4. Kansas City Children’s Mercy Hospital
Children’s Mercy is a medical center for children in Kansas City, Missouri.
Challenges
- A high number of specialized devices: Children’s Mercy has a growing array of specialized interconnected medical assets that remain unmanaged for a long period, resulting in vulnerabilities across the medical system.
- Lack of departmental role allocation: The collaboration across medial billing, bio-med, and clinical engineering lacks a well-defined role allocation.
Solutions and outcome
Children’s Mercy’s Leadership moved forward with micro segmentation implementation, focusing on grouping and configuring unsupervised medical devices while assigning roles.
Thus, the company created a risk-scored inventory of linked assets and accurately identified vulnerabilities in current devices. Children’s Mercy administration identified and eliminated outmoded processes, and reorganized employees’ roles with “security group tagging”.
- Automated micro segmentation policies: Device-specific security policies were automatically generated and offered to Children’s Mercy’s system.
- Security grouping: Leadership used device-specific profiles and security policies by applying security group tagging to assign device privileges. For example, managers configured the database to ensure only authorized staff (e.g. medical billing clerks) could access financial patient information.5
5. MaterDei Hospital
MaterDei is one of the major hospital systems in Minas Gerais, Brazil.
Challenges
- Complex IT infrastructure: MaterDei’s has a complicated IT architecture including a mix of Windows, Linux, and MacOS systems. MaterDei also uses Kubernetes and Docker to create microservices, and most of its apps are cloud-based, with distinct cybersecurity controls required for each network tier.
- Low granular access control across endpoints: MaterDei is challenged to achieve granular network segments over data flows against endpoint attacks. For example, the company did not have API-level security, hence when an IT employee who can access the company database tries to “edit” certain API content the application will perform the request since no access control permissions are set for the specified API.
- Costs and technology concerns: MaterDei is concerned about finding a cost-effective solution with flexible features based on their unique business needs.
Solutions and outcome
MaterDei has implemented a micro segmentation solution and changed its network security rulesets in less than three weeks.
- Increased granular control: MaterDei has secured its multi-state Brazil hospital network and patient services by lowering the attack surface. The company has achieved critical granular information flows into its workload connections across numerous cloud data centers.
- Rapid network visibility: MaterDei gained continuous network visibility, which enabled detailed views into all resources and cross-segment traffic in data centers. For example, administrators could view access restrictions based on network zones such as “sales department IT administrators with limited permissions”
- Higher authority on network security policy management: The company gained control and flexibility on network security configurations throughout its complicated hybrid IT architecture. For example, administrators could define who can access each part of a system, and what they can do with that access.6
Read more: Network security policy management solutions.
6. Modern Woodmen
Modern Woodmen is a financial services and insurance company that offers a self-service website that allows users to check accounts, manage portfolios, and pay bills.
Challenges
- Heterogeneous network infrastructure: The organization used a data center product to manage its network backbone across many data centers. However, the data center product only controlled virtual infrastructure traffic, leaving around 20% of physical device communication uncontrolled.
- Complex micro segmentation implementation: The company needed help to handle and monitor all east-west traffic at scale, however, the dashboard management took a lot of work. This resulted in a security gap when implementing micro segmentation policies across various environments.
- Lack of east-west segmentation: The lack of segmentation standards and east-west firewalling across development environments left a security gap. This caused an increased attack surface during lateral data flows including database replication, file transfers, and inter-process communication.
Solutions and outcome
Modern Woodmen upgraded their network infrastructure to a micro segmentation solution designed for modern networks and can operate in virtual, cloud, and data center settings.
- Improved network control: Migrating to a micro segmentation solution improved Modern Woodmen’s network center across virtual and physical infrastructures, including distributed data centers. For example, with the legacy data center product administrators could not manage 20% of the physical infrastructure, however, the micro segmentation solution enabled administrators to manage workflows operating on virtual machines and all the physical appliances using a single GUI.
- Enabled network traffic monitoring with tags: The company prevented possible threat actors from transiting the network by monitoring network traffic and applying tags in real time. For example, labeling all API services with an API tag, enabled the company to define sources and targets for east-west firewalling across application, hardware, and user end-points.7
Read more: Firewall assessment.
7. Sani Marc
Sani Marc is a leading chemical manufacturer and distributor of cleaning and sanitation products in Québec, Canada.
Challenges
- Low level of security: Sani Marc uses firewalls and (endpoint detection and response) EDR tools to secure its perimeter, however, the level of security provided by firewalls and EDR is not sufficient, since Sani Marc has dozens of data centers and warehouses across 16 locations in Canada and one in Europe. Therefore, the company is searching for a more detailed security solution that offers application-level protection.
- Email or URL breaches: According to George Henderson, Sani Marc’s IT Manager, most network dangers in their company originate from users who request others to join the network via email or a URL. Therefore, Sani Marc is intended to add an inside barrier to prevent lateral movement inside their network.
- Complex implementation and maintenance: The current security systems were labor-intensive and costly. Sani Marc’s has a small IT team of six, hence they need a solution that is simple to implement and requires minimal maintenance.
Solutions and outcome
Sani Marc mitigated a micro segmentation solution for all of its clients and servers in 30 days, using an automated “95% hands-off” procedure.
- AI in micro segmentation: The AI support in the micro segmentation solution allowed the company to eliminate manual rule adjustments by creating automated rules and policies (that only required 2-3 days of fine-tuning).
- Increased transparency: The company claims that it achieved transparency by micro segmenting its network after 30 days of observing all connections, enabling it to deploy multi-factor authentication (MFA) through all ports, protocols, and applications.
- Lowered operating costs: The company claims that the new micro segmentation solution enabled them to stop using an externally hosted zero trust identification system, saving $150k in three years.8
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 NCCM Software: Based on 4,000 Reviews
- Role-based access control (RBAC)
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
AIMultiple can assist your organization in finding the right vendor.
- 1. ”FEDERAL BUREAU OF INVESTIGATION Internet Crime report 2023”. FEDERAL BUREAU OF INVESTIGATION, IC3. 2023. Retrieved May 13, 2024.
- 2. ”CASE STUDY INSIGHTS: MICRO-SEGMENTATION TRANSFORMS SECURITY”. VMWare. 2016. Retrieved May 9, 2024.
- 3. Securing, Virtualizing, and Micro-Segmenting Private Banking Infrastructure with Cisco.
- 4. Flex Case Study - Palo Alto Networks.
- 5. ”CHILDREN’S MERCY KANSAS CITY FAST-TRACKS NETWORK SEGMENTATION”. Claroty. 2023. Retrieved May 13, 2024.
- 6. Leading Hospital Network Secures Rapid Growth with Illumio | Illumio Customers. Illumio
- 7. ”Modern Woodmen Enables Segmentation, Network Detection and Response”. VMWare. 2021. Retrieved May 9, 2024.
- 8. Sani Marc saves 3x with Zero Networks | Zero Networks.



Comments
Your email address will not be published. All fields are required.