The increased mobility in introduces risks of data loss or theft, which can lead to severe financial losses and reputational damage for companies. Effective Data loss prevention (DLP) software need to prevent the unauthorized movement of private data and personally identifiable information (PII) to limit reputational and financial risk.
Explore DLP fundamentals, challenges organizations face when implementing DLP solutions, and actionable strategies to overcome these hurdles.1
If you are already aware of data loss prevention and want to leverage an automated tool, here is a guide and list of the top DLP software.
What is data loss prevention (DLP)?
Data loss prevention (DLP) refers to strategies, tools, and practices aimed at detecting and preventing unauthorized access, transfer, or exposure of sensitive business data. DLP solutions help organizations detect and prevent data breaches, ex-filtration, or unwanted destruction of sensitive data. It is essential for organizations to protect their sensitive data and maintain compliance with regulatory requirements.
Key elements of DLP include:
- Data Identification: Classifying and tagging sensitive data.
- Data Visibility: Monitoring data access and movement across systems.
- Access Control: Restricting data access based on user roles and permissions.
Types of DLP
Data loss prevention has three types based on the different business environments that the solutions and practices are targeted towards.
- Endpoint DLP: Protects data on end-user devices such as laptops, smartphones, and desktops by monitoring and controlling activities that could lead to data breaches. Example: Blocking unauthorized file transfers from a company laptop to an external drive. For more on Endpoint DLP and software comparison.
- Network DLP: Monitors and secures data in transit across the network, preventing unauthorized data transfers and ensuring sensitive information does not leave the organization’s network, such as protecting email communications, instant messaging, and file transfers. Example: Restricting sensitive email attachments to external recipients. For more on Network DLP and software comparison.
- Cloud DLP: Safeguards data stored in cloud services by applying security policies and controls to prevent unauthorized access and data leakage from cloud-based environments, such as Google Drive, Dropbox, and AWS. Example: Preventing unauthorized downloads of sensitive files from a shared cloud folder. For more on Cloud DLP and software comparison.
What are the causes of data leaks?
Data leaks in organizations can occur due to a variety of reasons, often involving both technical vulnerabilities and human factors. This section highlights some of the major causes of data leaks and breaches in organizations.
Read more: Data breach incident response.
1. Human errors
One of the most common causes of data leaks is human error. This can include accidental sharing of sensitive data, misconfiguring databases, sending sensitive data to the wrong recipient, or even losing devices containing sensitive data.
This can also happen via the various communication channels employees use, including mobile devices, to send data and store their data in many different places. If they don’t follow the organization’s data loss prevention and data usage policies, unauthorized parties can gain access to sensitive business data, leading to data leaks and breaches.
2. External threats
Malware and other cyber attacks, like data exfiltration attempts, are common causes of data losses. For example, opening suspicious emails or accessing untrusted websites can lead to data breaches.
2.1. Phishing attacks
Cybercriminals often use phishing attacks to trick employees into revealing confidential or sensitive data, such as login credentials. Once these credentials are compromised, attackers can gain unauthorized access to the organization’s systems and data.
2.2. Weak or compromised passwords
Weak or reused passwords can be easily guessed by attackers. Additionally, if an employee uses the same password across multiple services, a breach in one can lead to a compromise in another, including the organization’s systems.
3. Insider threats
Giving access permission to sensitive data can enable a malicious insider to copy or steal your business data, including proprietary data and confidential information.
Here is our detailed research on insider threat:
4. Outdated or unpatched software
Vulnerabilities in software can be exploited by attackers if they are not promptly patched. Organizations that fail to keep their software and systems updated are at a higher risk of data breaches.
Why is data loss prevention important?
Stats from the IBM Cost of a Data Breach Report:2
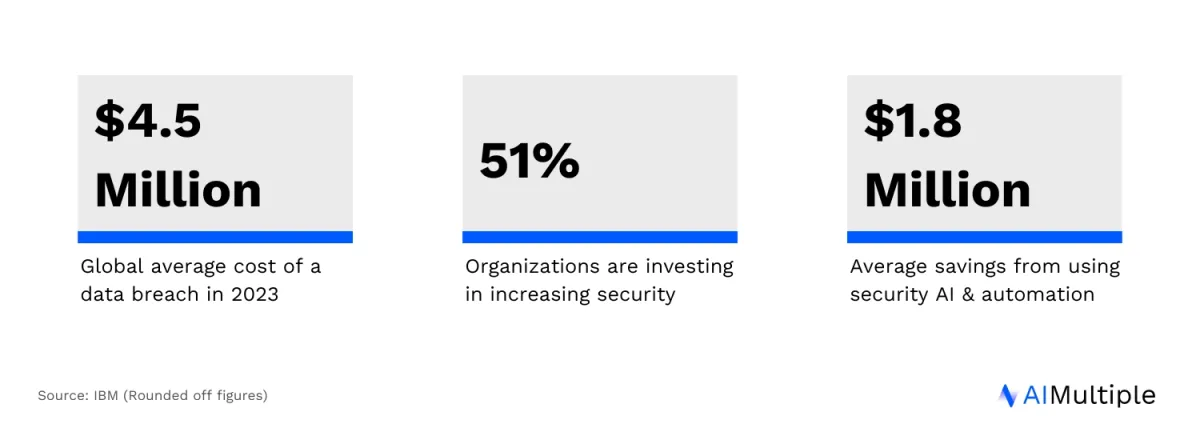
Data loss can also damage companies’ productivity, reputation, and revenue. For these reasons, a detailed data loss prevention strategy is crucial to secure companies’ confidential or sensitive data. A comprehensive data loss prevention solution can reduce the data loss risk by monitoring endpoint activities and filtering data streams, and by using machine learning for better detection and prevention.
What are the top DLP challenges and how to overcome them?
Implementing effective Data Loss Prevention is essential for organizations to protect data, especially sensitive information like personally identifiable information (PII) and financial data. However, there are several challenges in achieving this. Here are the top 5 DLP challenges and strategies to overcome them:
1. Identifying sensitive data
Challenge: One of the biggest hurdles is accurately identifying sensitive data, such as PII, business-critical data, and financial information, which need protection.
Recommendations: You can implement automated DLP tools that utilize machine learning to analyze and classify data. These tools can be trained to recognize various forms of sensitive data, enhancing data visibility and ensuring that the right data is protected.
2. Balancing data access and security
Challenge: Ensuring employees have the necessary access to company data while preventing unauthorized users from accessing sensitive information.
Recommendations: Some DLP solutions offer granular data access controls. You can implement role-based access policies and regularly audit access logs to ensure that only authorized personnel have access to sensitive data. This can lead to balanced operational efficiency and security.
3. Monitoring data across diverse environments
Challenge: With data spread across cloud repositories, consumer cloud storage services, and on-premises servers, tracking data movement and storage becomes complex.
Recommendations: Consider deploying a DLP software that offers comprehensive coverage across all platforms where data is stored or processed. You should also ensure that these tools can monitor data transfer and storage in real time. They should also provide visibility into where data is stored, how it’s being used, and who is accessing it.
4. Compliance and auditing requirements
Challenge: Keeping up with various regulatory compliance standards like the General Data Protection Regulation (GDPR) requires strict control over how data is handled.
Recommendations:
- An AI-powered DLP tool that is designed to help with compliance can make this process significantly efficient. The tool should have features for encrypting data, generating detailed reports for auditing, and ensuring that confidential and critical information handling aligns with regulatory requirements.
- It is also important to regularly train your staff on compliance requirements and the importance of data protection. This ensures that everyone understands their role in maintaining compliance.
5. Protecting against insider threats:
Challenge: Insider threats, where employees or associates misuse access to sensitive data, pose a significant risk.
Recommendations:
- You can implement strict access controls and divide responsibilities among employees, along with conducting thorough background checks of new hires.
- It is also important to enhance physical security measures, maintain a positive work environment, and establish clear procedures for both ongoing audits and the management of departing employees.
To learn more about data loss prevention best practices.
HIPAA Compliance and DLP
HIPAA places extensive data security requirements on businesses that have access to, process, and store protected health information. DLP is vital for organizations that need to comply with HIPAA.
DLP solutions can help organizations identify, classify, and tag data that is covered by regulations.
Further reading
- RPA for Cybersecurity: Use Cases & Best Practices
- Top 10 Network Security Policy Management Solutions (NSPM)
- Top 10 Firewall Audit Software & Review-based Analysis
If you have questions, we would like to help:
External resources
- 1. IBM. Average cost of a data breach worldwide from May 2020 to March 2023, by industry (in million U.S. dollars). Statista. Accessed: 16/January/2024.
- 2. Cost of a data breach 2024 | IBM.

Comments
Your email address will not be published. All fields are required.