Network security statistics show that 420+ million people were exposed to data breaches in the U.S. in 2022.1 Demilitarized Zone (DMZ) can help companies:
- Enhance network security and network visibility.
- Secure sensitive data against the most common cyber attack vectors.
Learn about Demilitarized Zone (DMZ), its examples, implementations and benefits:
What is Demilitarized Zone (DMZ) network security?
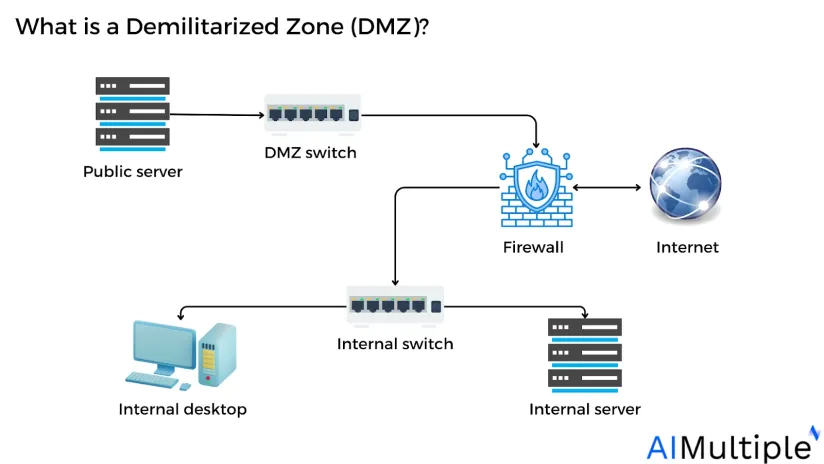
A Demilitarized Zone (DMZ) network is a subnetwork containing an organization’s publicly accessible services. It serves as an exposed point to an untrusted network, often the Internet.
The purpose of a DMZ is to provide an additional layer of protection to an organization’s local network.
Why is DMZ network security important?
DMZs add a layer of network segmentation to defend internal operational technology. These subnetworks limit external access to internal servers and assets, making it more challenging for attackers to penetrate the internal network. This method is appropriate for both individual usage and large companies.
A DMZ is designed to achieve two primary objectives:
1. The first step is to separate public access assets from the rest of your network.
2. The second step is to minimize complexity.2
Read more: Mandatory access control (MAC), role-based access control (RBAC), and network segmentation examples.
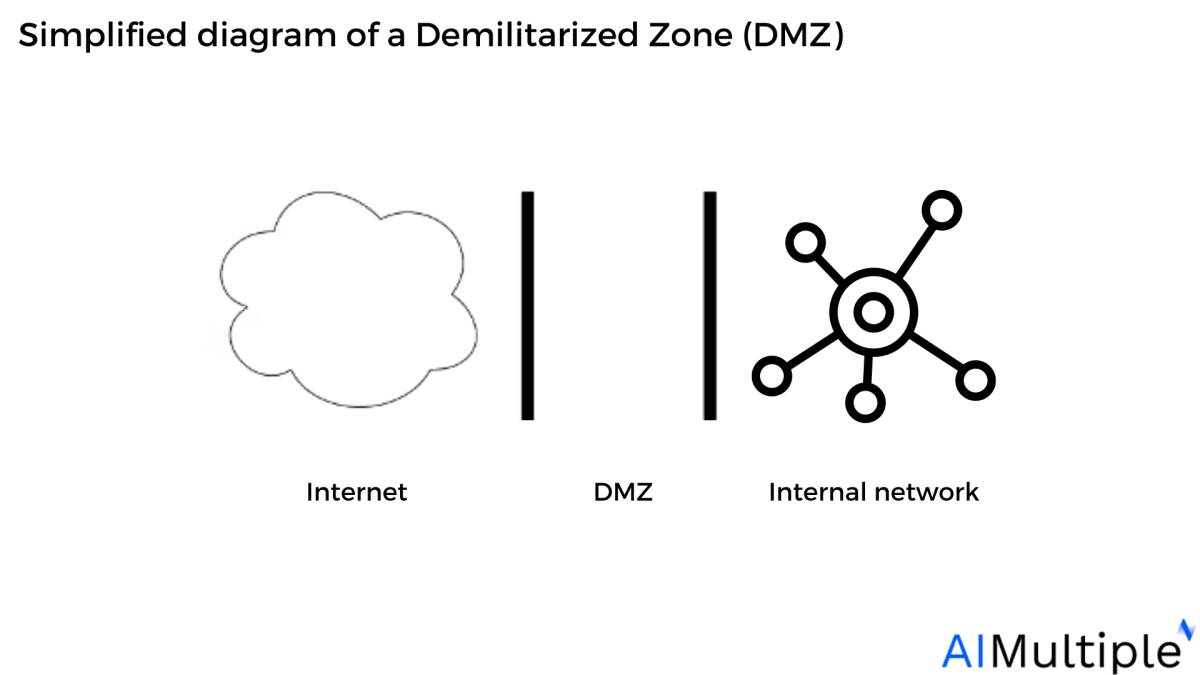
How does a DMZ work?
The DMZ works by allowing secure connection between protected company resources, such as internal databases, and authorized Internet traffic.
DMZ creates a buffer zone between the public internet and private networks and the DMZ subnet is configured between two firewalls. All internal network packets are inspected by a firewall or other security appliances before being sent to DMZ servers.
DMZ examples
DMZ example 1
As seen in Figure 1, the DMZ network is neither within nor outside the firewall. It is accessible through both internal and external networks.
One of the primary advantages of this network diagram is isolation. For example, If the email server is hacked, the attacker will be unable to access the internal network. In this scenario, the attacker may access various servers in the DMZ as they share the same physical network.
Figure 1: Simple DMZ diagram
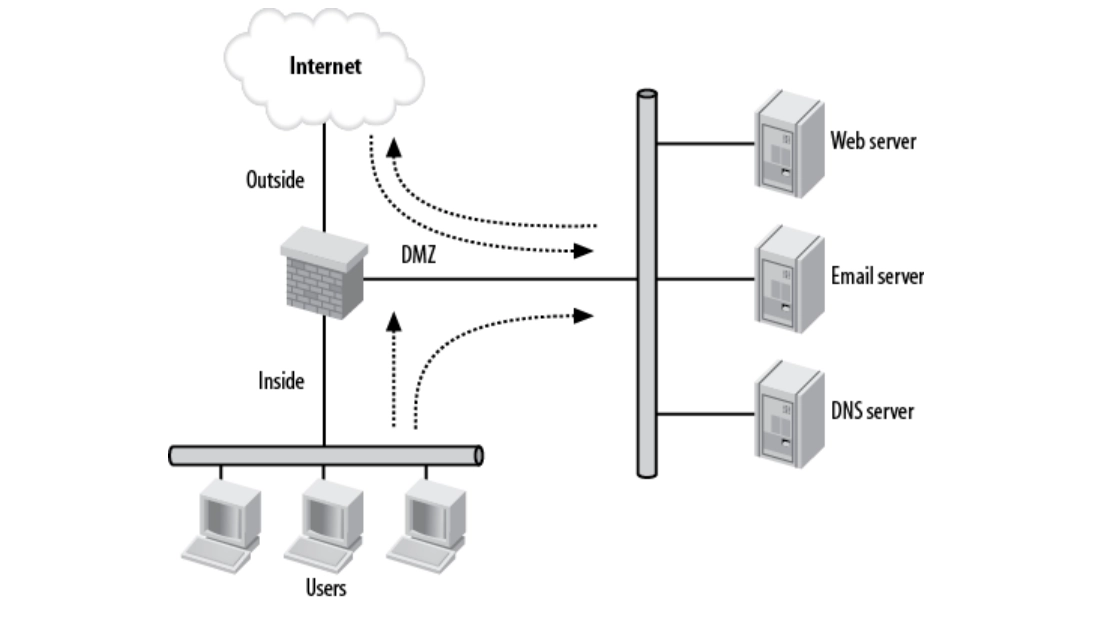
Source: International Journal of Wireless and Microwave Technologies3
In this network, DMZ helps to achieve the following:
- Inside network: The internal network can start connections to external networks, but the network cannot start connections to the internal network.
- Outside network: The outside network cannot establish connections with the inner network, however, the outside network can begin connections to the DMZ.
DMZ example 2: A DMZ connected to a third-party device
Another typical DMZ approach is connecting to a third-party device, such as a vendor. Figure 2 depicts a network with a vendor linked by T1 to a router in the DMZ.
This DMZ example can be used when companies outsource their systems to an outside party, allowing access to the vendor’s server via this setup.
Figure 2: DMZ connecting to a vendor
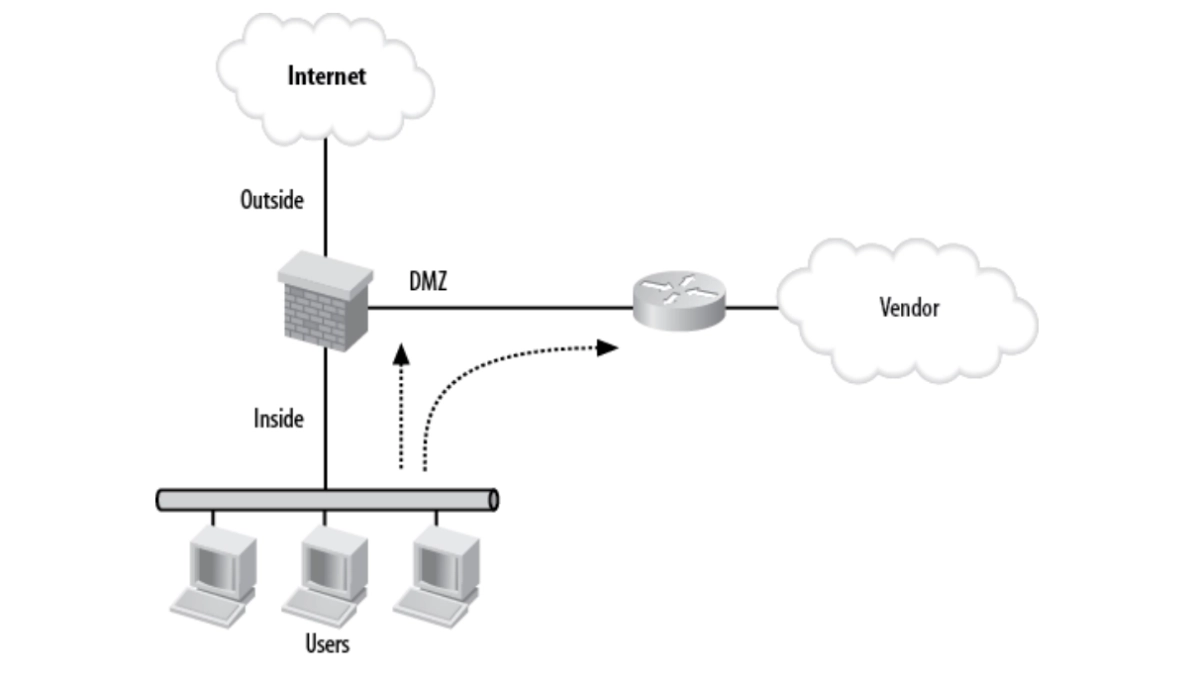
Source: O’Reilly Media4
DMZ example 3: Multiple DMZs connected to a third-party device
Sometimes a single DMZ is insufficient for organizations that operate complex networks. Figure 3 depicts a network that has several DMZs. The design combines the first two examples: the Internet is outside, and the users are within the network.
Figure 3: Multiple DMZs
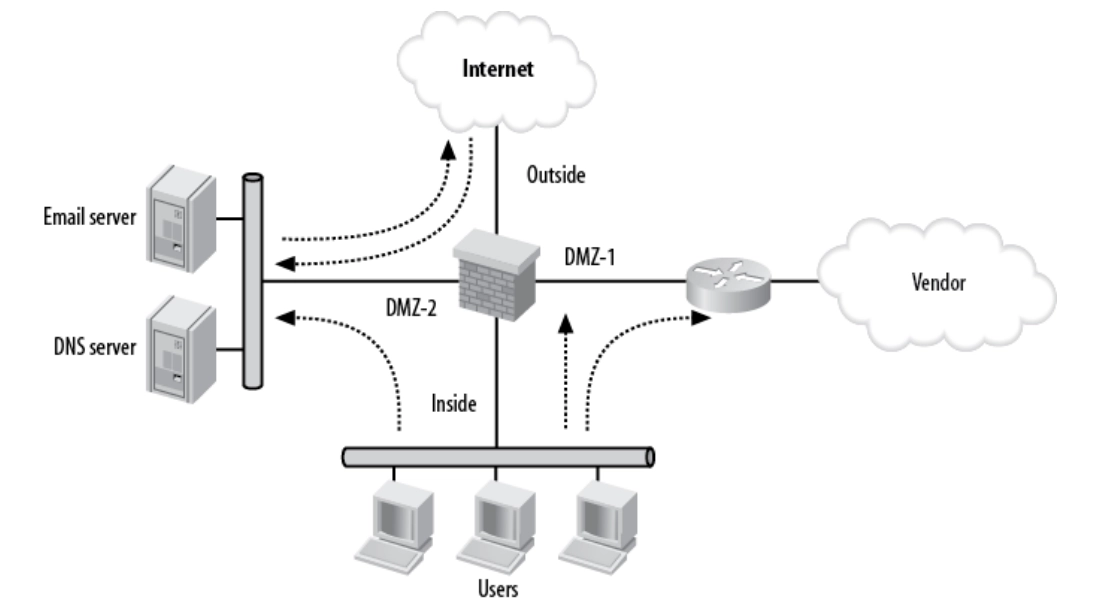
Source: O’Reilly Media5
- DMZ-1 is an access point to a vendor.
- DMZ-2 is where the Internet servers are located.
The security criteria remain the same as in the previous section (example 2), but it must additionally be evaluated whether DMZ-1 is allowed to start connections to DMZ-2 and vice versa. This helps to increase granular network security across complex networks
DMZ architecture
A DMZ can be configured in a variety of ways, ranging from a single firewall to dual or multiple firewalls. The majority of current DMZ architectures include twin firewalls that can be scaled to support complex networks.
1. Single firewall
A single firewall with at least three network interfaces is needed to build a network architecture that includes a DMZ.
Figure: Illustration of a single firewall architecture
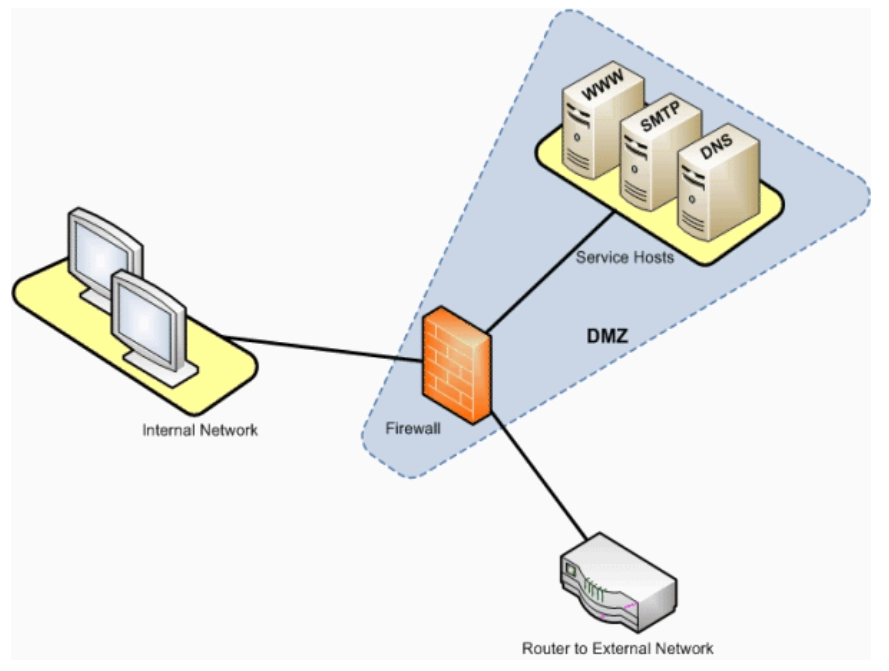
Source: SAP6
2. Dual firewall
This implementation creates a DMZ using two firewalls.
Figure: Illustration of dual firewall architecture
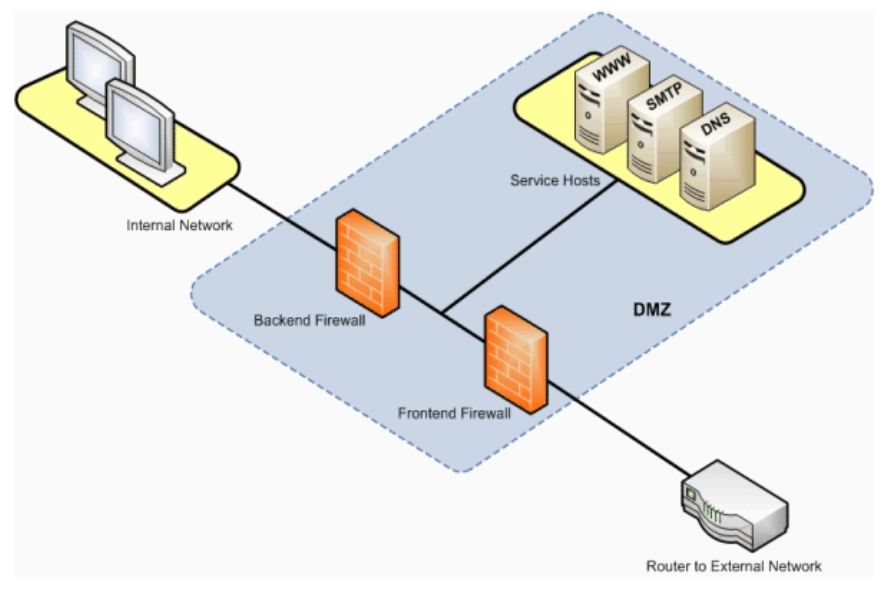
Source: SAP7
Why to use dual firewalls: Dual firewalls offer a more secure system. In some companies, the two firewalls are offered by separate providers. If an attacker can breach the first firewall, it may take longer to breach the second one if it is built by a different manufacturer, making it less likely to fall victim to the same vulnerabilities.
Benefits of Demilitarized Zone (DMZ)
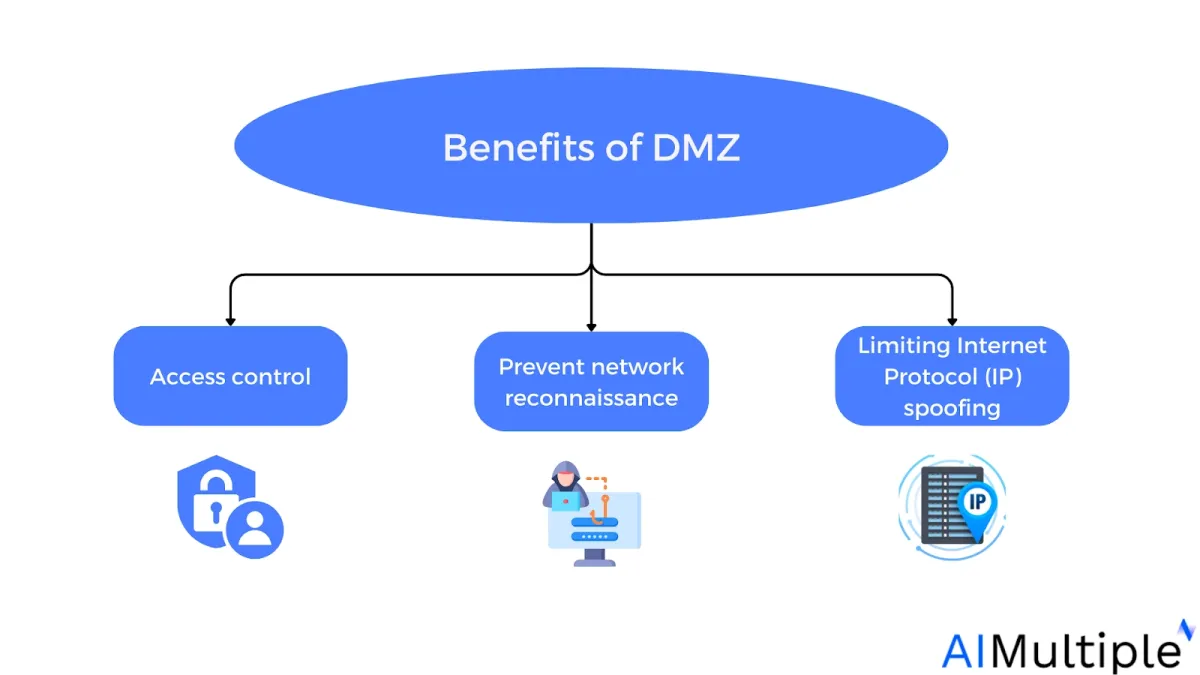
A DMZ’s principal value is that it provides public internet users with access to specific protected services while acting as a barrier between those users and the company’s internal network.
This line of defense provides various security benefits:
Provides access controls: A DMZ network controls access to services accessible over the internet that are not within a company’s network perimeter. It also adds a layer of network segmentation, increasing the amount of barriers a user must overcome before getting admission to a company’s private network.
Prevent network reconnaissance: A DMZ limits an attacker from assessing prospective targets on the network. Even if a machine in the DMZ is hacked, the internal firewall defends the private network by isolating it from the DMZ. This configuration makes external network exploits more difficult.
Limiting Internet Protocol (IP) spoofing: Attackers try to obtain unauthorized access to networks by spoofing an IP address of an authorized device logged into a network. A DMZ can detect and prevent such spoofing efforts while another service checks the IP address’s validity.
Applications of DMZs
Cloud services: Some cloud services employ a hybrid security strategy in which a DMZ is established between the company’s on-premises network and its logical network. This strategy is commonly employed when the company’s services run partially on-premises and partially over a logical network.
Home networks: A DMZ can also be useful for home networks that use LAN settings and broadband routers. Several household routers include DMZ options or DMZ host settings. These options enable users to connect only one device to the internet.
Industrial control systems (ICS): DMZs may provide a solution to the security problems associated with ICS.
Most of the operational technology (OT) equipment that connects to the internet is not as well-designed for mitigating attacks as IT devices are. A DMZ can strengthen OT network segmentation, making it more difficult for malware, viruses, or other network threats.
Companies commonly combine the listed software for DMZ security:
Microsegmentation tools: Separate a network into granular segments and implement security controls based on the needs of each segment.
NCCM software: Monitor information about your organization’s network devices by documenting network device configurations.
DSPM vendors: Provide network visibility into where to find sensitive data, who has access to it, and how it has been used across the cloud.
Open source microsegmentation tools: Enable control and enforce network communication policies at the API layer to block the network traffic flow.
Network security policy management solutions (NSPM): Protect network infrastructure using firewalls and security policies against all threats.
Network security audit tools: Identify threats, vulnerabilities, and malicious activity to help companies mitigate cyber attacks and follow compliance with regulations.
SDP software: Deliver a software-defined perimeter (SDP) across the cloud to determine who gets access to what resources.
For guidance on choosing the right tool or service, check out our data-driven lists of unified threat management (UTM) software.
Further reading
- Top 10 Microsegmentation Tools
- Microsegmentation: What is it? Benefits & Challenges
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor for firewall audit and cybersecurity needs. Feel free to reach out to us:
External links
- 1. Number of data breaches and victims U.S. 2024| Statista. Statista
- 2. ”The Science DMZ: A network design pattern for data-intensive science“. (PDF). Proceedings of the International Conference on High Performance Computing, Networking, Storage and Analysis. August 14, 2014. Retrieved February 6, 2024.
- 3. ”Evaluation the Performance of DMZ“. (PDF). International Journal of Wireless and Microwave Technologies. January 2018. Retrieved February 6, 2024.
- 4. ”Network Warrior“. (PDF). O’Reilly Media. May 2011. Retrieved February 6, 2024.
- 5. ”Network Warrior“. (PDF). O’Reilly Media. May 2011. Retrieved February 6, 2024.
- 6. ”Understanding DMZ and Firewall“. SAP. 2024. Retrieved February 6, 2024.
- 7. ”Understanding DMZ and Firewall“. SAP. 2024. Retrieved February 6, 2024.


Comments
Your email address will not be published. All fields are required.